当前位置:网站首页>Analysis of penetration test learning and actual combat stage
Analysis of penetration test learning and actual combat stage
2022-07-06 13:48:00 【One call yyds】
Initial contact stage
Many little partners who have just come into contact with the penetration testing industry when you walk out of the gate of the College , Sometimes I feel very confused , I don't know the plan for the future after learning penetration testing .
According to my analysis for many years , Come up with a set of my own ideas and opinions .
The first step is , Of course, first learn the basic knowledge of penetration testing .
The second step , It belongs to the advanced stage , Constantly summarize what content of penetration testing in the process of the project is the most helpful to us through actual combat .
The third step , Constantly learn from the practical experience of our predecessors , Thus, it can be flexibly applied to actual combat .
Step four , Analyze simply , Technical expertise , Go back to the source .
Step five , Mining and analyzing the most primitive elements , Discover the latest 0day Loophole .
I think the cognitive level should also be constantly improved , The cognitive side represents your height , Knowledge represents the current height .
Learning penetration testing must have their own ideas , Just like setting goals , What to do first, then what to do , Don't mess up the rhythm .
Here is a share of my learning and practical experience .
I am a rookie with dreams ,
The first stage , Of course, it is to understand the market of the network security industry , And development trend 、 The work done .
The second stage , So I began to look for ways to learn , Method , Ask Baidu if you don't understand , Baidu has also given me many methods of predecessors . So we choose the learning method that suits us to start learning .
I just started to learn PHP programing language , Secondly, I revisited MySQL database , Then learn how to collect information , Then learn about loopholes , Basic loopholes .
The third stage , It is to apply knowledge to actual combat , This stage is a small breakthrough stage , At first, I was digging some unprotected sites , Put the knowledge learned on the real website , So I chose src, Digging holes in actual combat is a stage of the formation of self thinking , Every penetration testing engineer should have his own ideas and methods of vulnerability mining , Bring everyone together , What is digested is what belongs to you .
Goals matter , In the actual combat stage, I plan to be on the list at least , So I studied some methods of vulnerability fast mining .
