当前位置:网站首页>攻防世界MISC练习区(gif 掀桌子 ext3 )
攻防世界MISC练习区(gif 掀桌子 ext3 )
2022-07-06 09:23:00 【不知名白帽】
目录
gif
题目介绍
解题思路
打开附件


内容呈现黑白色,猜测可能为二进制数字,且一共104(0-103)张图片,我们假设白色为0,黑色为1,每8个一组进行ASCII解码。
ASCII解码
将图片转换成二进制数字
01100110 01101100 01100001 01100111 01111011 01000110 01110101 01001110 01011111 01100111 01101001 01000110 01111101
二进制转换成ASCII地址:https://coding.tools/cn/binary-to-text
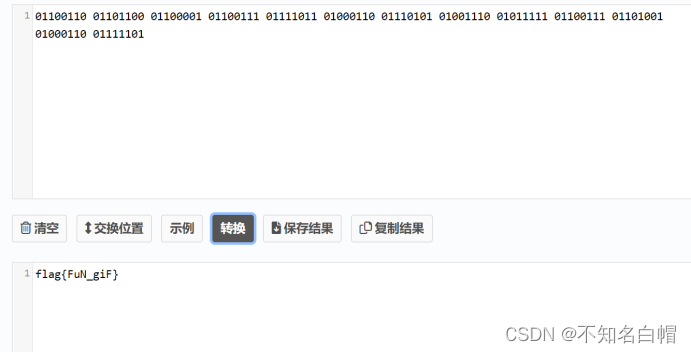
找到flag
flag{FuN_giF}
掀桌子
题目介绍
解题思路
对密文进行解码
c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2
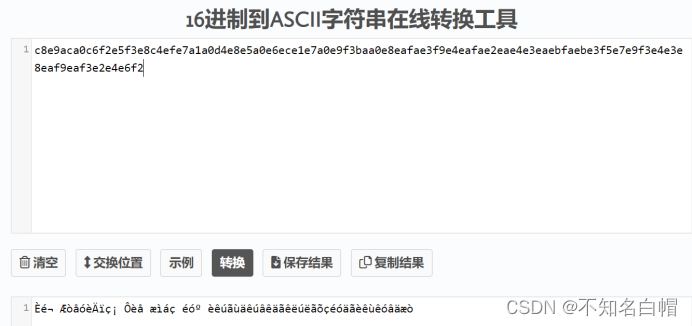
查看一下ASCII码表
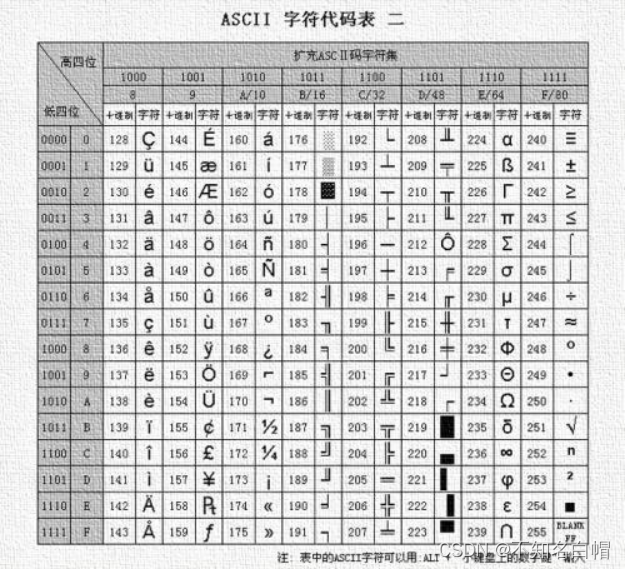
根据观察我们发现,得到的这一串很明显是128-255部分的。
于是我们考虑对得到的ascii码进行取余操作
对ASCII进行取余
flag = ''
s='c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2'
l = len(s)//2
for i in range(l):
flag += chr(int(s[i*2:(i+1)*2], 16) % 128)
print(flag, end='')python运行网址:https://c.runoob.com/compile/9/
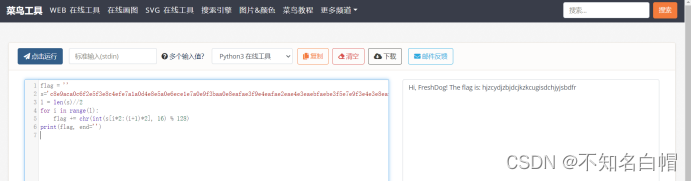
找到flag
flag{hjzcydjzbjdcjkzkcugisdchjyjsbdfr}
ext3
题目介绍
解题思路
