当前位置:网站首页>How to use FRP intranet penetration +teamviewer to quickly connect to the intranet host at home when mobile office
How to use FRP intranet penetration +teamviewer to quickly connect to the intranet host at home when mobile office
2022-07-05 16:13:00 【yuanfan2012】
How to use mobile office frp Intranet through +teamviewer Way to quickly connect to the intranet host at home
I wrote it before Deploy on Tencent virtual machine FRP+Teamviewer Penetrate the intranet for remote operation and maintenance
This paper makes further optimization based on this article
One 、 Scene description
As shown in the figure
( Click to enlarge the picture )
There is one at home 24 It's on in hours NUC
The operating system is VMware ESXi7.0 Virtualization platform
The following virtual machines are deployed above
( Click to enlarge the picture )
among CentOS7.9 Deployed on the virtual machine frpc Intranet penetration client
Put the intranet Win7 virtual machine (192.168.31.239) Of Teamviewer( Port is 5938) Tencent cloud server mapped to the public network
frpc And frps Screenshot of configuration section
( Click to enlarge the picture )
( Click to enlarge the picture )
At this time, if you need a laptop to work outside, you want to pass Teamviewer Visit home intranet Win7 virtual machine Need a virtual machine firewalld to open up 5938 port
You need to enter a command
firewall-cmd --permanent --zone=public --add-port=5938/tcp
firewall-cmd --reload
Then the virtual machine security group is also released 5938 port
( Click to enlarge the picture )
In this way, the notebook working outside is ready at any time , Only Teamviewer Connect to the virtual machine public network IP You can visit your home Win7 virtual machine
( Click to enlarge the picture )
( Click to enlarge the picture )
Two 、 Safety considerations
But for safety reasons : Security group 0.0.0.0 Too big , Worried about security risks
So at this time, I want to realize that only the public network of the current laptop network is allowed IP Join in 5938 Port security group white list
But in this way, you have to log in to the ECS console and manually whiten it every time , The operation is too troublesome , And it takes time and effort , It is estimated that 2~3 More than minutes
So I think of a relatively safe way
1、 The security group on the cloud console remains 5938 port allow 0.0.0.0/0 Security group rules for
2、 Has been removed public zone Globally open 5938 port
firewall-cmd --permanent --zone=public --remove-port=5938/tcp
firewall-cmd --reload
3、 adopt firewalld Of rich-rule To achieve whitening
SSH After logging in who am i View the exit public network of the current notebook IP
And put this public network IP Use rich-rule Add white
[[email protected] ~]# who am i
root pts/1 2022-06-19 20:04 (XX.XX.XX.XX)
[[email protected] ~]#
[[email protected] ~]# firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="XX.XX.XX.XX" port port="5938" protocol="tcp" accept'
success
[[email protected] ~]# firewall-cmd --reload
success
( Click to enlarge the picture )
3、 ... and 、 The optimization process
Can you shorten the time of the above steps ? For example, I work outside the notebook SSH Log in to ECs and execute a script, and it will be automatically whitened , Is this more convenient
By constantly modifying and repeatedly testing the script , This effect is finally achieved
The script is as follows
[[email protected] ~]# vim teamviewer_add_loginIP.sh
[[email protected] ~]# cat teamviewer_add_loginIP.sh
#!/bin/bash
# eliminate Teamviewer_5938 Port history rich-rules And overloading
firewall-cmd --list-rich-rules| grep 5938 > /tmp/5938_richrules.txt
while read -r line
do
Temp_Rule=`echo $line`
echo $Temp_Rule
firewall-cmd --permanent --remove-rich-rule "$Temp_Rule"
firewall-cmd --reload
done < /tmp/5938_richrules.txt
# Get the current login server IP Address , And for the current IP Add open Teamviewer5938 Port of rich-rule
LoginIP=$(who am i | awk '{print $5}' | sed 's/(//g' | sed 's/)//g')
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address='$LoginIP' port port="5938" protocol="tcp" accept'
firewall-cmd --reload
( Click to enlarge the picture )
Four 、 verification
stay MacOS How to use it under the system
1、iTerm2 Log in to ECS SSH( Key free login )
2、 Execute the script teamviewer_add_loginIP.sh
3、 Straight through Teamviewer Connect to the ECS public network IP, You can connect to your home Win7 virtual machine Time consuming 10 Less than a second
边栏推荐
- Fundamentals of data communication - Principles of IP routing
- Use of set tag in SQL
- sql中查询最近一条记录
- Record the pits encountered in the raspberry pie construction environment...
- Exception com alibaba. fastjson. JSONException: not match : - =
- 企业级备份软件Veritas NetBackup(NBU) 8.1.1服务端的安装部署
- 我们为什么要学习数学建模?
