当前位置:网站首页>Build domain environment (win)
Build domain environment (win)
2022-07-06 14:03:00 【Lazy and talented】
Catalog
Common domain environments use :win2012 win7 win2003
Ben blog Environmental Science :Windows Server 2012 R2 and Win2008
1.Window Server 2012 R2 Server configuration
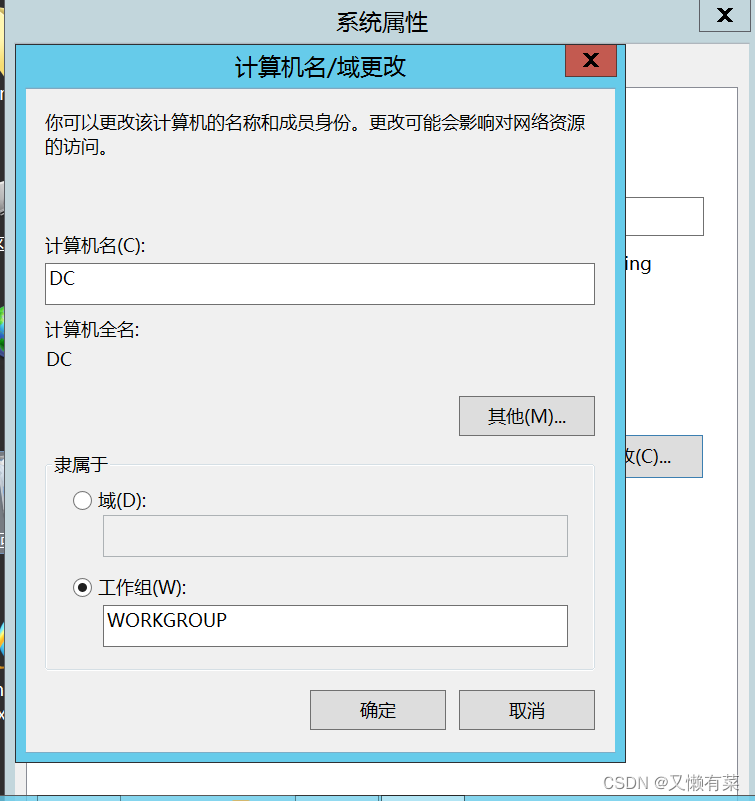
1) Change computer name DC( The computer used to store the active directory database )
3) Install domain controller (AD DS) and DNS service
4) Upgrade the server Click on the above “ Triangle exclamation point ”
5) add to Active Directory user
2.Win2008 Computer configuration
1) Set up DNS Resolve to server IP
2) adopt cmd ping DNS See if the configuration is successful
3) take win2008 Join in win2012 Created domain
4) Successfully joined the domain cai.yulab
Common domain environments use :win2012 win7 win2003
Server 2012 R2、Window7 perhaps Server 2003 The operating system Windows Domain environment .
Ben blog Environmental Science :Windows Server 2012 R2 and Win2008
MSDN, I tell you - Make a quiet tool station (itellyou.cn) https://msdn.itellyou.cn/
https://msdn.itellyou.cn/
1.Window Server 2012 R2 Server configuration
1) Change computer name DC( The computer used to store the active directory database )
Restart after the change
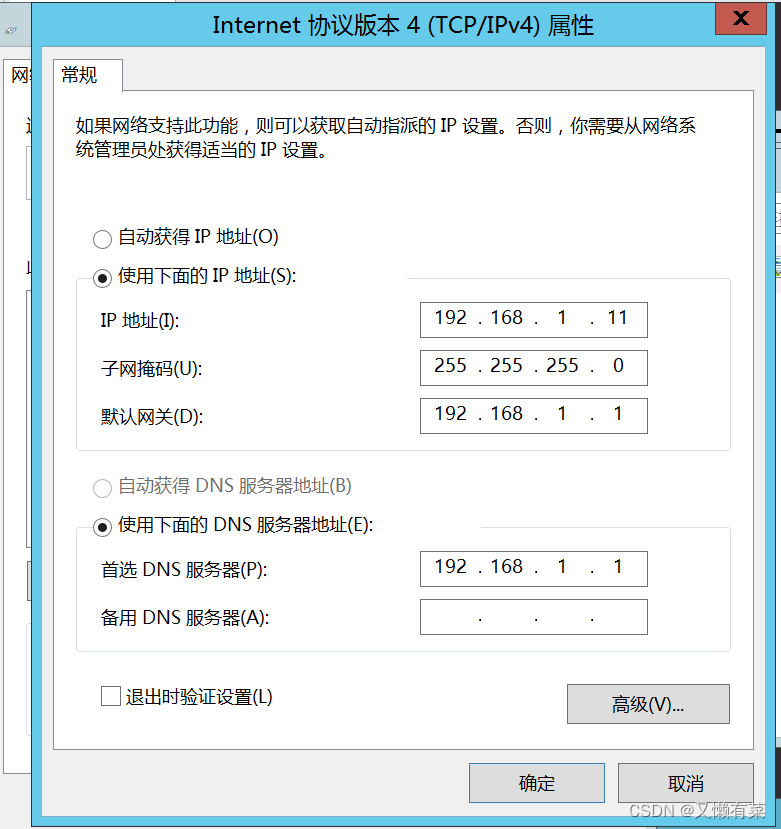
2) Setup server IP,DNS
Set up IP by 192.168.1.11( Don't set 192.168.1.1 It may overlap with the physical machine ip)
The subnet mask is 255.255.255.0
DNS Set to 192.168.1.11(win2012 As a server Set this IP)
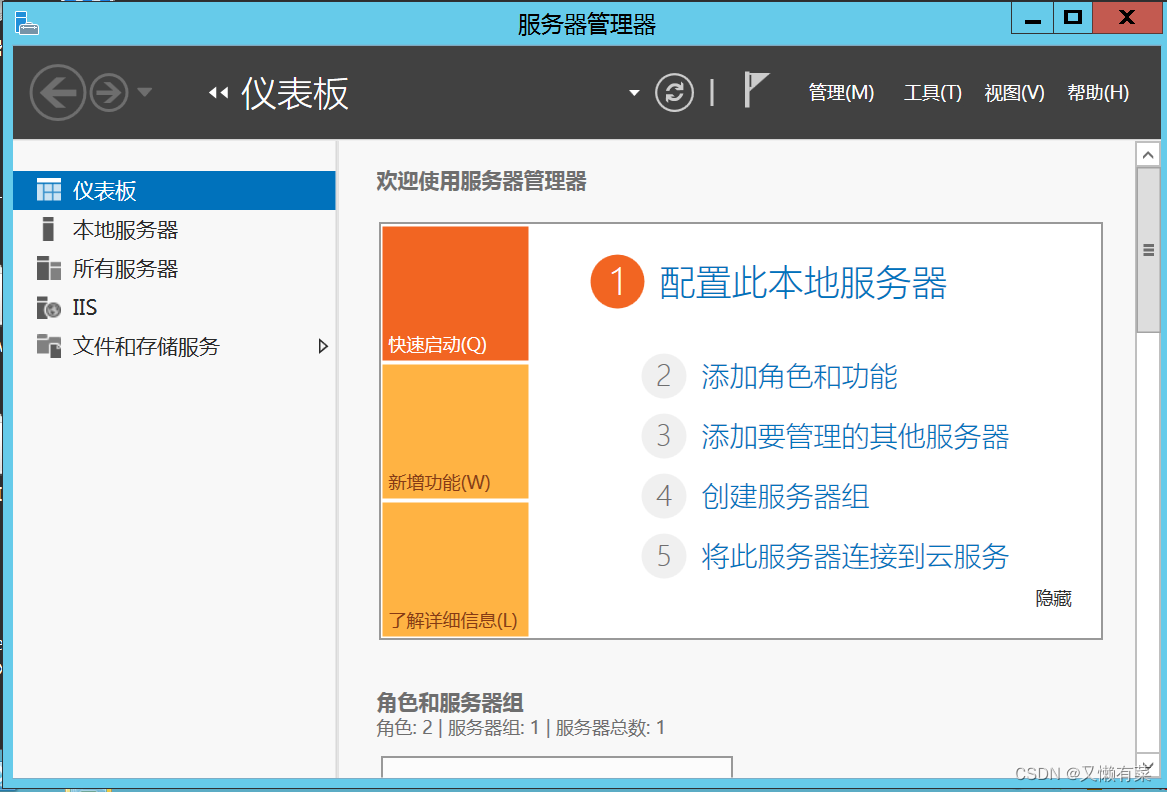
3) Install domain controller (AD DS) and DNS service
Sign in win2012 The server , You can see " Server Manager " window
0x01、 single click “ Add roles and features ” , Get into “ Add color correction and Function Wizard ” Interface . Again “ Before the start ” part , default setting .