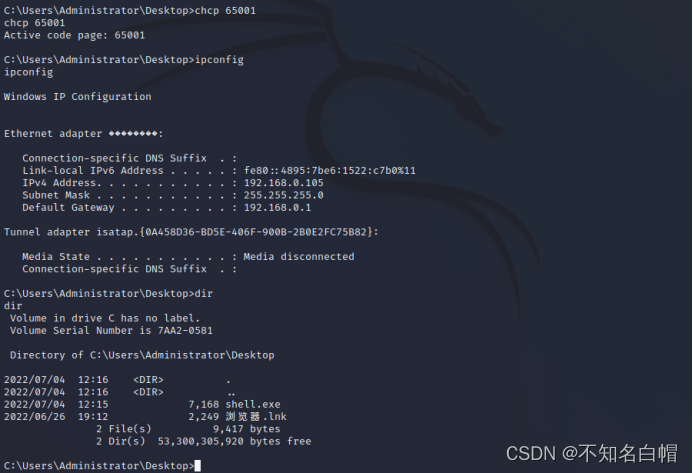
将目标文件放入kali中进行挂载
┌──(root㉿kali)-[~/Desktop]
└─# mkdir xctf-misc
┌──(root㉿kali)-[~/Desktop]
└─# ls
Burp_Suite_Pro_v2020.1.1 f1fc23f5c743425d9e0073887c846d23 vulhub xctf-misc
┌──(root㉿kali)-[~/Desktop]
└─# mount f1fc23f5c743425d9e0073887c846d23 xctf-misc/
┌──(root㉿kali)-[~/Desktop]
└─# cd xctf-misc
┌──(root㉿kali)-[~/Desktop/xctf-misc]
└─# ls
02CdWGSxGPX.bin 0wDq5 3J 7H7geLlS5 8RxQG4bvd h i jj LO0J8 m9V0lIaElz Nv orcA Q Raf3SYj sdb.cramfs T
0GY1l 0Xs 44aAm 8A2MFawD4 FinD H imgLDPt4BY KxEQM lost+found MiU o oSx2p qkCN8 rhZE1LZ6g sn TFGVOSwYd.txt
0h3a5 1 4A 8DQFirm0D fm H2Zj8FNbu ix1EMRHRpIc2 LG6F LvuGM Mnuc O7avZhikgKgbF OT QmUY1d Ruc9 SPaK8l2sYN
0l 2X 6JR3 8HhWfV9nK1 g hdi7 j6uLMX Lh lWIRfzP n o8 poiuy7Xdb QQY3sF63w RZTOGd SrZznhSAj
0qsd 3 6wUaZE1vbsW 8nwg gtj hYuPvID jE LlC6Z0zrgy.bin m NgzQPW OOoOs px6u r scripts t
┌──(root㉿kali)-[~/Desktop/xctf-misc]
└─# find / -name flag.txt
/root/Desktop/xctf-misc/O7avZhikgKgbF/flag.txt
┌──(root㉿kali)-[~/Desktop/xctf-misc]
