当前位置:网站首页>Remember an experience of ECS being blown up by passwords - closing a small black house, changing passwords, and changing ports
Remember an experience of ECS being blown up by passwords - closing a small black house, changing passwords, and changing ports
2022-07-06 12:17:00 【A pole】
Remember the experience of a server being blown up
List of articles
I see this warning when I log in , I realized that my server might be exploding
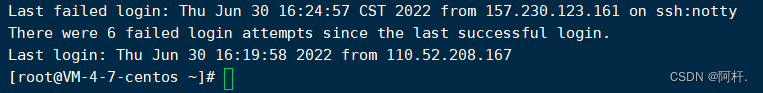
Check login
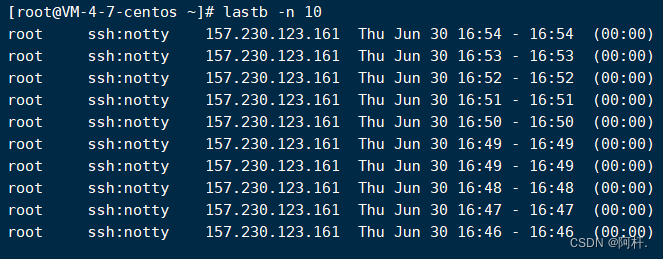
So I immediately passed the order lastb The login failure record was queried , The output shocked me , About fiveorsix seconds ? Maybe more , Login record display , From this month's 1 The start , Now I write this blog , For a whole month , Someone has been trying to log in to my server ...
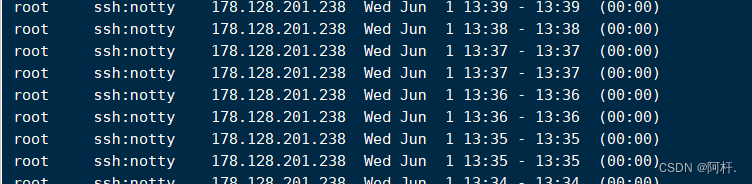
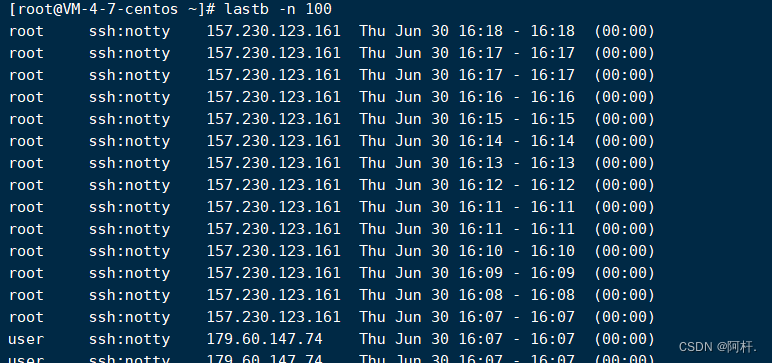
these ip They are all from abroad , And the attacker is still trying to explode , It means that he may not have logged in successfully , So I input last Instructions , Check the successful login ip:
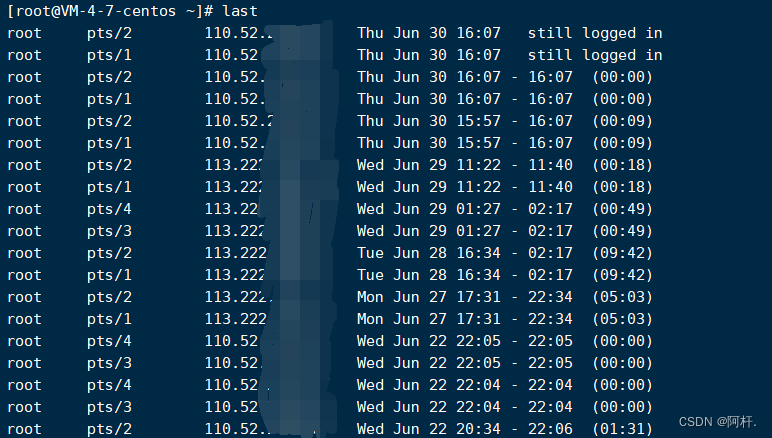
Then I put these ip Checked it all , No abnormalities found ip( Here are all mine ip, I'll code it ).
Here we are , I can be sure for the time being , The attacker has not logged on to my server , Then don't worry , Let's start with , Make a note by the way .
