当前位置:网站首页>Hackmyvm target series (5) -warez
Hackmyvm target series (5) -warez
2022-07-06 13:58:00 【The moon should know my meaning】
One 、 information gathering
Scan a wave of network segment first , Find the target .
nmap -sP 192.168.220.0/24
Use nmap Port scan , Found open 22,80,6800 Three ports .
nmap -sC -sV -T4 -p- -sT -A 192.168.220.128
Visit a wave http service , The page is as follows . I don't know what it is , But found keywords Aria2 WebUI, Search on Baidu , I found that this is a thing to download resources .

Take a look at the source code , Find the following keywords , Search for a wave of , See if there are any loopholes that can be exploited .

forehead ....., Out of line , There is really no one .

Come on , On gobuster Do a wave of directory scanning
gobuster dir -u "http://192.168.220.128/" -w directory-list-2.3-medium.txt -t 30 -x php,html,txt,7z,zip,bak,gzgive the result as follows , Found two txt file ,robots.txt,result.txt

robots.txt The contents are as follows

result.txt The contents are as follows , Um. .... This thing doesn't look very familiar ? Don't worry , Look at the following

I am here kali On the implementation ps -aux, Combined with the above figure , See? , The above should be the process list . And it turns out that aria2c In order to carolina Identity running .

Notice the following arrows , This is a download tool , guess dir Is the default directory we download .

Click Add , Click the use link to download . Can we use kali Generate the key , Then open a http service , This enables the target machine to download to /home/carolina Under the directory ?

Two 、 Exploit
Use kali Generate the key
ssh-keygenUse python To start a http service
python3 -m http.server 80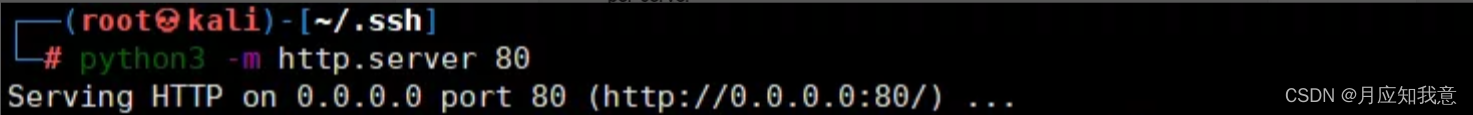
Add download links and save directories

Here's the picture , Download successful

ssh [email protected] -i id_rsaSuccessfully log in to the target machine with the private key , Get the first one flag

3、 ... and 、 Elevated privileges
The next step is to raise the permission to root 了 .
Let's see if there is sudo The abuse of ,??? No order ?

Forget it , First let's see if we can suid and sgid Raise your rights .
find / -perm -u=s -type f 2>/dev/nullPictured , Find a /usr/bin/rtorrent, See if you can raise your rights

After Baidu , Found that this can be used execute.throw Execute some system commands , But use rtorrent The premise is that you need a configuration file .rtorrent.rc, So I'll use to create this file first , Then enter the following , establish /root/.ssh Catalog , And copy the public key to the directory .
because rtorrent Command has suid jurisdiction , So when other users execute the command, they can get root jurisdiction , So create /roo/.ssh Catalog , And copy the public key .

stay kali Login with private key on root, Successfully get the second flag

边栏推荐
- 实验六 继承和多态
- Yugu p1012 spelling +p1019 word Solitaire (string)
- HackMyvm靶机系列(2)-warrior
- Safe driving skills on ice and snow roads
- 7-5 走楼梯升级版(PTA程序设计)
- 深度强化文献阅读系列(一):Courier routing and assignment for food delivery service using reinforcement learning
- Detailed explanation of redis' distributed lock principle
- 渗透测试学习与实战阶段分析
- Nuxtjs quick start (nuxt2)
- Strengthen basic learning records
猜你喜欢
Strengthen basic learning records

Mixlab unbounded community white paper officially released
![[面试时]——我如何讲清楚TCP实现可靠传输的机制](/img/d6/109042b77de2f3cfbf866b24e89a45.png)
[面试时]——我如何讲清楚TCP实现可靠传输的机制
7-5 staircase upgrade (PTA program design)
FAQs and answers to the imitation Niuke technology blog project (II)
![[during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission](/img/d6/109042b77de2f3cfbf866b24e89a45.png)
[during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission
优先队列PriorityQueue (大根堆/小根堆/TopK问题)
.Xmind文件如何上传金山文档共享在线编辑?

7-7 7003 组合锁(PTA程序设计)
仿牛客技术博客项目常见问题及解答(一)
随机推荐
TypeScript快速入门
Redis实现分布式锁原理详解
Read only error handling
Poker game program - man machine confrontation
强化学习基础记录
[experiment index of educator database]
FAQs and answers to the imitation Niuke technology blog project (II)
Difference and understanding between detected and non detected anomalies
[the Nine Yang Manual] 2021 Fudan University Applied Statistics real problem + analysis
【VMware异常问题】问题分析&解决办法
Safe driving skills on ice and snow roads
UGUI—Text
Experiment 8 exception handling
记一次猫舍由外到内的渗透撞库操作提取-flag
The difference between cookies and sessions
FAQs and answers to the imitation Niuke technology blog project (I)
Hackmyvm Target Series (3) - vues
Strengthen basic learning records
2022 Teddy cup data mining challenge question C idea and post game summary
【MySQL数据库的学习】