当前位置:网站首页>Attack and defense world ----- summary of web knowledge points
Attack and defense world ----- summary of web knowledge points
2022-07-07 12:23:00 【hcjtn】
WEB
One . The way of web page source code
Add... Before the address bar view-source, Such as view-source:https://www.baidu.com
Use developer tools in the browser's settings menu box , You can also view the web page source code .
Two . robots(robtos.txt)
robots It's the agreement between the website and the crawler , Use simple and direct txt The format text mode tells the corresponding crawler the permission allowed , in other words robots.txt It's the first file to view when visiting a website in a search engine . When a search spider visits a site , It will first check if the root directory of the site exists robots.txt, If there is , The search robot will follow the contents of the file to determine the scope of access ; If the file does not exist , All search spiders will be able to access all pages on the site that are not password protected .( Baidu )
3、 ... and . http Two request methods of
- get- Request data from specified resources . eg(/?a=1)
- post- Submit the data to be processed to the specified resource .
| get | post | |
|---|---|---|
| Back button / Refresh | harmless | The data will be resubmitted ( The browser should inform the user that the data will be resubmitted ). |
| Bookmarks | Can be bookmarked | Can't be bookmarked |
| cache | Can be cached | Can't cache |
| The encoding type | application/x-www-form-urlencoded | application/x-www-form-urlencoded or multipart/form-data. Use multiple encoding for binary data . |
| history | Parameters remain in browser history . | Parameters are not saved in browser history . |
| Restrictions on data length | Yes . When sending data ,GET Method direction URL Add data ;URL The length of is limited (URL The maximum length of is 2048 Characters ). | unlimited . |
| Restrictions on data types | Only ASCII character . | There is no limit to , Binary data is also allowed . |
| Security | And POST comparison ,GET It's not safe , Because the data sent is URL Part of . Never use... When sending passwords or other sensitive information GET ! | POST Than GET More secure , Because parameters are not saved in browser history or web In the server log . |
according to HTTP standard ,POST Represents a request that may modify resources on a variable server ,GET For information acquisition , And it should be safe and idempotent .
- Differences in the transmission process ,
Let's take a look first HTTP Form of agreement :
HTTP request :
<request line> //http Request line
<headers> //http Request message header
<blank line> // return vehicle Line break
[<request-body>] //http Request body
difference
(1)GET Submit , The requested data is attached URL after ( Is to put the data in the HTTP Protocol header ), With ? Division URL And transmit data , Multiple parameters with & Connect ; example Such as :login.action?
POST Submit : Place the submitted data in yes HTTP In the package .
therefore ,get The submitted data will be displayed in the address ,post The address bar will not change
(2) Transfer data size :
get Specific browsers and servers have requirements for device length .
post each WEB The server will say yes post Limit the size of the submitted data .
(3) Security :
post Safety ratio get High safety .
Four ,backup
File suffix bck.
explain :
full: Full backup
incremental: Incremental backup
level: Level backup
backup_type: Backup object
5、 ... and ,cookie
- Cookie It's a plain text file saved on the client side . When we visit a web page through a browser , The server will generate a certificate and return it to my browser and write it to our local computer . This certificate is cookie. Generally speaking cookie All are plain text files written by the server to the client .
