当前位置:网站首页>Class A, B, C networks and subnet masks in IPv4
Class A, B, C networks and subnet masks in IPv4
2022-07-06 03:59:00 【yanwu_ nuc】
Reference article
Reference article
When two computers connected to a network communicate with each other , The packets they transmit contain some additional information , These additional information is the address of the computer that sends the data and the address of the computer that receives the data . When the network exists with IP Protocol based communication , These addresses for sending and receiving data are IP Address .
The following are involved IP All addresses are Ipv4 Of 32 position IP Address
IP Address format :IP Address = network address + The host address
IP Address according to network address Mainly can be divided into A、B、C Three types of address
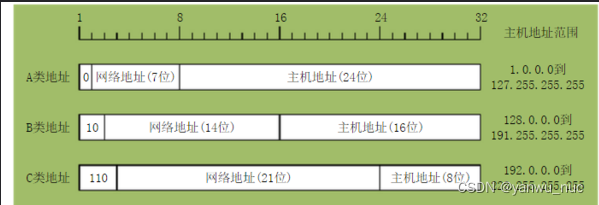
1. A class IP Address
One A class IP Address by 1 Byte network address and 3 Byte host address composition , The highest bit of the network address must be “0”, Address range from 1.0.0.0 To 126.0.0.0. Usable A There are 126 individual , Every network can hold 1 More than 100 million hosts .
2. B class IP Address
One B class IP Address by 2 Byte network address and 2 Byte host address composition , The highest bit of the network address must be “10”, Address range from 128.0.0.0 To 191.255.255.255. Usable B There are 16382 individual , Every network can hold 6 More than ten thousand hosts .
3. C class IP Address
One C class IP Address by 3 Byte network address and 1 Byte host address composition , The highest bit of the network address must be “110”. Range from 192.0.0.0 To 223.255.255.255.C Class network up to 209 More than a , Every network can hold 254 Host computer .
Subnet mask (subnet mask):
The subnet mask is a 32 Bit address , For shielding IP Part of the address to distinguish between a network ID and a host ID , The subnet mask cannot exist alone , It has to be combined with IP Address used together .
Function of subnet mask :
1、 For shielding IP Part of the address to distinguish between a network ID and a host ID , Only Network identity The same two hosts can communicate with each other without routing .
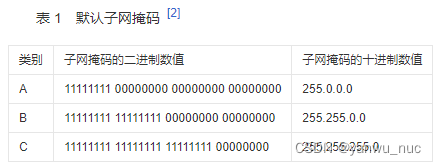 The subnet mask must match IP Address to use . For common Networks A、 B、C class IP The binary and decimal correspondence of the default subnet mask of the address is shown in the table 1 Shown .
The subnet mask must match IP Address to use . For common Networks A、 B、C class IP The binary and decimal correspondence of the default subnet mask of the address is shown in the table 1 Shown .
The working process of subnet mask is : take 32 Bit subnet mask and IP Address carries out bitwise logic in binary form “ And ” The result of the operation is the network address , Sum the result of the subnet mask binary non with IP Address binary logic “ And ”(AND) operation , What you get is the host address .
Such as :192.168.10.11 AND 255.255.255.0, The result is 192.168.10.0, The meaning of its expression is : The IP The address belongs to 192.168.10.0 The network , Its host number is 11, That is, the number in this network is 11 The host .
2、 The second is to put a big IP The network is divided into several small subnetworks .
In order to better manage the network in the intranet , Network administrators also take advantage of the subnet mask , Artificially divide a larger intranet into more small subnets , recycling Three layer switch The routing function of realizes the interconnection of subnets , So as to effectively solve the network broadcast storm and network virus and many other network management problems .
The subnet mask mechanism provides a method for subnet partition . Its effect is : Reduce traffic on the network ; save IP Address ; Easy to manage ; Solve some problems of the physical network itself . After using the subnet mask to divide the subnets , Communication is possible in the subnet , Cannot communicate across subnets , Routers should be used for communication between subnets , And correctly configure the static routing information . Divide subnets , You should follow the rules of subnet partition structure . Is to use continuous 1 stay IP Add the network address in the address , At the same time, reduce the number of bits representing the host address .
for example ,IP The address is 130.39.37.100, The network address is 130.39.37.0、 The subnet address is 130.39.37.0、 The subnet mask is 255.255.255.0, The network address part and the subnet identification part are “1” Corresponding , The host identification part is “0” Corresponding . Use CIDR Expressed as :130.39.37.100/24 namely IP Address / Mask length . On the third byte 255 The corresponding 8 Bit binary value is to lend the host address bits to the network address part , Acts as the number of bits for dividing subnets .
边栏推荐
- Custom event of C (31)
- Conditionally [jsonignore]
- cookie,session,Token 这些你都知道吗?
- [FPGA tutorial case 12] design and implementation of complex multiplier based on vivado core
- MySQL reads missing data from a table in a continuous period of time
- RT thread -- FTP of LwIP (2)
- Align items and align content in flex layout
- [matlab] - draw a five-star red flag
- C#(二十七)之C#窗体应用
- Développement d'un module d'élimination des bavardages à clé basé sur la FPGA
猜你喜欢
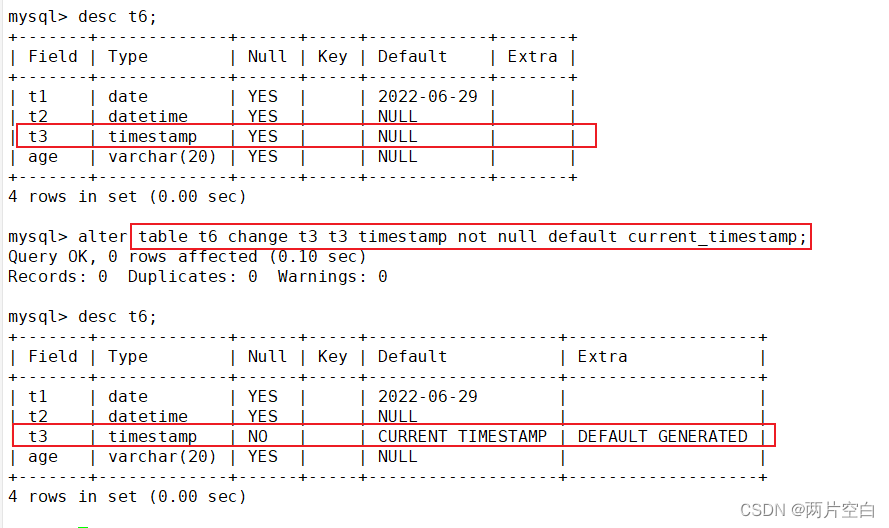
如何修改表中的字段约束条件(类型,default, null等)

