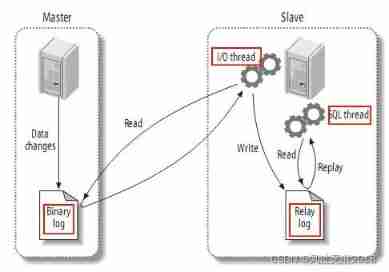
当前位置:网站首页>Master-slave replication principle of MySQL database
Master-slave replication principle of MySQL database
2022-07-04 06:57:00 【No trace after wind 2018】
边栏推荐
- Centos8 install mysql 7 unable to start up
- Chapter 1 programming problems
- Lottery system test report
- Google Chrome Portable Google Chrome browser portable version official website download method
- Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
- the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
- Responsive mobile web test questions
- 云Redis 有什么用? 云redis怎么用?
- tars源码分析之10
- MySQL 45 lecture learning notes (XIV) count (*)
猜你喜欢
《剑指Offer》第2版——力扣刷题
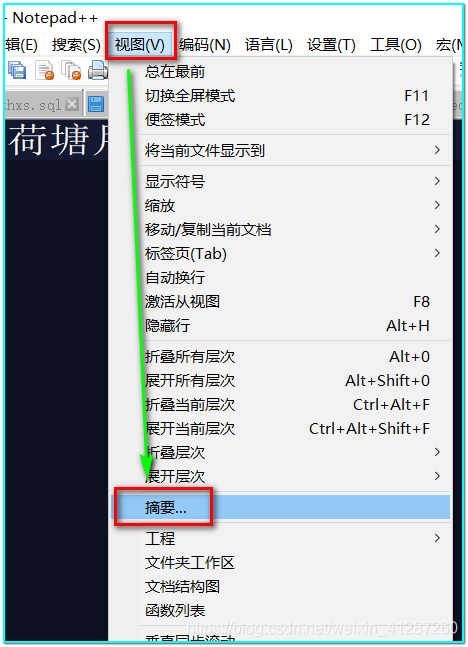
notepad++如何统计单词数量
校园网络问题
移动适配:vw/vh
Fundamentals of SQL database operation
【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
图的底部问题
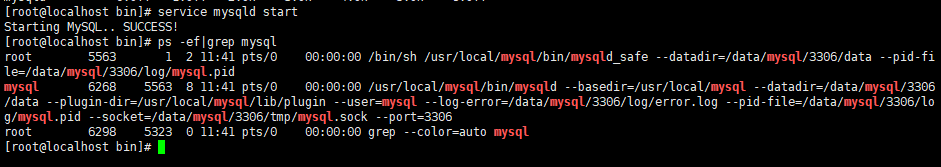
Centos8 install mysql 7 unable to start up
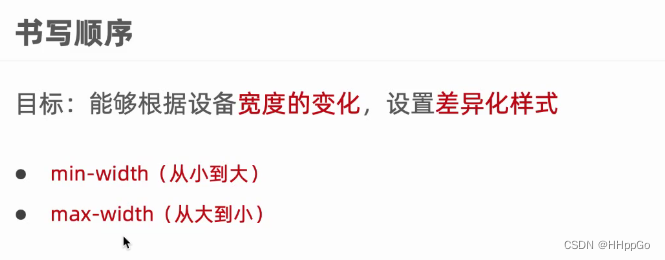
Responsive - media query

The cloud native programming challenge ended, and Alibaba cloud launched the first white paper on application liveliness technology in the field of cloud native
随机推荐
Modify TCP timestamp to optimize transmission performance
抽奖系统测试报告
Shopping malls, storerooms, flat display, user-defined maps can also be played like this!
Mysql 45讲学习笔记(十三)表数据删掉一半,表文件大小不变
Bottom problem of figure
Check and display one column in the known table column
Analysis of tars source code 1
Common usage of time library
Tar source code analysis 8
ABCD four sequential execution methods, extended application
Mysql 45讲学习笔记(十二)MySQL会“抖”一下
CMS source code of multi wechat management system developed based on thinkphp6, with one click curd and other functions
Crawler (III) crawling house prices in Tianjin
tars源码分析之6
Google Chrome Portable Google Chrome browser portable version official website download method
Summary of June 2022
Software keywords and process information intercepted by Golden Shield video player
What is industrial computer encryption and how to do it
About how idea sets up shortcut key sets
How can the old version of commonly used SQL be migrated to the new version?