当前位置:网站首页>The most popular colloquial system explains the base of numbers
The most popular colloquial system explains the base of numbers
2022-07-06 14:09:00 【Big talk code farmer】
A lot of friends , I don't know much about base , Today, let's talk about base , To understand hexadecimal, let's first think about a scenario , In ancient times , At the beginning, human beings had no concept of numbers , Every time I finish hunting , Just pile them together . Maybe one day, an ape man used his finger to represent a prey , After that, every time I came back from hunting, I would use my fingers to represent a prey , With more and more prey , He used up all his fingers and found that they could only represent ten prey , No amount of prey can be counted , This is after his hard thinking , Finally came up with this idea : That is, when ten fingers are used up , Just use a stick to replace the ten fingers of the hand just counted , This is the great invention of Radix , It's just that he didn't expect it to be a base , This is the decimal system , Later, ten wooden sticks were used , Using the same idea, use a larger stick to represent the just counted ten sticks , This has become a familiar , ten , Hundred bit .
But from the perspective of base, it is low , High position , High again .
This is to recall that our parents told us to count when we were young ,1 2 3 4 5 6 7 8 9 10
When I was a child, I always had a question why I had to count until 10, Looking back, it seems that our ancestors grew ten fingers :).
If it grows 8 A finger , Then we may count to 8 It stops .
边栏推荐