How does technology have the ability to solve problems perfectly
![[optimization model] Monte Carlo method of optimization calculation](/img/e6/2865806ffbbfaa8cc07ebf625fcde6.jpg)
[optimization model] Monte Carlo method of optimization calculation
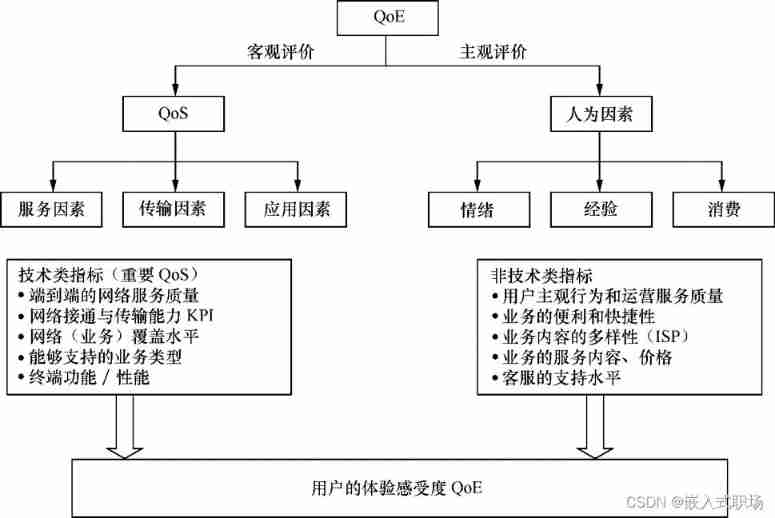
Factors affecting user perception
math_极限&微分&导数&微商/对数函数的导函数推导(导数定义极限法)/指数函数求导公式推导(反函数求导法则/对数求导法)
![Cf464e the classic problem [shortest path, chairman tree]](/img/6b/65b2dc62422a45cc72f287c38dbc58.jpg)
Cf464e the classic problem [shortest path, chairman tree]

MySQL master-slave replication

Ipv4中的A 、B、C类网络及子网掩码
【按键消抖】基于FPGA的按键消抖模块开发
Network security - Security Service Engineer - detailed summary of skill manual (it is recommended to learn and collect)
随机推荐
MySQL about self growth
ESP32(基于Arduino)连接EMQX的Mqtt服务器上传信息与命令控制
After five years of testing in byte, I was ruthlessly dismissed in July, hoping to wake up my brother who was paddling
Ybtoj coloring plan [tree chain dissection, segment tree, tarjan]
P7735-[noi2021] heavy and heavy edges [tree chain dissection, line segment tree]
C (XXIX) C listbox CheckedListBox Imagelist
Introduction to data types in MySQL
Record the pit of NETCORE's memory surge
Indicator system of KQI and KPI
Cf603e pastoral oddities [CDQ divide and conquer, revocable and search set]
在 .NET 6 中使用 Startup.cs 更简洁的方法
In Net 6 CS more concise method
Detailed explanation of serialization and deserialization
[analysis of variance] single factor analysis and multi factor analysis
Alibaba testers use UI automated testing to achieve element positioning
[FPGA tutorial case 11] design and implementation of divider based on vivado core
STC8H开发(十二): I2C驱动AT24C08,AT24C32系列EEPROM存储
MySql数据库root账户无法远程登陆解决办法
2.13 weekly report
Proof of Stirling formula