当前位置:网站首页>Experiment 9 input and output stream (excerpt)
Experiment 9 input and output stream (excerpt)
2022-07-06 13:55:00 【Wen Wen likes Guo Zia】
Experiment 9 I / O stream
The experiment purpose
1. understand Java In the technical system “ flow ” The concept of .
2. master System.in and System.out The basic use method
3. Master the common classes and usage methods of byte stream and character stream .
4. master Java The basic operation of the program on the file .
Experimental hours 4 Class hours
Experimental content
1. Write programs using System.in Object's read() Method read keyboard input , When the program is running , First, ask the number of data you need to input , Then input the integer of the specified number in turn , After input , Output the sum of all input integers .
package code91;
import java.io.BufferedReader; // Character input stream with buffer function
import java.io.IOException;
import java.io.InputStreamReader; // Byte stream to character stream converted stream
public class code91 {
public static void main(String[] args)throws NumberFormatException,Exception {
// TODO Automatically generated method stubs
int a[]=new int[512]; // Create an input stream that receives keyboard input data
int sum=0;
InputStreamReader c = new InputStreamReader(System.in); // Put the input stream into the buffer stream
BufferedReader d = new BufferedReader(c);
System.out.println(" Please enter the total number of numbers :");
int n=Integer.parseInt( d.readLine()); // Convert to basic data type int
System.out.println(" These numbers are :");
