当前位置:网站首页>[Li Kou 387] the first unique character in the string
[Li Kou 387] the first unique character in the string
2022-07-06 10:37:00 【Spring breeze ~ eleven years】
Title Description : Given a string s , find Its first non repeating character , And return its index . If it doesn't exist , Then return to -1 .
Example 1:
Input : s = “leetcode”
Output : 0
Example 2:
Input : s = “loveleetcode”
Output : 2
Example 3:
Input : s = “aabb”
Output : -1
Tips :
- 1 <= s.length <= 105
- s Contains only lowercase letters
Solution 1 :
We can define one map aggregate ,key Character ,value Is the number of occurrences , Traversal string , Put each character in turn , First count the number of times each character appears , Then traverse the original string to find the first character that appears once , Just return the subscript .
class Solution {
public int firstUniqChar(String s) {
if(s == null) return -1;
HashMap<Character,Integer> map = new HashMap<>();
for(char ch : s.toCharArray()) {
if(map.get(ch) == null) {
map.put(ch,1);
}else{
int count = map.get(ch);
map.put(ch,count+1);
}
}
for(int i = 0;i < s.length();i++) {
if(map.get(s.charAt(i)) == 1) {
return i;
}
}
return -1;
}
}
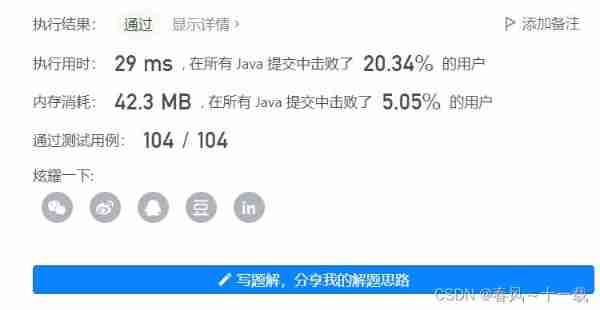
Solution 2 :
The second time we traverse the above method is the string , We can also traverse the hash map the second time , You only need to traverse all the values in the hash map once , Find out which is not -1 The minimum value of , That is, the index of the first non repeating character . If all values in the hash map are -1, We'll go back to -1, That is, there is no unique character
class Solution {
public int firstUniqChar(String s) {
Map<Character, Integer> position = new HashMap<Character, Integer>();
int n = s.length();
for (int i = 0; i < n; ++i) {
// First traversal string
char ch = s.charAt(i);
if (position.containsKey(ch)) {
position.put(ch, -1);
} else {
// When the string first appears
position.put(ch, i);
}
}
int m = n;
for (Map.Entry<Character, Integer> entry : position.entrySet()) {
// Traverse the hash map for the second time
int pos = entry.getValue();
if (pos != -1 && pos < m) {