Shut up the black house
First of all, we can define the current ip Deal with small black houses .
I use Tencent cloud server ( The operation of Alibaba cloud is similar ), I immediately went to the backstage of Tencent cloud to have a look , It is found that no abnormality is detected , The abnormal login here is also my own .
In password cracking, nothing is detected directly , I don't know if it's because I modified ssh The reason for the port ...
Query the currently exploding ip
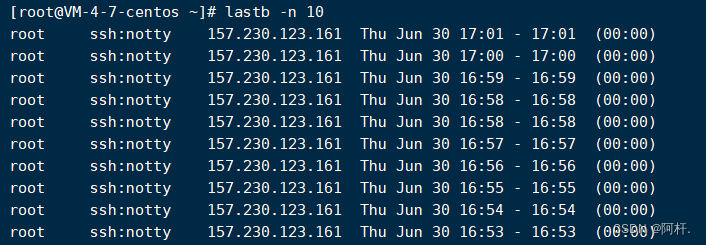
First, through lastb -n 10 To check the latest 10 Records of login failures :
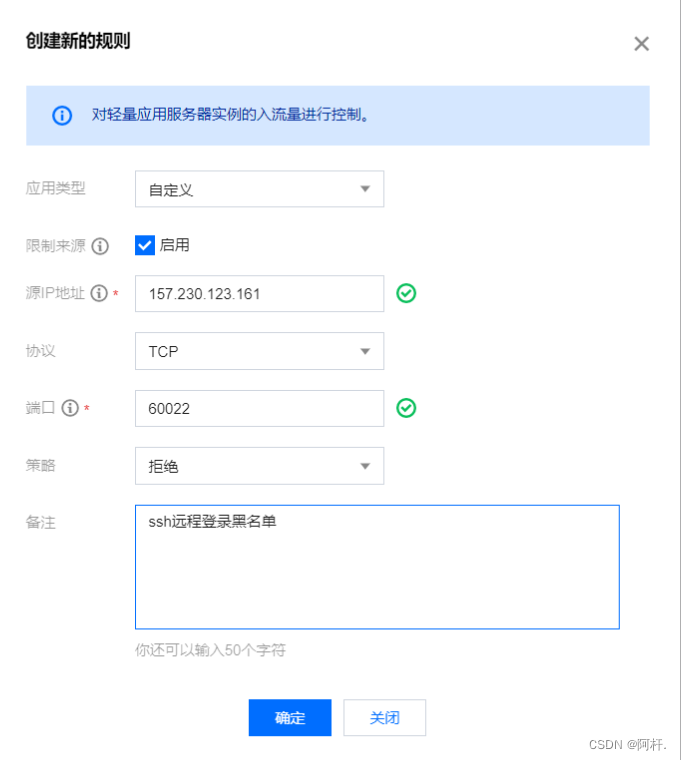
Then you can directly check the ip Blacklist processing .
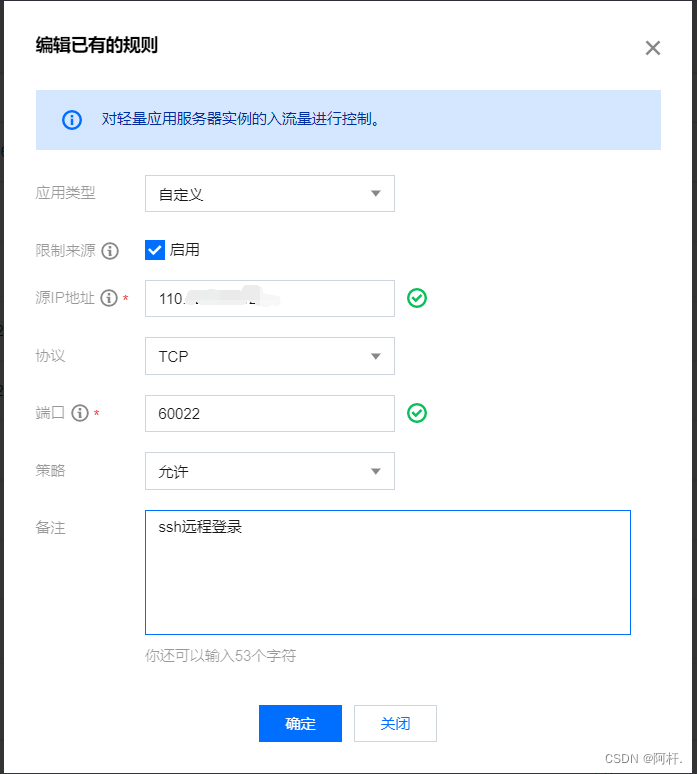
Add a firewall rule , Enable restricted sources , The address is the address that needs to be hacked , Then the strategy is to reject , The port number is the login port number ( The default is 22, I modified it to 60022 Of ). Click ok .
