当前位置:网站首页>1039 Course List for Student
1039 Course List for Student
2022-07-05 05:51:00 【Brosto_Cloud】
Zhejiang University has 40000 students and provides 2500 courses. Now given the student name lists of all the courses, you are supposed to output the registered course list for each student who comes for a query.
Input Specification:
Each input file contains one test case. For each case, the first line contains 2 positive integers: N (≤40,000), the number of students who look for their course lists, and K (≤2,500), the total number of courses. Then the student name lists are given for the courses (numbered from 1 to K) in the following format: for each course i, first the course index i and the number of registered students Ni (≤200) are given in a line. Then in the next line, Ni student names are given. A student name consists of 3 capital English letters plus a one-digit number. Finally the last line contains the N names of students who come for a query. All the names and numbers in a line are separated by a space.
Output Specification:
For each test case, print your results in N lines. Each line corresponds to one student, in the following format: first print the student's name, then the total number of registered courses of that student, and finally the indices of the courses in increasing order. The query results must be printed in the same order as input. All the data in a line must be separated by a space, with no extra space at the end of the line.
Sample Input:
11 5
4 7
BOB5 DON2 FRA8 JAY9 KAT3 LOR6 ZOE1
1 4
ANN0 BOB5 JAY9 LOR6
2 7
ANN0 BOB5 FRA8 JAY9 JOE4 KAT3 LOR6
3 1
BOB5
5 9
AMY7 ANN0 BOB5 DON2 FRA8 JAY9 KAT3 LOR6 ZOE1
ZOE1 ANN0 BOB5 JOE4 JAY9 FRA8 DON2 AMY7 KAT3 LOR6 NON9
Sample Output:
ZOE1 2 4 5
ANN0 3 1 2 5
BOB5 5 1 2 3 4 5
JOE4 1 2
JAY9 4 1 2 4 5
FRA8 3 2 4 5
DON2 2 4 5
AMY7 1 5
KAT3 3 2 4 5
LOR6 4 1 2 4 5
NON9 0使用map、set容器;
map实现字符串映射,set实现课程从小到大自动排序。
#include <iostream>
#include <vector>
#include <algorithm>
#include <string>
#include <set>
#include <map>
using namespace std;
map<string, set<int>>m;
int n, k;
map<string, int>cnt;
int main() {
cin >> n >> k;
int c, num; //课程编号,选课人数
string name;
for (int i = 0; i < k; i++) {
cin >> c >> num;
