当前位置:网站首页>Condition and AQS principle
Condition and AQS principle
2022-07-06 01:10:00 【@Overstep】
Condition brief introduction
Any one of them java Objects are all inherited from Object class , Communication between online programs is often applied to Object Several methods of , such as wait(),wait(long timeout),wait(long timeout, int nanos) And notify(),notifyAll() Several ways to implement wait / A notification mechanism , alike , stay java Lock Under the system, there will still be the same way to achieve waiting / A notification mechanism . On the whole Object Of wait and notify/notify It is to cooperate with the object monitor to complete the inter thread waiting / A notification mechanism , and Condition And Lock Cooperate with the completion waiting notification mechanism , The former is java At the bottom level , The latter is at the language level , It has higher controllability and expansibility . The two are different in use , There are still many differences in functional features :
- Condition Can support no response interrupt , But by using Object The way doesn't support ;
- Condition Can support multiple waiting queues (new Multiple Condition object ), and Object Only one... Can be supported ;
- Condition It can support the setting of timeout time , and Object I won't support it
Condition analysis :
(1)Condition The essence of waiting for notification is waiting queue and The interactive process of synchronizing queues , Follow object Of wait()/notify() The mechanism is the same ;Condition Based on synchronous lock state Realized , and objec Is based on monitor Pattern implementation .
(2) One lock(AQS) There can be multiple Condition, That is, multiple waiting queues , There is only one synchronization queue .
(3)Condition.await() Method execution , Will synchronize the... In the queue head Lock released , Encapsulate threads into new node Add to the waiting queue ;Condition.signal() Method execution , The first node in the waiting queue will be moved to the synchronization queue , Until the lock state It's only when you get it that you wake up .
AQS Principle Overview
It's a framework for building locks and synchronizers , Use AQS A large number of synchronizers can be constructed simply and efficiently
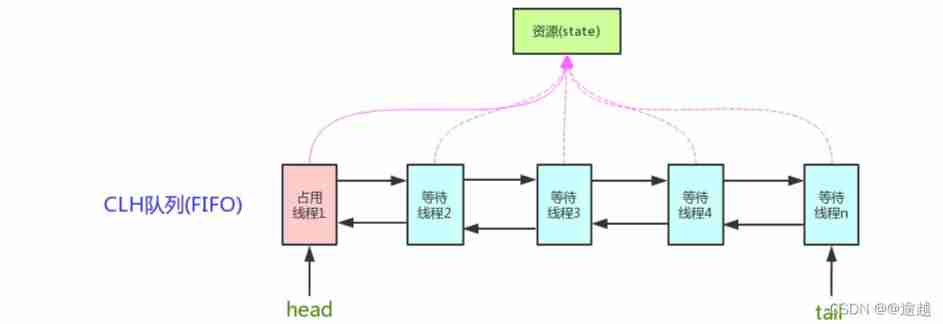
AQS The core idea is , If the requested shared resource is free , Set the thread of the current request resource to a valid worker thread , And set the shared resources to the locked state . If the requested shared resource is occupied , Then we need a set of mechanism for thread blocking waiting and lock allocation when it is awakened , This mechanism AQS Yes, it is CLH The implementation of queue lock , Join the queue with the thread temporarily unable to acquire the lock .
CLH(Craig,Landin,andHagersten) A queue is a virtual two-way queue ( Virtual two-way queue means there is no queue instance , There is only an association between nodes ).AQS It is to encapsulate each thread requesting shared resources into a CLH A node in a lock queue (Node) To achieve lock allocation .
AQS Define two ways to share resources
1)Exclusive( Monopoly )
Only one thread can execute , Such as ReentrantLock. It can be divided into fair lock and unfair lock ,ReentrantLock Two locks are supported at the same time , Let's say ReentrantLock Introduce the definition of these two kinds of locks :
- Fair lock : In the order in which threads are queued in the queue , First come, first get the lock
- Not fair lock : When a thread wants to acquire a lock , Pass it twice first CAS Operate to grab the lock , If you don't get , The current thread then joins the queue waiting for wakeup .