Wait a few minutes , Then check the login record , Find out what to do ip The login record of has stopped ( The current time is 17:04, Stopped. 3 minute ).
New problems and solutions
So the current login explosion is blocked , But the attacker is obviously not the only one ip, Because there are many in the previous login records ip 了 , Then I can't add another one to it ...
It's a matter of time , Just finished writing the above words , Check the login record again , Sure enough, another one ip Here we go again ... Man, you're really tortured ...

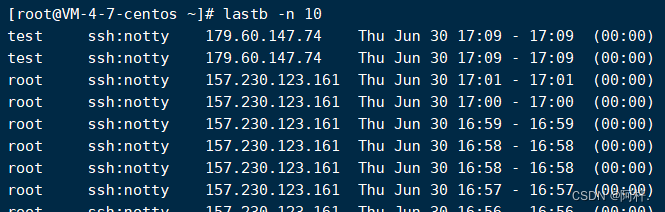
This ip It's also from abroad , Several previous attempts to log in ip They are all foreign , So in that case , I directly put foreign ip Wouldn't it be good if it were all Limited ? Then I decisively went to Baidu to check the domestic ip Address range , Mama ah , This is a little too much , And it's messy .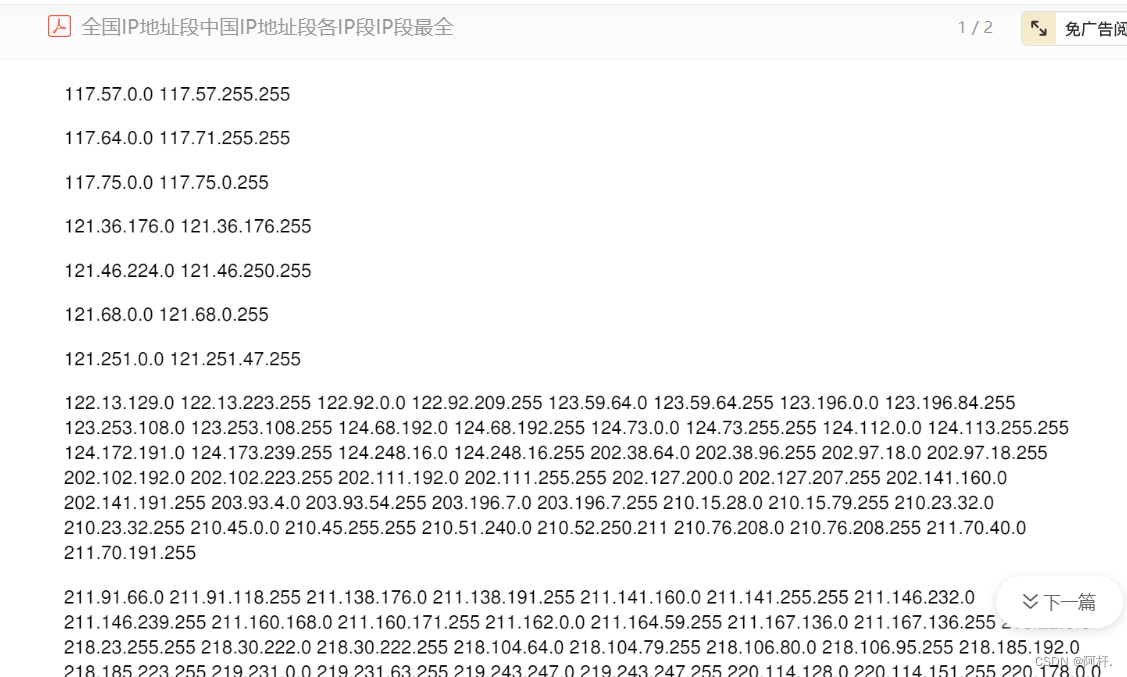
Put it another way , Actually, remote login , I only need to give myself a few that I may use ip Just use it , So in that case , I can directly limit it to only what I use ip Just allow access .
