当前位置:网站首页>Improve application security through nonce field of play integrity API
Improve application security through nonce field of play integrity API
2022-07-07 11:49:00 【Google developers 】

author / Oscar Rodriguez, Developer Relations Engineer
We recently released Play Integrity API, Hope to help developers protect their applications and games , Protect them from fraudulent interactions that may pose risks ( Such as spoofing and unauthorized access ) Hazards of , Enable you to take appropriate measures to prevent attacks and reduce abuse .
Play Integrity API
https://developer.android.google.cn/google/play/integrity
In addition to application integrity 、 Useful signals related to equipment integrity and licensing information ,Play Integrity API It also provides a simple but very practical function , namely "nonce". If used properly , Developers can further strengthen Play Integrity API Existing protective measures , And reduce the risk of specific types of attacks , For example, intermediaries (PITM) Tamper attack and replay attack .
In this article , We will introduce in depth what is nonce、 How it works , And how to use it nonce Field to further protect your applications and games .
What is? nonce?
In cryptography and security engineering ,nonce (number once) It is a number that can only be used once in secure communication .nonce A wide range of uses , Like authentication 、 Data encryption and hash processing .
stay Play Integrity API in ,nonce You are calling API Opacity set before integrity check Base64 Code binary blob, And return the original sample through the signed response . Create and verify according to nonce The way , You can use it to further enhance Play Integrity API Existing protective measures , And mitigate specific types of attacks , For example, intermediaries (PITM) Tamper attack and replay attack .
Except return as is in the signed response nonce,Play Integrity API It won't be right nonce Any processing of actual data , So you can set any value , As long as it is an effective Base64 value . in other words , To digitally sign the response ,nonce The value will be sent to Google The server , So please do not nonce Set to any type of personally identifiable information (PII), For example, user name 、 Phone or email address .
Set up nonce
Set your app to use Play Integrity API after , You can use setNonce() Method , Or its appropriate variant settings nonce, These variants apply to API Of Kotlin、Java、Unity and Native edition .
Set your app to use Play Integrity API
https://developer.android.google.cn/google/play/integrity/setup
Set up nonce
https://developer.android.google.cn/google/play/integrity/verdict#request
Kotlin:
val nonce: String = ...
// establish manager Example
val integrityManager =
IntegrityManagerFactory.create(applicationContext)
// adopt nonce Get integrity token
val integrityTokenResponse: Task<IntegrityTokenResponse> =
integrityManager.requestIntegrityToken(
IntegrityTokenRequest.builder()
.setNonce(nonce) // Set up nonce
.build())Java:
String nonce = ...
// establish manager Example
IntegrityManager integrityManager =
IntegrityManagerFactory.create(getApplicationContext());
// adopt nonce Get integrity token
Task<IntegrityTokenResponse> integrityTokenResponse =
integrityManager
.requestIntegrityToken(
IntegrityTokenRequest.builder()
.setNonce(nonce) // Set up nonce
.build());Unity:
string nonce = ...
// establish manager Example
var integrityManager = new IntegrityManager();
// adopt nonce Get integrity token
var tokenRequest = new IntegrityTokenRequest(nonce);
var requestIntegrityTokenOperation =
integrityManager.RequestIntegrityToken(tokenRequest);Native:
// establish IntegrityTokenRequest object
const char* nonce = ...
IntegrityTokenRequest* request;
IntegrityTokenRequest_create(&request);
IntegrityTokenRequest_setNonce(request, nonce); // Set up nonce
IntegrityTokenResponse* response;
IntegrityErrorCode error_code =
IntegrityManager_requestIntegrityToken(request, &response);verification nonce
Play Integrity API Response of with JSON Network token (JWT) Form return of , Its load is plain text JSON, The format is as follows :
{
requestDetails: { ... }
appIntegrity: { ... }
deviceIntegrity: { ... }
accountDetails: { ... }
}JSON Network token (JWT)
https://jwt.io/
Pure text JSON
https://developer.android.google.cn/google/play/integrity/verdict#returned-payload-format
You can go to requestDetails Structure nonce, The format is as follows :
requestDetails: {
requestPackageName: "...",
nonce: "...",
timestampMillis: ...
