当前位置:网站首页>3、 High quality programming and performance tuning practical youth training camp notes
3、 High quality programming and performance tuning practical youth training camp notes
2022-07-07 07:28:00 【A low-key horse】
High quality programming and performance tuning | Youth Camp notes
This is my participation 「 The third youth training camp - Back end field 」 The third part of note creation activities 3 Notes
High quality principle :1、 simplicity 2、 Readability 3、 Productivity
Annotation specifications
Code is the best comment , Comments should provide context information that the code does not express , Common symbols should always be annotated
- Comments should explain what the code does
- Comments should explain how the code does
- Comments should explain why the code is implemented
- Comments should explain what goes wrong with the code
Naming specification
Variable naming
- Contains the amount of information about variable names
- It has a specific meaning
- Avoid passing in wrong values , Cause unexpected errors
Function name
Do not carry the context information of the package name
Be as brief as possible
eg:
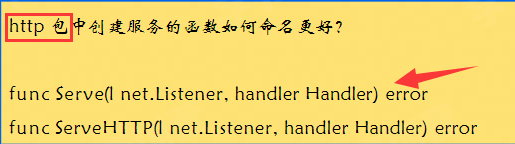
Package name naming
- It's just small letters . Does not contain characters such as uppercase letters and underscores
- Contains certain context information
- It does not have the same name as the standard library .
Coding standards
Control process
Avoid nesting
If if else Both branches of contain return sentence , Then redundant... Can be removed else Convenient for subsequent maintenance ,else Generally, it is a normal process , If it is necessary to add judgment logic in the normal process , Avoid branch nesting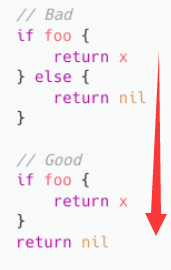
Prioritize errors and special situations , Return early or continue the loop to reduce nesting
Error and exception handling
Simple error
- priority of use errors.New To create anonymous variables to directly represent simple errors
- If there is a need for formatting , Use fmt.Errorf
Complex error (Wrap and Unwrap)
Wrap Provides a error Nest another error The ability of , To create a error Tracking chain
stay fmt.Errorf Use in :%w Keyword to associate an error to the error chain
Wrong judgment
Specific errors : Use errors.Is To determine whether it is a specific error . Different from using ==, Using this method, we can determine All errors in the error chain Whether there are specific errors
Certain kinds of errors : Get a specific kind of error on the error chain , Use errors.As
panic( Be careful ! I always use in projects )
Only for really abnormal situations
Not recommended ( When an irreversible error occurs during the start-up phase of the program , Can be in init or main Use in a function panic)
recover
recover Effective range , At present goroutine The quilt of defer The nesting that takes effect in the function of cannot take effect
defer The statement is last in, first out
The common situation is to record panic Call stack information , When problems occur, it is convenient to analyze and locate . If you need more context information , Sure recover In the after log Record the current call stack
performance optimization (Benchmark Tools )
slice Use advice
slice Pre allocated memory , Estimated space
- Try to use make() Provide capacity information when initializing slices , Avoid multiple expansions ( Because we need to open up a larger space in memory to store and copy , It's a waste )
- You can use copy Instead of creating a new slice( Avoid the huge space occupied by calling the original slice , The large memory of the original slice cannot be released )
map Use advice
Pre allocated memory , Estimated space , To reduce memory copies and Rehash Consume
string manipulation
Among the three string splicing methods ,strings.Builder The fastest ,bytes.Buffer secondly ,+ The slowest
When using + Splicing 2 A string , Generate a new string , We need to open up a new space , The size of the new space is the sum of the size of the original two strings . When splicing the third string , Open up a new space 、 The size of the new space is the sum of the sizes of the three strings , And so on
and strings.Builder,bytes.Buffer The bottom is []byte Array memory expansion strategy , There is no need to reallocate memory every time you splice
Empty structure
Empty structures do not occupy memory space , Can be used as a placeholder
- Realization Set, Consider using map Instead of
- For this scenario , Just use map Key , You don't need a value
- Even if it's going to be map Is set to bool type , Will occupy more 1 Byte space
atomic The difference between bag and lock
The lock is realized through the operating system , It's a system call
atomic The operation is realized by hardware , It's more efficient than a lock
sync.Mutex It should be used to protect a piece of logic , Not just to protect a variable
For non numeric operations , have access to atomic.Value, Can carry a interface{}
performance tuning
principle
- Rely on data, not speculation
- Locate the biggest bottleneck rather than the details
- Don't optimize too early
- Don't over optimize
Performance analysis tool pprof
do , have access to atomic.Value, Can carry a interface{}
performance tuning
principle
- Rely on data, not speculation
- Locate the biggest bottleneck rather than the details
- Don't optimize too early
- Don't over optimize
Performance analysis tool pprof
Official documents :https://blog.wolfogre.com/posts/go-ppof-practice/
边栏推荐
- 云备份项目
- 面试官:你都了解哪些开发模型?
- "Xiaodeng in operation and maintenance" meets the compliance requirements of gdpr
- 深度学习花书+机器学习西瓜书电子版我找到了
- Databinding exception of kotlin
- 二、并发、测试笔记 青训营笔记
- Kuboard无法发送邮件和钉钉告警问题解决
- $parent(获取父组件) 和 $root(获取根组件)
- Model application of time series analysis - stock price prediction
- How do I get the last part of a string- How to get the last part of a string?
猜你喜欢

Deep learning Flower Book + machine learning watermelon book electronic version I found
Outsourcing for three years, abandoned
Communication between non parent and child components
Basic process of network transmission using tcp/ip four layer model
計算機服務中缺失MySQL服務
普通测试年薪15w,测试开发年薪30w+,二者差距在哪?
关于二进制无法精确表示小数
Advanced level of C language (high level) pointer
机器人技术创新与实践旧版本大纲
Talk about seven ways to realize asynchronous programming
随机推荐
普通测试年薪15w,测试开发年薪30w+,二者差距在哪?
Apache AB stress test
Detailed explanation of neo4j installation process
Jesd204b clock network
Chinese and English instructions prosci LAG-3 recombinant protein
$parent (get parent component) and $root (get root component)
面试官:你都了解哪些开发模型?
FullGC问题分析及解决办法总结
Unity C function notes
外包幹了三年,廢了...
Nesting and splitting of components
1089: highest order of factorial
Pass parent component to child component: props
我理想的软件测试人员发展状态
Sqlmap tutorial (IV) practical skills three: bypass the firewall
At the age of 20, I got the ByteDance offer on four sides, and I still can't believe it
URP - shaders and materials - light shader lit
Communication between non parent and child components
Wechat applet full stack development practice Chapter 3 Introduction and use of APIs commonly used in wechat applet development -- 3.10 tabbar component (I) how to open and use the default tabbar comp
Reflection (II)