当前位置:网站首页>Leetcode-6108: decrypt messages
Leetcode-6108: decrypt messages
2022-07-05 06:09:00 【Chrysanthemum headed bat】
leetcode-6108: Decrypt the message
subject
Topic linking
Here is the string key and message , Represent an encryption key and an encrypted message respectively . Decrypt message The steps are as follows :
Use key in 26 The order of the first occurrence of English lowercase letters is used to replace the letters in the table The order .
Align the replacement table with the common English alphabet , Form a comparison table .
According to the comparison table Replace message Every letter in .
Space ' ' remain unchanged .
for example ,key = "happy boy"( The actual encryption key will contain every letter in the alphabet At least once ), Accordingly , You can get some comparison tables ('h' -> 'a'、'a' -> 'b’、'p' -> 'c'、'y' -> 'd'、'b' -> 'e'、'o' -> 'f').
Returns the decrypted message .
Example 1: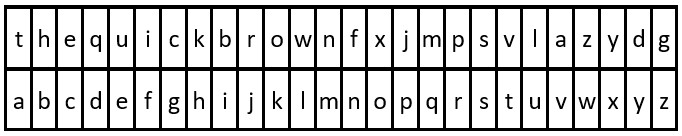
Input :key = "the quick brown fox jumps over the lazy dog", message = "vkbs bs t suepuv"
Output :"this is a secret"
explain : The comparison table is shown in the above figure .
extract "the quick brown fox jumps over the lazy dog" The first occurrence of each letter in can get a replacement table .
Example 2: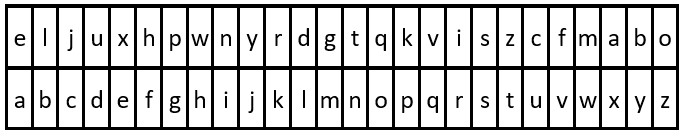
Input :key = "eljuxhpwnyrdgtqkviszcfmabo", message = "zwx hnfx lqantp mnoeius ycgk vcnjrdb"