└─# cd O7avZhikgKgbF
┌──(root㉿kali)-[~/Desktop/xctf-misc/O7avZhikgKgbF]
└─# ls
flag.txt
┌──(root㉿kali)-[~/Desktop/xctf-misc/O7avZhikgKgbF]
└─# cat flag.txt
ZmxhZ3tzYWpiY2lienNrampjbmJoc2J2Y2pianN6Y3N6Ymt6an0=
进行base64解码
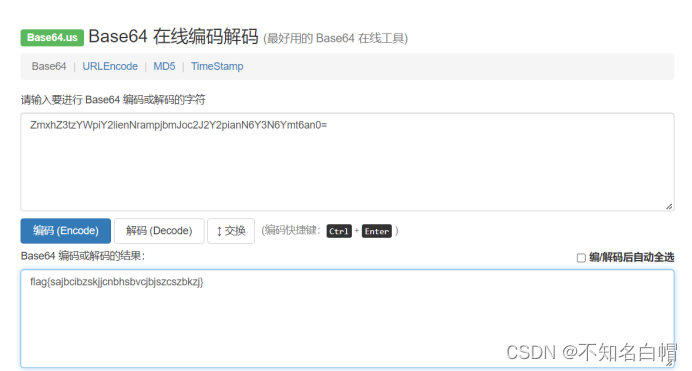
找到flag
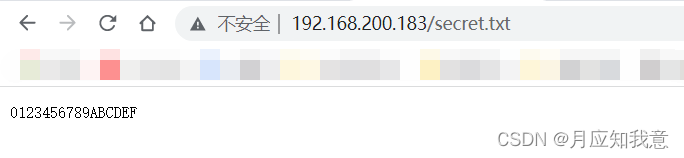
flag{sajbcibzskjjcnbhsbvcjbjszcszbkzj}
边栏推荐
- 7-1 输出2到n之间的全部素数(PTA程序设计)
- String ABC = new string ("ABC"), how many objects are created
- 7-7 7003 combination lock (PTA program design)
- FAQs and answers to the imitation Niuke technology blog project (II)
- 7-15 h0161. 求最大公约数和最小公倍数(PTA程序设计)
- [insert, modify and delete data in the headsong educator data table]
- HackMyvm靶机系列(6)-videoclub
- 力扣152题乘数最大子数组
- Experiment 7 use of common classes (correction post)
- 7-3 构造散列表(PTA程序设计)
猜你喜欢
HackMyvm靶机系列(4)-vulny
Differences among fianl, finally, and finalize
Renforcer les dossiers de base de l'apprentissage
Hackmyvm target series (7) -tron
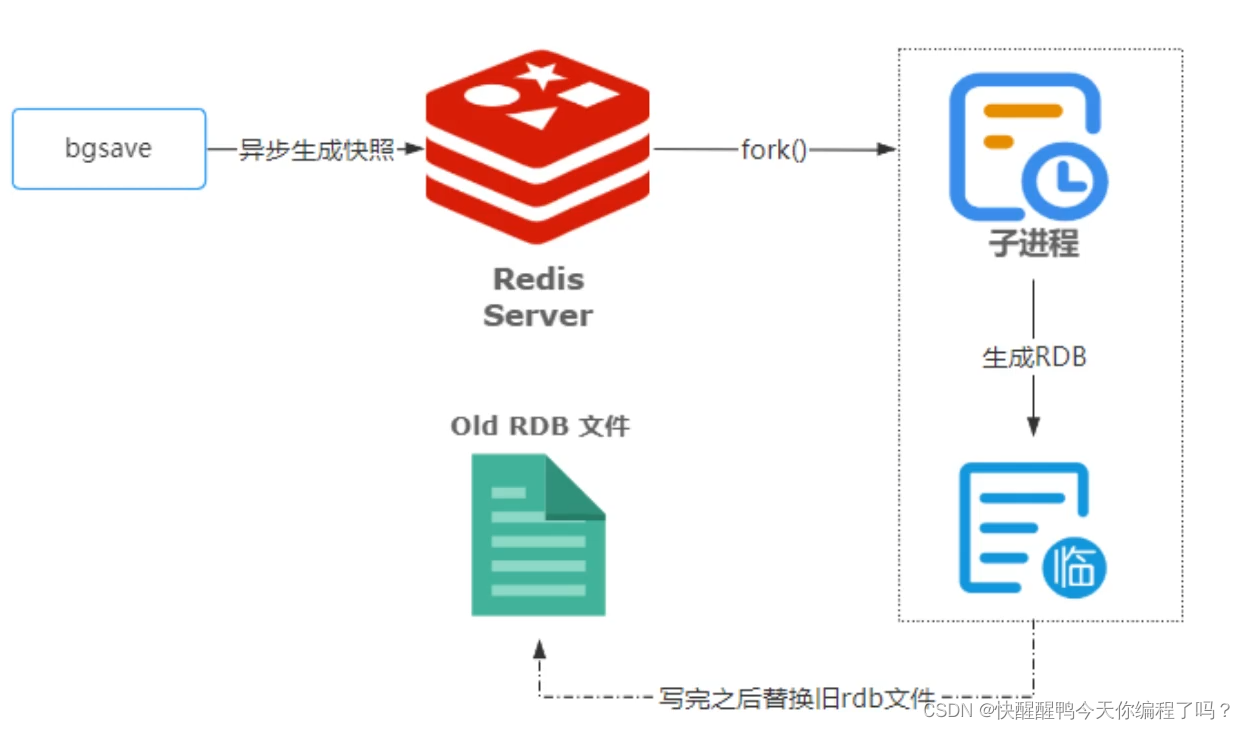