single click “ next step ”, Get into “ Installation type ” part , choice “ Role based or feature-based installation ” Options .
single click “ next step ”, Get into “ Server selection ” part . default setting
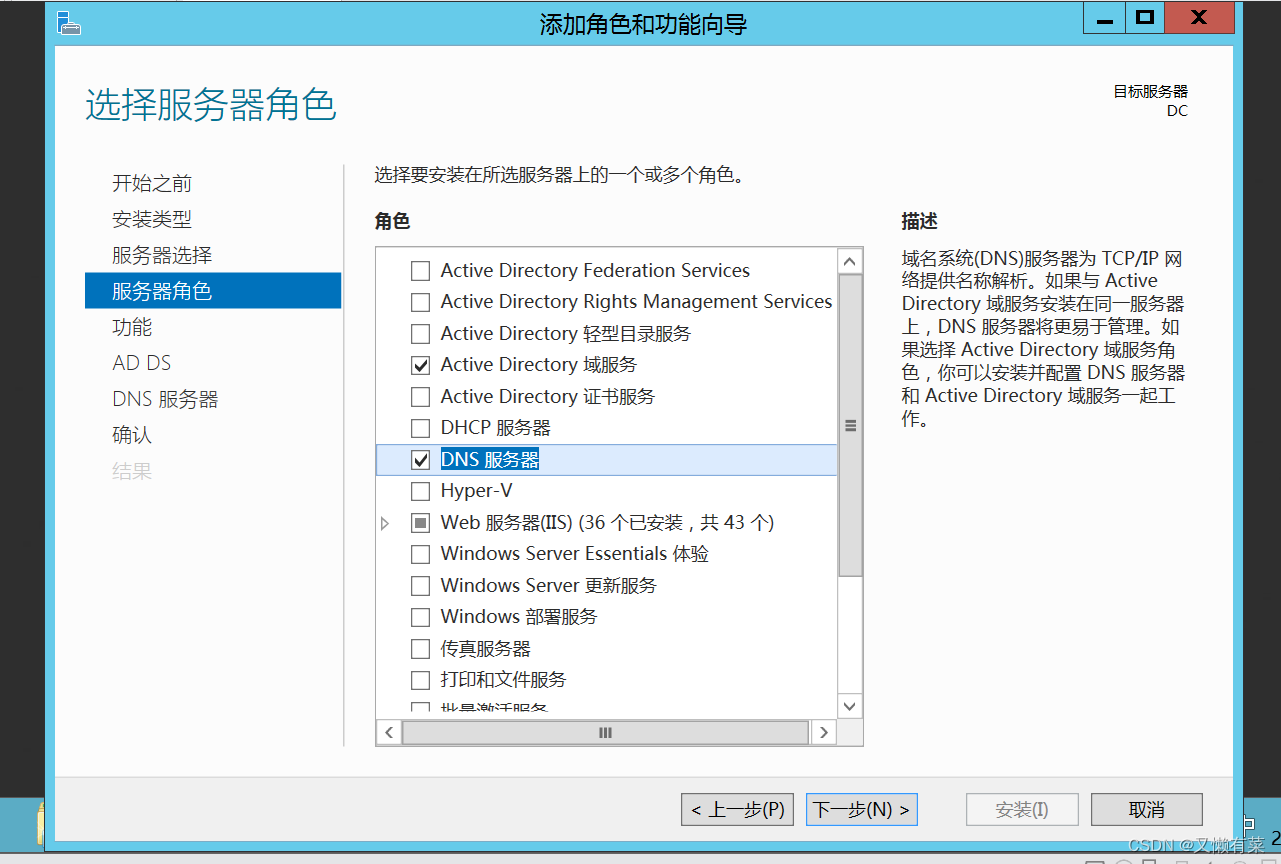
single click “ next step ”, Check “Active Directory Domain services ” and “DNS The server ”.