for(int i=0;i<n;i++) {
int b=Integer.parseInt(d.readLine());
a[i]=b;
sum+=a[i];
}
System.out.println(" The sum of all input numbers is :"+sum);
}
}
2. On computer D Create a disk named FileList Text file for , take D Save the names of all files and folders on the disk to this file .
package code92;
import java.io.File;
import java.io.FileWriter;
public class code92 {
public static void main(String[] args) {
// TODO Automatically generated method stubs
try {
File f=new File("D:\\FileList");
if(!f.exists()){
f.createNewFile(); // Create a text file
}
else {
System.out.println(" file already exist ");
}
File file=new File("D:\\");
File[] fs=file.listFiles();
FileWriter out = new FileWriter(f);
for(File fs1 : fs) {
out.write(fs1.getPath()+'\r'+'\n');
}
out.close();
}catch(Exception e) {
e.printStackTrace();
}
}
}
5. Important files usually need to be encrypted , Please write a program to encrypt text files , The password table is as follows , If the plaintext is in capital letters, the ciphertext is also in capital letters corresponding to the password table , If the plaintext is in lowercase letters, the ciphertext is also in lowercase letters corresponding to the password table .
Plaintext | A | B | C | D | E | F | G | H | I | J | K | L | M |
Ciphertext | T | O | I | A | N | D | E | G | H | Z | B | K | F |
Plaintext | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
Ciphertext | J | M | C | L | P | Y | V | X | Q | R | W | U | S |
package code95;
import java.io.File;
import java.io.FileReader; // File character input stream
