当前位置:网站首页>Gbase observation | how to protect the security of information system with frequent data leakage
Gbase observation | how to protect the security of information system with frequent data leakage
2022-07-08 01:41:00 【Gbase database】
In recent years, , With the evolution of new information technology represented by cloud services , Many users have begun to use new technology to build and transform the original information system , However, some users lack safety vigilance and specifications in the use process , Data leaks are common . Regarding this ,GBASE Information security experts say : For information systems with high security requirements , For example, classified information system 、 Information systems above level 3 specified in the requirements for security level protection of information systems 、 Core information system of pillar industries of national economy , And other information systems, which have high security requirements for data management , The database used , It is suggested to strengthen safety protection measures , Including data encryption 、 Comply with national information security standards and system security :
One 、 Data encryption
Data encryption is one of the most reliable methods to protect user data . Through data encryption 、 Storage encryption 、 Data integrity authentication 、 Key management and other technologies encrypt the information in the database , It can effectively protect the information security of users when they encounter dragging libraries , It can also prevent data from being compromised during storage and transmission .
The security database product should also support hardware quotient algorithm , Conform to the national security algorithm , Follow strictly 《 Code device application interface specification 》, By using the hardware password card that obtains the national password model certificate , It can effectively ensure the security of user passwords , Protect the confidentiality of stored data .
Two 、 Comply with national information security standards
Each component module of the information system ( For example, operating system 、 database 、 Middleware etc. ) Products that meet national safety standards must be used . Not because of a certain product ( For example, cloud services 、 Cloud database ) No security certificate , Make a compromise . In the field implementation , Physical isolation between ordinary data and sensitive data must be ensured , Especially when the unsafe business model of public cloud service is adopted .
Business system with high security level , High safety should be adopted 、 High performance 、 Highly available secure database products . Such database products should generally have 《 China national information security product certification certificate 》、 adopt 《 Password detection criteria for secure database products 》、 Issued by the State Password Administration 《 Commercial password product type certificate 》, Meet national confidentiality Standards 《 Technical requirements for information system security database products involving state secrets 》、《 Product inspection certificate of classified information system 》, Reach the national standard (GB/T 20273-2019 Information security technology Security technical requirements of database management system ) Level IV technical requirements .
Database products that conform to national information security standards should provide users with data transmission encryption 、 Storage encryption 、 Identification 、 Autonomous access control 、 Safety signs 、 Enforce access control 、 Security audit 、 Data integrity protection 、 Separation of powers 、 Inference control and other safety functions and means , So as to greatly improve the security of data , Protect the security of sensitive data of information system .
therefore , In the selection process of information construction database, we should choose database products that strictly comply with national security standards , Avoid the recurrence of such leaks .
3、 ... and 、 Security system
Last , The information system with high security requirements is in use , There must be a perfect safety management system to escort , Build a set of safety standard supervision and use process , Standardize personnel information security management , Improve personnel's awareness of information security , Undertake and earnestly perform the corresponding information security responsibilities of each post , It is the premise of the security of all information systems .
NTU general security database management system GBase 8s
GBase 8s It is independently developed by Nanjing University General Motors with high security 、 High performance 、 Highly available high-end secure database products . Is the first to get 《 China national information security product certification certificate 》 Secure database 、 First pass 《 Password detection criteria for secure database products 》 It has been issued by the State Password Administration 《 Commercial password product type certificate 》 Secure database 、 The first to meet the national confidentiality Standards 《 Technical requirements for information system security database products involving state secrets 》 And get 《 Product inspection certificate of classified information system 》 Secure database 、 And reach the national standard (GB/T 20273-2019 Information security technology Security technical requirements of database management system ) Level IV technical requirements .
GBase 8s Security database is mainly applicable to classified information systems 、 Information systems above level 3 specified in the requirements for security level protection of information systems 、 Core information system of pillar industries of national economy , And other information systems, which have high security requirements for data management .
GBase 8s The security database has been used in finance 、 energy 、 The government 、 traffic 、 It is widely used in the core business system of industry and other industries . The future will also bring new vitality to the industry , While providing security protection for sensitive data of various information systems , Provide more efficient access 、 More stable and reliable operation .
边栏推荐
- Guojingxin center "APEC investment +": some things about the Internet sector today | observation on stabilizing strategic industrial funds
- Redis master-slave replication
- 写一个纯手写的qt的hello world
- 2022 safety officer-c certificate examination paper and safety officer-c certificate simulated examination question bank
- A little experience from reading "civilization, modernization, value investment and China"
- QT build with built-in application framework -- Hello World -- use min GW 32bit
- Understanding of prior probability, posterior probability and Bayesian formula
- NPDP在国内有认可度吗?看一看就明白了!