2)Share( share )
边栏推荐
- 关于softmax函数的见解
- The detailed page returns to the list and retains the original position of the scroll bar
- MobileNet系列(5):使用pytorch搭建MobileNetV3并基于迁移学习训练
- SSH login is stuck and disconnected
- Lone brave man
- Test de vulnérabilité de téléchargement de fichiers basé sur dvwa
- Cf:d. insert a progression [about the insert in the array + the nature of absolute value + greedy top-down]
- KDD 2022 | EEG AI helps diagnose epilepsy
- DD's command
- Who knows how to modify the data type accuracy of the columns in the database table of Damon
猜你喜欢
《强化学习周刊》第52期:Depth-CUPRL、DistSPECTRL & Double Deep Q-Network
SSH login is stuck and disconnected
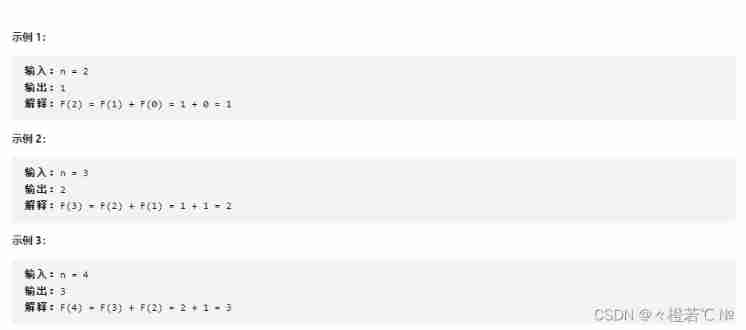
Fibonacci number
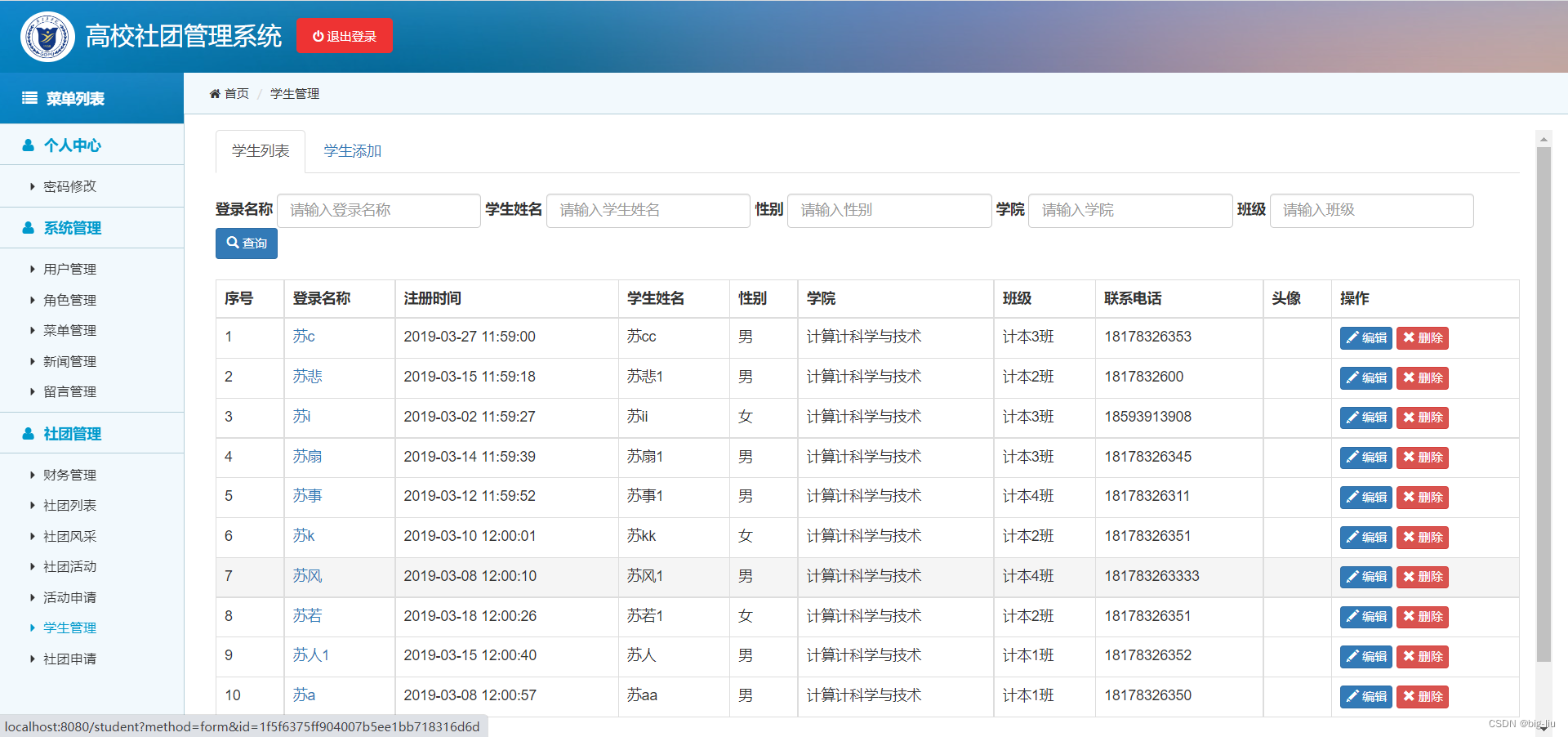
BiShe - College Student Association Management System Based on SSM

cf:D. Insert a Progression【关于数组中的插入 + 绝对值的性质 + 贪心一头一尾最值】
![Cf:h. maximum and [bit operation practice + K operations + maximum and]](/img/c2/9e58f18eec2ff92e164d8d156629cf.png)
Cf:h. maximum and [bit operation practice + K operations + maximum and]
Beginner redis
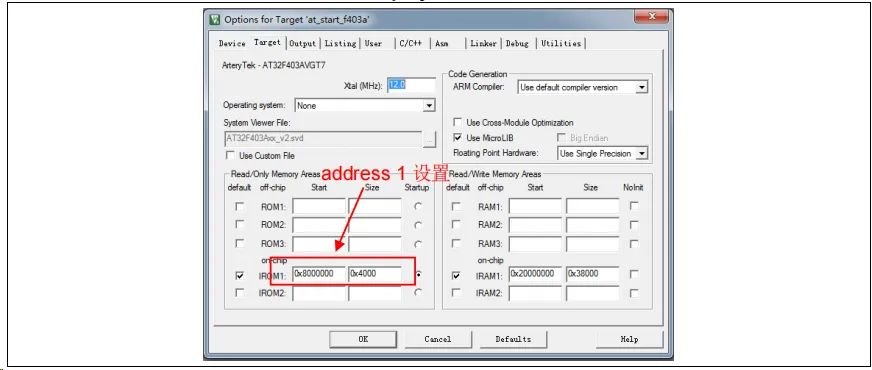
MCU通过UART实现OTA在线升级流程
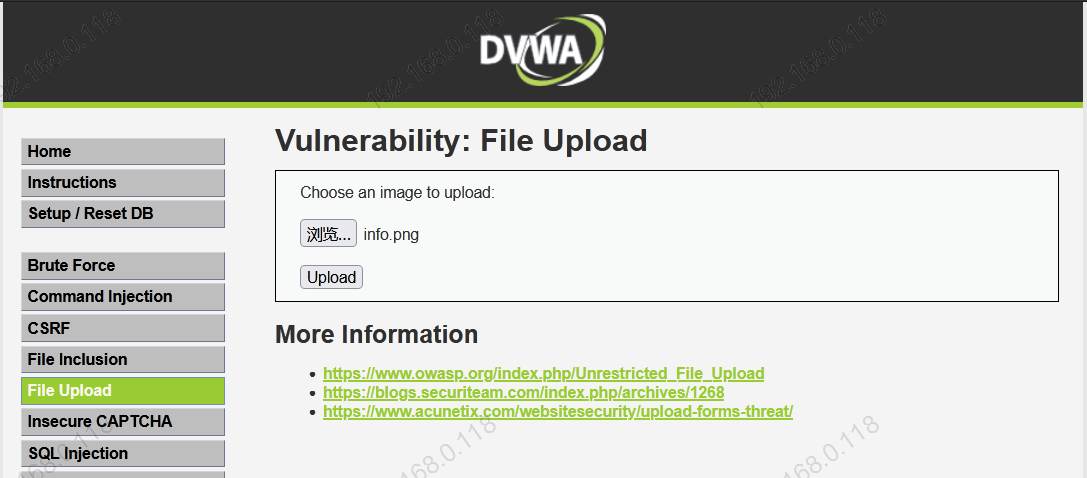
基于DVWA的文件上传漏洞测试
Four dimensional matrix, flip (including mirror image), rotation, world coordinates and local coordinates
随机推荐
GNSS terminology
BiShe - College Student Association Management System Based on SSM
After 95, the CV engineer posted the payroll and made up this. It's really fragrant
Leetcode study - day 35
Xunrui CMS plug-in automatically collects fake original free plug-ins
Leetcode daily question solution: 1189 Maximum number of "balloons"
Ubantu check cudnn and CUDA versions
Four dimensional matrix, flip (including mirror image), rotation, world coordinates and local coordinates
程序员搞开源,读什么书最合适?
MCU通过UART实现OTA在线升级流程
[groovy] compile time meta programming (compile time method interception | method interception in myasttransformation visit method)
Mlsys 2020 | fedprox: Federation optimization of heterogeneous networks
Starting from 1.5, build a micro Service Framework - call chain tracking traceid
Lone brave man
Finding the nearest common ancestor of binary tree by recursion
China Taiwan strategy - Chapter 8: digital marketing assisted by China Taiwan
KDD 2022 | EEG AI helps diagnose epilepsy
DD's command
VMware Tools installation error: unable to automatically install vsock driver
FFT 学习笔记(自认为详细)