当前位置:网站首页>Check point: the core element for enterprises to deploy zero trust network (ztna)
Check point: the core element for enterprises to deploy zero trust network (ztna)
2022-07-07 06:01:00 【Netgoods world】
since 2020 Year begins , The outbreak of COVID-19 has led enterprises 、 Organizations have shifted to remote and hybrid working environments on a large scale , This greatly increases its attack surface and risk . meanwhile , Many companies are accelerating their cloud initiatives , To provide access to data and resources ; After the enterprise returns to work BYOD Policies allow employees to access company assets through home and personal devices ; Supply chain partners now also need remote access to information …… This series of changes undoubtedly provides criminals with all-round opportunities to attack , This is also one of the main drivers of the increasing number of cyber attacks in recent years .
up to now , Companies rely on Virtual Private Networks (VPN) And local based security methods to achieve secure remote access . Since the new crown , The limitations of these methods become more and more obvious . First VPN It is impossible to realize on-demand expansion in deployment , This makes it possible to BYOD And it is extremely difficult to implement installation and maintenance on partner equipment ; meanwhile , Deploy in hybrid cloud environment 、 Use VPN It's very complicated , Enterprises often need to face the impact of declining performance and flexibility ; Last VPN Most of the local security methods are not oriented DevOps And privileged access management of engineering users (PAM) function , Making their operation and maintenance costs very high .
therefore , Zero trust network access (ZTNA) Is becoming a key element of a standardized security architecture .ZTNA Model “ Never trust and always verify ”. In implementation ,ZTNA can :
• Restrict access according to specific applications ;
• Authenticate every device and user anytime, anywhere ;
• Well aware of today's complex network situation , Don't make any assumptions .
Gartner take ZTNA Defined as “ Products and services that can create identity based and context based logical access boundaries . The agent is verifying the identity of a specific participant 、 Access is allowed only after context and policy compliance , And it can minimize the horizontal movement of other positions in the network .”
As shown below ,Gartner The definition of separates the control layer from the data layer .
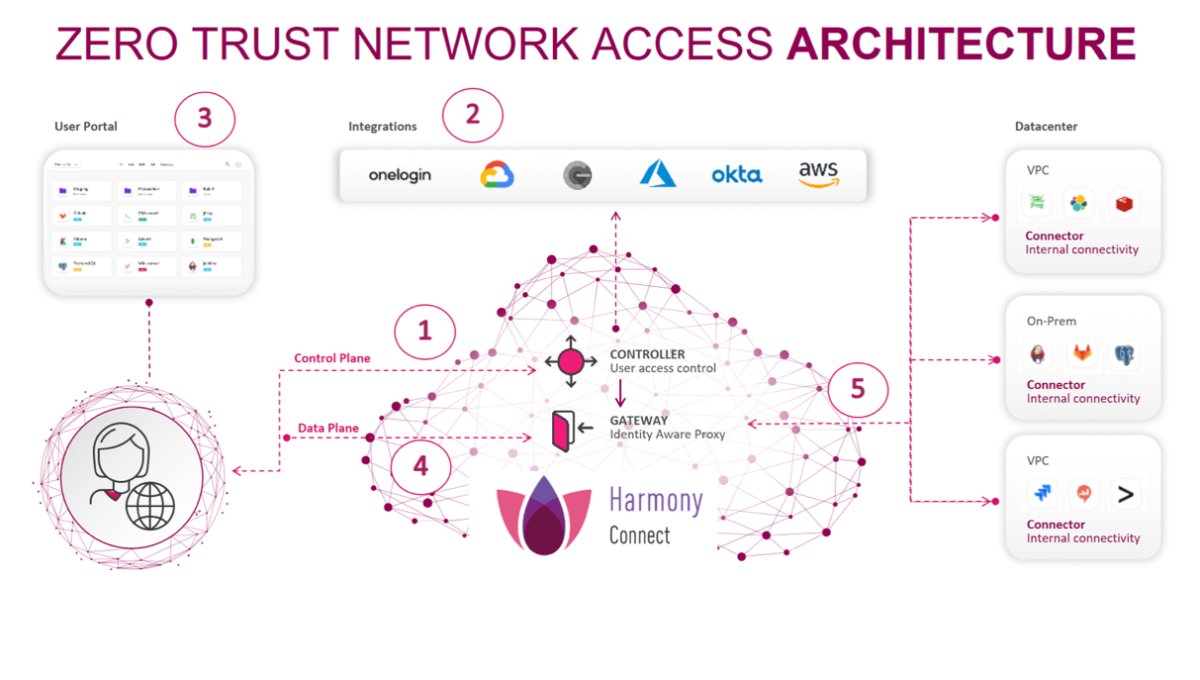
ZTNA not only VPN alternatives , It can also ensure that all users and devices inside and outside the institutional network are allowed or supported to access applications and data , Both have been authenticated and authorized, and have passed the continuous verification of security configuration and protection .
Choose the best ZTNA Solution
Check Point It is recommended to conduct environmental assessment for enterprises ZTNA When it comes to solutions , The following elements should be considered .
