当前位置:网站首页>Fundamentals of face recognition (facenet)
Fundamentals of face recognition (facenet)
2022-07-02 13:05:00 【Konjaku in the east wind】
List of articles
Main ideas for reference :
- FaceNet The paper :FaceNet: A Unified Embedding for Face Recognition and Clustering
- Wu Enda video
- Keras bosses
Face verification VS Face recoginition
For face verification , We can regard it as a binary classification problem , But face recognition has developed to the present , We still use face recognition to solve .
Encoder
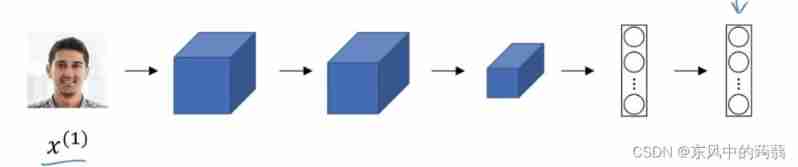
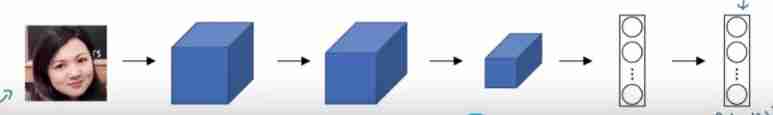
- We enter a picture into encoder, Through a series of Networks , Output a unique password , This string of passwords compiles this person .
- When we compare , Pass the current picture through encoder Code to get a string of passwords , Compare this string of passwords with all the passwords in the database . If f ( k e y , k e y i d a t a b a s e ) ≤ α f(key,key_{i_{database}}) \leq\alpha f(key,keyidatabase)≤α, We think this person is the person in the database .
Triplet Loss
That's the question : How do we train this network (Encoder)?

We divide the data into three groups .
( A n c h o r , P o s i t i v e , N e g a t i v e ) A n c h o r surface in I People Need to be want knowledge other Of this individual people , P o s i t i v e surface in The people Of another One Zhang chart slice , N e g a t i v e surface in another One individual people Of chart slice . (Anchor,Positive,Negative)\\ Anchor Indicates the person we need to identify ,Positive Another picture of the person \\,Negative A picture of another person . (Anchor,Positive,Negative)Anchor surface in I People Need to be want knowledge other Of this individual people ,Positive surface in The people Of another One Zhang chart slice ,Negative surface in another One individual people Of chart slice .
I People set The righteous T r i p l e t L o s s : M a x ( ∣ ∣ ( k e y A n c h o r ) − ( k e y P o s i t i v e ) ∣ ∣ − ∣ ∣ ( k e y A n c h o r ) − ( k e y N e g a t i v e ) ∣ ∣ + α , 0 ) We define Triplet Loss:\\ Max(||(key_{Anchor}) - (key_{Positive})|| -||(key_{Anchor})\\ - (key_{Negative})|| + \alpha ,0) I People set The righteous TripletLoss:Max(∣∣(keyAnchor)−(keyPositive)∣∣−∣∣(keyAnchor)−(keyNegative)∣∣+α,0)
We are optimizing Encoder When , We need different photos of the same person Encoder The compiled key The gap should be as small as possible , At the same time, I hope that the pictures of different people will be compiled key The gap should be as big as possible .
As for the neural network in the middle , You can write your own , You can even use the previous image classification VGG perhaps ConvNet.
边栏推荐
- Linear DP acwing 902 Shortest editing distance
- Oracle从入门到精通(第4版)
- C#修饰符
- C#运算符
- Wechat official account payment prompt MCH_ ID parameter format error
- Js6day (search, add and delete DOM nodes. Instantiation time, timestamp, timestamp cases, redrawing and reflow)
- Browser storage scheme
- Floyd AcWing 854. Floyd finds the shortest path
- spfa AcWing 851. SPFA finding the shortest path
- LTC3307AHV 符合EMI标准,降压转换器 QCA7005-AL33 PHY
猜你喜欢
Execute any method of any class through reflection

线性DP AcWing 896. 最长上升子序列 II

Async/await asynchronous function

阿里初面被两道编程题给干掉,再次内推终上岸(已拿电子offer)

Counter attack of flour dregs: MySQL 66 questions, 20000 words + 50 pictures in detail! A little six

Heap acwing 838 Heap sort
![[opencv learning] [template matching]](/img/4c/7214329a34974c59b4931c08046ee8.jpg)
[opencv learning] [template matching]
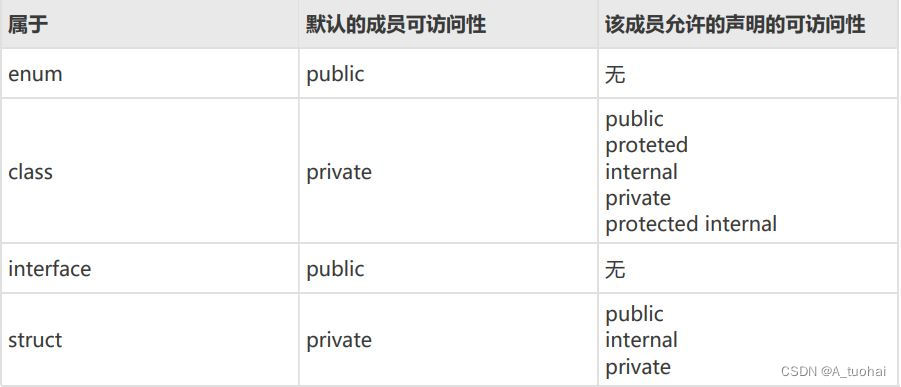
C modifier

West digital decided to raise the price of flash memory products immediately after the factory was polluted by materials
Redis sentinel mechanism and configuration
随机推荐
Should I have a separate interface assembly- Should I have a separate assembly for interfaces?
基于STM32的OLED 屏幕驱动
js4day(DOM开始:获取DOM元素内容,修改元素样式,修改表单元素属性,setInterval定时器,轮播图案例)
spfa AcWing 851. SPFA finding the shortest path
线性DP AcWing 896. 最长上升子序列 II
Js1day (syntaxe d'entrée / sortie, type de données, conversion de type de données, Var et let différenciés)
Use MySQL events to regularly perform post seven world line tasks
Linear DP acwing 895 Longest ascending subsequence
Counting class DP acwing 900 Integer partition
Window10 upgrade encountered a big hole error code: 0xc000000e perfect solution
Rust language document Lite (Part 1) - cargo, output, basic syntax, data type, ownership, structure, enumeration and pattern matching
Five best software architecture patterns that architects must understand
. Net, C # basic knowledge
Js10day (API phased completion, regular expression introduction, custom attributes, filtering sensitive word cases, registration module verification cases)
Redis sentinel mechanism and configuration
Post order traversal sequence of 24 binary search tree of sword finger offer
Day4 operator, self increasing, self decreasing, logical operator, bit operation, binary conversion decimal, ternary operator, package mechanism, document comment
NTMFS4C05NT1G N-CH 30V 11.9A MOS管,PDF
[opencv learning] [Canny edge detection]
Js3day (array operation, JS bubble sort, function, debug window, scope and scope chain, anonymous function, object, Math object)