m = pos;
}
}
if (m == n) {
// There is no unique character
m = -1;
}
return m;
}
}
边栏推荐
- text 文本数据增强方法 data argumentation
- 基于Pytorch肺部感染识别案例(采用ResNet网络结构)
- MySQL32-锁
- 数据库中间件_Mycat总结
- The appearance is popular. Two JSON visualization tools are recommended for use with swagger. It's really fragrant
- MySQL storage engine
- MySQL28-数据库的设计规范
- What is the current situation of the game industry in the Internet world?
- MySQL实战优化高手07 生产经验:如何对生产环境中的数据库进行360度无死角压测?
- MySQL實戰優化高手04 借著更新語句在InnoDB存儲引擎中的執行流程,聊聊binlog是什麼?
猜你喜欢
解决在window中远程连接Linux下的MySQL

Preliminary introduction to C miscellaneous lecture document
Mysql28 database design specification
![[Julia] exit notes - Serial](/img/d0/87f0d57ff910a666fbb67c0ae8a838.jpg)
[Julia] exit notes - Serial
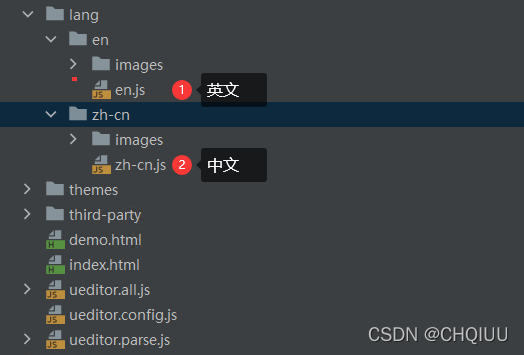
Ueeditor internationalization configuration, supporting Chinese and English switching
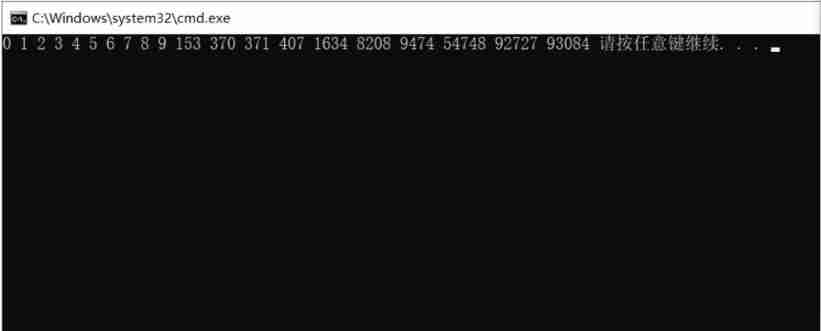
How to find the number of daffodils with simple and rough methods in C language
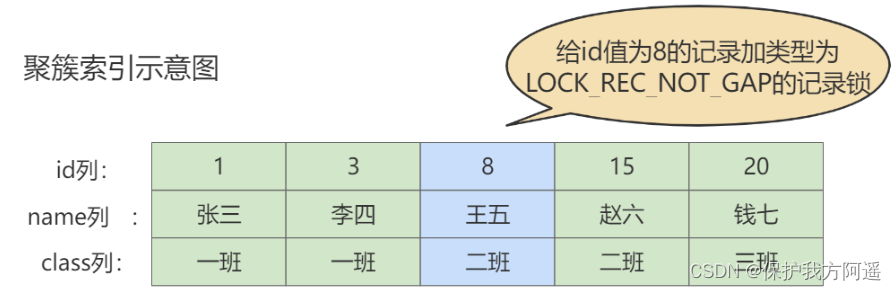
Mysql32 lock
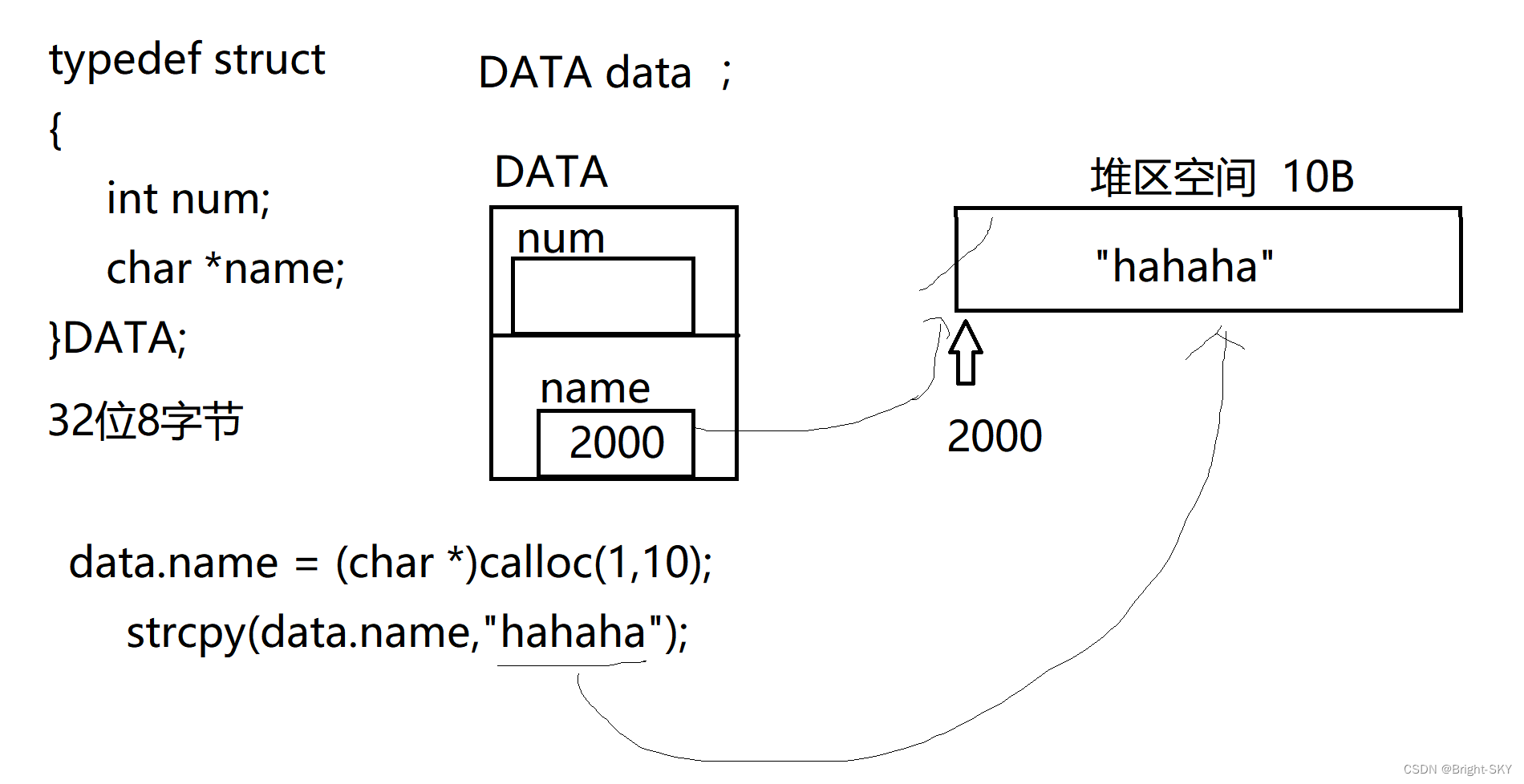
C miscellaneous shallow copy and deep copy
Nanny hand-in-hand teaches you to write Gobang in C language
Mysql36 database backup and recovery
随机推荐
MySQL23-存储引擎
使用OVF Tool工具从Esxi 6.7中导出虚拟机
解决在window中远程连接Linux下的MySQL
基于Pytorch的LSTM实战160万条评论情感分类
Time complexity (see which sentence is executed the most times)
Super detailed steps for pushing wechat official account H5 messages
MySQL27-索引优化与查询优化
Mysql27 index optimization and query optimization
[after reading the series] how to realize app automation without programming (automatically start Kwai APP)
Mysql23 storage engine
该不会还有人不懂用C语言写扫雷游戏吧
MySQL29-数据库其它调优策略
高并发系统的限流方案研究,其实限流实现也不复杂
Global and Chinese markets of static transfer switches (STS) 2022-2028: Research Report on technology, participants, trends, market size and share
Security design verification of API interface: ticket, signature, timestamp
MySQL30-事务基础知识
Transactions have four characteristics?
MySQL实战优化高手10 生产经验:如何为数据库的监控系统部署可视化报表系统?
评估方法的优缺点
Preliminary introduction to C miscellaneous lecture document