当前位置:网站首页>[redis design and implementation] part I: summary of redis data structure and objects
[redis design and implementation] part I: summary of redis data structure and objects
2022-07-06 21:09:00 【Twilight_ years】
Simple dynamic string :SDS
【Redis note 】 Simple dynamic string (SDS)_ Twilight _ Blog years -CSDN Blog _sds Dynamic string
Linked list :linkedlist
Dictionaries :hashtable、map
【Redis note 】 Data structure and objects : Dictionaries _ Twilight _ Blog years -CSDN Blog
Skip list :skiplist
Set of integers :intset
Compressed list :ziplist
【Redis note 】 Compressed list (ziplist)_ Twilight _ Blog years -CSDN Blog
object :
The benefits of using objects :
(1) Judge whether an object can execute a given instruction according to the type of object
(2) You can set a variety of different data structures for objects according to different usage scenarios
The type and encoding of the object :
Redis Each object consists of a redisObject Structural representation
type: Record the type of object

Redis The key of is always a string object .
encoding: Determine the data structure of the object
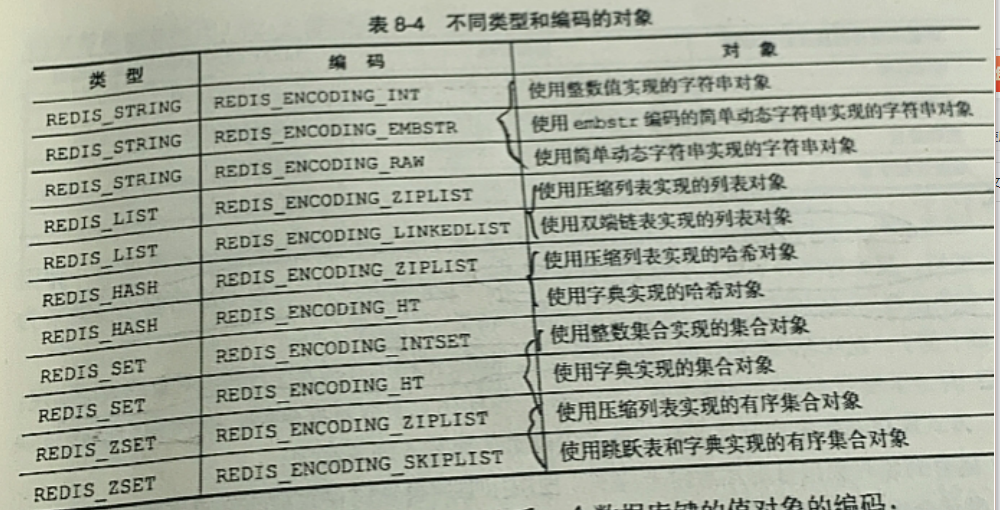
benefits : adopt encoding Property to set the data structure used by the object , Promoted Redis Flexibility and efficiency , because Redis You can set different data structures for an object according to different usage scenarios , So as to optimize the efficiency of the object in a certain scene .
ptr The pointer : Data structures that point to the underlying implementation of the object
String object :
Three coding methods :int,raw,embstr
(1) If a string object holds an integer value , And this integer can be used long Type said , Then the string object will store the integer value in the string object structure ptr Properties of the , And will encoding Set to REDIS_ECODING_INT.
(2) If the string object holds a string value , And the length of this string value is greater than 32 byte , Then the string object will use SDS To save the string value , And set the object's encoding to REDIS_ENCODING_RAW
(3) If the string object holds a string value , And the length of this string value is less than or equal to 32 byte , Then the string object uses embstr Code to save the string value .
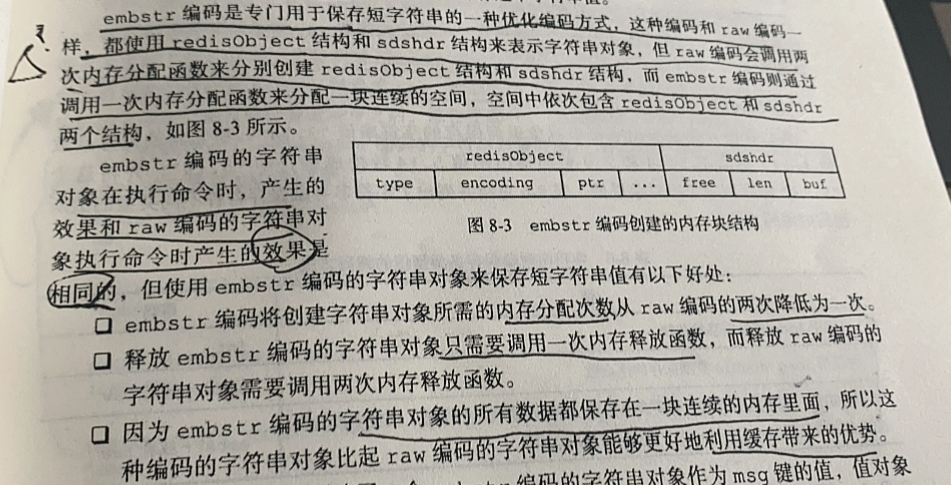
explain :long double Floating point numbers of type are Redis Is also saved as a string value . Floating point numbers <-> character string
Encoding conversion :
int->raw: Objects no longer hold integer values
embstr->raw: because embstr read-only , If the embstr Execute any modification commands , The program first encodes the object from embstr Convert to raw, Then execute the modify command .
List objects :
Two data structure implementation methods :ziplist,linkedlist
1、 Use ziplist The implementation , Each compressed list node holds a list element .
2、 Use linkedlist The implementation , Each double ended linked list node stores a string object , Each string object holds a list element .
String object Redis5 Objects of each type are the only objects that will be nested by objects of the other four types
Encoding conversion :

