当前位置:网站首页>(POJ - 3579) median (two points)
(POJ - 3579) median (two points)
2022-07-06 16:09:00 【AC__ dream】
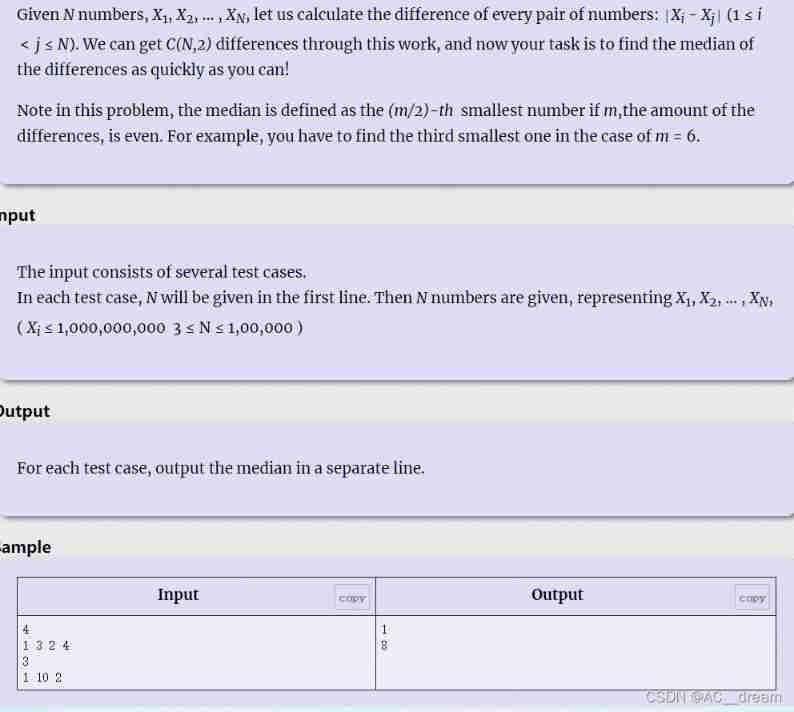
Chinese question meaning : Now there is N A mysterious number (A1,A2,A3….An), We need to get a password from this string of numbers .
The way to get the password is :
First calculate the difference between each number :|Ai-Aj|(1<=i<j<=N), In the end, you can get C Difference .
The final password is the median of these numbers .
If C It's even , It is stipulated that the median is C/2 Small difference .
This question and POJ-3579 The method of question is similar , We also solve it by dichotomy , For each number to be bisected x, We go through check Function to determine whether it is less than or equal to x How many pairs of distances are there , If the distance is less than or equal to x The number of pairs of is greater than half of the logarithm of the total , that r=x, conversely l=x+1, How should the specific dichotomy be carried out ? Let's start with a Sort the array from small to large , The dichotomy is found in ai On the right and the distance is less than or equal to x The number of , because aj-ai It is monotonically increasing , So this process is carried out through dichotomy , Traverse in turn ai, The distance is less than x Number to number , Two points are enough , There are quite a lot of details , See the code for details :
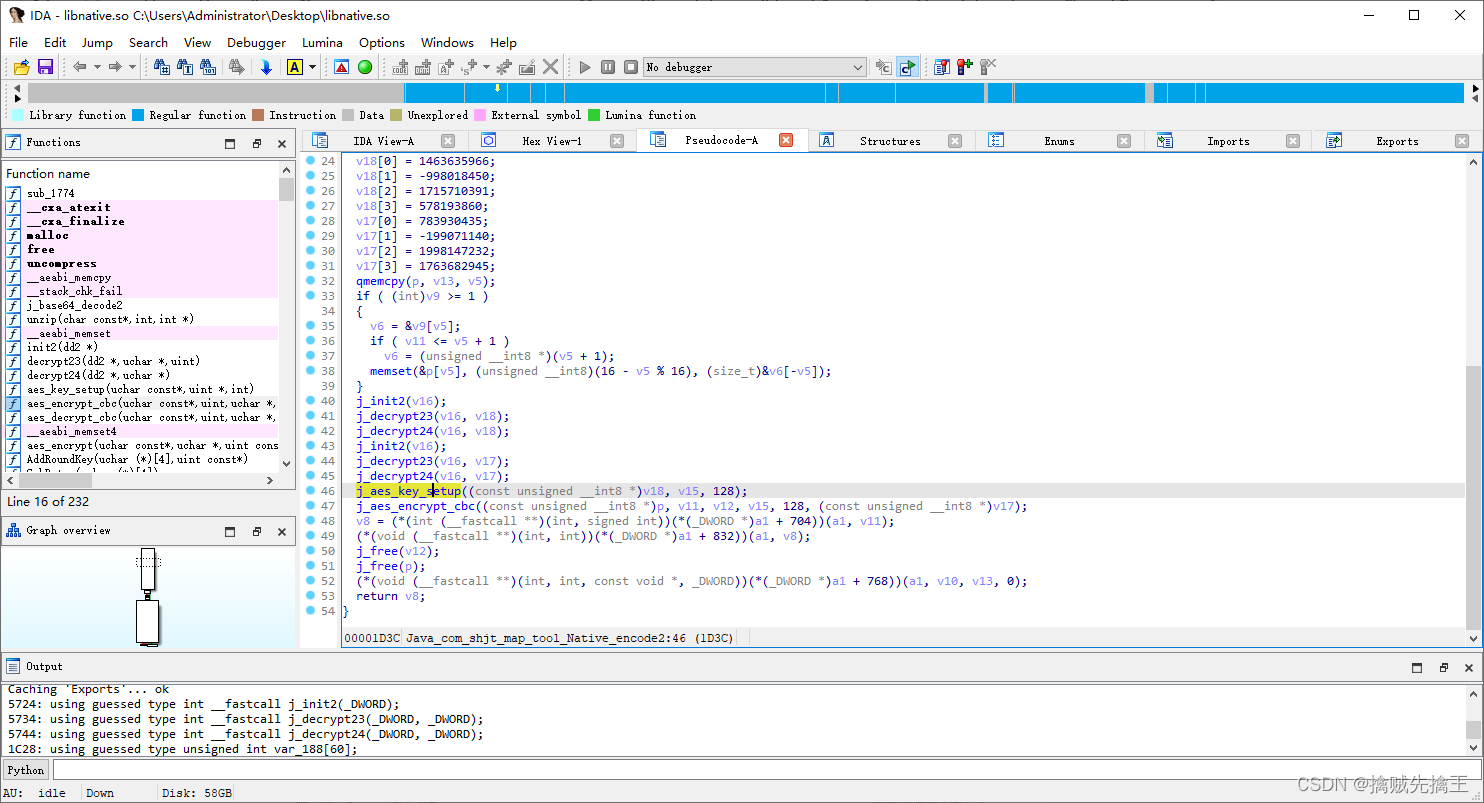