for (int j = 0; j < num; j++) {
cin >> name;
cnt[name]++;
m[name].insert(c);
}
}
for (int i = 0; i < n; i++) {
cin >> name;
cout << name << ' ' << cnt[name];
for (set<int>::iterator it = m[name].begin(); it != m[name].end(); it++) {
cout << ' ' << *it;
}
if (i != n - 1) {
cout << endl;
}
}
return 0;
}
边栏推荐
- One question per day 1447 Simplest fraction
- 【实战技能】如何做好技术培训?
- Sword finger offer 53 - ii Missing numbers from 0 to n-1
- Personal developed penetration testing tool Satania v1.2 update
- Convolution neural network -- convolution layer
- A problem and solution of recording QT memory leakage
- [article de jailhouse] jailhouse hypervisor
- Wazuh开源主机安全解决方案的简介与使用体验
- Sword finger offer 09 Implementing queues with two stacks
- 中职网络安全技能竞赛——广西区赛中间件渗透测试教程文章
猜你喜欢
Sword finger offer 05 Replace spaces
7. Processing the input of multidimensional features
【Jailhouse 文章】Jailhouse Hypervisor
Solution to game 10 of the personal field
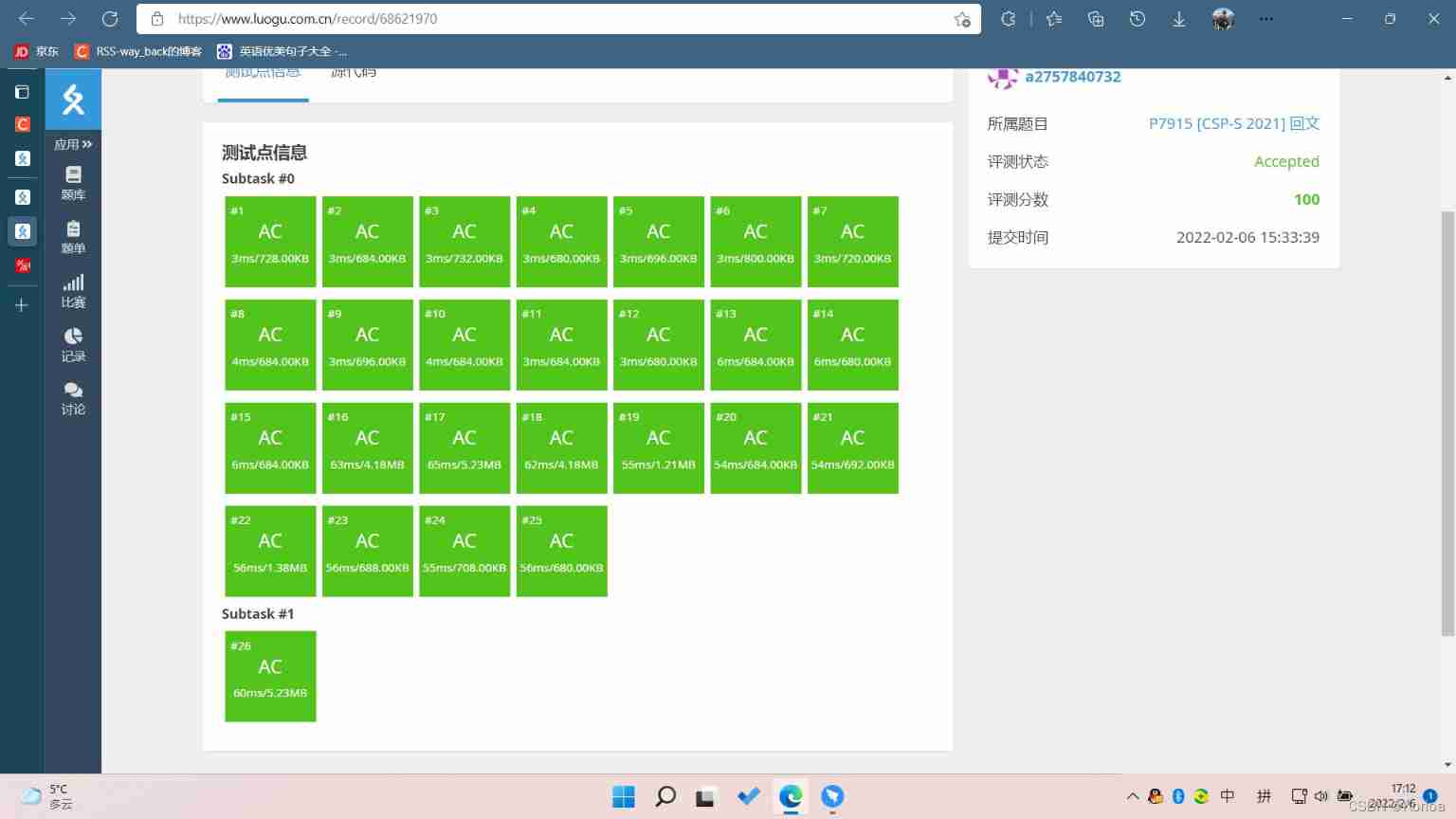
Palindrome (csp-s-2021-palin) solution
Analysis of backdoor vulnerability in remote code execution penetration test / / phpstudy of national game title of national secondary vocational network security B module

Chapter 6 data flow modeling - after class exercises
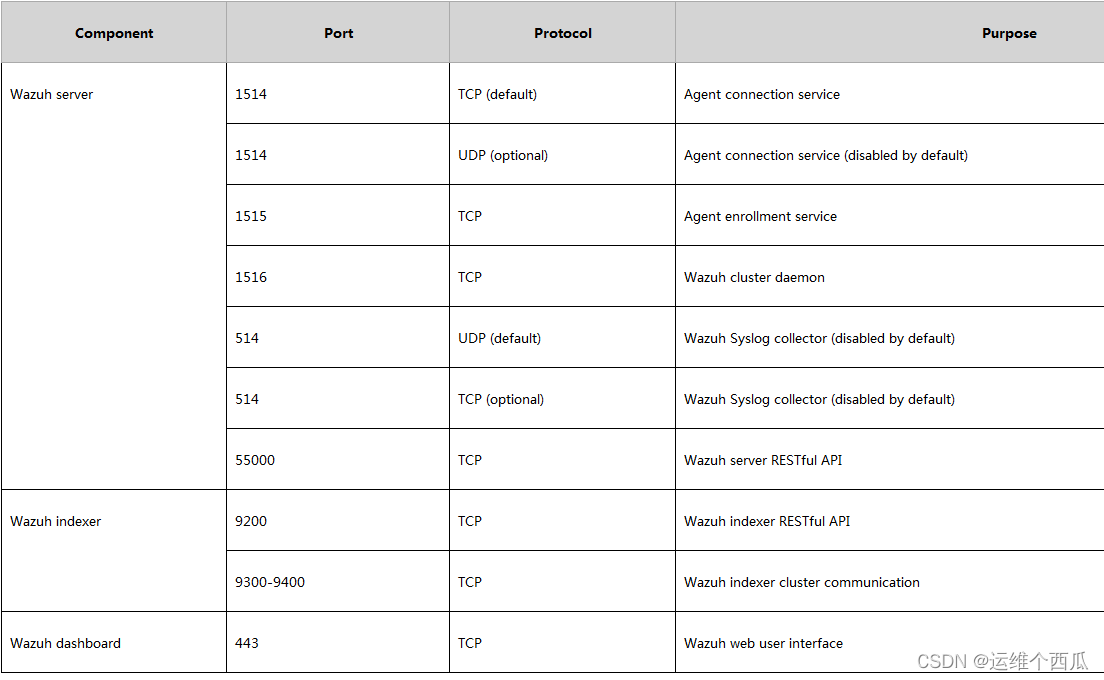
Introduction and experience of wazuh open source host security solution
In this indifferent world, light crying
1.14 - 流水线
随机推荐
一些工具的记录2022
Graduation project of game mall
Cluster script of data warehouse project
Light a light with stm32
全国中职网络安全B模块之国赛题远程代码执行渗透测试 //PHPstudy的后门漏洞分析
[jailhouse article] jailhouse hypervisor
LeetCode 0107.二叉树的层序遍历II - 另一种方法
Sword finger offer 06 Print linked list from beginning to end
卷积神经网络——卷积层
【Jailhouse 文章】Jailhouse Hypervisor
6. Logistic model
Educational codeforces round 109 (rated for Div. 2) C. robot collisions D. armchairs
【Rust 笔记】17-并发(下)
1.14 - 流水线
leetcode-22:括号生成
2022 pole technology communication arm virtual hardware accelerates the development of Internet of things software
Introduction and experience of wazuh open source host security solution
Annotation and reflection
2022年貴州省職業院校技能大賽中職組網絡安全賽項規程
Sword finger offer 04 Search in two-dimensional array