当前位置:网站首页>Three forms of multimedia technology commonly used in enterprise exhibition hall design
Three forms of multimedia technology commonly used in enterprise exhibition hall design
2022-07-07 18:46:00 【warm88】
The development of digital technology accelerates the transmission of information , It also makes the display more colorful , The design of enterprise exhibition hall has also become an important form of enterprise publicity , Next, let's walk into the enterprise exhibition hall , Learn about the common forms of multimedia technology !
One 、 Holographic display
Holographic projection is a technical form that can vividly display the three-dimensional model of products , For this reason, it is often included in the scheme of enterprise product display , Restore the product appearance through three-dimensional modeling , Help users understand the composition and structure of the product in the interaction .
Two 、 Slide screen
For many industrial enterprises , Their products are often complicated 、 There are many functions 、 There are many types , The enterprise exhibition hall often adopts the way of interactive slide screen , To introduce the product launch sequence , Let's introduce the changes of products , Users are interacting with interactive multimedia , It can strengthen the trust of products .
3、 ... and 、VR Virtual reality
As an interactive multimedia product with highly immersive experience , It often acts as the image of the scene builder in the planning scheme of the product exhibition hall , User pass VR technology , It can simulate the operation process of the product , Have a deeper understanding of the versatility of products , meanwhile VR Technology also adds more interest to the digital enterprise exhibition hall .
The above is the enterprise exhibition hall design https://www.heihuoshi.cn/cp/qyzt/ Three commonly used technical forms in , With the increase of interactive multimedia forms , The overall effect of the exhibition has also become more delicate and rich , We can also look forward to its subsequent development and changes .
边栏推荐
- 高考填志愿规则
- [principle and technology of network attack and Defense] Chapter 6: Trojan horse
- 云景网络科技面试题【杭州多测师】【杭州多测师_王sir】
- AntiSamy:防 XSS 攻击的一种解决方案使用教程
- Sports Federation: resume offline sports events in a safe and orderly manner, and strive to do everything possible for domestic events
- 手撕Nacos源码(先撕客户端源码)
- Learn to make dynamic line chart in 3 minutes!
- String type, constant type and container type of go language
- Classification of regression tests
- RIP和OSPF的区别和配置命令
猜你喜欢
随机推荐
Datasimba launched wechat applet, and datanuza accepted the test of the whole scene| StartDT Hackathon
[trusted computing] Lesson 13: TPM extended authorization and key management
Kirk borne's selection of learning resources this week [click the title to download directly]
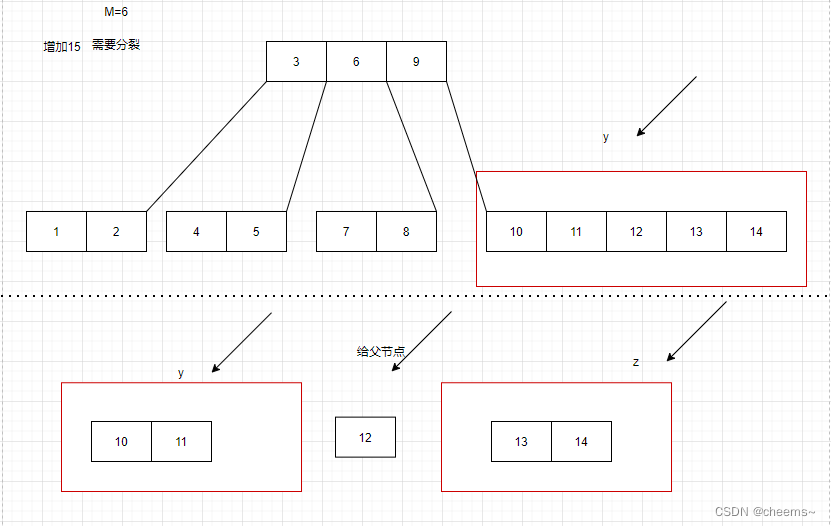
Disk storage chain B-tree and b+ tree
Wireshark分析抓包数据*.cap
idea彻底卸载安装及配置笔记
[principle and technology of network attack and Defense] Chapter 7: password attack technology Chapter 8: network monitoring technology
Chapter 3 business function development (safe exit)
磁盘存储链式的B树与B+树
CVPR 2022 - learning non target knowledge for semantic segmentation of small samples
Improve application security through nonce field of play integrity API
上市十天就下线过万台,欧尚Z6产品实力备受点赞
“解密”华为机器视觉军团:华为向上,产业向前
元宇宙带来的创意性改变
AI 击败了人类,设计了更好的经济机制
String type, constant type and container type of go language
【软件测试】从企业版BOSS直聘,看求职简历,你没被面上是有原因的
What is the general yield of financial products in 2022?
Summary of debian10 system problems
[principle and technology of network attack and Defense] Chapter 6: Trojan horse
![[trusted computing] Lesson 13: TPM extended authorization and key management](/img/96/3089e80441949d26e39ba43306edeb.png)