stay “ function ” Interface default settings . Default 、 Default
single click “ next step ”, Get into “ confirm ” part . next step wait for 2 minute restart
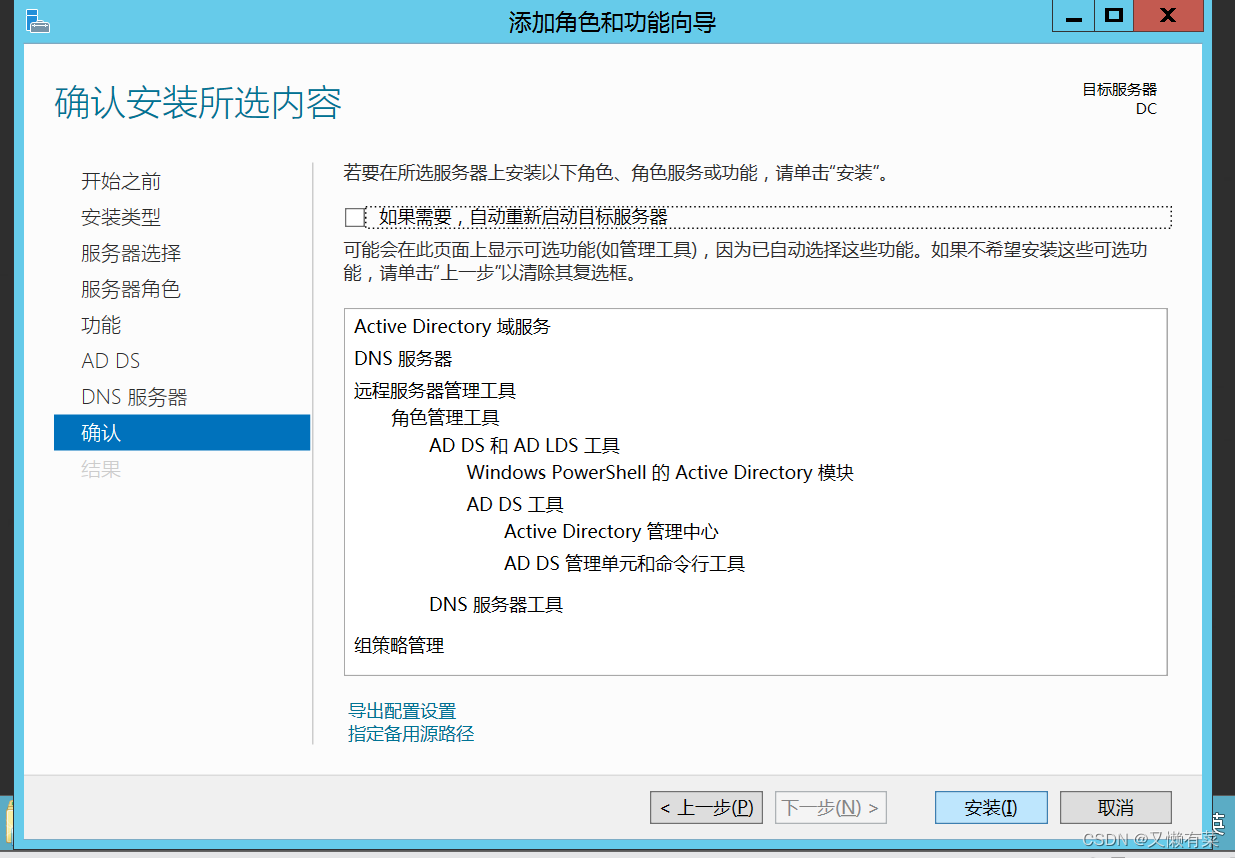
4) Upgrade the server Click on the above “ Triangle exclamation point ”
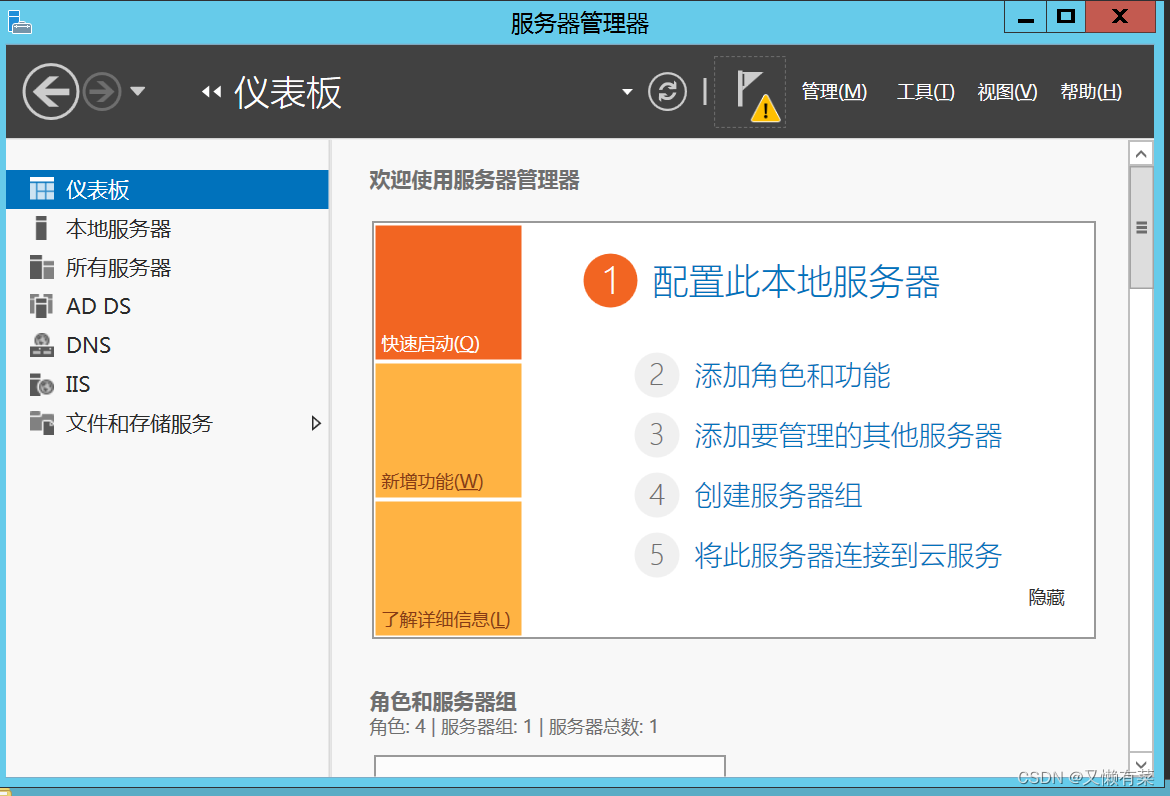
Click on “ Promote this server to a domain controller ”.