}nonce The value of the field should be the same as you called API The passed values match exactly . Besides , because nonce Values in the Play Integrity API In the encrypted signature response , After receiving the response, it cannot be changed . Through these properties , You can use nonce Further protect your application .
Protect important operations
Imagine this scene , An attacker is trying to maliciously falsely report players' scores to the game server . In this case , The equipment and application are complete , However, the attacker can still view and modify the communication data flow with the game server through the proxy server or virtual private network , So as to achieve the purpose of falsely reporting scores .
under these circumstances , Call only Play Integrity API Not enough to protect the application : The device has not been cracked 、 Application is also legal , Therefore, this operation can be done through Play Integrity API All inspections of .
But you can use Play Integrity API Of nonce To protect this specific high-value operation that reports game scores , That is to say nonce The value of the encoding operation in . The implementation method is as follows :
Users initiate important operations ;
The application is ready to protect messages , for example JSON Formatted message ;
The application calculates the encrypted hash value of the message to be protected . for example , Use SHA-256 or SHA-3-256 The hash algorithm ;
Application call Play Integrity API, And call setNonce() In order to nonce Field is set to the encrypted hash value calculated in the previous step ;
The message that the application will protect and Play Integrity API Send the signature result of to the server ;
The application server verifies whether the encrypted hash value of the message it receives is consistent with nonce Field values match , And reject any mismatched results .
The following sequence diagram illustrates the relevant steps :
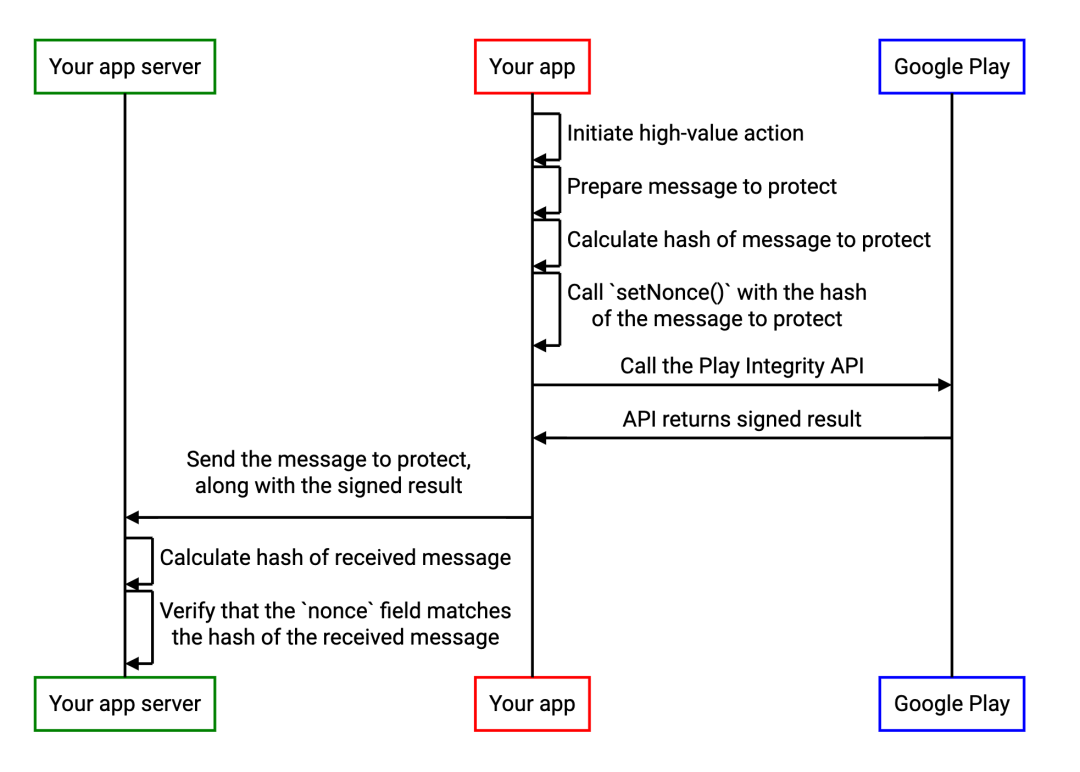
As long as the protected original message is sent with the signature result , And both the server and the client use the same mechanism to calculate nonce, In this way, the message will not be tampered .