6、 ... and ,simple_js
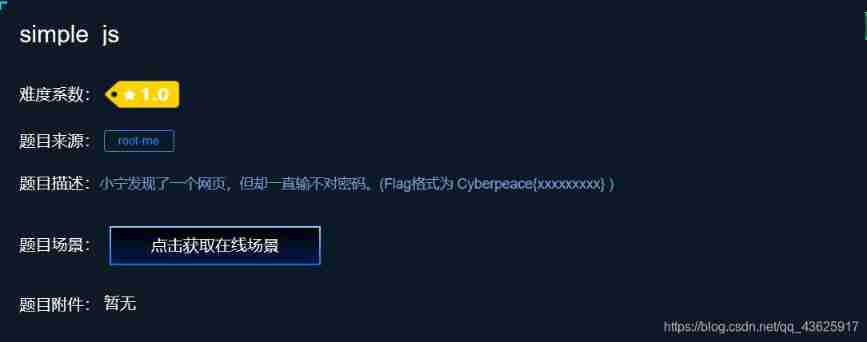
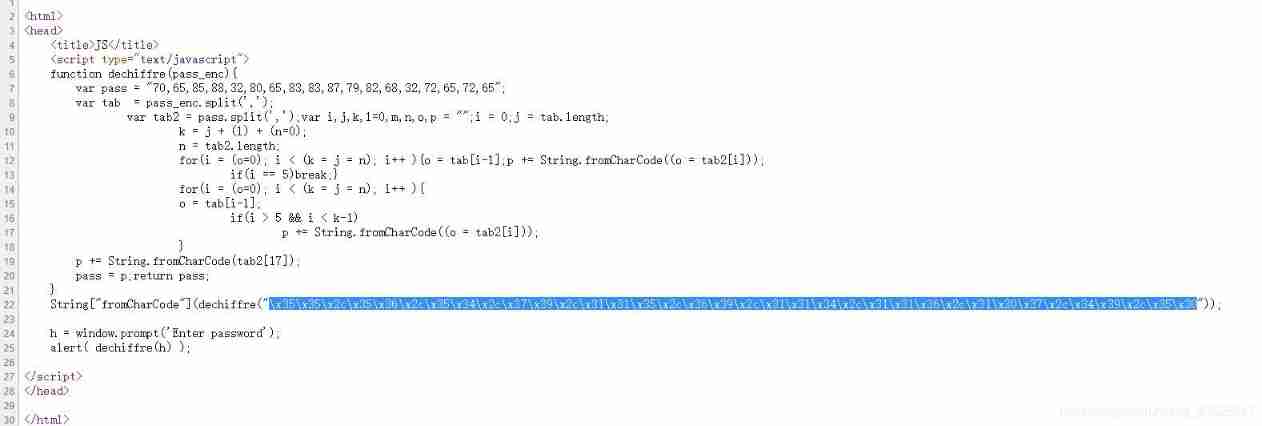
View source code , You will find a string of numbers similar to hexadecimal , Convert it to decimal , Then convert the decimal system into ASCLL code , obtain flag.
Here's the picture :
7、 ... and ,disabled_button
- Definition :disable Attribute specified as disabled button ( The disabled button is neither available , You can't click ).
- usage : You can set its properties , To restore users' use of it . then , have access to JavaScript(JavaScript yes Web Programming language . All modern HTML All pages use JavaScript) To get rid of disabled attribute , To make the text area available .
The operation is as follows :
View window review elements , Find out “disable=”, Next, double-left click on , Click on HTML, Delete its attribute , Click the button .
8、 ... and ,xff_referer
1,xff( Fake ip)
xff Its full name is X-Forwarded-Forxff On the general client HTTP The request does not exist , But when passing through the proxy server , The proxy server will add a xff, Its content is client IP Address , If there is a proxy server behind , Then a proxy server will be added later IP, So this gives us fake IP The possibility of , If we send on the client HTTP Add a when requesting XFF, And point its address to another IP, Then the server will regard our host as a proxy server , And write us IP As a client .
In short ,xff Is the final message that tells the server about the current requester ip Of http Request header field
Usually it can be directly through modify http In the header X-Forwarded-For Field to simulate the final of the request ip
2,Referer
referer( yes http A field in the header , The format is URL) It represents the page from which we entered this page , For example, I click to open a website ,
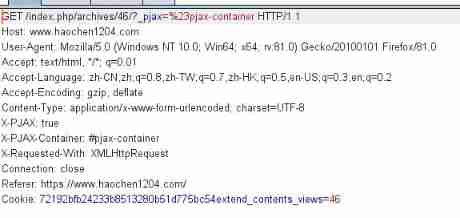
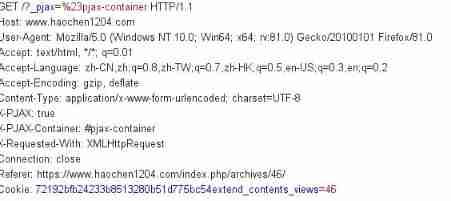
You can see get Followed by the address and other information we want to visit , and referer It means that I visit this address from my website . for example : Let's move from one website to another , Will find referer The following content has become our current website .
Nine ,weak_auth( Weak Authentication )
The principle of brute force cracking is to use the attacker's own user name and password dictionary , Enumerate one by one , Try whether you can log in .
cookie: It is used to maintain the connection with the server in the process of brute force cracking
referer: Some websites need to be verified referer Information , Tell the server , Which page did I turn from
post/get: Decide how to submit the data package
Field name : Usually stored in cookie among , Know the correct field name , In order to correctly submit the data to the server
Ten ,webshell
webshell That is to say asp、php、jsp perhaps cgi etc. Webpage A code execution environment in the form of a file , Mainly used for website management 、 Server management 、 Permission management and other operations .
effect :
One side ,webshell It is often used by webmasters for website management 、 Server management wait , according to FSO jurisdiction Different , The function is to edit web script online 、 Upload and download files 、 view the database 、 Execute arbitrary program commands, etc .