So I went to check my ip:
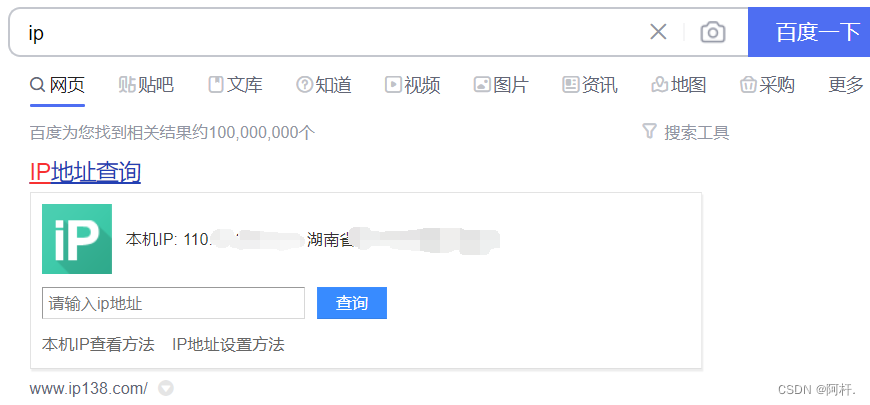
Put this ip Designed to allow remote login port access ip, And delete the rules of other remote login ports :
Enhance security
Although the above operations can basically ensure that others can no longer try to blast login , But I'm still not sure , So I still want to do some other measures .
Change Password
Changing the password is the simplest , Input instruction passwd , The default is to change the password of the current user , If input passwd tom, It's modification tom User's password .
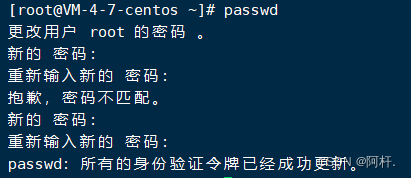
It should be noted that , When you enter the password , It will not display any characters , even * It doesn't show , It's easy for novices to think that they didn't enter , It's not . After entering twice, you can change it successfully , It is suggested to change the password more difficult , Then write it down in a reliable place .
Modify port number
In fact, changing the port number should be more effective without changing the password , Because the total port number is only 216 individual , In theory, passwords can have 2062 Maybe (20 Bit code ,a-zA-Z0-9, altogether 62 Characters ), Therefore, complex passwords can more effectively resist attacks .
But to be on the safe side , So I'd better change the port number .
modify SSH The configuration file ( Note that sshd_config instead of ssh_config, More than a d)
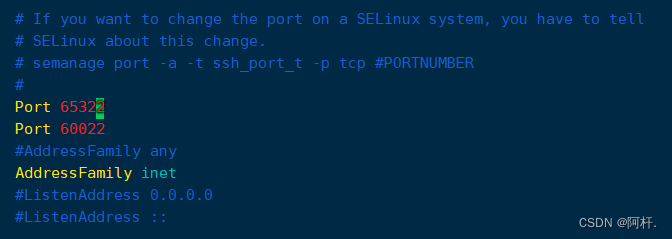
vim /etc/ssh/sshd_configfind “#Port 22”, Type... Directly in this line “yyp” Copy the line to the next line , Then put two lines of “#” No. note removed , Modified into :
Port 22 ( Here is the original port number , If it has not been modified, it is 22, My previous changes , So it is 60022)
Port 65322 ( Write your intended port number here )SSH The default listening port is 22, If you don't force other ports ,”Port 22” Note: all comments are open 22 Access port . I kept it 22 port , Prevent the following problems due to various permissions and configuration , Lead to company 22 The ports are inaccessible , That would be awkward . When everything is ok 了 , To shut down 22 port .
Open a new port at the firewall
firewall-cmd --zone=public --add-port=65322/tcp --permanentMeaning of order :
–zone # Scope
–add-port=65322/tcp # Add port , The format is : port / Communication protocol
–permanent # permanent , Failure after restart without this parameterrestart SSH Services and firewalls
systemctl restart sshd systemctl restart firewalld.serviceOpen a new port in the firewall of Tencent cloud control panel
If it is a cloud server , Then the service provider will still be linux A management software is installed in the host , This software also has the function of firewall , We used the firewall of the little black house before , So the login port here should also be added . Alibaba cloud is similar to Tencent cloud or any other cloud , Basically, this operation is required .