Output :"the five boxing wizards jump quickly"
explain : The comparison table is shown in the above figure .
extract "eljuxhpwnyrdgtqkviszcfmabo" The first occurrence of each letter in can get a replacement table .
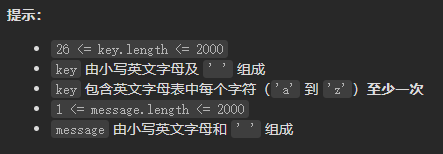
Problem solving
Method 1 : Hashtable
1. By hashing map, Record each letter in key The order in which they first appear , And assign corresponding letters .
2. Space directly skip , Replace letters
class Solution {
public:
string decodeMessage(string key, string message) {
unordered_map<char,char> map;
char c='a';
for(int i=0;i<key.size();i++){
if(key[i]==' ') continue;
if(!map.count(key[i])){
map[key[i]]=c;
c++;
}
}
for(int i=0;i<message.size();i++){
if(message[i]==' ') continue;
char c=message[i];
message[i]=map[c];
}
return message;
}
};
边栏推荐
- Common optimization methods
- The sum of the unique elements of the daily question
- Real time clock (RTC)
- Codeforces Round #732 (Div. 2) D. AquaMoon and Chess
- [article de jailhouse] jailhouse hypervisor
- 2022 极术通讯-Arm 虚拟硬件加速物联网软件开发
- QT判断界面当前点击的按钮和当前鼠标坐标
- One question per day 1765 The highest point in the map
- Data visualization chart summary (II)
- How to adjust bugs in general projects ----- take you through the whole process by hand
猜你喜欢
QQ computer version cancels escape character input expression
Full Permutation Code (recursive writing)

