当前位置:网站首页>Analysis of using jsonp cross domain vulnerability and XSS vulnerability in honeypot
Analysis of using jsonp cross domain vulnerability and XSS vulnerability in honeypot
2022-07-07 08:37:00 【It old culvert】

One 、 Preface
When we played the red team , I often encounter honeypots , And some more “ Active defense ” Some cross domain vulnerabilities and xss, Make a simple analysis of this .
Two 、 The concept of honeypot
Honeypot is mainly through the arrangement of bait , Entice the attacker to attack , Then capture through traffic 、 Behavioral analysis, etc. on the attacker's portrait and trace the source .
for example HFish Honeypot , It belongs to the honey pot of high intercourse , By capturing attacker behavior , Get attacker attack data 、IP Address, etc , However, it is far from enough to obtain these data for the attacker's portrait , and HFish It also provides customization web Deployment of Honeypot , Simply analyze the two honeypots you encounter .
The following are screenshots of two honeypots encountered in the red team and vulnerability mining .
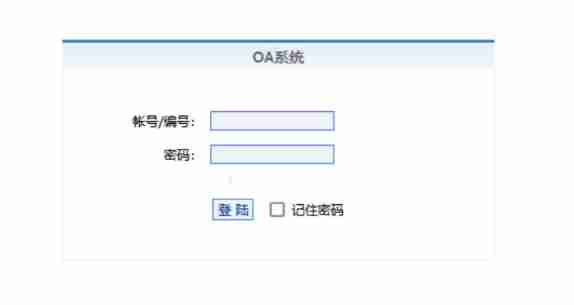

Why is it “ Active defense ” Well ?
When the attacker visits the page ,JS Automatically , Send requests to many of our favorite websites , These requests take advantage of many websites jsonp Cross domain vulnerabilities and xss Loophole , Get COOKIE、 user name 、 Mobile phone number and other information , So as to trace the source of the attacker , And the attacker just visits this page , So it's “ Active defense ”.
3、 ... and 、jsonp Cross domain
jsonp Cross domain vulnerabilities are similar to CSRF Loophole , Some are also called read type CSRF Loophole , You can get some user names of website users 、 Mobile phone number and other sensitive data , If you are not familiar with this vulnerability, you can baidu by yourself ~
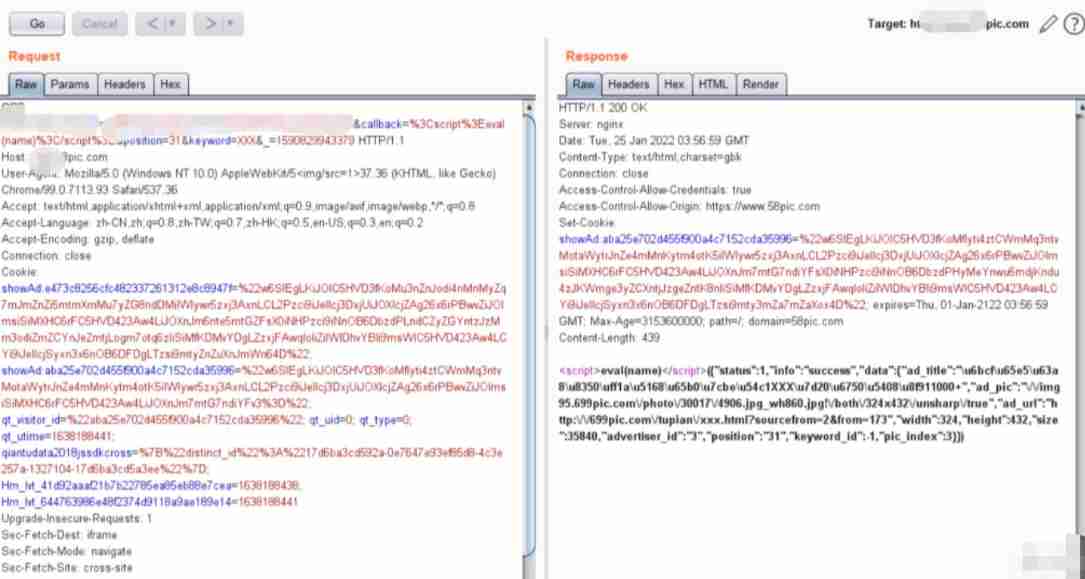