import java.io.FileWriter; // File character output stream
import java.util.Scanner;
public class code95 {
public static void main(String[] args) throws Exception {
char reality[] = { 'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P', 'Q', 'R',
'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z' };
char fake[] = { 'T', 'O', 'I', 'A', 'N', 'D', 'E', 'G', 'H', 'Z', 'B', 'K', 'F', 'J', 'M', 'C', 'L', 'P', 'Y',
'V', 'X', 'Q', 'R', 'W', 'U', 'S' }; // Create two arrays , Fill in letters and encrypted ciphertext respectively
FileWriter fw = new FileWriter(new File("D:\\FileList"));
FileReader fr = new FileReader(new File("D:\\FileList")); // Yes, the experiment 2 Encrypt the file created in
Scanner in = new Scanner(System.in);
String str = in.nextLine();
char[] a = str.toCharArray(); // Convert string to character array
for (int n = 0; n < a.length; n++) {
for (int i = 0; i < 26; i++) {
if (a[n] == reality[i]) { // Encrypted letter
a[n] = fake[i];
break;
} else if (a[n] <= 'z' && a[n] >= 'a') { // Conversion of lowercase letters to uppercase letters
if (reality[i] == (char) (a[n] - 32)) { // Cast
a[n] = (char) (fake[i] + 32); // Convert upper ciphertext to lower case
break;
}
}
}
}
fw.write(a);
in.close();
fw.close();
fr.close();
}
}边栏推荐
- String abc = new String(“abc“),到底创建了几个对象
- Canvas foundation 2 - arc - draw arc
- Implementation of count (*) in MySQL
- [during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission
- 【手撕代码】单例模式及生产者/消费者模式
- The latest tank battle 2022 full development notes-1