On the other hand , Used by intruders , In order to control Web server Purpose . these Web script Often called WEB Script Trojan , More popular asp or php Trojan horse , It's also based on .NET Script Trojan and JSP Script Trojan . Commonly used in China WebShell There is Haiyang ASP Trojan horse ,Phpspy,c99shell etc. .
webshell According to the script, it can be divided into PHP Script Trojan ,ASP Script Trojan , It's also based on .NET Script Trojan horse and JSP Script Trojan . According to the function, it is also divided into horse and pony , Pony usually refers to a Trojan horse , for example :<%eval request(“pass”)%> Usually write this sentence into a document , Then change the file name to xx.asp. Then send it to the server . The working mode in Malaysia is much simpler , There is no difference between client and server , Some scripts, Daniel, directly integrate the server of the Trojan horse in one sentence , Upload Malaysia via upload vulnerability , Then copy the horse's url Address direct access , Execute on the page web Server penetration work .
php function :
phpinfo Function can show PHP All relevant information . It is the troubleshooting configuration php Is the main way to configure the module if there is an error or omission
system Functions that execute system commands
11、 ... and ,Web11 command_execution
ping
ping Command is a common network command , It is usually used to test connectivity with the target host .
1. Command format :ping [ Parameters ] [ Host name or IP Address ]
2. Command function :
ping The command is used for : Determine the status of the network and each external host ; Track and isolate hardware and software issues ; test 、 Evaluate and manage the network . If the host is running and connected to the Internet , It responds to the echo signal .WAF
Web Application protection system ( Also known as : Website Application level intrusion prevention system . english :Web Application Firewall, abbreviation : WAF)