Please note that , In the above scenario , The effectiveness of the security model is limited to attacks that occur in the network ( Not in devices or applications ), So verify Play Integrity API The equipment and application integrity signals provided are also particularly important .
Prevent replay attacks
Let's imagine another scenario , An application or game uses Play Integrity API To protect yourself C/S framework , But the attacker tried to interact with the server by using the cracked device , And don't let the server detect .
If you want to " a " This attack target , The attacker will first make the application and Play Integrity API Interact , And get the signed response content , Then run the application on the cracking device and intercept Play Integrity API Call to , Use previously recorded 、 Respond with the signed response content , In this way, the integrity check will not be performed .
Since the signed response has not been changed in any way , So digital signature seems normal , The application server will mistakenly think that it is communicating with legitimate devices . We call this Replay attack .
The first line of defense against such attacks is to verify the signature response timestampMillis Field . This field contains the timestamp when the response was created , Even if the digital signature is verified , It can also be used on the server side to detect whether it is a suspicious old response .
in other words , Application servers can also take advantage of Play Integrity API Medium nonce, Assign a unique value to each response , And verify that the response matches the unique value set previously . The implementation method is as follows :
The server creates globally unique values in a way that attackers cannot predict . for example ,128 Encrypted secure random numbers with bits or more ;
Application call Play Integrity API, And will nonce Field is set to the unique value received by the application server ;
The app will Play Integrity API Send the signature result of to the server ;
The server verifies nonce Whether the field matches the previously generated unique value , And reject all mismatched results .
The following sequence diagram illustrates the relevant steps :
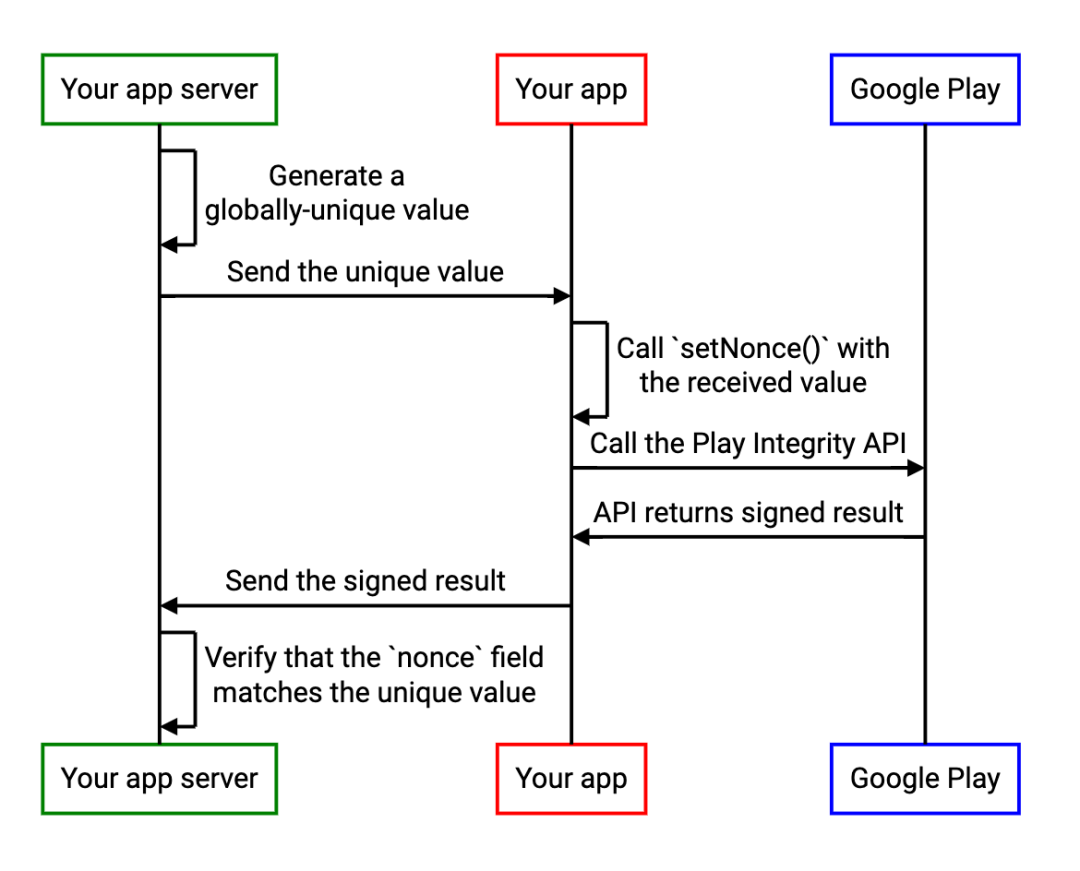
After realizing the above process , Every time the server requires the application to call Play Integrity API when , It will use different globally unique values , So as long as the attacker cannot predict this value ,nonce Does not match the expected value , The previous response cannot be reused .