Hash object :
Two ways of implementation :ziplist,hashtable
1、 Use ziplist The implementation , Whenever a new key value pair is added to the hash object , The program will first save the key node and add it to the end of the table , Then add the value node to the end of the table
(1) Two nodes of the same key value pair are always close together
(2) The key value pairs added first are in the header , The key value pair added after is at the end of the table .
2、 Use hashtable The implementation , Key value pairs are saved using dictionary key value pairs . Every key and value in the dictionary is a string object .
Code conversion :

A collection of objects :
Two ways of coding :intset,hashtable
1、 Use intset when , All elements of the collection object are saved in intset in .
2、 Use hashtable when , Each key in the dictionary is a string object , Each string object contains a collection element , All values are set to null
Encoding conversion :

An orderly collection of objects :
Two ways of coding :ziplist,skiplist
1、 Use ziplist when , Each set uses two compressed list nodes next to each other to save , The first node holds the members of the element , The second element holds the score of the element .
The set elements in the compressed list are sorted from small to large , Elements with smaller scores are placed close to the heading , Elements with larger branches are placed in the direction of the footer .
2、 Use skiplist when , Use zset Structure implementation , Including dictionary and jump table .
(1) The jump table saves all element sets from small to large according to the score , Each hop table node holds a set element :object Attribute save member ,score Save score . If you only use dictionaries , Keep an orderly time O(logn), Space O(n)
(2) The dictionary creates a mapping from members to scores for an ordered set , In the dictionary Each key value pair of the holds a collection element . Can pass O(1) Find the score of a given member . If you only use the jump table ,O(logn)
(3)zset Structure uses both jump tables and dictionaries to store set elements , But they share members and scores of the same element through pointers . So using them at the same time won't waste extra memory .
Encoding conversion :

Redis Properties of objects :
Type checking :
Redis There are two kinds of commands for operating keys :
You can perform... On any type of key ; Can only be performed on a specific type of key .
Before executing a type specific command ,Redis Will check the type of key , Then decide whether to execute the command .
Command polymorphism :
Redis According to the encoding method of the value object , Choose the appropriate code to implement the command .
Type based polymorphism : No matter what type of key you enter , Commands can be executed correctly
Coding based polymorphism : One command can be used to handle many different codes at the same time
Memory recovery :
Redis A reference counting mechanism is built in the object system to realize memory recycling , The program can track the reference count information of the object , Automatically release objects and reclaim memory when appropriate .

Object sharing :
Object reference counting can realize object sharing .
stay Redis in , An object that allows multiple keys to share the same value :
(1) Let the value pointer of the key point to an existing object .
(2) Add the reference count of the shared object 1
The shared object mechanism is helpful to save memory , The more objects with the same value are saved , Object sharing mechanism can save more memory .
(1)Redis When the server is initialized , establish 0~9999 String objects of all integer values are shared .
(2)Redis Only string objects containing integer values are shared

The idle time of the object :

边栏推荐
- Thinking about agile development
- Hardware development notes (10): basic process of hardware development, making a USB to RS232 module (9): create ch340g/max232 package library sop-16 and associate principle primitive devices
- Leetcode hot topic Hot 100 day 32: "minimum coverage substring"
- Is it safe to open an account in flush? Which securities company is good at opening an account? Low handling charges
- 基于STM32单片机设计的红外测温仪(带人脸检测)
- Pat 1085 perfect sequence (25 points) perfect sequence
- 038. (2.7) less anxiety
- el-table表格——sortable排序 & 出现小数、%时排序错乱
- 966 minimum path sum
- Data Lake (VIII): Iceberg data storage format
猜你喜欢

3D face reconstruction: from basic knowledge to recognition / reconstruction methods!
Infrared thermometer based on STM32 single chip microcomputer (with face detection)