WAF The main protection is from the dynamic data attack on the website origin , The types of attacks that can be protected include SQL Inject 、XSS attack 、CSRF attack 、 Malicious reptiles 、 Scanner 、 Remote file inclusion and other attacks , It's like a firewall .
Twelve Web12:simple_php
is_numerc() Function is used to detect whether the variable is a number or a number . character string
Pass in the corresponding string to get flag
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-7HPa1f88-1638497558435)(C:\Users\hcj\Pictures\image-20211121164838008.png)]
Add
ping
ping-c 3 | id
ping-c 3 || id
ping-c 3 & id
ping-c 3 ;id
; find / -name “flag*” Search the root directory for the name flag The file of
; cat( Sometimes it will be shielded , Will use tac,head,tail) /home/flag.txt Read the file
head Read from the beginning to the end ,tail Read from the end forward
Reference address :
The rest comes from the Internet .
边栏推荐
- 百度数字人度晓晓在线回应网友喊话 应战上海高考英语作文
- Introduction to three methods of anti red domain name generation
- SwiftUI 4 新功能之掌握 WeatherKit 和 Swift Charts
- Rationaldmis2022 advanced programming macro program
- Solve server returns invalid timezone Go to ‘Advanced’ tab and set ‘serverTimezone’ property manually
- 112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]
- 30. Few-shot Named Entity Recognition with Self-describing Networks 阅读笔记
- Camera calibration (1): basic principles of monocular camera calibration and Zhang Zhengyou calibration
- Flet教程之 16 Tabs 选项卡控件 基础入门(教程含源码)
- Sonar:Cognitive Complexity认知复杂度
猜你喜欢
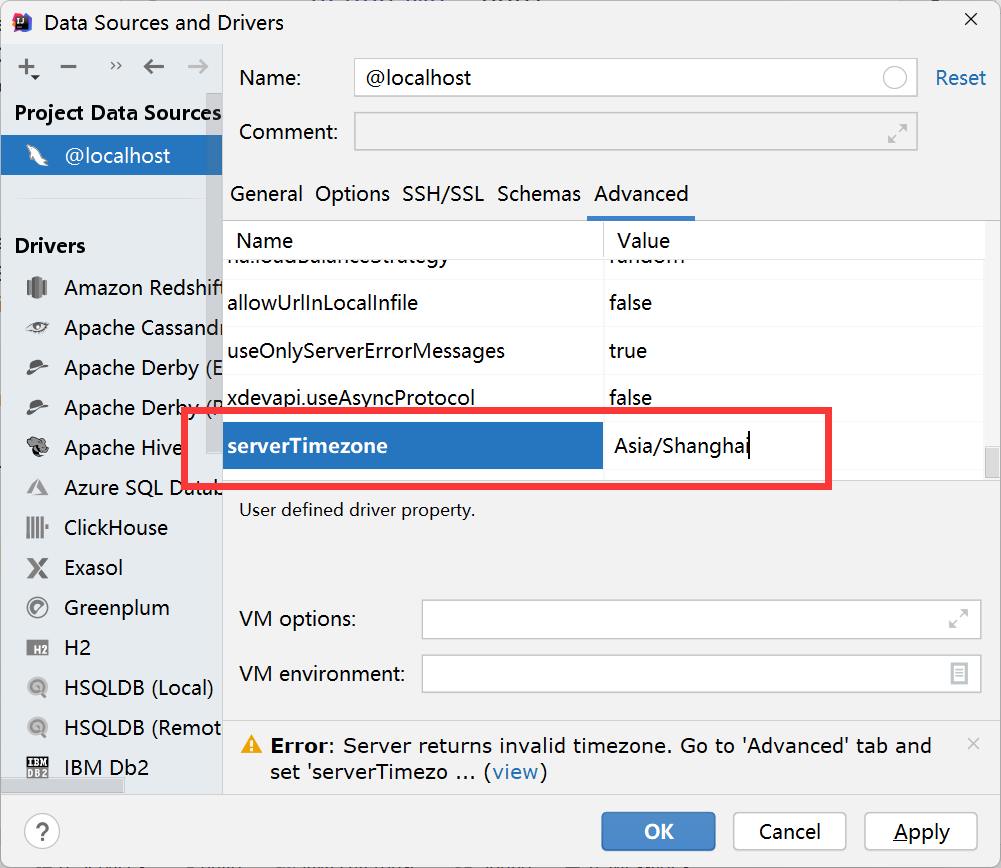
解决 Server returns invalid timezone. Go to ‘Advanced’ tab and set ‘serverTimezone’ property manually
2022 年第八届“认证杯”中国高校风险管理与控制能力挑战赛
30. Few-shot Named Entity Recognition with Self-describing Networks 阅读笔记
消息队列消息丢失和消息重复发送的处理策略
千人规模互联网公司研发效能成功之路