- About the parental delegation mechanism and the process of class loading
- 力扣152题乘数最大子数组
- 7-4 散列表查找(PTA程序设计)
- 7-7 7003 组合锁(PTA程序设计)
猜你喜欢
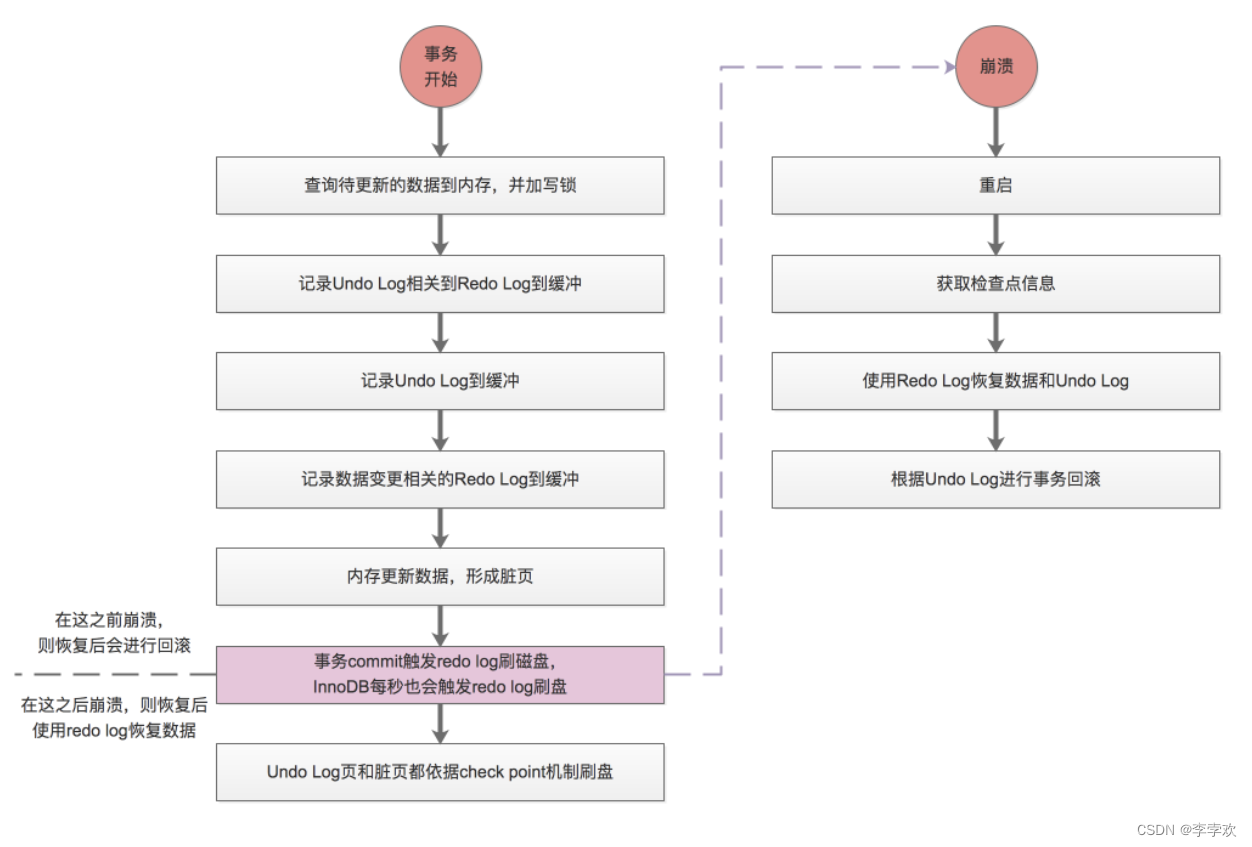
A comprehensive summary of MySQL transactions and implementation principles, and no longer have to worry about interviews
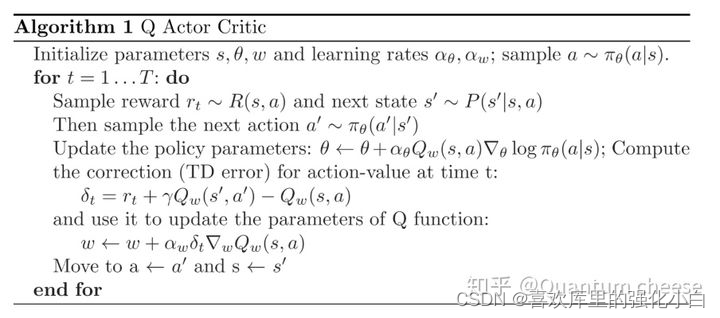
强化学习基础记录
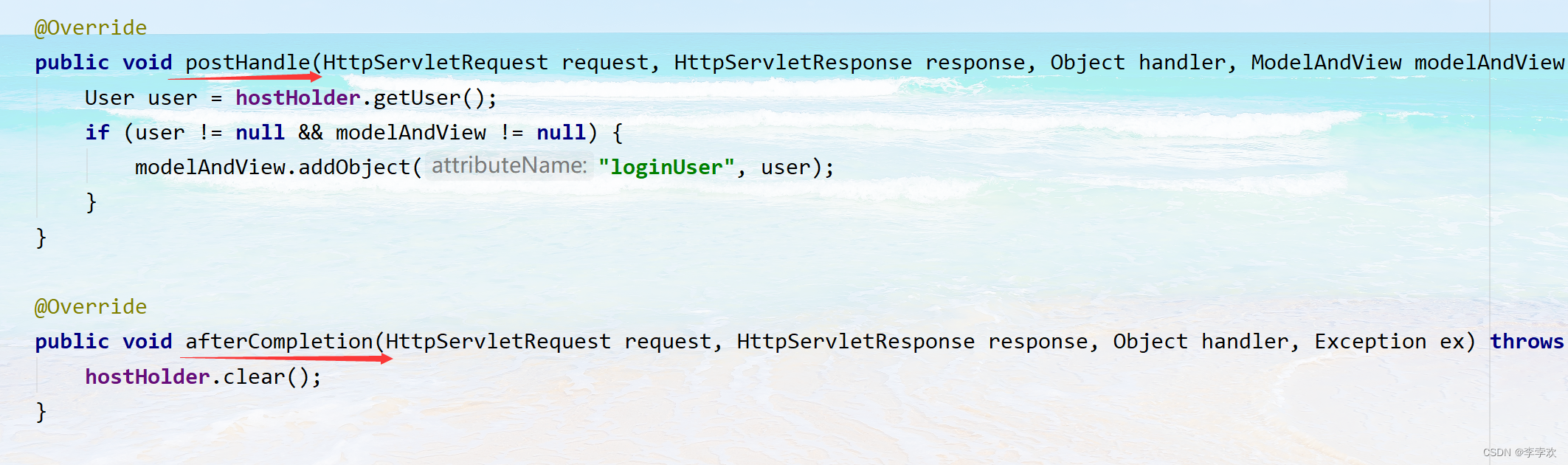
FAQs and answers to the imitation Niuke technology blog project (I)
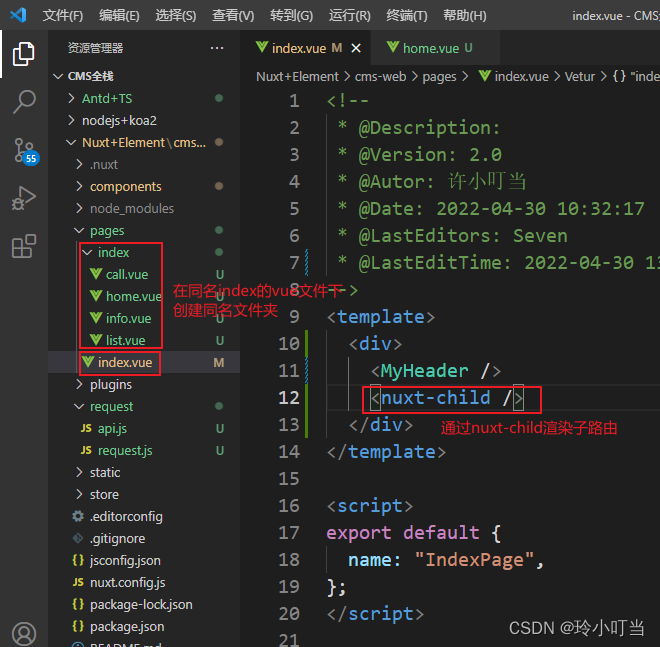
Nuxtjs快速上手(Nuxt2)
Meituan dynamic thread pool practice ideas, open source

仿牛客技术博客项目常见问题及解答(一)
Leetcode.3 无重复字符的最长子串——超过100%的解法
甲、乙机之间采用方式 1 双向串行通信,具体要求如下: (1)甲机的 k1 按键可通过串行口控制乙机的 LEDI 点亮、LED2 灭,甲机的 k2 按键控制 乙机的 LED1
7-5 走楼梯升级版(PTA程序设计)
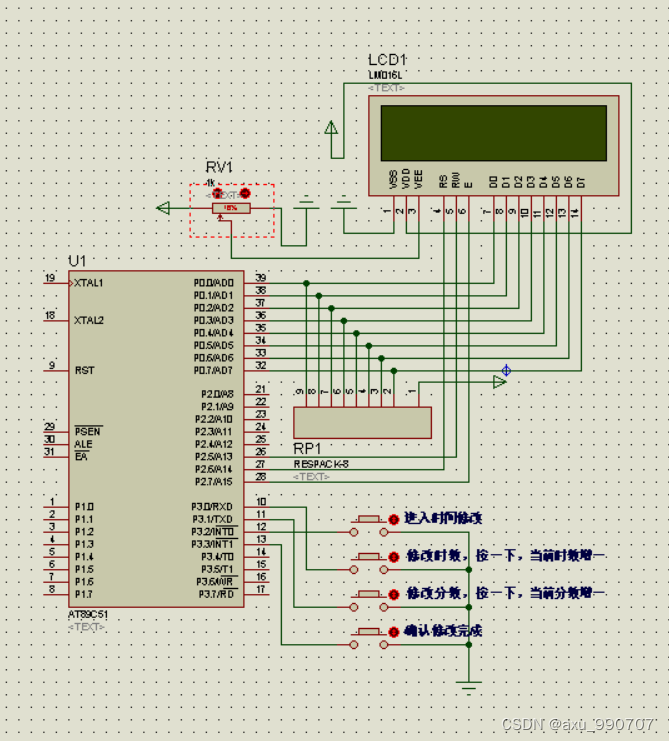
(原创)制作一个采用 LCD1602 显示的电子钟,在 LCD 上显示当前的时间。显示格式为“时时:分分:秒秒”。设有 4 个功能键k1~k4,功能如下:(1)k1——进入时间修改。
随机推荐
7-6 矩阵的局部极小值(PTA程序设计)
Matlab opens M file garbled solution
【educoder数据库实验 索引】
【黑马早报】上海市监局回应钟薛高烧不化;麦趣尔承认两批次纯牛奶不合格;微信内测一个手机可注册俩号;度小满回应存款变理财产品...
1143_ SiCp learning notes_ Tree recursion
Get started with typescript
强化学习系列(一):基本原理和概念
关于双亲委派机制和类加载的过程
Record a penetration of the cat shed from outside to inside. Library operation extraction flag
C language Getting Started Guide
为什么要使用Redis
A piece of music composed by buzzer (Chengdu)
SRC挖掘思路及方法
Inaki Ading
实验六 继承和多态
Write a program to simulate the traffic lights in real life.
受检异常和非受检异常的区别和理解
Analysis of penetration test learning and actual combat stage
FAQs and answers to the imitation Niuke technology blog project (I)
【VMware异常问题】问题分析&解决办法