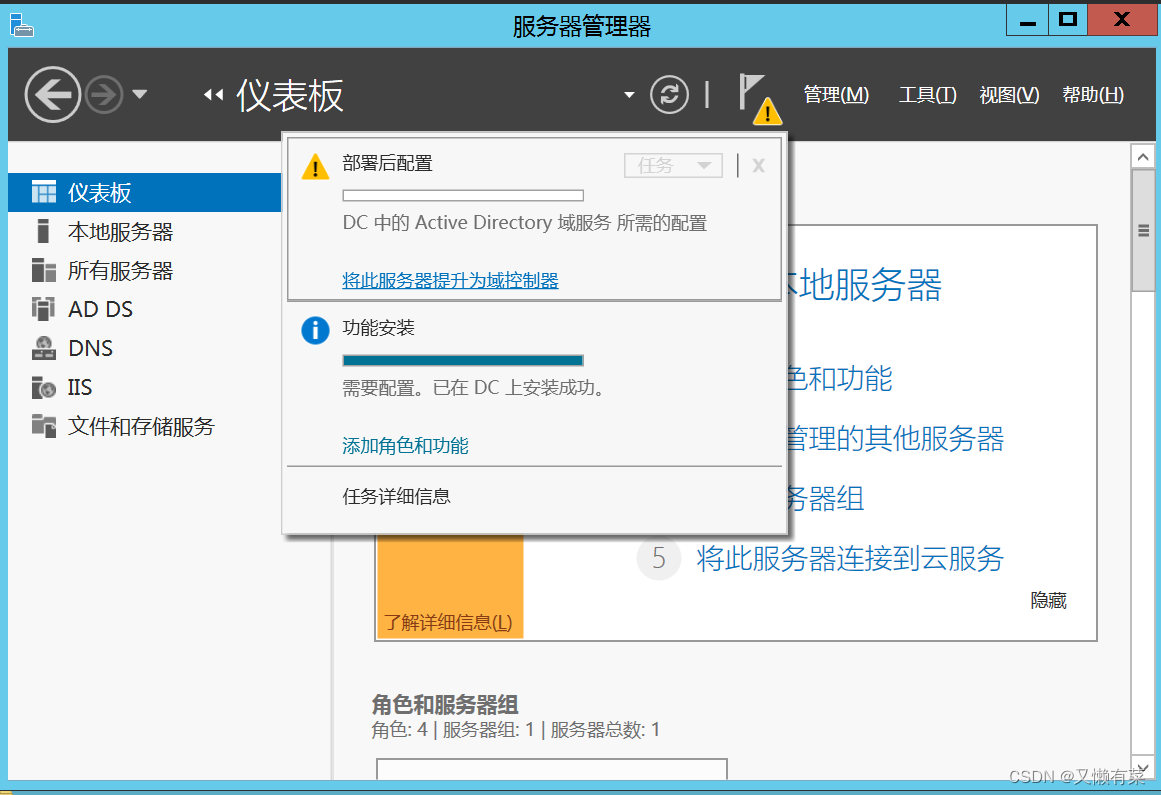
Get into “Active Directory Domain services configuration wizard ”
choice “ Add new forest ” , The root domain name should conform to DNS Domain name resolution
wait for 2 minute
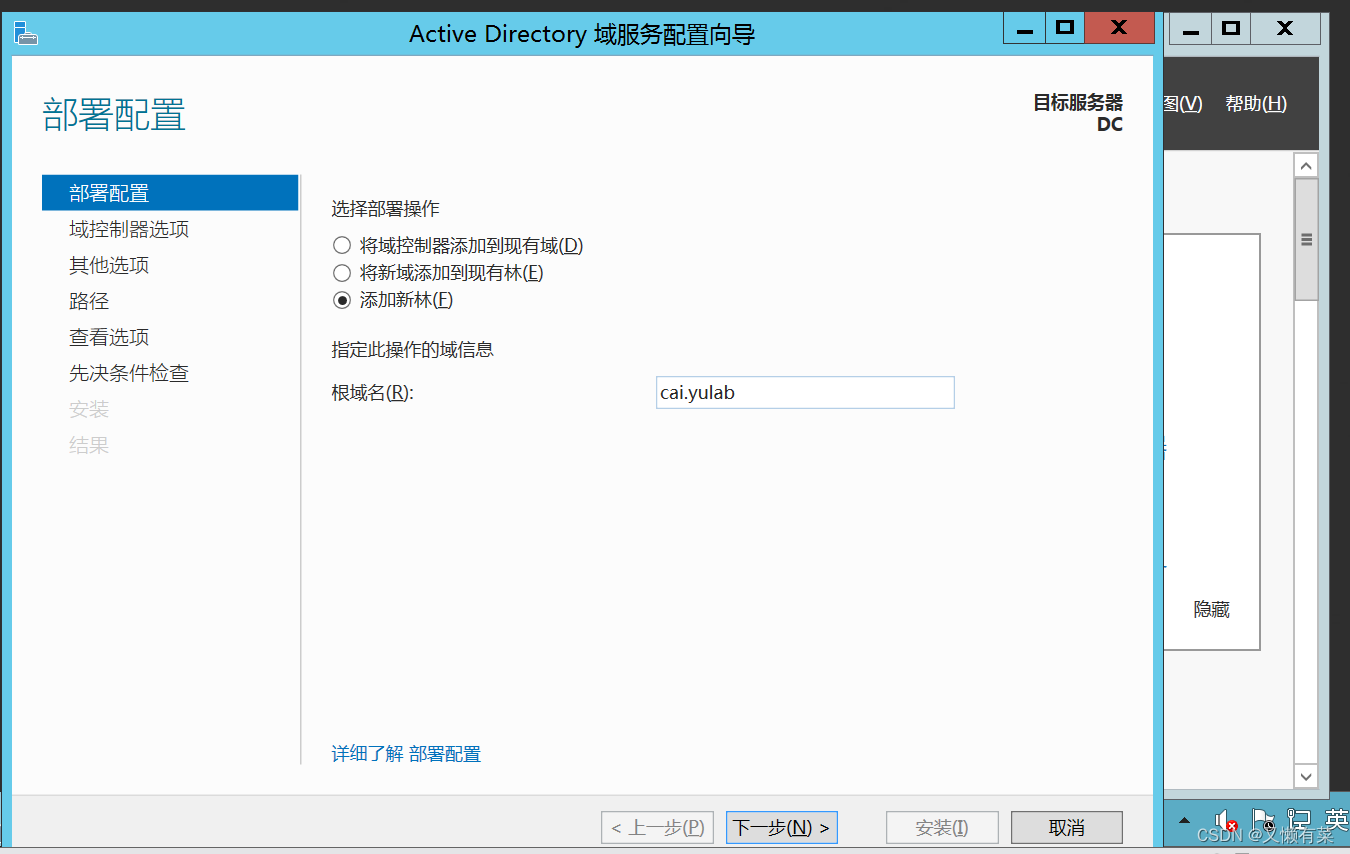
Once again into the “ Server Manager ”
Dashboard pull-down ,AD DS And DNS Have been configured
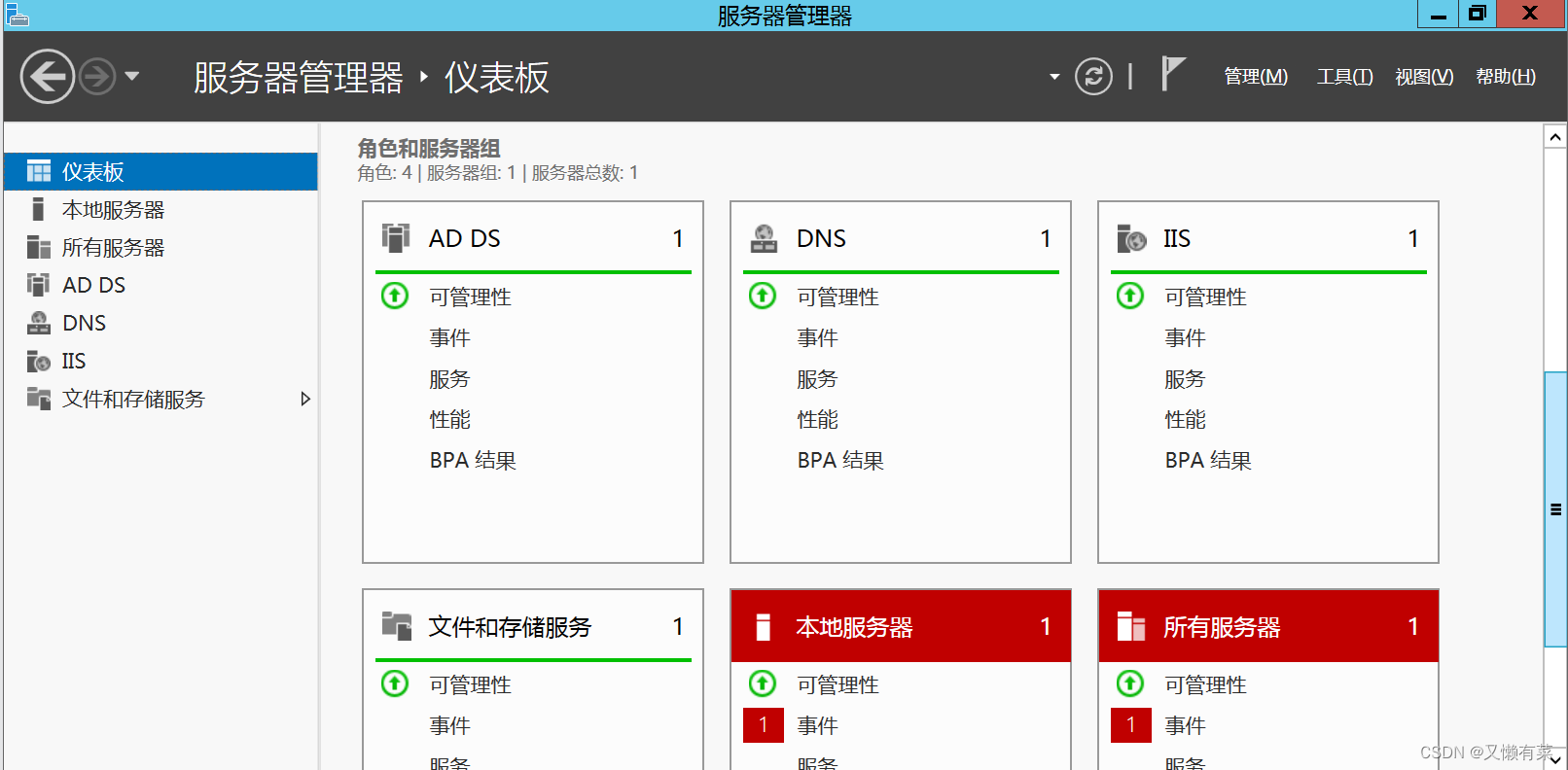
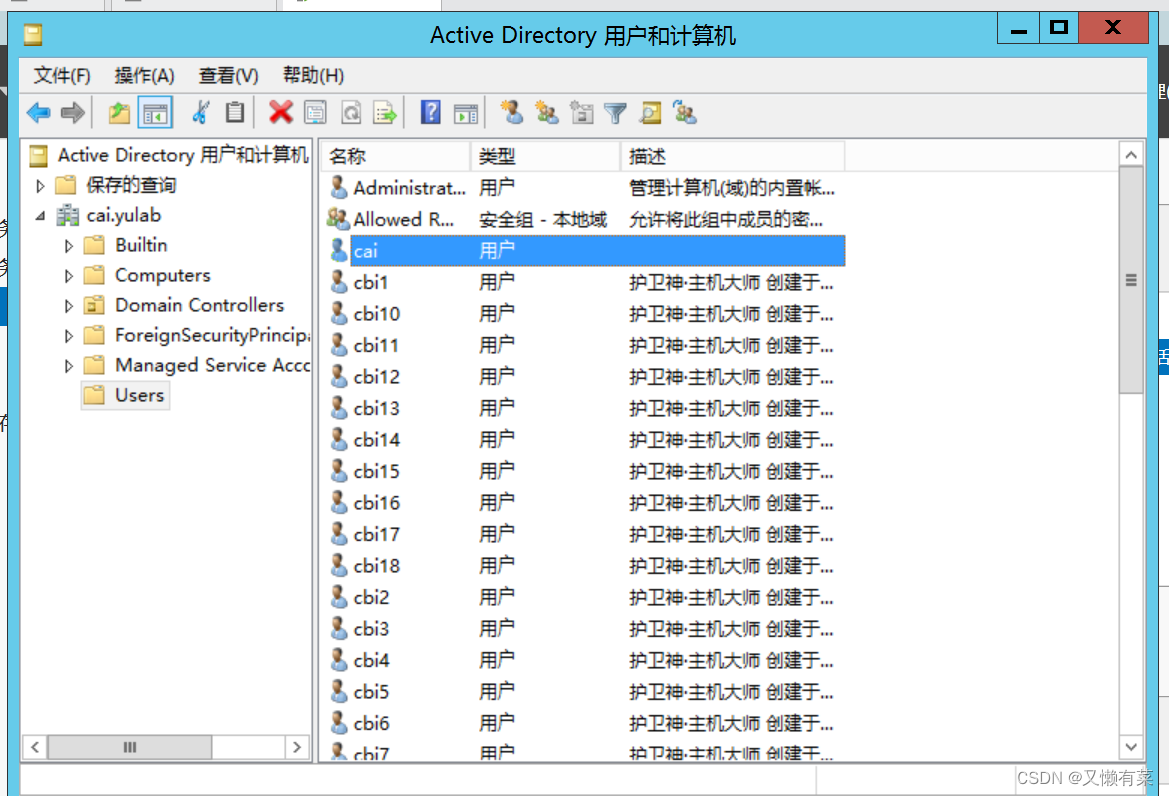