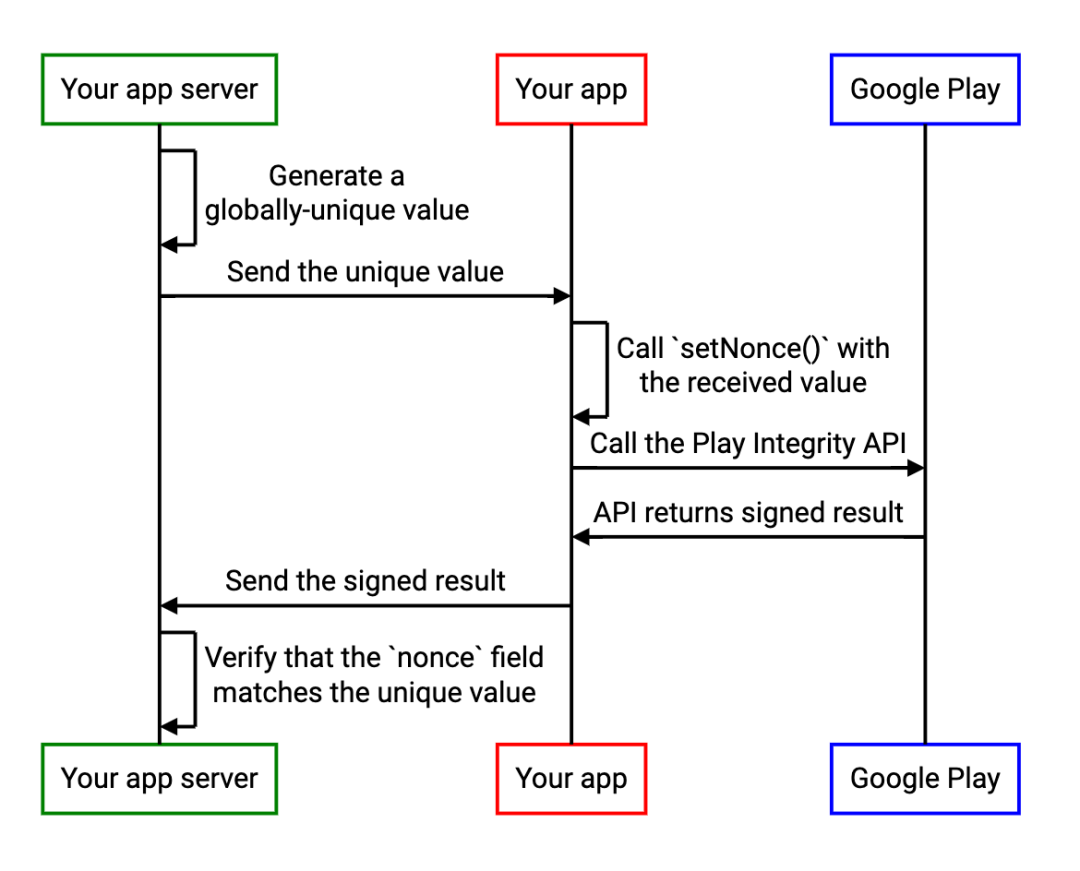
Improve application security through nonce field of play integrity API

Up meta - Web3.0 world innovative meta universe financial agreement

全球首堆“玲龙一号”反应堆厂房钢制安全壳上部筒体吊装成功
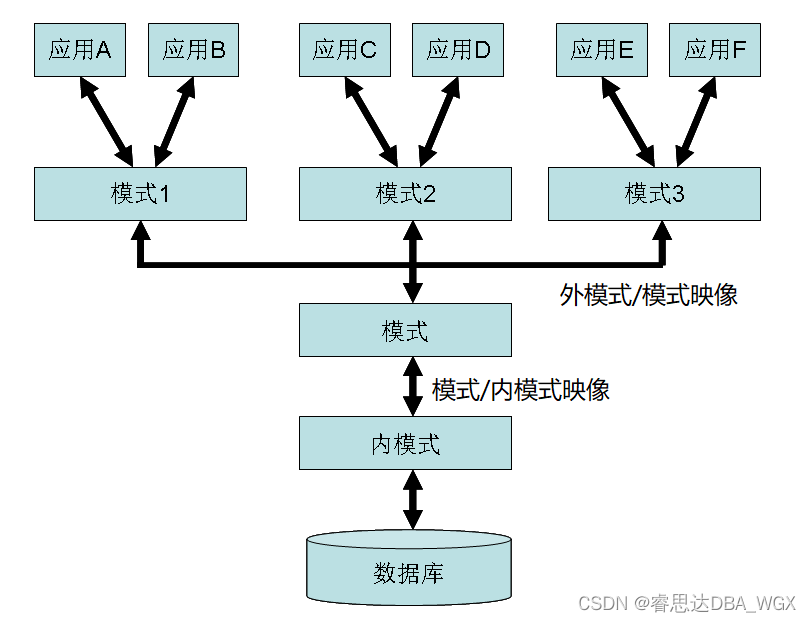
数据库系统原理与应用教程(007)—— 数据库相关概念
Flet教程之 17 Card卡片组件 基础入门(教程含源码)
随机推荐
Steps of redis installation and self startup configuration under CentOS system
Epp+dis learning road (2) -- blink! twinkle!
Tutorial on the principle and application of database system (008) -- exercises on database related concepts
UP Meta—Web3.0世界创新型元宇宙金融协议
110. Network security penetration test - [privilege promotion 8] - [windows sqlserver xp_cmdshell stored procedure authorization]
Superscalar processor design yaoyongbin Chapter 10 instruction submission excerpt
Camera calibration (1): basic principles of monocular camera calibration and Zhang Zhengyou calibration
Matlab implementation of Huffman coding and decoding with GUI interface
Flet教程之 19 VerticalDivider 分隔符组件 基础入门(教程含源码)
Solve server returns invalid timezone Go to ‘Advanced’ tab and set ‘serverTimezone’ property manually
[extraction des caractéristiques de texture] extraction des caractéristiques de texture de l'image LBP basée sur le mode binaire local de Matlab [y compris le code source de Matlab 1931]
<No. 9> 1805. Number of different integers in the string (simple)
SwiftUI 教程之如何在 2 秒内实现自动滚动功能
Rationaldmis2022 advanced programming macro program
What are the top-level domain names? How is it classified?
@What happens if bean and @component are used on the same class?
The function of adding @ before the path in C #
Detailed explanation of debezium architecture of debezium synchronization
When sink is consumed in mysql, the self incrementing primary key has been set in the database table. How to operate in Flink?
Upgrade from a tool to a solution, and the new site with praise points to new value