当前位置:网站首页>Binary search template
Binary search template
2022-07-05 05:42:00 【A big pigeon】
author :labuladong
link :https://leetcode-cn.com/problems/binary-search/solution/er-fen-cha-zhao-xiang-jie-by-labuladong/
source : Power button (LeetCode)
Give a binary search template , Include : Binary search target value , Left boundary , Right border .
(Java and Python edition )
It's easy to find the target value directly ,
nums[mid]<target, Compress left left = mid +1
nums[mid]>target, Compress right right = mid -1
nums[mid]==target , return mid
Find the first two parts of the left boundary, similar to , but nums[mid]==target Continue to compress the right boundary , Lock left boundary , Finally, return to the left boundary . Pay attention to handling cross-border situations .
Finding the right boundary is the same as .
int binary_search(int[] nums, int target) {
int left = 0, right = nums.length - 1;
while(left <= right) {
int mid = left + (right - left) / 2;
if (nums[mid] < target) {
left = mid + 1;
} else if (nums[mid] > target) {
right = mid - 1;
} else if(nums[mid] == target) {
// Go straight back to
return mid;
}
}
// Go straight back to
return -1;
}
int left_bound(int[] nums, int target) {
int left = 0, right = nums.length - 1;
while (left <= right) {
int mid = left + (right - left) / 2;
if (nums[mid] < target) {
left = mid + 1;
} else if (nums[mid] > target) {
right = mid - 1;
} else if (nums[mid] == target) {
// Don't go back , Lock the left border
right = mid - 1;
}
}
// Finally, check left The situation of crossing the border
if (left >= nums.length || nums[left] != target)
return -1;
return left;
}
int right_bound(int[] nums, int target) {
int left = 0, right = nums.length - 1;
while (left <= right) {
int mid = left + (right - left) / 2;
if (nums[mid] < target) {
left = mid + 1;
} else if (nums[mid] > target) {
right = mid - 1;
} else if (nums[mid] == target) {
// Don't go back , Lock the right border
left = mid + 1;
}
}
// Finally, check right The situation of crossing the border
if (right < 0 || nums[right] != target)
return -1;
return right;
}
class Solution:
def binary_search(self,nums: List[int], target: int) -> int:
left, right = 0, len(nums) - 1
while left <= right:
mid = left + (right - left) // 2
if nums[mid] < target:
left = mid + 1
elif nums[mid] > target:
right = mid - 1
elif nums[mid] == target:
return mid
return -1
