### Concept introduction ** Name ** Netfilter/iptables The module consists of two parts : Netfilter Framework and iptables,iptables It's divided into iptables( Core space ) and iptables Command line tools ( User space ); Netfilter/iptables Module In the eyes of ordinary users, it is abbreviated to iptables, But in fact, in the eyes of relevant developers, they tend to call it Netfilter, From the address of the official website of the project, we can see that : https://netfilter.org/ ** effect ** For packet processing , such as : Forwarding of messages 、 Filtration 、 modify , Network address translation and other functions , It's a software firewall . ### iptables The basic principle #### Basic workflow ** Basic work flow chart ** 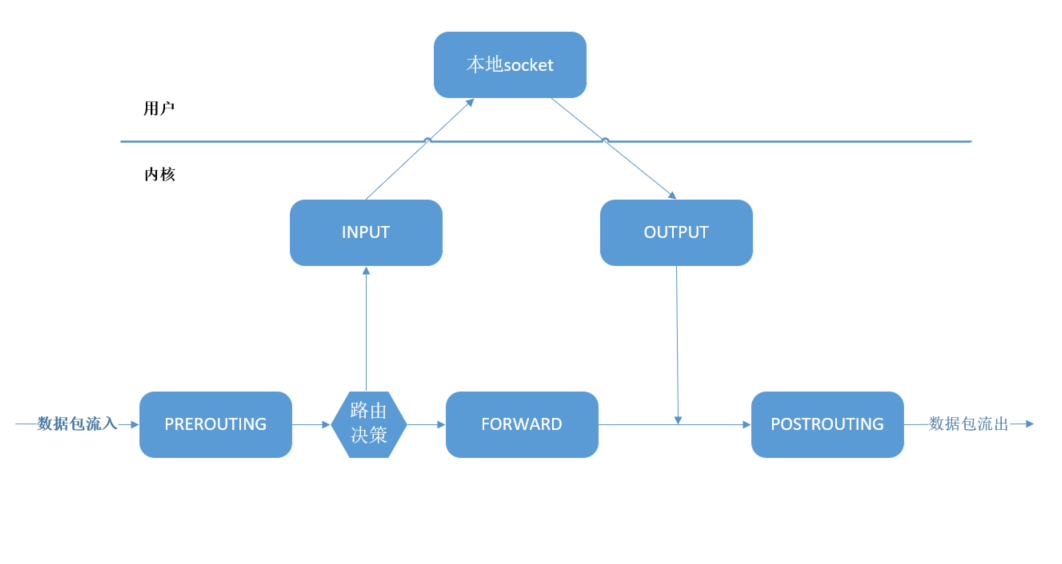 Packets travel along the chain ,iptables Yes 5 Chain :PREROUTING, INPUT, FORWORD, OUTPUT, POSTROUTING, It can be thought of as 5 A level , Every level has a lot of rules , There may be no rules . The workflow is as follows : 1、 When a packet enters the network card , Will enter it first PREROUTING, Then the routing decision is made according to the destination address , If the destination address is local , Then go INPUT, If it's not the machine, it's going FORWARD, And then go POSTROUTING Turn around . 2、 Enter INPUT Will be transferred to the local program , After the program is processed , New packages will be sent , go OUTPUT, And then pass by POSTROUTING Turn around . 3、 Of course, the above process goes through a chain , Match the rules in the chain according to the order of the rules in the chain , Whenever a matching rule is encountered, it will be handled according to this rule , The latter rules no longer work on this information . #### Simple rules add Only local socket It's user mode , The rest is core processing . We usually add iptables Rules , That's what's added to each chain , We set up a container to test , I've installed it in the container iptables, Use it directly iptables Command is enough : ```shell # Start a container first [
[email protected] ~]# docker run -itd --name "cos8_test" --cap-add=NET_ADMIN centos:base /bin/bash bd0c29186387b01ae64514050b3b4b804babc988f3dbc52c0cfe6eeac115d1b2 ``` > notes : To modify the container network , The container should be started with --cap-add=NET_ADMIN, Otherwise, execute in the container iptables The command will report an error : > >(nf_tables): Could not fetch rule set generation id: Permission denied (you must be root) Look at iptables Rules , You can see that there is no strategy at present ```shell [
[email protected] ~]# docker ps | grep cos8 bd0c29186387 centos:base "/bin/bash" 21 hours ago Up 21 hours cos8_test [
[email protected] ~]# docker exec -it bd0 bash [
[email protected] /]# [