Combine two protective measures
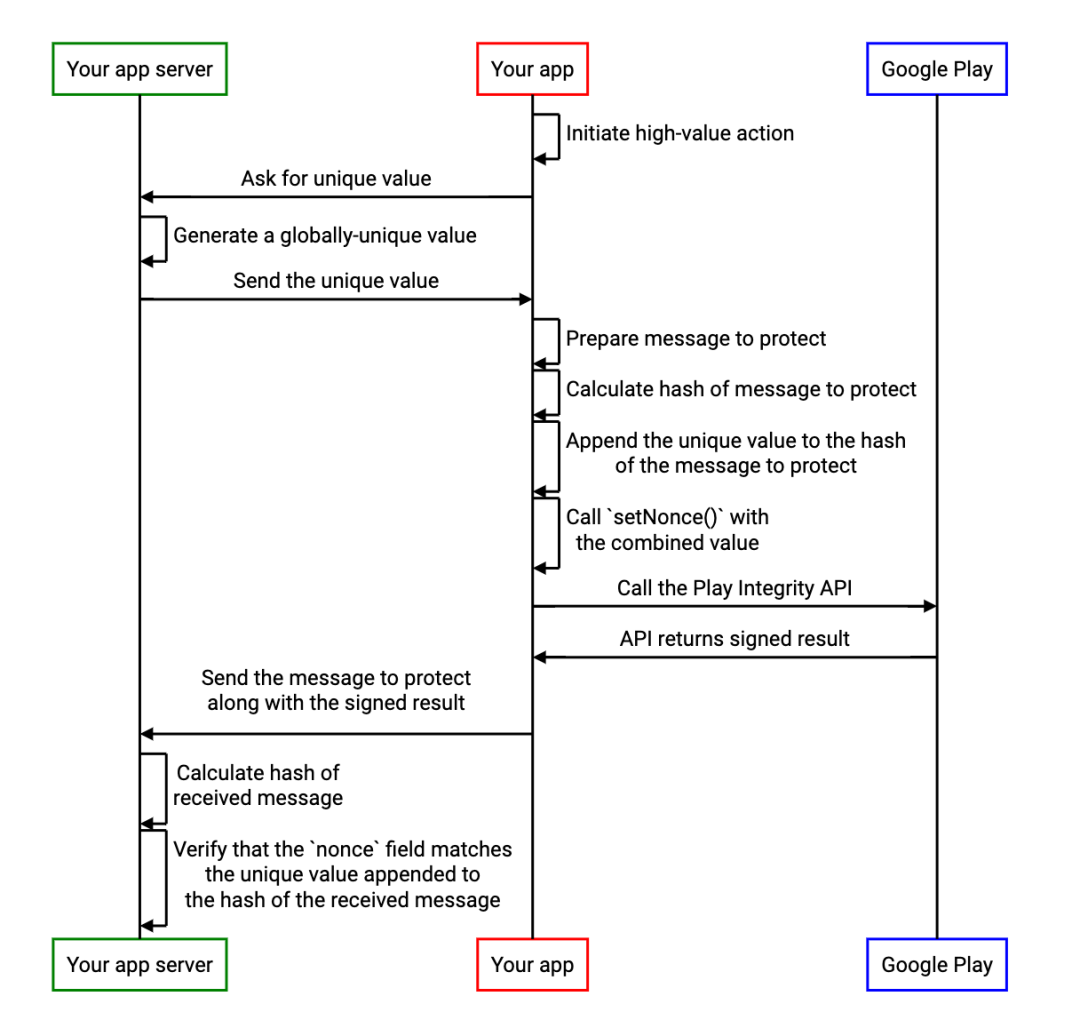
Although the above two mechanisms work in different ways , But if the application needs two kinds of protection at the same time , These two mechanisms can be combined in one Play Integrity API in call , for example , Attach the results of the two protective measures to a larger Base64 nonce in . The implementation method of combining the two protection measures is as follows :
Users initiate important operations ;
The application requires the server to provide a unique value to identify the request ;
The application server generates a globally unique value , Prevent attackers from making predictions . for example , You can create such a value using a cryptographic secure random number generator . We recommend that you create not less than 128 The value of a ;
The application server sends a globally unique value to the application ;
The application is ready to protect messages , for example JSON Formatted message ;
The application calculates the encrypted hash value of the message to be protected . for example , Use SHA-256 or SHA-3-256 The hash algorithm ;
The application creates a string by appending the unique value received from the application server and the hash value of the message to be protected ;
Application call Play Integrity API, And call setNonce() In order to nonce Field is set to the string created in the previous step ;
The message that the application will protect and Play Integrity API Send the signature result of to the server ;
Application server split nonce Value of field , Then verify whether the encrypted hash value of the message and the previously generated unique value match the expected value , And reject any mismatched results .
The following sequence diagram illustrates the relevant steps :
The above is what you can use nonce Some examples of further protecting applications from malicious user attacks . If your application can handle sensitive data , Or easy to be abused , We suggest you consider using Play Integrity API, Take relevant measures to mitigate the threat .
For information about using Play Integrity API For more information and start experiencing , Please go to Play Integrity API page :
https://developer.android.google.cn/google/play/integrity
 Click at the end of the screen | Read the original | immediately understand Play Integrity API For more information
Click at the end of the screen | Read the original | immediately understand Play Integrity API For more information

Check the size and color of the square at the same time
边栏推荐
- 正在運行的Kubernetes集群想要調整Pod的網段地址
- Use references
- STM32 entry development NEC infrared protocol decoding (ultra low cost wireless transmission scheme)
- Enclosed please find. Net Maui's latest learning resources
- Complete collection of common error handling in MySQL installation
- Flet教程之 15 GridView 基础入门(教程含源码)
- C#中在路径前加@的作用
- Excel公式知多少?