5) add to Active Directory user
The right choice “Active Directory Users and computers ”
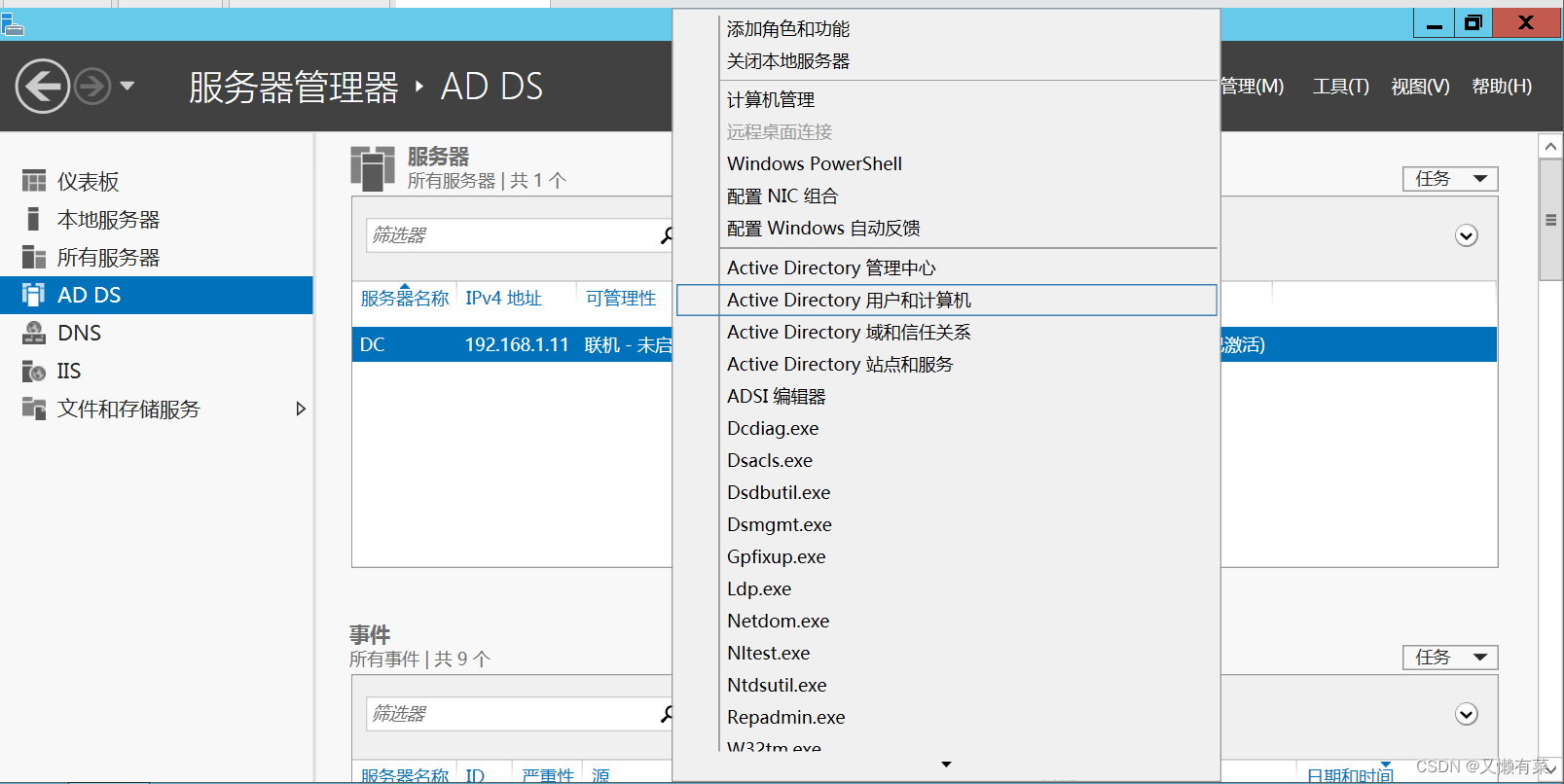
Right click ”Users“, add to “ new user ”, Set the password
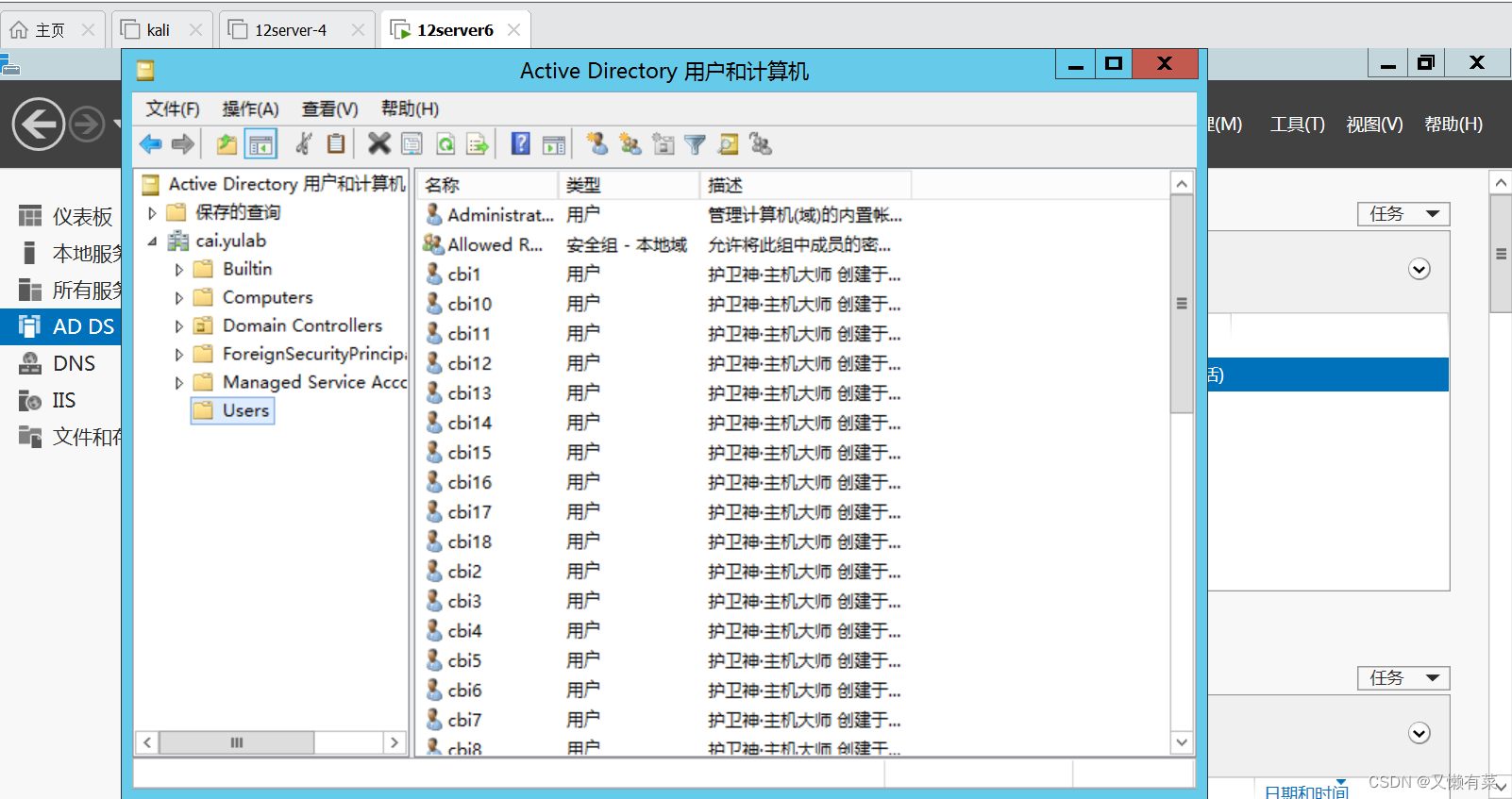
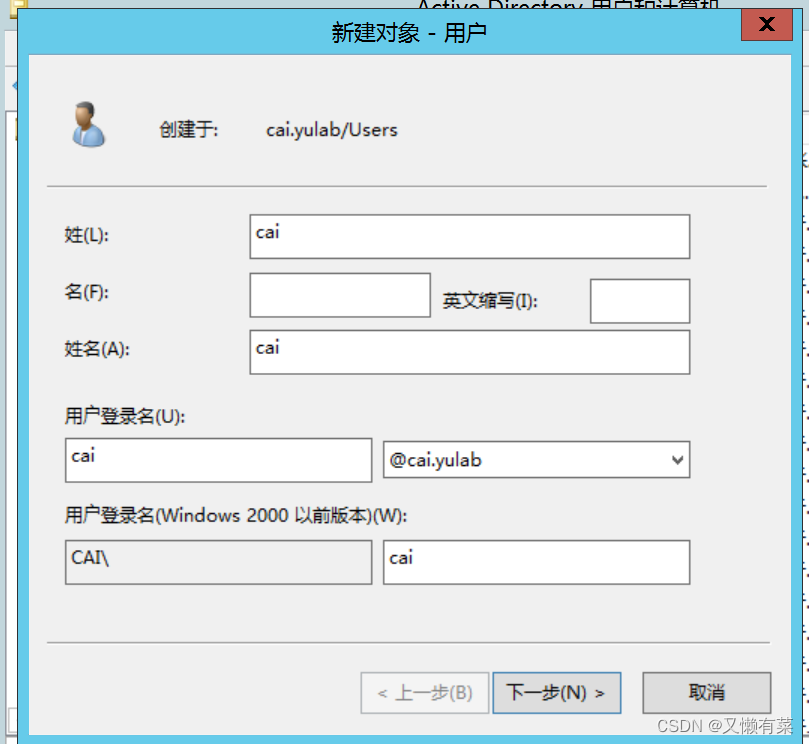
2.Win2008 Computer configuration
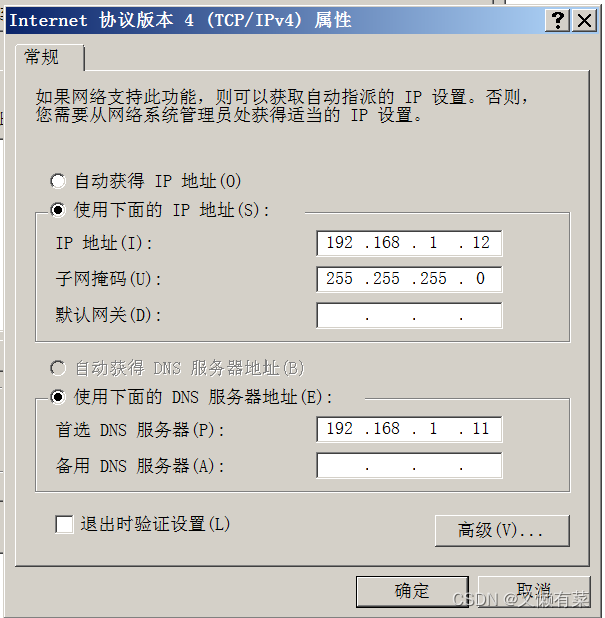
1) Set up DNS Resolve to server IP
IP The address and the server remain in the same network segment