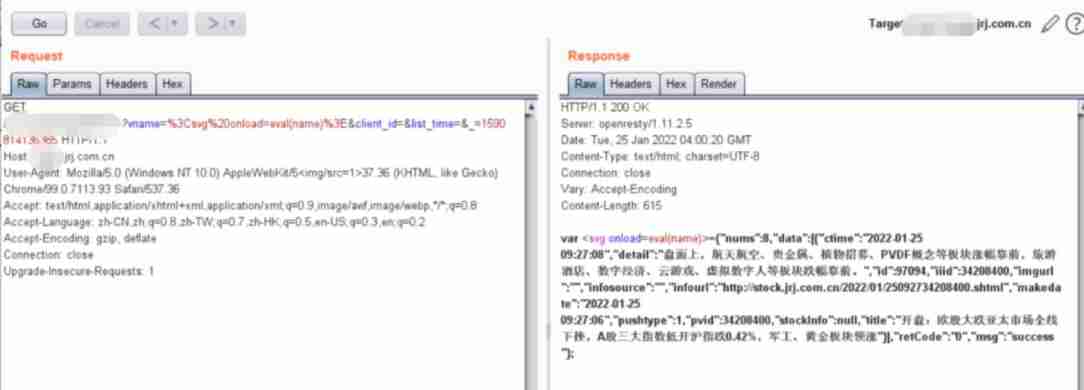
Here are some uses in the honey pot jsonp Screenshot of data package with cross domain vulnerability .
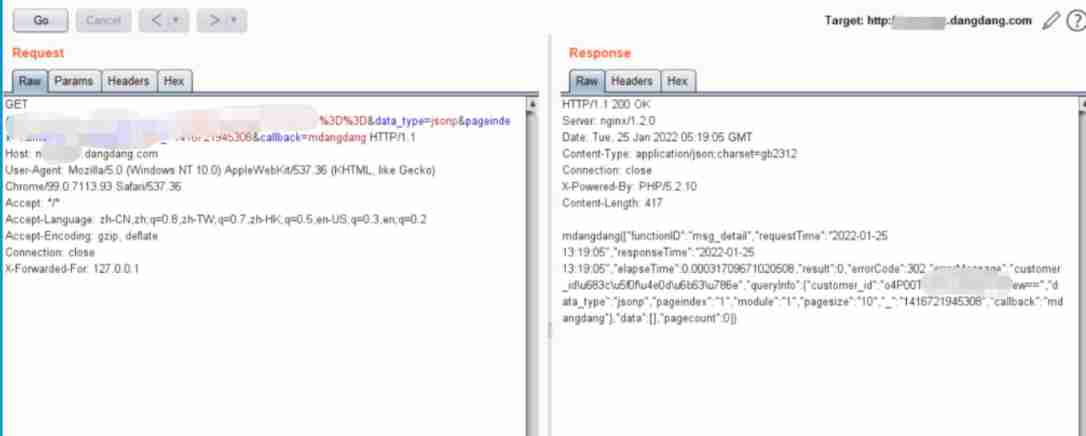
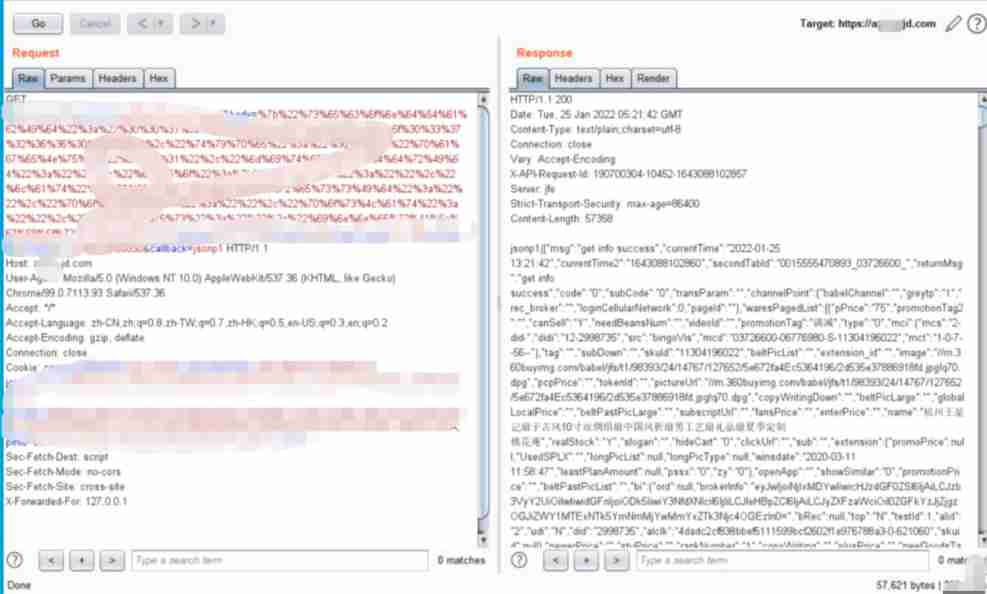
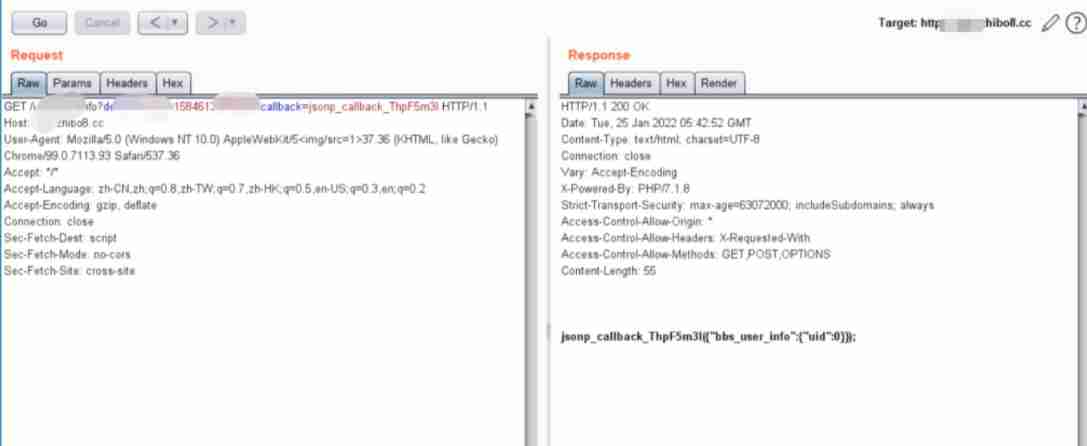
If you have logged in to the website and have cookie There is , You can often return the user name 、 Phone number data .
Four 、xss Loophole
xss Vulnerabilities are basically eval(name), I think there are some problems with the honeypot configuration , see js code , Is all added to one iframe In the label , Then set the iframe In the label name The variable is a string js Code , And here it is eval(name), In my understanding, it should be preset js Code , Set up name Variable , Then execute the string js Code .(P.S. JS I know a little about the code , This paragraph may be misunderstood and analyzed , I won't go into it .)
jsonp Improper configuration will also occur xss, Here's the picture :