#include<cstdio>
#include<iostream>
#include<cstring>
#include<vector>
#include<algorithm>
#include<map>
#include<cmath>
#include<queue>
using namespace std;
const int N=1000003;
int a[N],n;
bool check(int x)// Find that the distance is less than or equal to x How many pairs are there , More than half the logarithm of all numbers returns true, Otherwise return to false
{
int cnt=0;
for(int i=1;i<=n;i++)
cnt+=upper_bound(a+1,a+n+1,a[i]+x)-a-i-1;
if(cnt>=((long long)n*(n-1)/2+1)/2) return true;
return false;
}
int main()
{
while(scanf("%d",&n)!=EOF)
{
for(int i=1;i<=n;i++)
scanf("%d",&a[i]);
sort(a+1,a+n+1);
int l=0,r=1000000000,mid;
while(l<r)
{
mid=l+r>>1;
if(check(mid)) r=mid;
else l=mid+1;
}
printf("%d\n",l);
}
return 0;
}边栏推荐
- Openwrt build Hello ipk
- Gartner: five suggestions on best practices for zero trust network access
- Hdu-6025-prime sequence (girls' competition)
- 【练习-8】(Uva 246)10-20-30==模拟
- B - Code Party (girls' competition)
- Openwrt source code generation image
- 双向链表—全部操作
- Information security - threat detection engine - common rule engine base performance comparison
- (POJ - 2739) sum of constructive prime numbers (ruler or two points)
- 信息安全-安全专业名称|CVE|RCE|POC|VUL|0DAY
猜你喜欢

Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
![[exercise-7] crossover answers](/img/66/3dcba2e70a4cd899fbd78ce4d5bea2.png)
[exercise-7] crossover answers

409. Longest palindrome
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