- How does Matplotlib generate multiple pictures in turn & only save these pictures without displaying them in the compiler
- Understanding of maximum likelihood estimation
猜你喜欢
![Gnuradio operation error: error thread [thread per block [12]: < block OFDM_ cyclic_ prefixer(8)>]: Buffer too small](/img/ab/066923f1aa1e8dd8dcc572cb60a25d.jpg)
Gnuradio operation error: error thread [thread per block [12]: < block OFDM_ cyclic_ prefixer(8)>]: Buffer too small
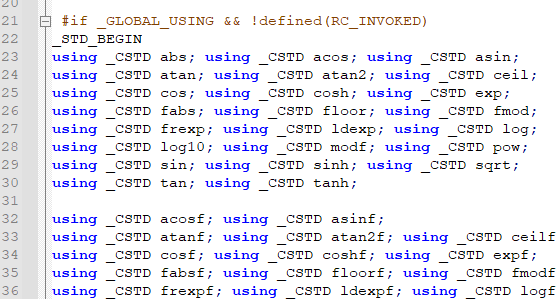
从cmath文件看名字是怎样被添加到命名空间std中的
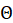
Understanding of maximum likelihood estimation
Android 创建的sqlite3数据存放位置
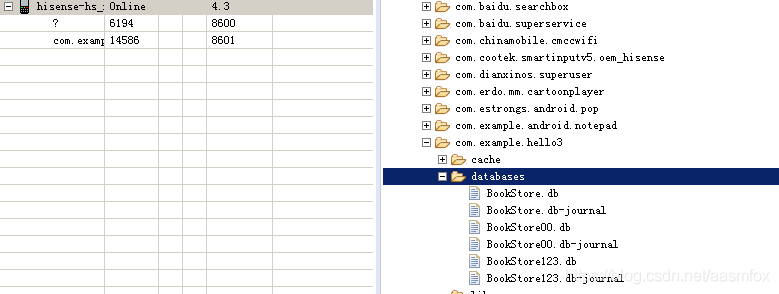
About snake equation (5)
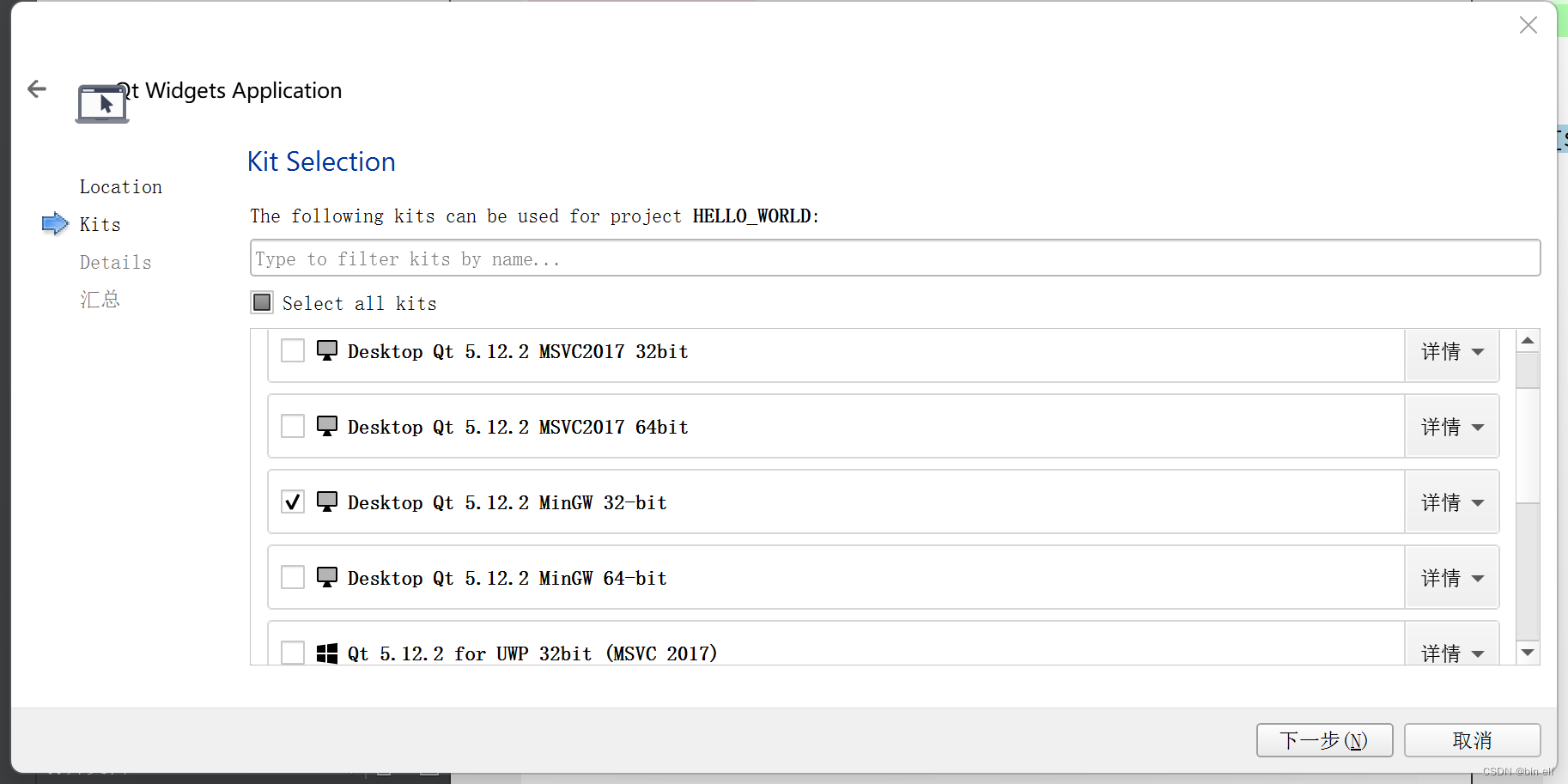
QT build with built-in application framework -- Hello World -- use min GW 32bit
qt--将程序打包--不要安装qt-可以直接运行

2022 safety officer-c certificate examination summary and safety officer-c certificate reexamination examination
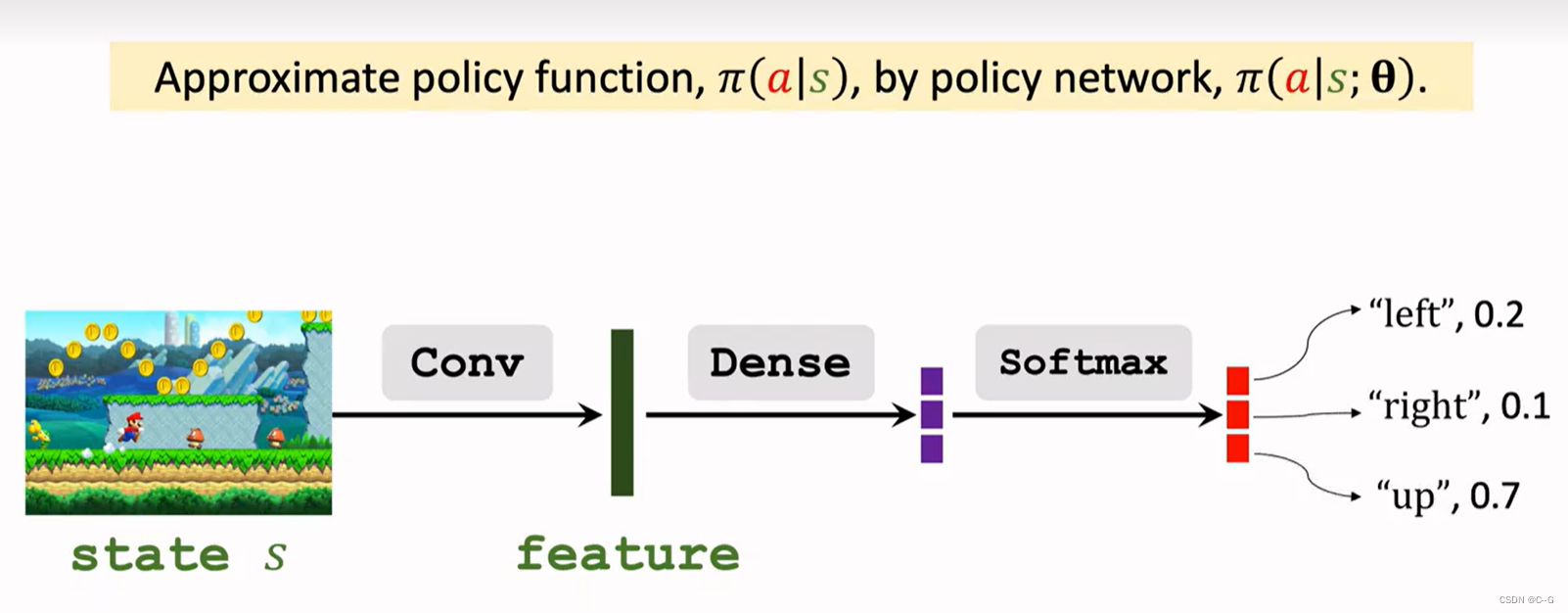
4. Apprentissage stratégique
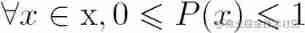
Probability distribution
随机推荐
4、策略学习
2022 operation certificate examination for main principals of hazardous chemical business units and main principals of hazardous chemical business units
2022 chemical automation control instrument examination summary and chemical automation control instrument simulation examination questions
Redis集群
Plot function drawing of MATLAB
项目经理有必要考NPDP吗?我告诉你答案
Mat file usage
Arm bare metal
用户之声 | 对于GBase 8a数据库学习的感悟
5. Discrete control and continuous control
4、策略學習
子矩阵的和
qt--将程序打包--不要安装qt-可以直接运行
2021 Shanghai safety officer C certificate examination registration and analysis of Shanghai safety officer C certificate search
Kafka-connect将Kafka数据同步到Mysql
Transportation, new infrastructure and smart highway
Gnuradio operation error: error thread [thread per block [12]: < block OFDM_ cyclic_ prefixer(8)>]: Buffer too small
小金额炒股,在手机上开户安全吗?
LeetCode 练习——剑指 Offer 36. 二叉搜索树与双向链表
About snake equation (1)