Educational Codeforces Round 116 (Rated for Div. 2) E. Arena
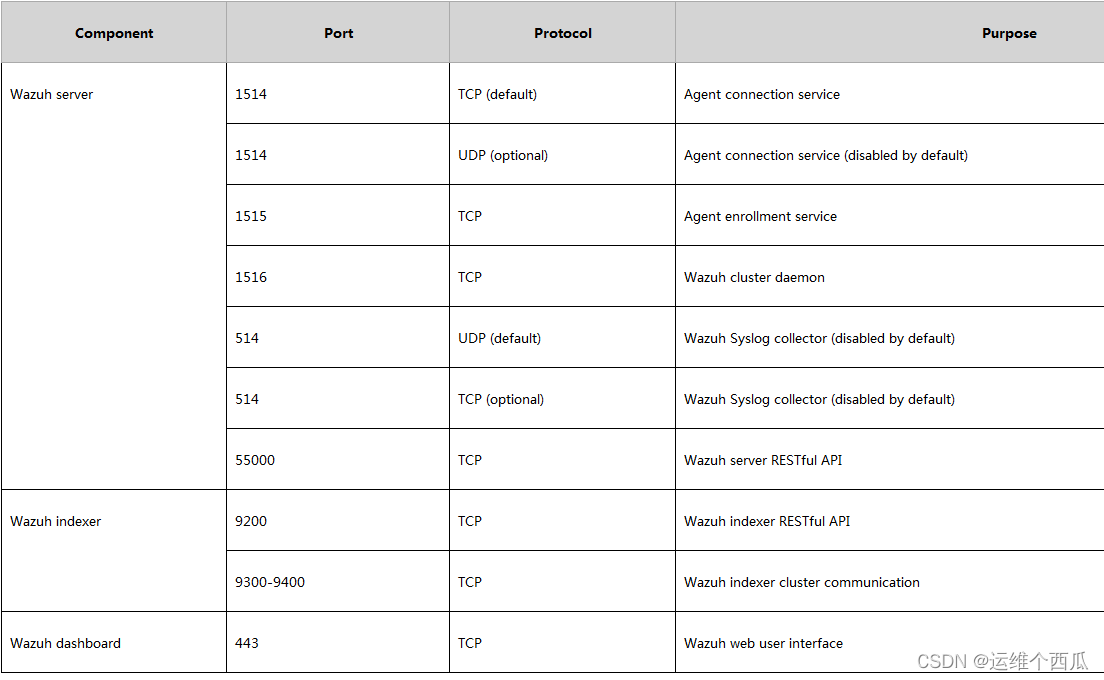
Introduction and experience of wazuh open source host security solution
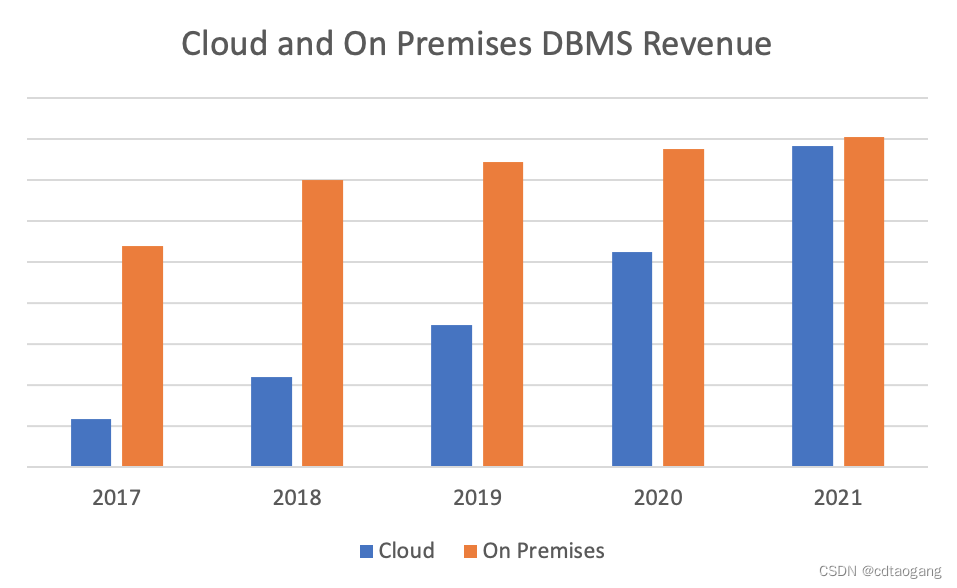
传统数据库逐渐“难适应”,云原生数据库脱颖而出
![[cloud native] record of feign custom configuration of microservices](/img/39/05cf7673155954c90e75a8a2eecd96.jpg)
[cloud native] record of feign custom configuration of microservices
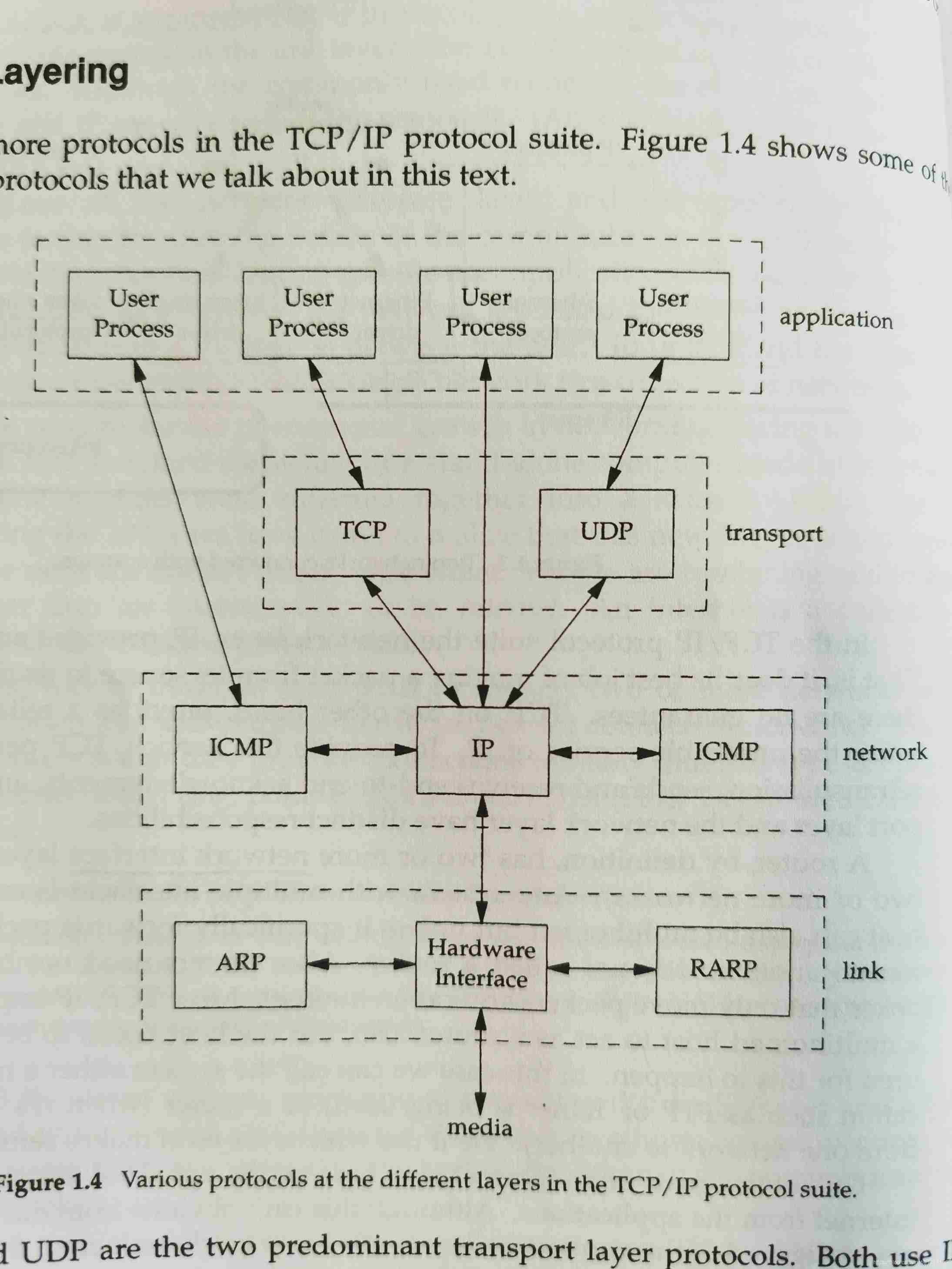
Brief introduction to tcp/ip protocol stack
Overview of variable resistors - structure, operation and different applications

全排列的代码 (递归写法)
6. Logistic model
随机推荐
2017 USP Try-outs C. Coprimes
Sqlmap tutorial (II) practical skills I
Erreur de connexion Navicat à la base de données Oracle Ora - 28547 ou Ora - 03135
Control unit
leetcode-6110:网格图中递增路径的数目
开源存储这么香,为何我们还要坚持自研?
927. Trisection simulation
【Rust 笔记】15-字符串与文本(下)
Error ora-28547 or ora-03135 when Navicat connects to Oracle Database
【Rust 笔记】13-迭代器(中)
R language [import and export of dataset]
Daily question 1342 Number of operations to change the number to 0
[jailhouse article] jailhouse hypervisor
打印机脱机时一种容易被忽略的原因
[rust notes] 16 input and output (Part 1)
可变电阻器概述——结构、工作和不同应用
全排列的代码 (递归写法)
中职网络安全技能竞赛——广西区赛中间件渗透测试教程文章
Educational codeforces round 109 (rated for Div. 2) C. robot collisions D. armchairs
Over fitting and regularization