当前位置:网站首页>What is SQL injection
What is SQL injection
2022-07-02 08:27:00 【Defeat of Fujiwara Qianhua】
What is? sql Inject ?
Since you will read this article , It shows that you are the same as me when writing this article , It's a safe little white . No matter what reason you want to know “ What is? sql Inject ”, I hope this article will give you some harvest as much as possible .
Two popular concepts
SQL Injection means web The application does not filter or judge the legitimacy of the data entered by the user , The parameter passed in by the front end is that the attacker can control , And the parameters are brought into the query of the database , An attacker can construct a malicious sql Statement to implement Responsibility for database Intentional operation .
Or to say
Through the sql Command insert into Web Submit the form or enter the query string of the domain name or page request , Finally, cheat the server to execute malicious SQL command
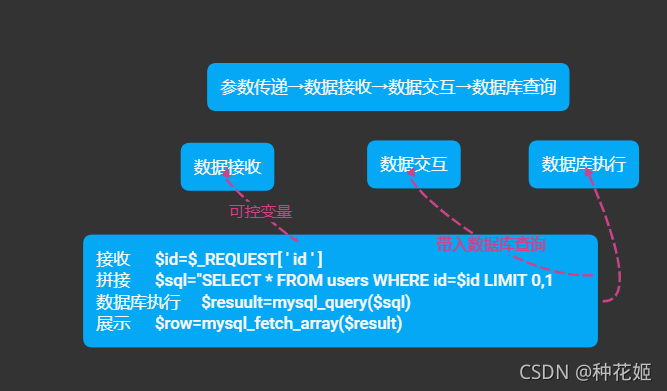
If you have some basic knowledge of development , It will be easy to understand SQL The concept of injection , Broadly speaking , When you dynamically request the server , There will be a process of data interaction . Above, PHP link MySQL Source code , Can be any SQL Inject into the shooting range to check . in general ,SQL Injection is a controllable variable , Brought into the database for query .(2021.9.30 Add )
When you browse some web pages , They mostly provide a query function , For example, you open a video website , You can search “xxxx”, To get the video you want . Something like this happened during this period : You press enter , A with the keywords you enter HTTP The request is sent to the server , Business logic layer Web The server parses your request through the script engine , Dynamically construct sql sentence , And ask for DBMS, perform SQL sentence .DBMS return SQL The execution result is given to Web Server,Web Server Encapsulate the page into HTML Format response to browser , Browser parsing HTML, Present the content to you .
To understand the above paragraph , You need a little network 、 Knowledge of database and middleware . Now? , You just need to package the knowledge you don't understand into a black box , This black box provides some required functions .
that ,sql Inject , It happens in dynamic construction SQL sentence , And return the execution result to Web Server This process of . Because the data entered by the user is not filtered , The maliciously constructed parameters are brought into DBMS The query , Realize the malicious operation of the database .
SQL How does injection happen ?
If you understand the above words , You would say , Oh , This is it. SQL Injection . When I think about it , You still find that you don't understand “ What is? SQL Inject ”. Next , You may need a little knowledge of databases , especially MySQL.
MySQL There is a system library information_schema, It stores all the relevant information of the database .
This library can be used for a complete injection . The following is the general process :
Guess the database :
select schema_name frominformation_schemata
select database()
Guess the data table of a library select table_name from information_schema.tables where table_schema=‘xxxx’
Guess all the columns of a table select column_name from information_schema.columns where table_name=‘xxxxx’
Get the contents of a column
select **** from *****
To begin our SQL Inject :
You'd better try it in the database you downloaded .
Suppose there is a student table , You want to check the student whose name is Zhang San , You would write like this :
select * from student where name = ' Zhang San ';
Maybe in the front-end interface , You just entered a “ Zhang San “, There is a variable for the browser to get your input $input in , Pass this variable to the script engine , The script engine does not do any processing , Directly construct a line with your input value dynamically SQL sentence , such as :
$sql = "select * from student where name = 'input'";
$result = mysql_query($sql);
The above code is PHP Language operation on Database , I don't know why I can do this ? You can learn ODBC or JDBC, Now? , It's just a black box . adopt mysql_query() This function ,$sql The statement of variable is passed MySQL Database execution . Everything is so perfect . however , If you type in
Zhang San ' // Just one more single quotation mark
Then the above statement will become
$sql = "select * from student where name = ' Zhang San ''";
It is equivalent to the following query in the database :
select * from student where name = ' Zhang San '';
The single quotation mark you entered , Close the single quotation mark of the previous original statement , There are more single quotation marks behind it , An error at this time .
What's the use of that ? This is so useful . Because you can close the previous clause , Then you can splice all the legal statements constructed by yourself , And add one at the end “ --+” Note the complex content behind , such as
select * from student where name = ' Zhang San ' union select 1,2,x,x --+
Come down here , You may really understand “ What is? SQL Inject ”
边栏推荐
- Principes fondamentaux de la théorie musicale (brève introduction)
- Carla-UE4Editor导入RoadRunner地图文件(保姆级教程)
- Media query usage
- Carsim 学习心得-粗略翻译1
- Simple implementation scheme of transcoding and streaming (I)
- On the back door of deep learning model
- Several methods of image enhancement and matlab code
- STM32 new project (refer to punctual atom)
- Carsim-路面3D形状文件参数介绍
- Matlab other
猜你喜欢
Carsim-问题Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
OpenCV3 6.2 低通滤波器的使用
Array and string processing, common status codes, differences between PHP and JS (JS)
How to back up the configuration before the idea when reinstalling the idea

Fundamentals of music theory (brief introduction)

When a custom exception encounters reflection

Carsim-实时仿真的动画同步问题
Opencv3 6.3 reduced pixel sampling with filters

CarSim problem failed to start solver: path_ ID_ OBJ(X) was set to Y; no corresponding value of XXXXX?
On the back door of deep learning model
随机推荐
[untitled]
HCIA—应用层
类和对象(类和类的实例化,this,static关键字,封装)
CarSim problem failed to start solver: path_ ID_ OBJ(X) was set to Y; no corresponding value of XXXXX?
Wang extracurricular words
SQLyog远程连接centos7系统下的MySQL数据库
Carla-ue4editor import Roadrunner map file (nanny level tutorial)
Comparison between setTimeout and requestanimationframe (page refresh)
Carsim-问题Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Causes of laptop jam
Global and Chinese market of tillage finishing machines 2022-2028: Research Report on technology, participants, trends, market size and share
Use the kaggle training model and download your own training model
Real world anti sample attack against semantic segmentation
Force buckle method summary: sliding window
樂理基礎(簡述)
Erase method in string
ARP及ARP欺骗
C语言实现XML生成解析库(XML扩展)
Method recursion (Fibonacci sequence, frog jumping steps, tower of Hanoi problem)
使用Matplotlib绘制图表初步