The fourth stage , It is the extension stage , Continue to expand the scope of our possible attacks , Or the way of defense .
Whatever it is , It is helpful for our attack , This will let us know how the target defends , In order to make better use of countermeasures . To achieve our goal of attacking target vulnerabilities .
The fifth stage , Analyze the origin of the vulnerability , Learn reverse thinking , No killing thought , Penetration testing technology , Programming technology , Network knowledge , Development integration and other knowledge , Think about what kind of problems it will produce , Try to explore new bug.
Maybe the idea is like this , After that, I will continue to publish my technical articles , Welcome to Europe !
边栏推荐
- 1. First knowledge of C language (1)
- The latest tank battle 2022 - full development notes-3
- 简单理解ES6的Promise
- 7-1 输出2到n之间的全部素数(PTA程序设计)
- 7. Relationship between array, pointer and array
- 3. Number guessing game
- Miscellaneous talk on May 14
- Wei Pai: the product is applauded, but why is the sales volume still frustrated
- 3.猜数字游戏
- 稻 城 亚 丁
猜你喜欢
Service ability of Hongmeng harmonyos learning notes to realize cross end communication
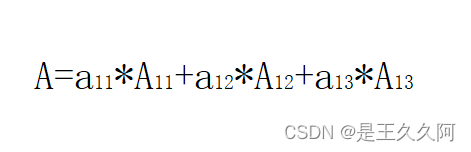
3. C language uses algebraic cofactor to calculate determinant

QT meta object qmetaobject indexofslot and other functions to obtain class methods attention
优先队列PriorityQueue (大根堆/小根堆/TopK问题)
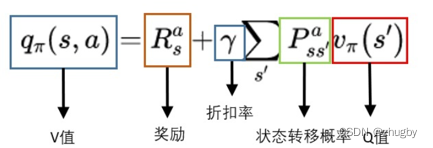
强化学习系列(一):基本原理和概念
![[during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission](/img/d6/109042b77de2f3cfbf866b24e89a45.png)
[during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission
hashCode()与equals()之间的关系
4. Branch statements and loop statements
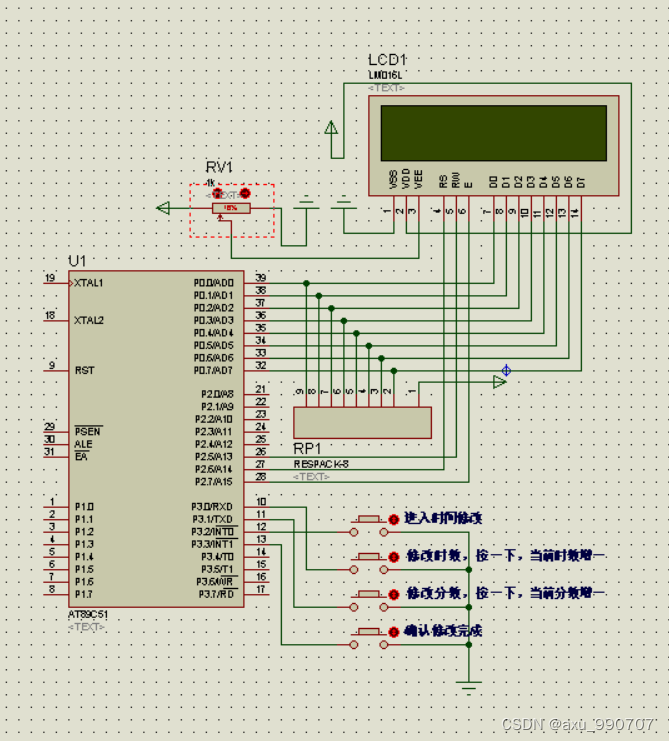
(原创)制作一个采用 LCD1602 显示的电子钟,在 LCD 上显示当前的时间。显示格式为“时时:分分:秒秒”。设有 4 个功能键k1~k4,功能如下:(1)k1——进入时间修改。
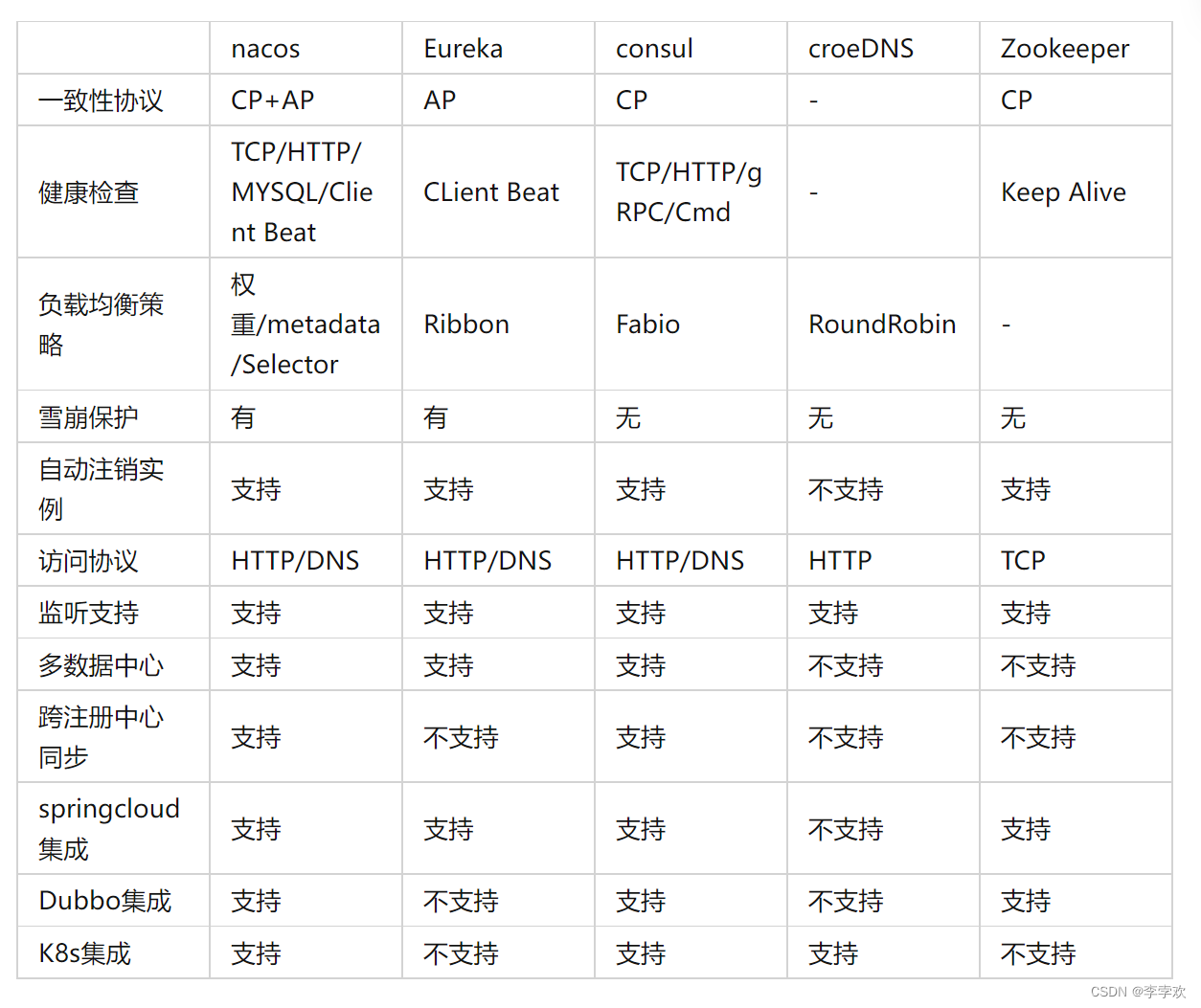
自定义RPC项目——常见问题及详解(注册中心)
随机推荐
[modern Chinese history] Chapter 9 test
ABA问题遇到过吗,详细说以下,如何避免ABA问题
Caching mechanism of leveldb
[hand tearing code] single case mode and producer / consumer mode
Floating point comparison, CMP, tabulation ideas
【手撕代码】单例模式及生产者/消费者模式
2. Preliminary exercises of C language (2)
Leetcode.3 无重复字符的最长子串——超过100%的解法
【黑马早报】上海市监局回应钟薛高烧不化;麦趣尔承认两批次纯牛奶不合格;微信内测一个手机可注册俩号;度小满回应存款变理财产品...
2022 Teddy cup data mining challenge question C idea and post game summary
Zatan 0516
[the Nine Yang Manual] 2020 Fudan University Applied Statistics real problem + analysis
JS interview questions (I)
[the Nine Yang Manual] 2017 Fudan University Applied Statistics real problem + analysis
js判断对象是否是数组的几种方式
优先队列PriorityQueue (大根堆/小根堆/TopK问题)
Miscellaneous talk on May 27
扑克牌游戏程序——人机对抗
【九阳神功】2021复旦大学应用统计真题+解析
仿牛客技术博客项目常见问题及解答(一)