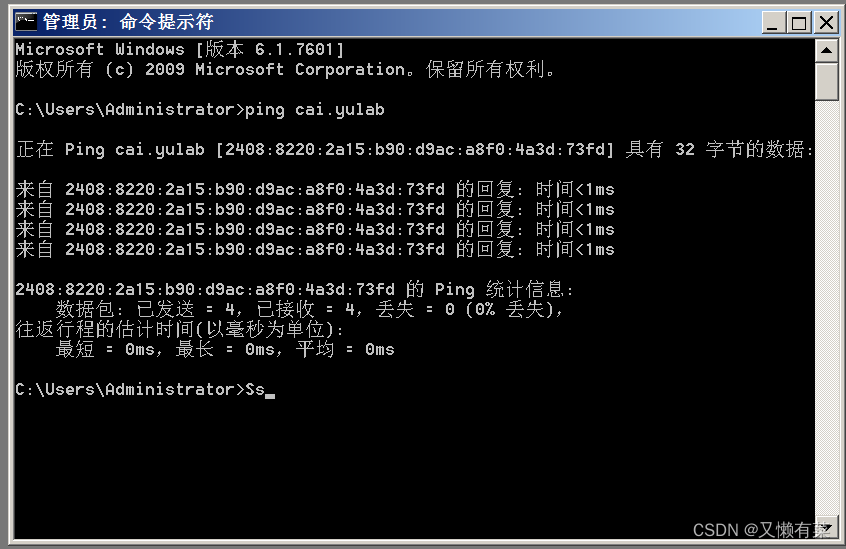
2) adopt cmd ping DNS See if the configuration is successful
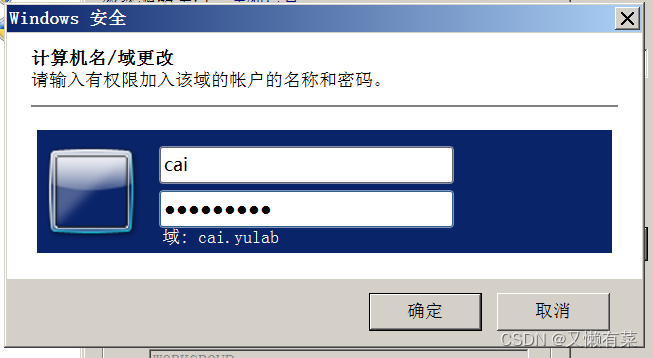
3) take win2008 Join in win2012 Created domain
Click on “ Domain ”, Click on “ determine ”
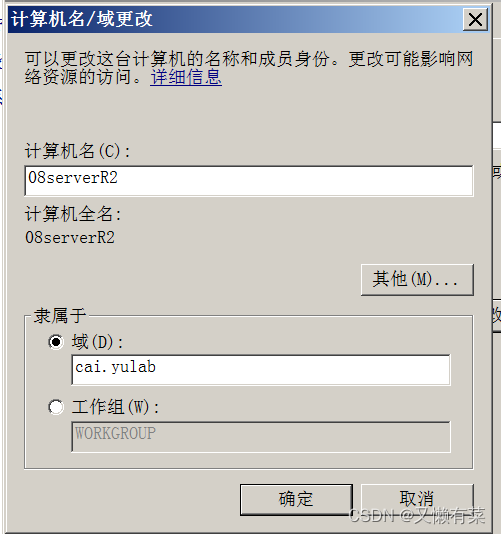
Enter the account and password set by the domain administrator
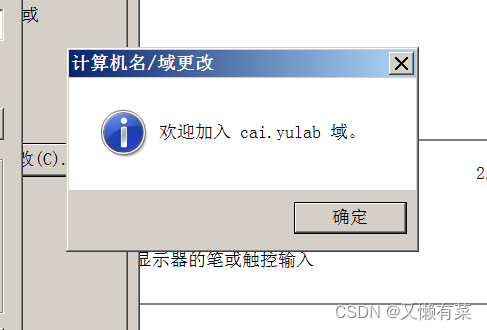
4) Successfully joined the domain cai.yulab
5) After the creation is successful, you can go to win7 Log in to the domain with the domain user account

Commonly known as intranet penetration testing , To a large extent, it is domain penetration testing , Build a domain test environment , stay windows Under the active directory environment of , Master its fabrication method and operation mechanism , It is of great help to the security maintenance of the intranet .