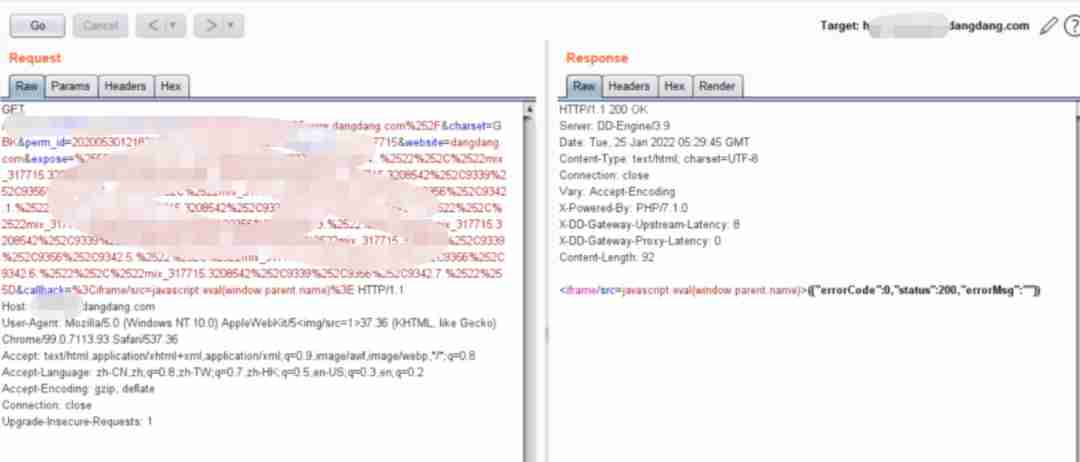
There are also direct xss, For example, this csdn Of (csdn The size of is a little heavier )
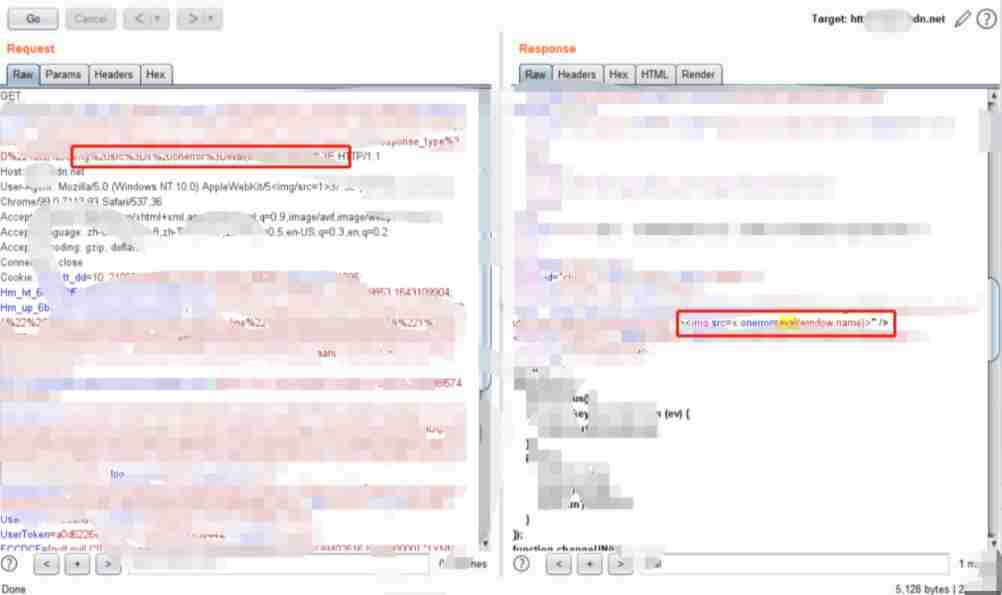
Blog park xss( Duplicate code )
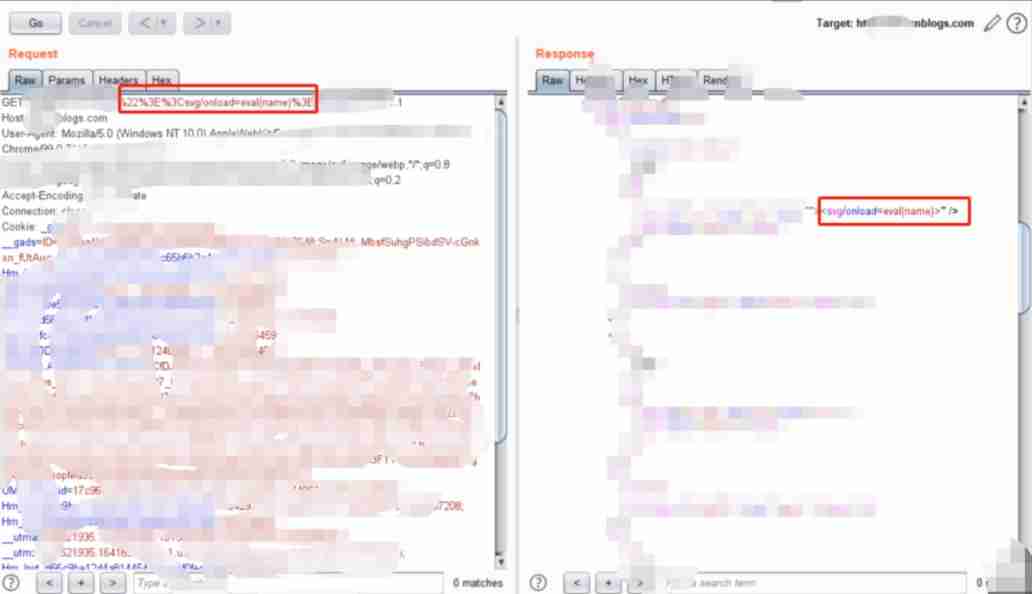
I believe these two websites are engaged in IT It should be used by most people , Honeypots exploit the loopholes of such websites , You can also easily get the attacker's user name 、 Mobile phone number and other information .
Sum up , The so-called active defense honeypot , As long as the attacker uses the browser to access , And there is a website that exploits the vulnerability of honeypot configuration to obtain user information in the browser cache COOKIE, Then the honey pot can be used jsonp perhaps xss Vulnerability to obtain the attacker's personal information , With a name 、ID、 After the mobile phone number and other information , Tracing the source of the red team has also become easier .