信息安全-威胁检测-NAT日志接入威胁检测平台详细设计
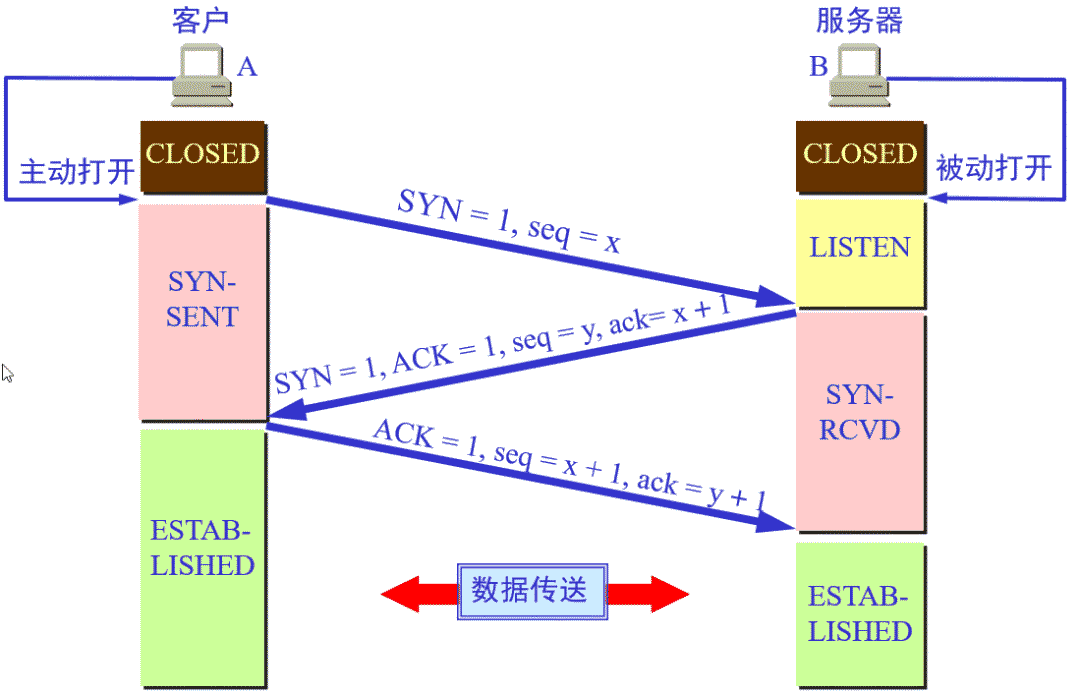
TCP's three handshakes and four waves

Information security - threat detection engine - common rule engine base performance comparison
frida hook so层、protobuf 数据解析
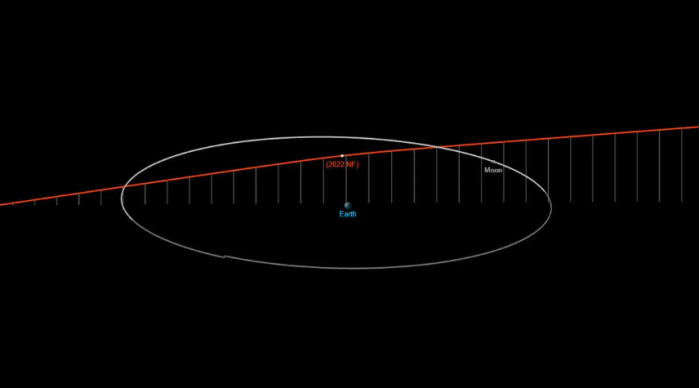
“鬼鬼祟祟的”新小行星将在本周安全掠过地球:如何观看
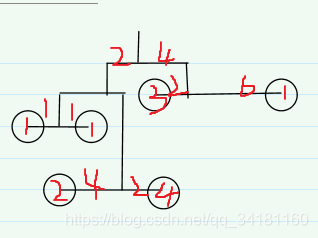
【练习-5】(Uva 839)Not so Mobile(天平)
随机推荐
Suffix expression (greed + thinking)
[exercise-7] crossover answers
X-Forwarded-For详解、如何获取到客户端IP
Research Report of peripheral venous catheter (pivc) industry - market status analysis and development prospect prediction
Write web games in C language
[teacher Gao UML software modeling foundation] collection of exercises and answers for level 20 cloud class
Vs2019 initial use
Nodejs+vue online fresh flower shop sales information system express+mysql
[exercise-6] (UVA 725) division = = violence
【练习-2】(Uva 712) S-Trees (S树)
Opencv learning log 30 -- histogram equalization
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
“鬼鬼祟祟的”新小行星将在本周安全掠过地球:如何观看
Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
Information security - threat detection - detailed design of NAT log access threat detection platform
Opencv learning log 24 -- Hough transform 2 (maximum interval and minimum length can be limited)
想应聘程序员,您的简历就该这样写【精华总结】
1605. Sum the feasible matrix for a given row and column
【练习-7】(Uva 10976)Fractions Again?!(分数拆分)
MySQL授予用户指定内容的操作权限