- 博客搬家到知乎
- Have you ever met flick Oracle CDC, read a table without update operation, and read it repeatedly every ten seconds
猜你喜欢
About how to install mysql8.0 on the cloud server (Tencent cloud here) and enable local remote connection
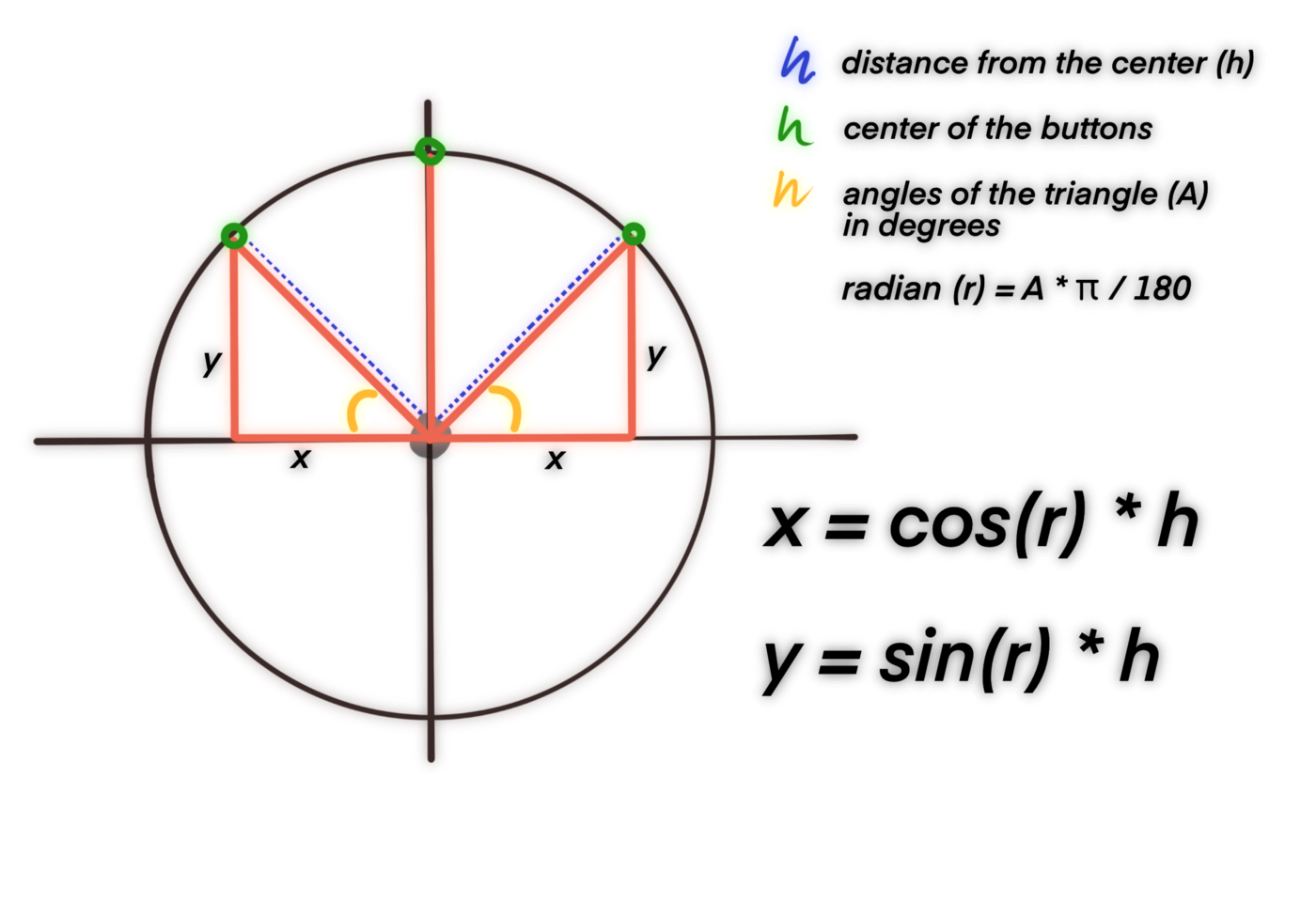
Swiftui swift internal skill how to perform automatic trigonometric function calculation in swift
Mastering the new functions of swiftui 4 weatherkit and swift charts
千人規模互聯網公司研發效能成功之路
Use metersphere to keep your testing work efficient
![[filter tracking] strapdown inertial navigation simulation based on MATLAB [including Matlab source code 1935]](/img/ae/52cdc98fb9db8c0d0776b8274ecd39.png)
[filter tracking] strapdown inertial navigation simulation based on MATLAB [including Matlab source code 1935]