【OpenCV 例程200篇】220.对图像进行马赛克处理
After working for 5 years, this experience is left when you reach P7. You have helped your friends get 10 offers
Aiko ai Frontier promotion (7.6)
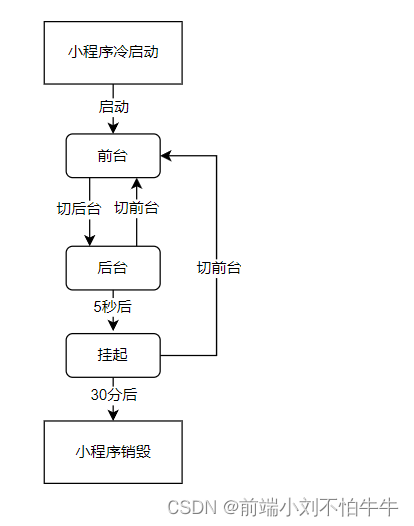
【微信小程序】運行機制和更新機制
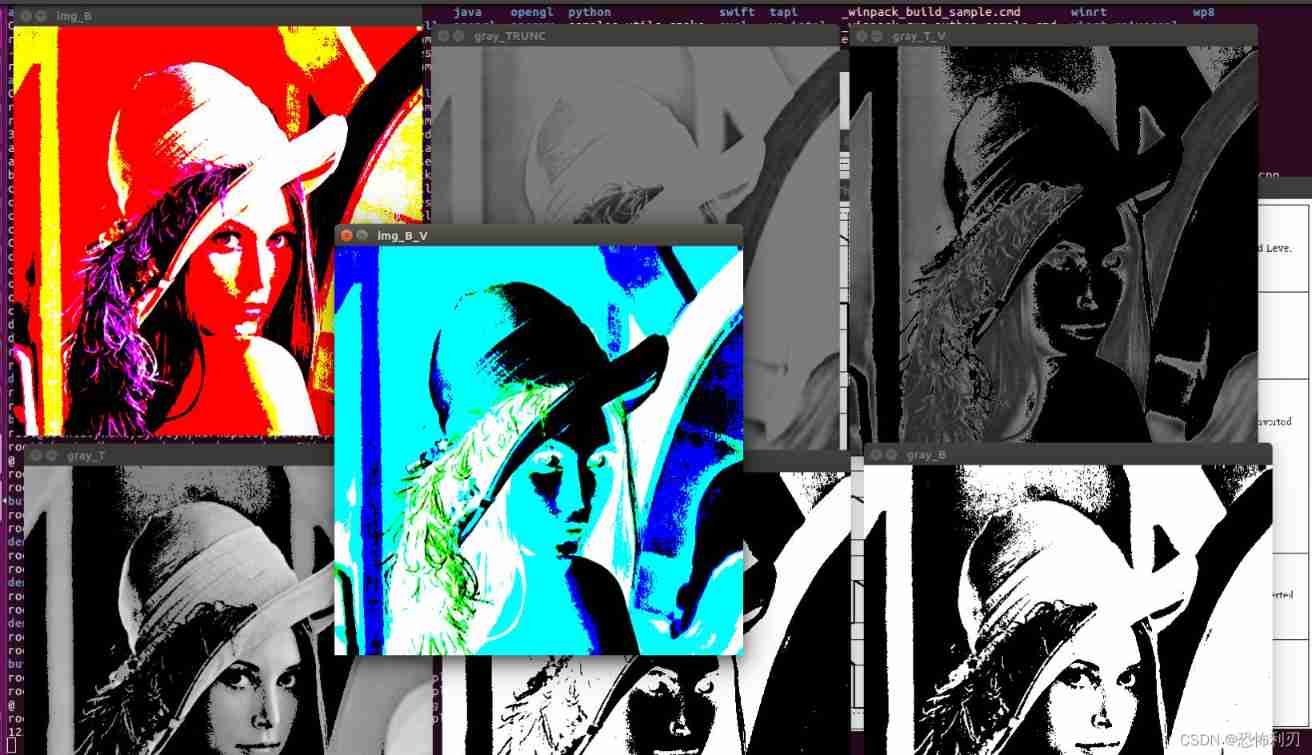
Opencv learning example code 3.2.3 image binarization

Laravel notes - add the function of locking accounts after 5 login failures in user-defined login (improve system security)

KDD 2022 | realize unified conversational recommendation through knowledge enhanced prompt learning
![[200 opencv routines] 220 Mosaic the image](/img/75/0293e10ad6de7ed86df4cacbd79b54.png)
[200 opencv routines] 220 Mosaic the image
随机推荐
Manifest of SAP ui5 framework json
Mécanisme de fonctionnement et de mise à jour de [Widget Wechat]
What key progress has been made in deep learning in 2021?
Tips for web development: skillfully use ThreadLocal to avoid layer by layer value transmission
[200 opencv routines] 220 Mosaic the image
Can novices speculate in stocks for 200 yuan? Is the securities account given by qiniu safe?
This year, Jianzhi Tencent
新型数据库、多维表格平台盘点 Notion、FlowUs、Airtable、SeaTable、维格表 Vika、飞书多维表格、黑帕云、织信 Informat、语雀
Is this the feeling of being spoiled by bytes?
[MySQL] basic use of cursor
Yyds dry goods count re comb this of arrow function
After working for 5 years, this experience is left when you reach P7. You have helped your friends get 10 offers
【mysql】游标的基本使用
How to turn a multi digit number into a digital list
Why do job hopping take more than promotion?
HMS Core 机器学习服务打造同传翻译新“声”态,AI让国际交流更顺畅
User defined current limiting annotation
#yyds干货盘点#重新梳理箭头函数的this
OneNote in-depth evaluation: using resources, plug-ins, templates
2017 8th Blue Bridge Cup group a provincial tournament