当前位置:网站首页>Codasip adds verify safe startup function to risc-v processor series
Codasip adds verify safe startup function to risc-v processor series
2022-07-05 15:44:00 【TechWeb】
【TechWeb】7 month 5 Daily news , Customizable RISC-V Processor intellectual property (IP) And the leader in Processor Design Automation Codasip Recently announced that ,Veridify Security The company's anti quantum security tools can now be supported by the secure boot function Codasip Of RISC-V processor . When firmware is loaded into Codasip On the processor ,Veridify The security algorithm will verify it , In order to make RISC-V Developers are convinced that embedded systems are safe and available .
Veridify The secure startup function of is based on an algorithm that runs faster than traditional encryption methods ; It only needs a small code space and ultra-low power consumption , Very suitable Codasip Low power embedded processor series . By using Veridify Methods ,Codasip Our customers can now easily verify the authenticity of firmware .

because Veridify Our verification method is quantum resistant to all known threats , They also support customers in the layout of embedded applications with long battery life Codasip processor , Such as remote monitoring system 、 Surveillance cameras and smart meters . Besides ,Veridify Tools can also be used to activate additional security functions , Such as security firmware update 、 Authentication and data protection .
2021 year ,Codasip and Veridify Reach cooperation intention , Introduce this safe start function Codasip Of RISC-V processor IP in . After repeated tests by two companies ,Codasip Of IP It's already in Veridify It has been verified on the platform — So that we can use Codasip Customers and developers of processors are convinced , They will take advantage of a fully compatible 、 A widely used and highly trusted secure boot source to verify the firmware on its processor .
Codasip Chief technical officer Zdenek Prikryl comments :“ take Veridify And Codasip The combination of processor cores can provide our customers with the greatest guarantee , It's about choosing Codasip Processors and tools , Customers not only choose the highest quality processors in the industry IP, And don't worry about malware in embedded firmware .”

“ We are happy to talk with Codasip cooperation , For its low power consumption RISC-V The processor provides a safe boot function for the future ,”Veridify Chairman and CEO Louis Parks Add .“Codasip Our customers can now be sure , Their firmware is real during startup , And believe what they use Codasip The processor of is safe and reliable throughout the life cycle of its equipment .”
边栏推荐
- sql server char nchar varchar和nvarchar的区别
- First PR notes
- wyt 。。
- SQL injection sqllabs (basic challenges) 1-10
- 定义严苛标准,英特尔Evo 3.0正在加速PC产业升级
- [brief notes] solve the problem of IDE golang code red and error reporting
- MySQL giant pit: update updates should be judged with caution by affecting the number of rows!!!
- The elimination strategy of redis
- Redis distributed lock principle and its implementation with PHP (1)
- Bugku's eyes are not real
猜你喜欢
Optional parameters in the for loop

Your childhood happiness was contracted by it
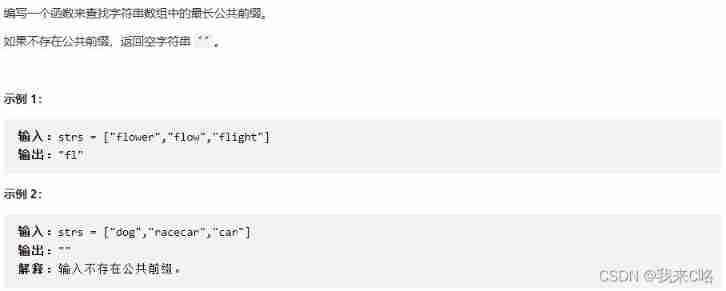
Huawei Hubble incarnation hard technology IPO harvester
Information collection of penetration test
![P1451 calculate the number of cells / 1329: [example 8.2] cells](/img/c4/c62f3464608dbd6cf776c2cd7f07f3.png)
P1451 calculate the number of cells / 1329: [example 8.2] cells
![1330: [example 8.3] minimum steps](/img/69/9cb13ac4f47979b498fa2254894ed1.gif)
1330: [example 8.3] minimum steps

数学建模之层次分析法(含MATLAB代码)
wxml2canvas
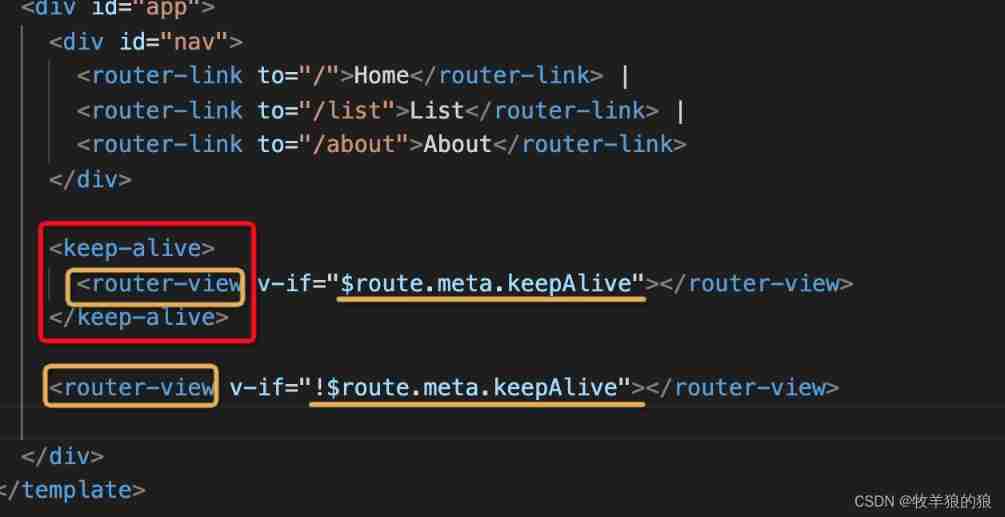
keep-alive
I spring and autumn blasting-1
随机推荐
Ctfshow web entry explosion
修改pyunit_time使得其支持‘xx~xx月’的时间文本
CODING DevSecOps 助力金融企业跑出数字加速度
Good article inventory
Information collection of penetration test
Common PHP interview questions (1) (written PHP interview questions)
Common MySQL interview questions
Nine hours, nine people, nine doors problem solving Report
keep-alive
Severlet learning foundation
RepLKNet:不是大卷积不好,而是卷积不够大,31x31卷积了解一下 | CVPR 2022
1330: [example 8.3] minimum steps
What are CSRF, XSS, SQL injection, DDoS attack and timing attack respectively and how to prevent them (PHP interview theory question)
No one consults when doing research and does not communicate with students. UNC assistant professor has a two-year history of teaching struggle
lv_ font_ Conv offline conversion
"Sequelae" of the withdrawal of community group purchase from the city
Bugku's steganography
Data communication foundation ACL access control list
Summary of the third class
Anti shake and throttling