当前位置:网站首页>【指针】八进制转换为十进制
【指针】八进制转换为十进制
2022-07-06 09:24:00 【|光|】
要求
编一个函数,实现八进制转换为十进制。(用指针实现)
代码
/* * 该函数用来实现将一个八进制数转换为十进制数 * 八进制数以字符串方式存放在形参a所指向的一维字符数组中 * 请将计算得到的十进制数以函数值的方式返回 */
int oct_to_dec(char* a)
{
int d=0;
int i;
int k=strlen(a)-1;
for(i=0;i<20;i++)
{
if(a[i]=='\0')
{
break;
}
else
{
d = d + ((a[i]-48)*pow(8,k));
k--;
}
}
return d;
}
main函数
int main()
{
char a[20];
int n;
gets(a);
n = oct_to_dec(a);
printf("%d",n);
return 0;
}
测试
测试输入
1234
输出
668
边栏推荐
- 内网渗透之内网信息收集(四)
- Circular queue (C language)
- [err] 1055 - expression 1 of order by clause is not in group by clause MySQL
- XSS之冷门事件
- 内网渗透之内网信息收集(二)
- 攻防世界MISC练习区(gif 掀桌子 ext3 )
- Apache APIs IX has the risk of rewriting the x-real-ip header (cve-2022-24112)
- C language file operation
- Interpretation of iterator related "itertools" module usage
- Intranet information collection of Intranet penetration (2)
猜你喜欢
JDBC看这篇就够了
How does SQLite count the data that meets another condition under the data that has been classified once
sqqyw(淡然点图标系统)漏洞复现和74cms漏洞复现
![New version of postman flows [introductory teaching chapter 01 send request]](/img/0f/a41a39093a1170cc3f62075fd76182.jpg)
New version of postman flows [introductory teaching chapter 01 send request]

Only 40% of the articles are original? Here comes the modification method
1.支付系统
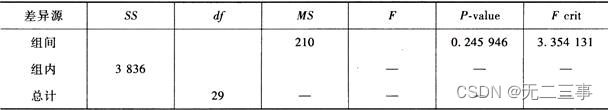
《统计学》第八版贾俊平第十章方差分析知识点总结及课后习题答案
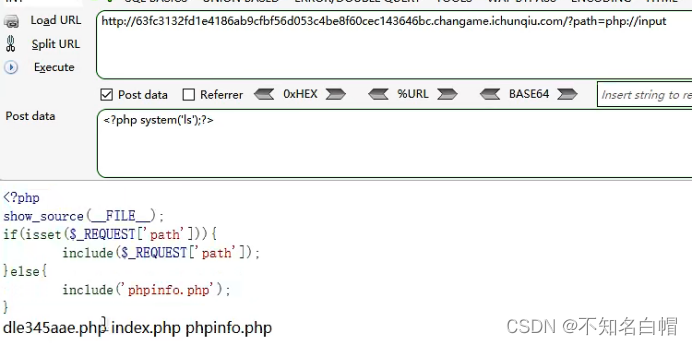
WEB漏洞-文件操作之文件包含漏洞
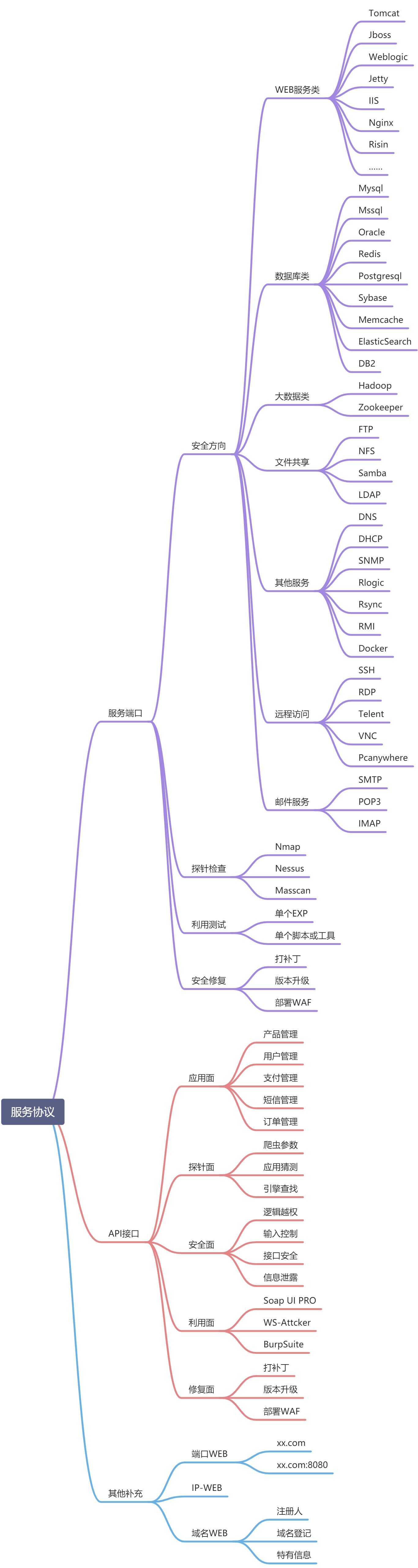
浅谈漏洞发现思路

Low income from doing we media? 90% of people make mistakes in these three points
随机推荐
msf生成payload大全
Binary search tree concept
Record an API interface SQL injection practice
Based on authorized access, cross host, and permission allocation under sqlserver
《英特尔 oneAPI—打开异构新纪元》
Sentinel overall workflow
《统计学》第八版贾俊平第十二章多元线性回归知识点总结及课后习题答案
Intranet information collection of Intranet penetration (5)
7-8 7104 Joseph problem (PTA program design)
Hackmyvm target series (3) -visions
Attack and defense world misc practice area (simplerar, base64stego, no matter how high your Kung Fu is, you are afraid of kitchen knives)
Interpretation of iterator related "itertools" module usage
WEB漏洞-文件操作之文件包含漏洞
Hcip -- MPLS experiment
JVM memory model concept
C language file operation
内网渗透之内网信息收集(二)
Xray and burp linkage mining
Intranet information collection of Intranet penetration (3)
XSS (cross site scripting attack) for security interview