Be careful : Don't delete the previous , Keep the original port to prevent login failure , Delete the original port after the operation is successfulVerify whether the new port can log in successfully
Log in using the new port , See if you can log in , If you can't board , Check the previous steps , And do it again 3 Step by step operation .Delete the original port
- vim /etc/ssh/sshd_config, Go in and comment out the previous port .
- firewall-cmd --zone=public --remove-port=60022/tcp --permanent, Delete your original port , I am here 60022, The default is 80 port
- restart SSH Services and firewalls , That is the first. 3 Step by step operation , Just do it again
- Go to Tencent cloud and delete the original port
- Check whether the original port is available , If it doesn't work , Congratulations on your success !
Postscript
Go here , There is almost no problem , If there's anything else to worry about , Here's another way , It can be used to shield all foreign ip, But I haven't learned , So I didn't do it for the time being , The link is here , You can check it by yourself :https://www.isres.com/linux/4760.html( I don't know if I can )
What I want to say is , You must not make the server password too simple , Like I was blasted for a month this time , If it weren't for my complicated password , There must be an accident , And then there is , When you log on to the server , Pay attention to the login prompt , Have you said how many login failures have been recorded recently , If any , Check as soon as possible , Prevent the server from being blasted successfully .
边栏推荐
- Basic operations of databases and tables ----- creating data tables
- Knowledge summary of request
- JS数组常用方法的分类、理解和运用
- Pytorch four commonly used optimizer tests
- 优先级反转与死锁
- RT-Thread 线程的时间片轮询调度
- ES6 grammar summary -- Part I (basic)
- C语言函数之可变参数原理:va_start、va_arg及va_end
- Arduino gets the length of the array
- Cannot change version of project facet Dynamic Web Module to 2.3.
猜你喜欢
![[esp32 learning-1] construction of Arduino esp32 development environment](/img/31/dc16f776b7a95a08d177b1fd8856b8.png)
[esp32 learning-1] construction of Arduino esp32 development environment
Comparison of solutions of Qualcomm & MTK & Kirin mobile platform USB3.0
【ESP32学习-2】esp32地址映射
Types de variables JS et transformations de type communes
小天才电话手表 Z3工作原理
Priority inversion and deadlock
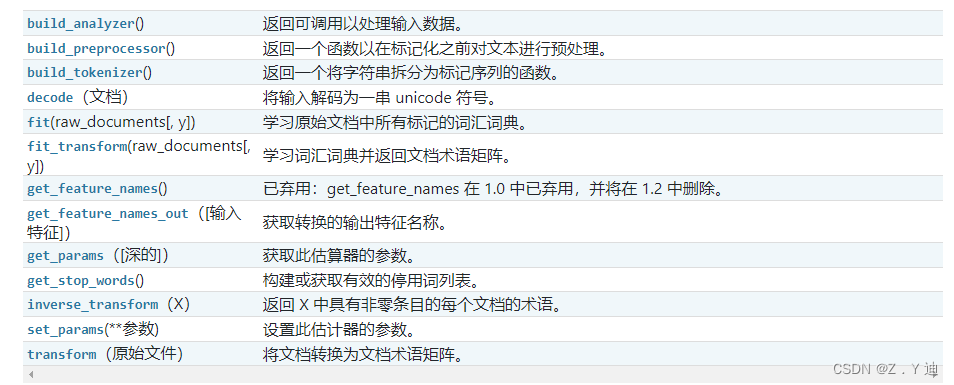
Feature of sklearn_ extraction. text. CountVectorizer / TfidVectorizer
Esp8266 uses Arduino to connect Alibaba cloud Internet of things

记一次云服务器被密码爆破的经历——关小黑屋、改密码、改端口

JS variable types and common type conversions
随机推荐
Navigator object (determine browser type)
Arm pc=pc+8 is the most understandable explanation
关键字 inline (内联函数)用法解析【C语言】
Analysis of charging architecture of glory magic 3pro
Types de variables JS et transformations de type communes
ESP learning problem record
高通&MTK&麒麟 手機平臺USB3.0方案對比
(一)R语言入门指南——数据分析的第一步
Togglebutton realizes the effect of switching lights
Basic operations of databases and tables ----- modifying data tables
ESP8266使用arduino连接阿里云物联网
Inline detailed explanation [C language]
Gallery's image browsing and component learning
Learning notes of JS variable scope and function
1081 rational sum (20 points) points add up to total points
AMBA、AHB、APB、AXI的理解
Keyword inline (inline function) usage analysis [C language]
Important methods of array and string
Use of lists
inline详细讲解【C语言】