def left_bound(self,nums: List[int], target: int) -> int:
left, right = 0, len(nums) - 1
while left <= right:
mid = left + (right - left) // 2
if nums[mid] < target:
left = mid + 1
elif nums[mid] > target:
right = mid - 1
elif nums[mid] == target:
right = mid -1
if left >= len(nums) or nums[left] != target:
return -1
return left
def right_bound(self,nums: List[int], target: int) -> int:
left, right = 0, len(nums) - 1
while left <= right:
mid = left + (right - left) // 2
if nums[mid] < target:
left = mid + 1
elif nums[mid] > target:
right = mid - 1
elif nums[mid] ==target:
left = mid + 1
if right < 0 or nums[right] != target:
return -1
return right边栏推荐
- Individual game 12
- Demonstration of using Solon auth authentication framework (simpler authentication framework)
- Bit mask of bit operation
- Web APIs DOM node
- Pointnet++ learning
- 【Jailhouse 文章】Look Mum, no VM Exits
- On-off and on-off of quality system construction
- Introduction to convolutional neural network
- On the characteristics of technology entrepreneurs from Dijkstra's Turing Award speech
- Solution to game 10 of the personal field
猜你喜欢
Light a light with stm32
【Jailhouse 文章】Jailhouse Hypervisor
Graduation project of game mall
Web APIs DOM node
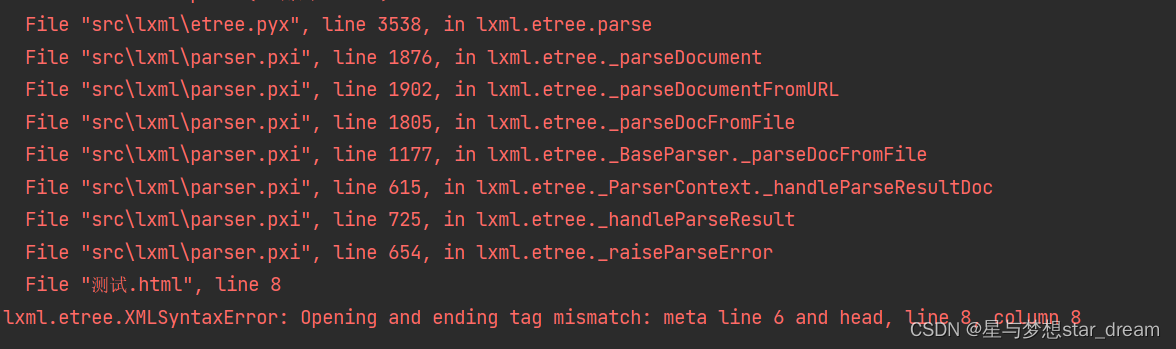
lxml.etree.XMLSyntaxError: Opening and ending tag mismatch: meta line 6 and head, line 8, column 8
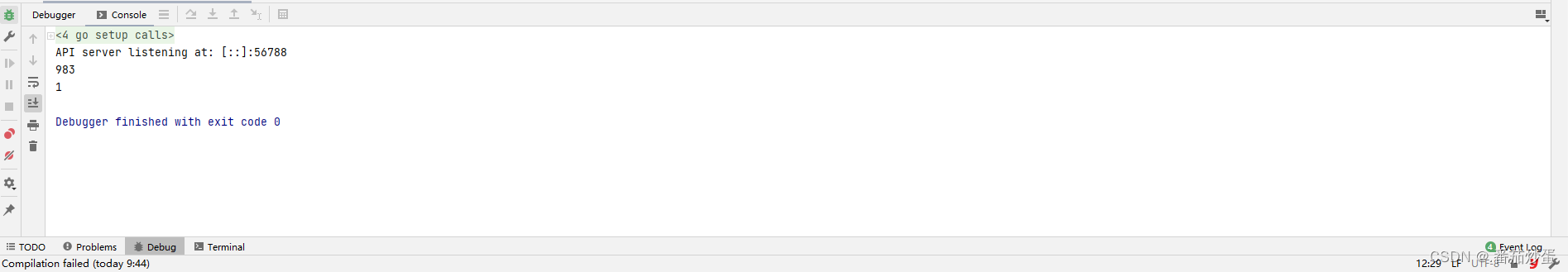
sync. Interpretation of mutex source code

智慧工地“水电能耗在线监测系统”
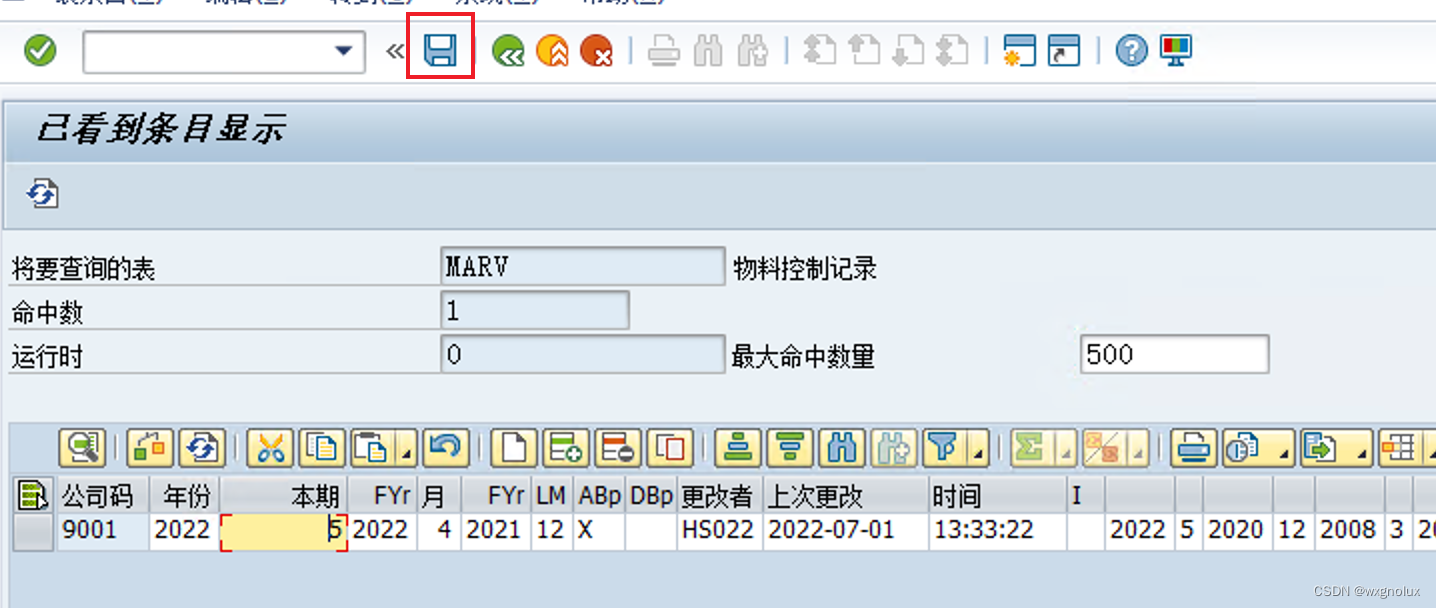
SAP-修改系统表数据的方法
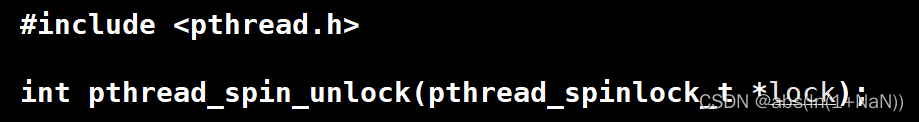
挂起等待锁 vs 自旋锁(两者的使用场合)
How to adjust bugs in general projects ----- take you through the whole process by hand
随机推荐
[article de jailhouse] jailhouse hypervisor
Daily question 2013 Detect square
Kubedm series-00-overview
全国中职网络安全B模块之国赛题远程代码执行渗透测试 //PHPstudy的后门漏洞分析
kubeadm系列-01-preflight究竟有多少check
软件测试 -- 0 序
Implement a fixed capacity stack
Some common problems in the assessment of network engineers: WLAN, BGP, switch
Hang wait lock vs spin lock (where both are used)
Drawing dynamic 3D circle with pure C language
Dichotomy, discretization, etc
剑指 Offer 04. 二维数组中的查找
Sword finger offer 04 Search in two-dimensional array
每日一题-无重复字符的最长子串
[jailhouse article] look mum, no VM exits
使用Electron开发桌面应用
PC register
Support multi-mode polymorphic gbase 8C database continuous innovation and heavy upgrade
The number of enclaves
Mysql database (I)