- It's never too late to start. The tramp transformation programmer has an annual salary of more than 700000 yuan
- sqqyw(淡然点图标系统)漏洞复现和74cms漏洞复现
- Get started with typescript
- 1. First knowledge of C language (1)
- Build domain environment (win)
- Strengthen basic learning records
- Implementation of count (*) in MySQL
- 7-4 散列表查找(PTA程序设计)
- 7-8 7104 Joseph problem (PTA program design)
- UGUI—Text
猜你喜欢
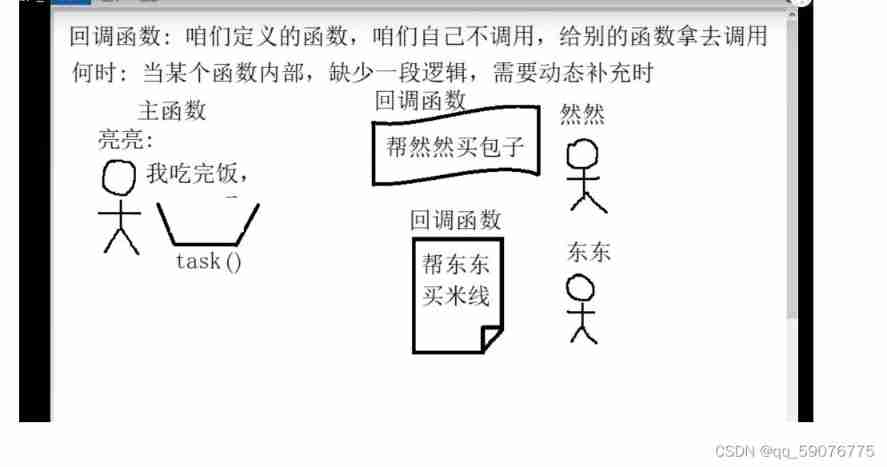
Callback function ----------- callback
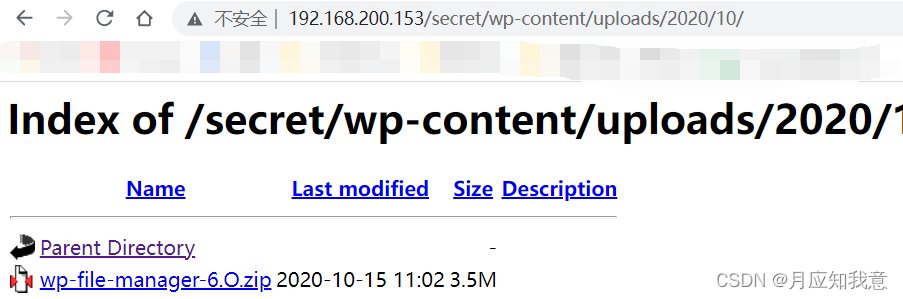
HackMyvm靶机系列(4)-vulny
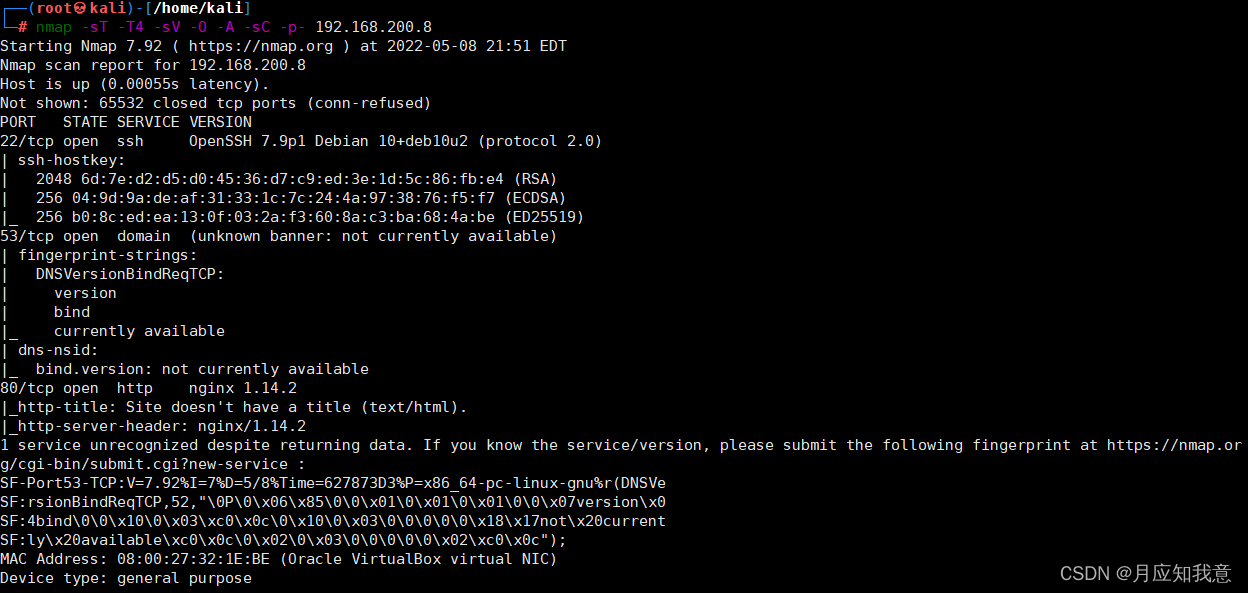
HackMyvm靶机系列(1)-webmaster
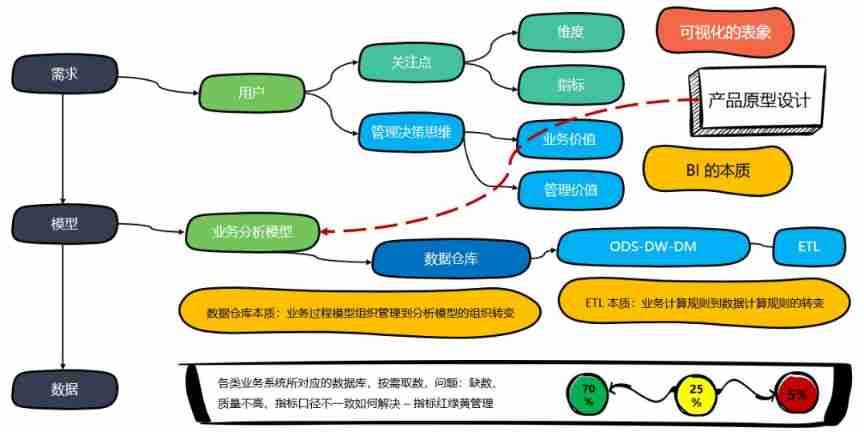
How to understand the difference between technical thinking and business thinking in Bi?
强化学习基础记录
SRC mining ideas and methods
内网渗透之内网信息收集(五)
Hackmyvm target series (5) -warez
Web vulnerability - File Inclusion Vulnerability of file operation
Nuxtjs quick start (nuxt2)
随机推荐
7-9 make house number 3.0 (PTA program design)
7-8 7104 Joseph problem (PTA program design)
Record a penetration of the cat shed from outside to inside. Library operation extraction flag
Brief introduction to XHR - basic use of XHR
Experiment 6 inheritance and polymorphism
MSF generate payload Encyclopedia
2. First knowledge of C language (2)
【educoder数据库实验 索引】
Build domain environment (win)
网络层—简单的arp断网
Beautified table style
HackMyvm靶机系列(1)-webmaster
Hackmyvm target series (3) -visions
内网渗透之内网信息收集(一)
记一次api接口SQL注入实战
Programme de jeu de cartes - confrontation homme - machine
2022 Teddy cup data mining challenge question C idea and post game summary
网络基础之路由详解
7-5 走楼梯升级版(PTA程序设计)
SQL injection