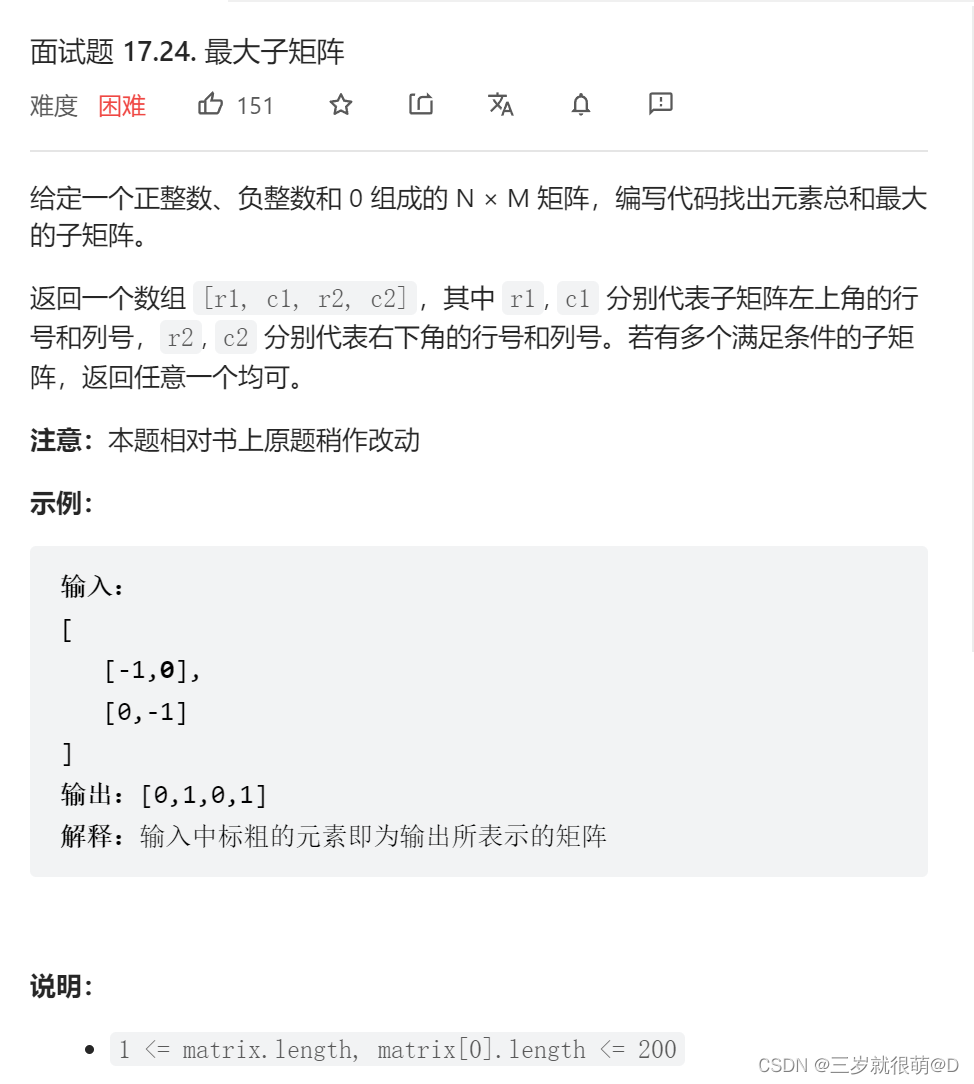
LeetCode - 面试题17.24 最大子矩阵
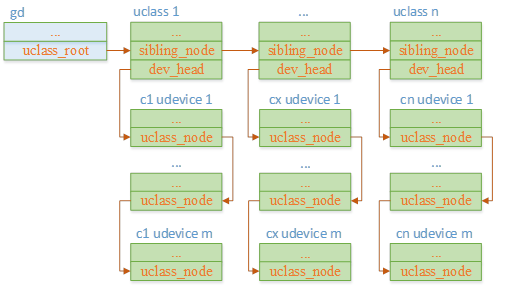
聊聊SOC启动(六)uboot启动流程二
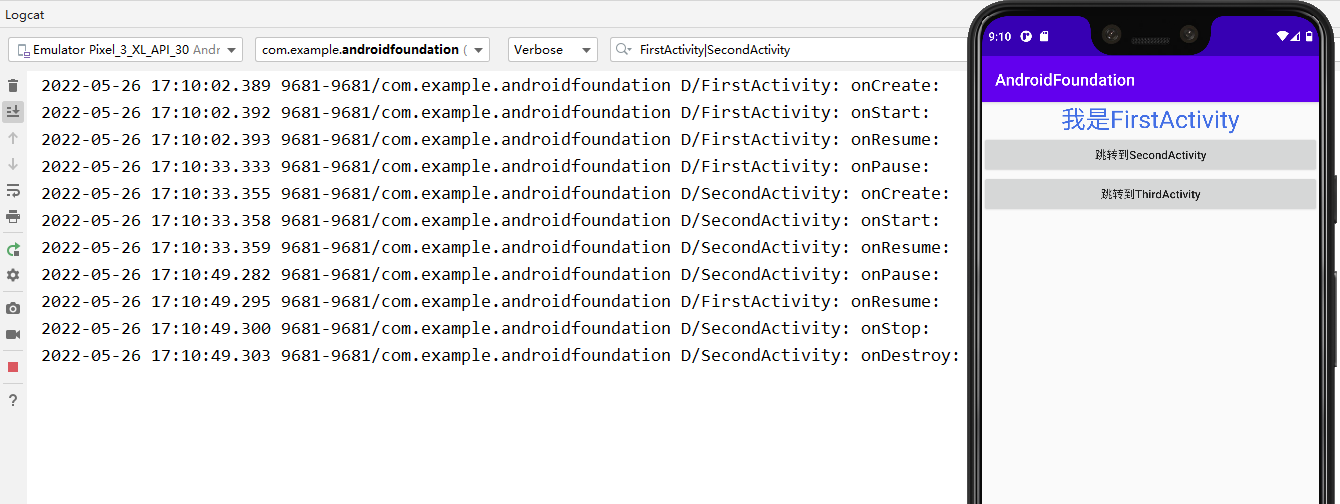
Activity lifecycle
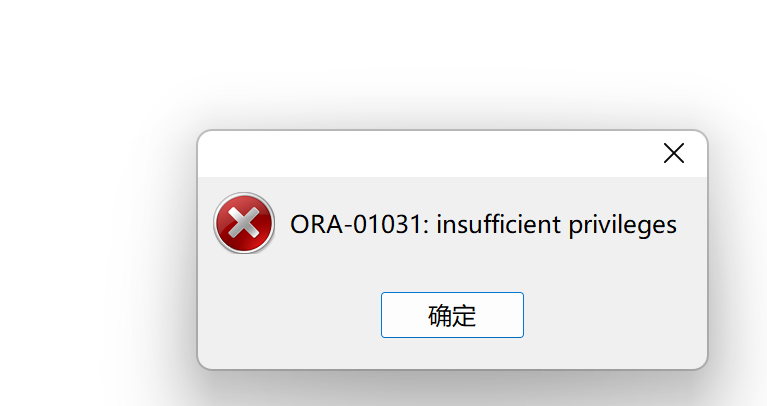
The Oracle message permission under the local Navicat connection liunx is insufficient
随机推荐
.NET MAUI 性能提升
Tsinghua Yaoban programmers, online marriage was scolded?
Poor math students who once dropped out of school won the fields award this year
正在运行的Kubernetes集群想要调整Pod的网段地址
R语言使用magick包的image_mosaic函数和image_flatten函数把多张图片堆叠在一起形成堆叠组合图像(Stack layers on top of each other)
Swiftui tutorial how to realize automatic scrolling function in 2 seconds
About how to install mysql8.0 on the cloud server (Tencent cloud here) and enable local remote connection
Briefly introduce closures and some application scenarios
SwiftUI Swift 内功之如何在 Swift 中进行自动三角函数计算
聊聊SOC启动(九) 为uboot 添加新的board
[question] Compilation Principle
In SQL, I want to set foreign keys. Why is this problem
Various uses of vim are very practical. I learned and summarized them in my work
【全栈计划 —— 编程语言之C#】基础入门知识一文懂
Programming examples of stm32f1 and stm32subeide -315m super regenerative wireless remote control module drive
Unsupervised learning of visual features by contracting cluster assignments
STM32F1与STM32CubeIDE编程实例-MAX7219驱动8位7段数码管(基于SPI)
Blog moved to Zhihu
Software design - "high cohesion and low coupling"
【最短路】Acwing1128信使:floyd最短路