- Transaction rollback exception
- obj解析为集合
- ES6深入—ES6 Class 类
猜你喜欢
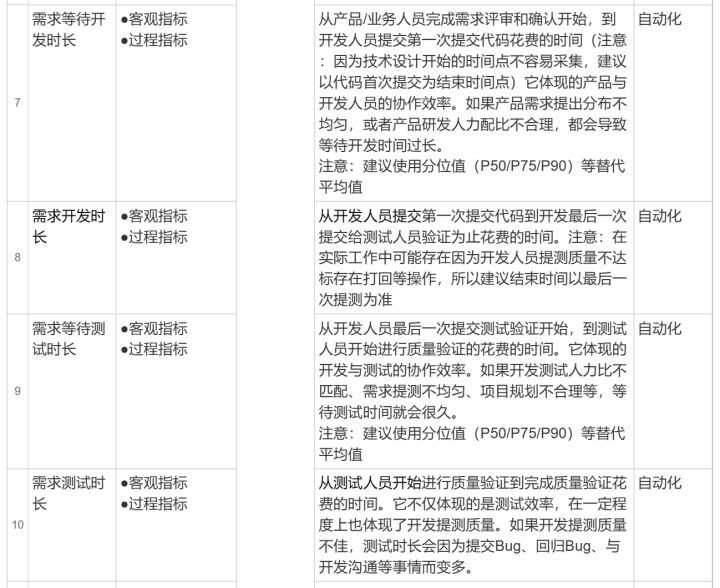
研发效能度量指标构成及效能度量方法论
Appium automation test foundation - appium basic operation API (II)
ES6深入—ES6 Generator 函数
ES6 deep - ES6 class class

超分辨率技术在实时音视频领域的研究与实践
ES6深入—async 函数 与 Symbol 类型
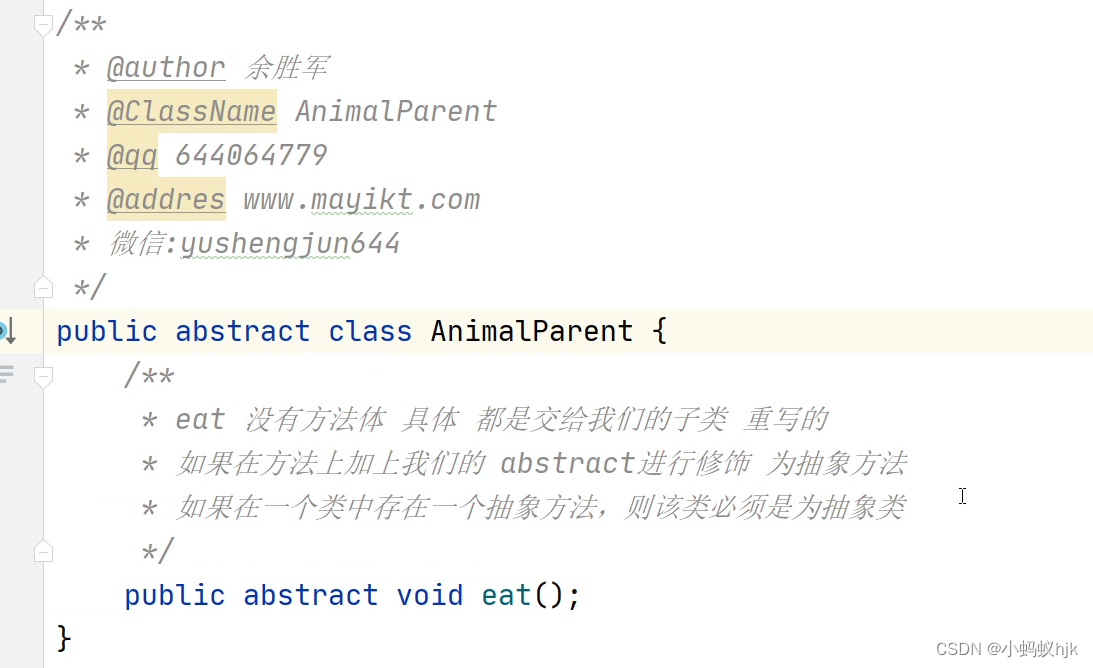
Subclasses and superclasses of abstract classes
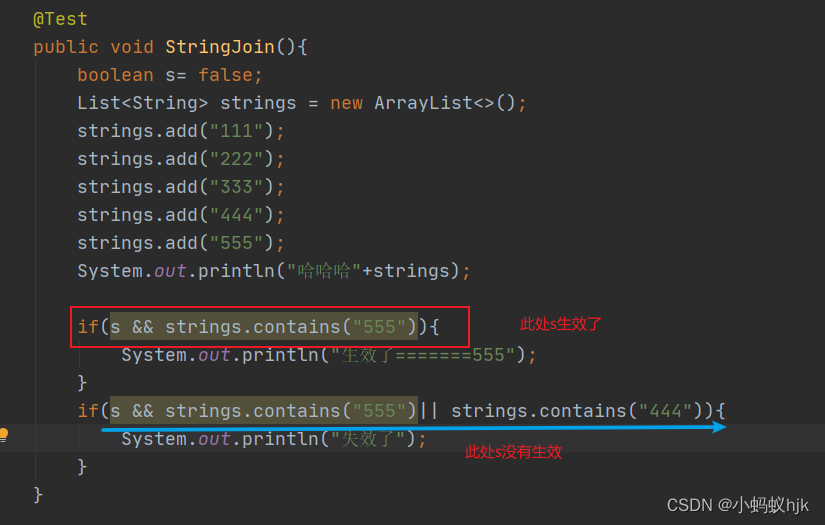
开发中Boolean类型使用遇到的坑
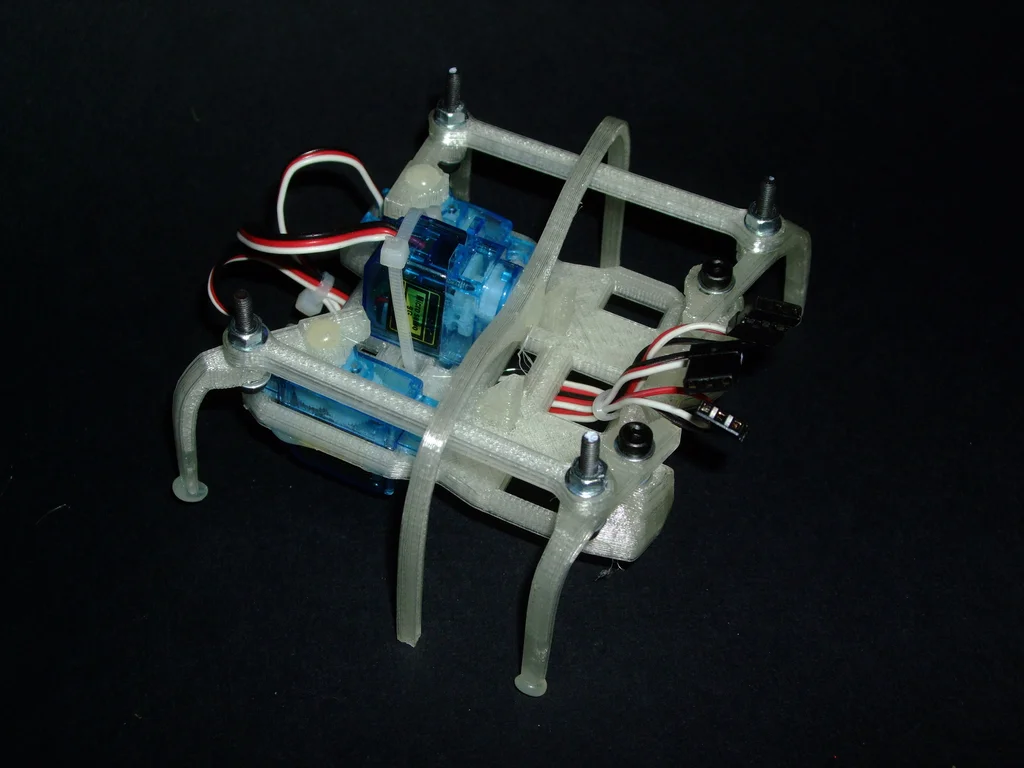
Arduino controls a tiny hexapod 3D printing robot
项目sql中批量update的时候参数类型设置错误
随机推荐
写单元测试的时候犯的错
OceanBase社区版之OBD方式部署方式本地安装
19.[STM32]HC_SR04超声波测距_定时器方式(OLED显示)
数据湖(十四):Spark与Iceberg整合查询操作
CODING DevSecOps 助力金融企业跑出数字加速度
【毕业季】作为一名大二计科在校生,我有话想说
Noi / 1.4 07: collect bottle caps to win awards
CISP-PTE之SQL注入(二次注入的应用)
利用GrayLog告警功能实现钉钉群机器人定时工作提醒
ES6深入—ES6 Class 类
DataArts Studio数据架构——数据标准介绍
Data communication foundation OSPF Foundation
How difficult is it to pass the certification of Intel Evo 3.0? Yilian technology tells you
Interval DP (gravel consolidation)
The difference between abstract classes and interfaces
vulnhub-Root_ this_ box
开发中Boolean类型使用遇到的坑
Dataarts studio data architecture - Introduction to data standards
效果编辑器新版上线!3D渲染、加标注、设置动画,这次一个编辑器就够了
The list set is summed up according to a certain attribute of the object, the maximum value, etc