Don't understand private letters Lazy and talented
Details refer to :《 Intranet security attack and defense - Penetration test guide 》—— Xu Yan
边栏推荐
- [three paradigms of database] you can understand it at a glance
- A complete collection of papers on text recognition
- Mode 1 two-way serial communication is adopted between machine a and machine B, and the specific requirements are as follows: (1) the K1 key of machine a can control the ledi of machine B to turn on a
- Wechat applet
- 简单理解ES6的Promise
- 7-8 7104 约瑟夫问题(PTA程序设计)
- [MySQL table structure and integrity constraint modification (Alter)]
- 扑克牌游戏程序——人机对抗
- A piece of music composed by buzzer (Chengdu)
- Experiment 7 use of common classes (correction post)
猜你喜欢
Hackmyvm target series (6) -videoclub
撲克牌遊戲程序——人機對抗
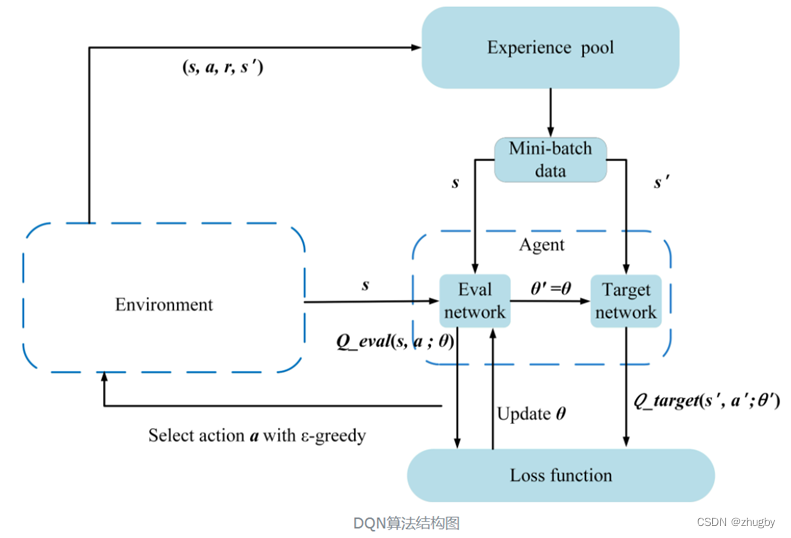
深度强化文献阅读系列(一):Courier routing and assignment for food delivery service using reinforcement learning

HackMyvm靶机系列(6)-videoclub
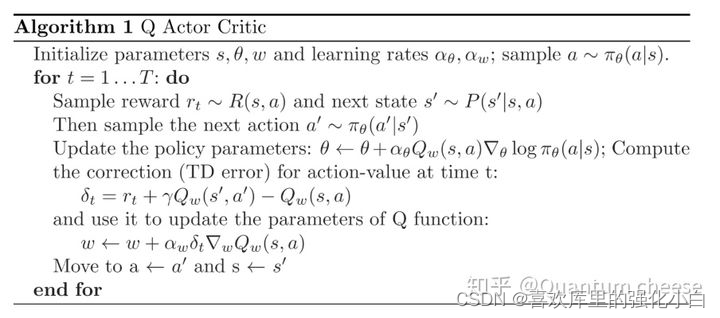
强化学习基础记录
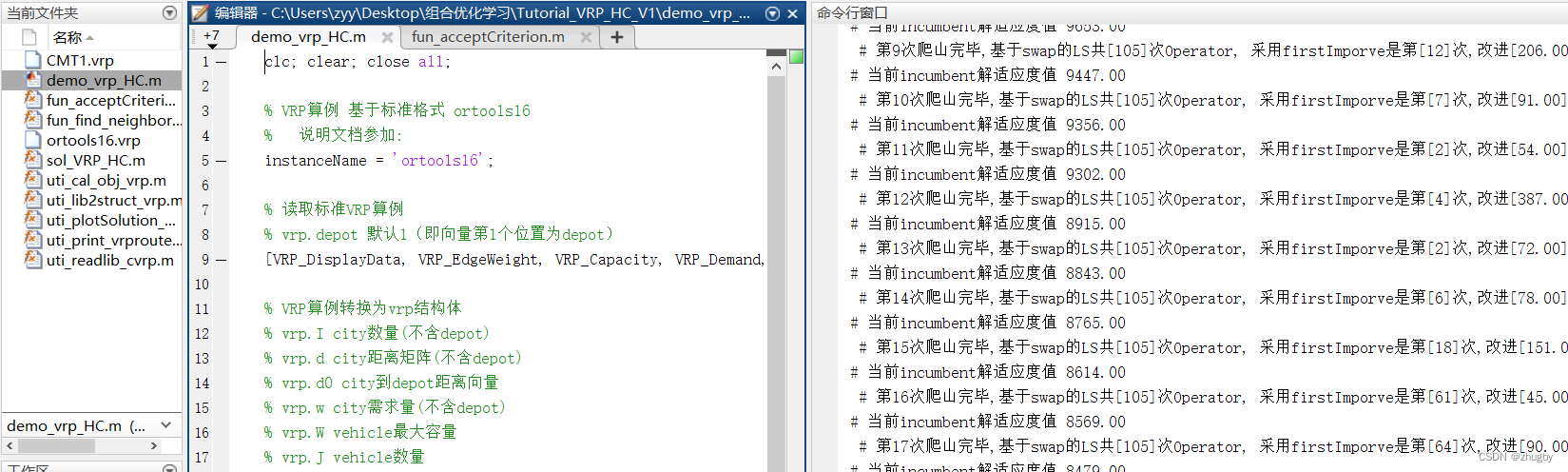
MATLAB打开.m文件乱码解决办法
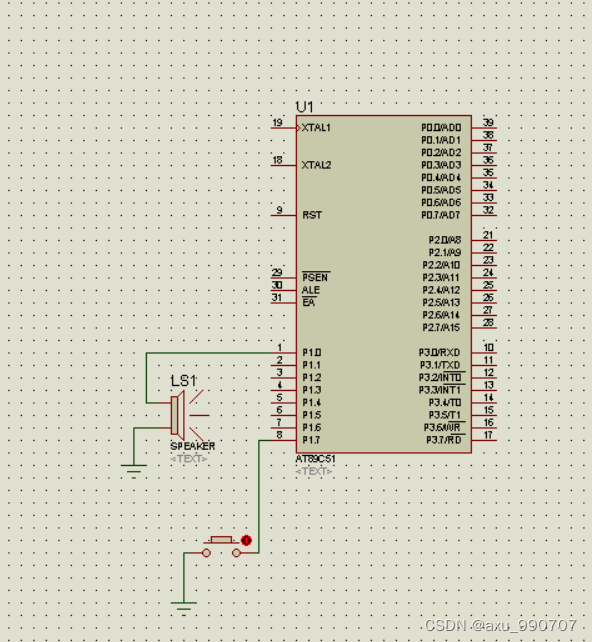
A piece of music composed by buzzer (Chengdu)
Package bedding of components
记一次猫舍由外到内的渗透撞库操作提取-flag

【黑马早报】上海市监局回应钟薛高烧不化;麦趣尔承认两批次纯牛奶不合格;微信内测一个手机可注册俩号;度小满回应存款变理财产品...
随机推荐
(original) make an electronic clock with LCD1602 display to display the current time on the LCD. The display format is "hour: minute: Second: second". There are four function keys K1 ~ K4, and the fun
Analysis of penetration test learning and actual combat stage
Miscellaneous talk on May 27
It's never too late to start. The tramp transformation programmer has an annual salary of more than 700000 yuan
Attach the simplified sample database to the SQLSERVER database instance
Which is more advantageous in short-term or long-term spot gold investment?
使用Spacedesk实现局域网内任意设备作为电脑拓展屏
Experiment 8 exception handling
7-8 7104 Joseph problem (PTA program design)
Experiment 7 use of common classes
Hackmyvm target series (3) -visions
Principles, advantages and disadvantages of two persistence mechanisms RDB and AOF of redis
【educoder数据库实验 索引】
Canvas foundation 1 - draw a straight line (easy to understand)
Yugu p1012 spelling +p1019 word Solitaire (string)
[MySQL database learning]
强化学习基础记录
实验七 常用类的使用
7-14 错误票据(PTA程序设计)
Callback function ----------- callback