5、 ... and 、 Reverse honeypot
The honeypot is also a system , There are also some loopholes , for example HFish Honeypot once had unauthorized access to information vulnerabilities and storage XSS Loophole , The magic array honeypot of mo'an technology also had an unauthorized access vulnerability , Take advantage of the loopholes in the honeypot itself to reverse the honeypot .
Honey pot my research is not deep , More ideas depend on the free play of teachers , You can still try it when you encounter it XSS And other loopholes .
6、 ... and 、 How to defend the honeypot
If these honeypots are commercial , Many interfaces are the same , For example, the second picture in this article , But there are also user-defined interfaces , So I think it is troublesome to prevent honeypots through features , And cannot be completely prevented .
7、 ... and 、 Precautions
1、 If you have code ability , You can write browser plug-ins or burp plug-in unit , Detected that the packet contains callback、jsonp Wait for keywords , Intercept and let the user confirm .
2、 Browsers use noscript Plug-ins can find potential xss threat , It can be found that partial utilization xss Loophole honeypot .
边栏推荐
- [IELTS speaking] Anna's oral learning records part2
- JS的操作
- AVL平衡二叉搜索树
- Are you holding back on the publicity of the salary system for it posts such as testing, development, operation and maintenance?
- 南京商品房买卖启用电子合同,君子签助力房屋交易在线网签备案
- 下载和安装orcale database11.2.0.4
- 2-3 lookup tree
- Improve the delivery efficiency of enterprise products (1) -- one click installation and upgrade of enterprise applications
- [untitled]
- 单场带货涨粉10万,农村主播竟将男装卖爆单?
猜你喜欢

Give full play to the wide practicality of maker education space
MySQL introduction - crud Foundation (establishment of the prototype of the idea of adding, deleting, changing and searching)
Data type - integer (C language)

About using CDN based on Kangle and EP panel
IP地址的类别
![[Yu Yue education] basic reference materials of electrical and electronic technology of Nanjing Institute of information technology](/img/2a/01db1b84c26502c851786aaca56abe.jpg)
[Yu Yue education] basic reference materials of electrical and electronic technology of Nanjing Institute of information technology
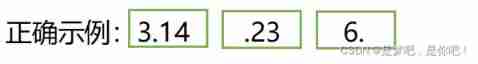
Data type - floating point (C language)

Opencv learning note 3 - image smoothing / denoising
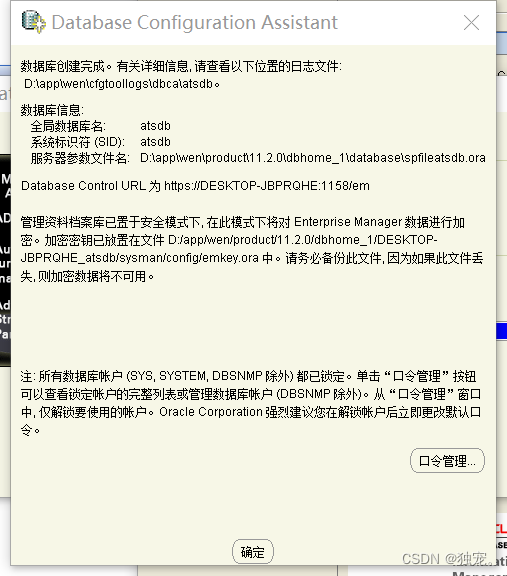
下载和安装orcale database11.2.0.4
![[untitled]](/img/b5/348b1d8b5d34cf10e715522b9871f2.png)
[untitled]
随机推荐
Rsync remote synchronization
JEditableTable的使用技巧
Leetcode 1984. Minimum difference in student scores
如何在图片的目标中添加目标的mask
Opencv learning notes 1 -- several methods of reading images
JS的操作
[hard core science popularization] working principle of dynamic loop monitoring system
Opencv learning note 5 - gradient calculation / edge detection
idea里使用module项目的一个bug
Golang compilation constraint / conditional compilation (/ / +build < tags>)
PLSQL的安装和配置
2-3 lookup tree
In go language, function is a type
iptables 之 state模块(ftp服务练习)
SSM 整合
Automatic upgrading of database structure in rainbow
[Chongqing Guangdong education] accounting reference materials of Nanjing University of Information Engineering
2-3查找树
mysql分区讲解及操作语句
如何在快应用中实现滑动操作组件