Principles, advantages and disadvantages of two persistence mechanisms RDB and AOF of redis
内网渗透之内网信息收集(一)
HackMyvm靶机系列(2)-warrior
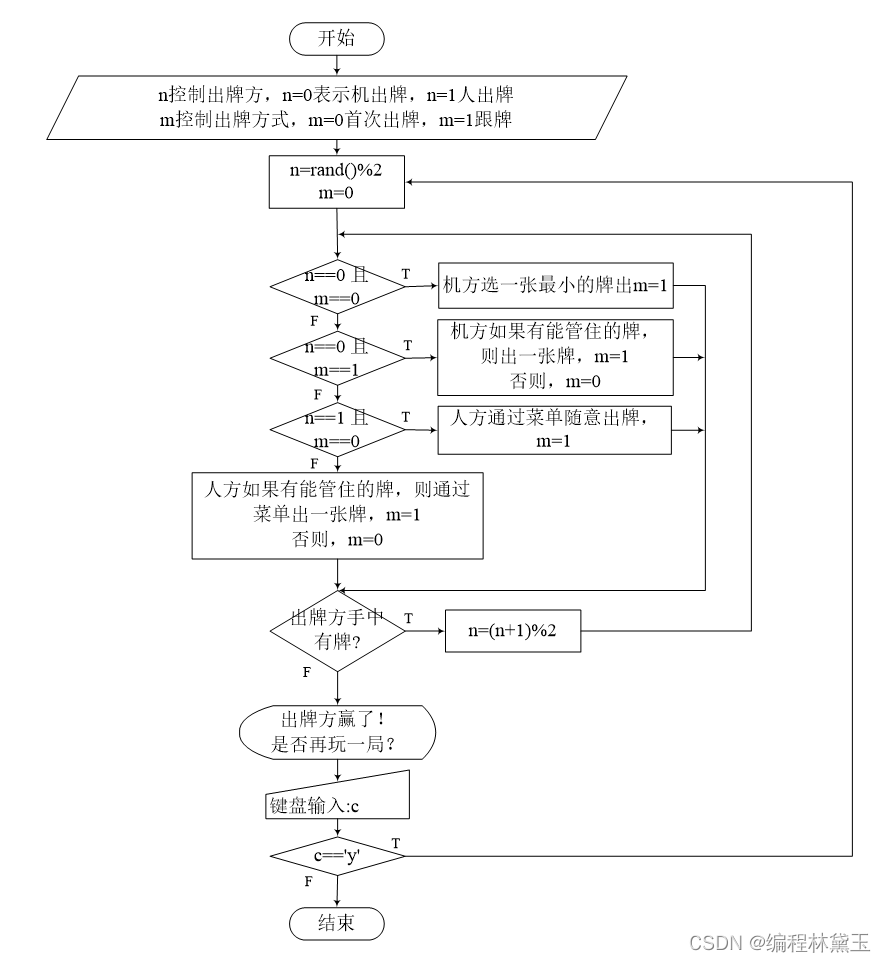
Poker game program - man machine confrontation
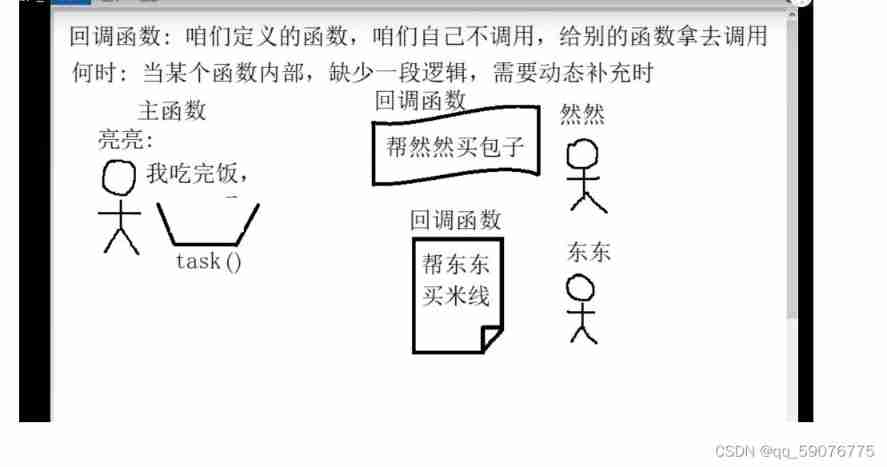
Callback function ----------- callback
FAQs and answers to the imitation Niuke technology blog project (II)
随机推荐
Wechat applet
7-7 7003 combination lock (PTA program design)
搭建域环境(win)
Hackmyvm target series (7) -tron
Nuxtjs快速上手(Nuxt2)
HackMyvm靶机系列(1)-webmaster
浅谈漏洞发现思路
Nuxtjs quick start (nuxt2)
TypeScript快速入门
【头歌educoder数据表中数据的插入、修改和删除】
7-7 7003 组合锁(PTA程序设计)
扑克牌游戏程序——人机对抗
Experiment 8 exception handling
网络基础之路由详解
Tencent map circle
7-15 h0161. 求最大公约数和最小公倍数(PTA程序设计)
.Xmind文件如何上传金山文档共享在线编辑?
(original) make an electronic clock with LCD1602 display to display the current time on the LCD. The display format is "hour: minute: Second: second". There are four function keys K1 ~ K4, and the fun
HackMyvm靶机系列(5)-warez
Why use redis