Ensure that all users are supported
The solution must ensure that employees 、 Third party partners 、 Engineering team and DevOps Users can safely access and use managed devices 、BYOD Devices and mobile devices . meanwhile , This scheme can support the secure access of employees using managed devices and no client architecture Web application 、 database 、 Remote desktop and security Shell (SSH) The server . For those who need to access the multi cloud environment and single sign on (SSO) To the server 、 A team of proprietary resources such as terminals and databases , Be sure to consider basic PAM requirement .
Ensure that all target resources are supported
Make sure ZTNA The solution supports all high priority proprietary applications and resources , Not just Web application . This includes visiting SSH terminal 、SQL database 、 Remote desktop (RDP) And servers .DevOps And engineering teams need zero trust access to infrastructure as a service (IaaS) product 、 Cloud production environment 、 Micro services and virtual private cloud .
Ensure easy operation
This plan needs to support enterprises without increasing personnel costs , Obtain maximum safety capability with minimum maintenance . meanwhile , This solution requires a cloud based solution with a unified console , Not only is it easy to use , And it can provide all ZTNA Visibility of use cases .
Ensure high performance and service availability
ZTNA Services must be provided close to 99.999% Uptime and meet service level agreements (SLA) A high performance . View the manufacturer's SLA standard , Look for global access points that support redundancy in each region (PoP) The Internet .
Ensure zero trust security and robustness
Look for ways to separate the control layer from the data layer ZTNA Solution , In order to really realize the minimum access to applications and other resources . The solution should provide fine-grained in application control , For example, read 、 write in 、 Manage permissions and support policy enforcement at the command and query levels . It can report groups by accessing video session records 、 User and application usage , Thus providing deep visibility . Other integrated security features also need to be checked , For example, Sandbox 、 cloud IPS and DLP.
Part of the edge of future oriented security services
Consider how to pass the edge of security services (SSE) take ZTNA The solution extends to other applications , For example, branch visits 、 Internet access 、 Proprietary applications . Protect remote ZTNA It is a key link in building a larger zero trust security architecture .
Why do you choose Check Point Harmony Connect The remote access
Check Point Harmony Connect Remote access can effectively protect the data center 、IaaS、 Access to any internal company application in the public cloud or private cloud . Easy to use , Can be found in 10 Deploy in minutes .
Harmony Connect Remote access can be implemented in the following two ways :• No client application level access : Through fine-grained application control, it will be intuitive ZTNA be applied to Web application 、 database 、 Remote desktop and SSH The server . Because there is no agent , Therefore, it is very suitable for protecting the remote access of employees' own devices and third-party partners . It can also be used for projects and projects that need rich cloud native automation functions DevOps The team provides secure access .
• Client based network level access : The VPN That is, the service option is very suitable for protecting employees' access through managed devices . It adds embedded cloud DLP And industry-leading IPS, It can protect applications from new vulnerabilities ( Such as Log4J) Influence .
边栏推荐
- Red Hat安装内核头文件
- An example of multi module collaboration based on NCF
- Message queuing: how to ensure that messages are not lost
- Loss function and positive and negative sample allocation in target detection: retinanet and focal loss
- 往图片添加椒盐噪声或高斯噪声
- [SQL practice] a SQL statistics of epidemic distribution across the country
- Polynomial locus of order 5
- Industrial Finance 3.0: financial technology of "dredging blood vessels"
- 云加速,帮助您有效解决攻击问题!
- cf:C. Column Swapping【排序 + 模拟】
猜你喜欢
PTA ladder game exercise set l2-004 search tree judgment
Randomly generate session_ id

毕业之后才知道的——知网查重原理以及降重举例
pytorch_ 01 automatic derivation mechanism
【SQL实战】一条SQL统计全国各地疫情分布情况
nVisual网络可视化
Harmonyos practice - Introduction to development, analysis of atomized services

How to improve website weight
Determine whether the file is a DICOM file
Jinfo of JVM command: view and modify JVM configuration parameters in real time
随机推荐
驱动开发中platform设备驱动架构详解
POI excel export, one of my template methods
[cloud native] what is the microservice architecture?
绕过open_basedir
Industrial Finance 3.0: financial technology of "dredging blood vessels"
Flask 1.1.4 werkzeug1.0.1 analyse du code source: processus de démarrage
SAP Spartacus checkout 流程的扩展(extend)实现介绍
[daily training -- Tencent selected 50] 292 Nim games
往图片添加椒盐噪声或高斯噪声
Things about data storage 2
Go language learning notes - Gorm use - Gorm processing errors | web framework gin (10)
Digital IC interview summary (interview experience sharing of large manufacturers)
Say sqlyog deceived me!
ML之shap:基于adult人口普查收入二分类预测数据集(预测年收入是否超过50k)利用shap决策图结合LightGBM模型实现异常值检测案例之详细攻略
Opensergo is about to release v1alpha1, which will enrich the service governance capabilities of the full link heterogeneous architecture
An example of multi module collaboration based on NCF
Convert numbers to string strings (to_string()) convert strings to int sharp tools stoi();
【日常训练--腾讯精选50】235. 二叉搜索树的最近公共祖先
Question 102: sequence traversal of binary tree
Why does the data center need a set of infrastructure visual management system