[email protected] /]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ``` Set up a rule : Deny all access to this machine 80 Port of tcp Data package . ```shell [
[email protected] /]# iptables -A INPUT -p tcp --dport 80 -j DROP [
[email protected] /]# [
[email protected] /]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 Chain FORWARD (policy ACCEPT) target prot opt source destination DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 Chain OUTPUT (policy ACCEPT) target prot opt source destination DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 ``` Here's an episode : You can see that I'm only in INPUT Added rules to the chain , But how FORWARD and OUTPUT There's also this rule in the chain , Then I manually deleted INPUT The rules in the chain , And then FORWARD and OUTPUT The rules in the chain disappear , Of this container OS The version and core information are as follows ```shell [
[email protected] /]# cat /etc/redhat-release CentOS Linux release 8.2.2004 (Core) [
[email protected] /]# [
[email protected] /]# uname -a Linux bd0c29186387 3.10.0-1127.13.1.el7.x86_64 #1 SMP Tue Jun 23 15:46:38 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux ``` I haven't used it before centos8, Considering that it might be OS Updated netfilter Module , So it was replaced by a centos7.8.2003 The container tested , Found that the new rules are in line with expectations , as follows ```shell [
[email protected] /]# docker run -itd --name "cos7" --cap-add=NET_ADMIN centos7:base /bin/bash c951c0a9d34d8e43a56e43872294ab5ab6a1504b365721238178de134e8d3bde [
[email protected] /]# [
[email protected] /]# docker exec -it cos7 bash [
[email protected] /]# [
[email protected] /]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination [
[email protected] /]# [
[email protected] /]# iptables -A INPUT -p tcp --dport 80 -j DROP [
[email protected] /]# [
[email protected] /]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ``` > Refuse can be used DROP, You can also use REJECT Keywords ,DROP No information will be returned to the client , So what the client sees is the connection timeout , It's hard to judge whether it's the firewall or the network device failure . > > and REJECT Then a rejection message is explicitly returned to the client , The client will know that I was rejected by the firewall . > > It can be used according to the scene ,REJECT More suitable for debugging ,DROP It's safer to resist attacks . Use after centos7 As a test , I don't care centos8 What's new . #### Four tables and five chains The rules I added above are as follows : ```shell iptables -A INPUT -p tcp --dport 80 -j DROP ``` But it's just short form , Write a little bit more completely as follows , In fact, it can be more complete , Don't say for the moment . ```shell iptables -t filter -A INPUT -s 0.0.0.0/0 -p tcp -d 0.0.0.0/0 --dport 80 -j DROP ``` -t : Designated table , Here is filter surface , Rules will be added to filter In the table . -s : Specify the source address ,0.0.0.0/0 It means everything IP. -d : Specify the destination address . --dport : Designated destination port . -j : Specify the processing action , Here is DROP, That is to throw away . ** The concept of table ** It's mentioned above that filter surface , What is a watch ? We add rules , Add to each chain , There are many rules in each chain , Some of the rules are similar , such as , Part of it is port filtering , Some of them are modification of messages , According to the type of rules , Put similar rules together , The set of rules put together is called a table . The different sets of rules are placed in different tables , There is... In all 4 Kind of watch , That is to say 4 Rules : filter surface : Responsible for the filtering function ; nat surface :network address translation, Network address translation function ; mangle surface : Take apart 、 modify 、 And re encapsulate the message ; raw surface : Shut down nat The connection tracing mechanism enabled on the table ; Because there are different rules in each chain , So tables exist in every chain , But not every chain has this 4 Kind of watch , PREROUTING The rules of can exist in :raw surface ,mangle surface ,nat surface . INPUT The rules of can exist in :mangle surface ,filter surface ,nat surface (centos7 There is nat surface ,centos6 Not in ). FORWARD The rules of can exist in :mangle surface ,filter surface . OUTPUT The rules of can exist in :raw surface mangle surface ,nat surface ,filter surface . POSTROUTING The rules of can exist in :mangle surface ,nat surface . Table processing priorities are as follows : raw --> mangle --> nat --> filter So we started with iptables The basic work flow chart can be more detailed 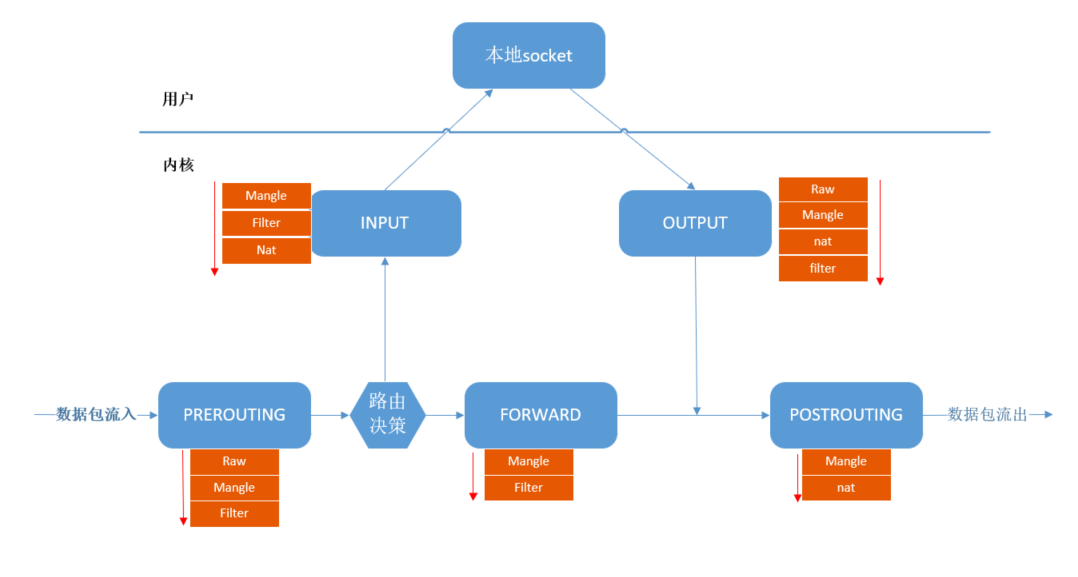 In fact, it can be more detailed , Let's take a chain alone , such as PREROUTING Chain , It's probably the following , Together, these rules form a chain . 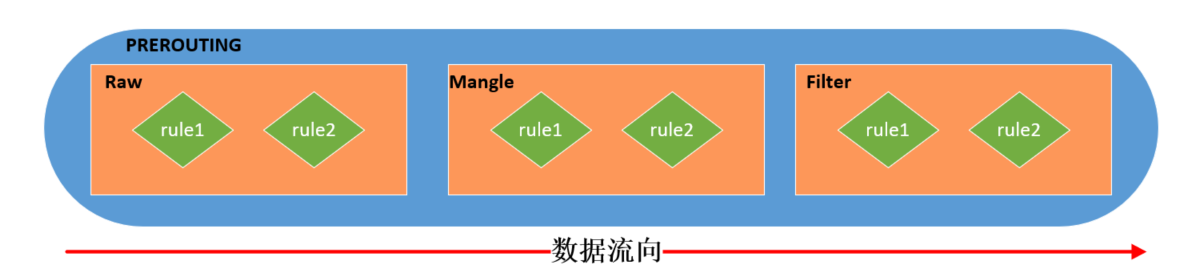 therefore , We have added a ban on access to this machine 80 The rules of the port are stored in filter In the table , Let's examine filter The rules in the table , You can see our new rules ,netfilter Preset handle 80 The port system is http. ```shell [
[email protected] /]# iptables -L -t filter Chain INPUT (policy ACCEPT) target prot opt source destination DROP tcp -- anywhere anywhere tcp dpt:http Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ``` #### iptables Examples of common commands are ** Inspection rules ** ```shell Click on the table to view : iptables -L -t table Follow the chain : iptables -nL INPUT ``` ** Set the default rules of the chain ** ```shell #INPUT Chain default rejects all packets iptables -P INPUT DROP #OUTPUT Default allows all data to be packed out iptables -P INPUT ACCEPT ``` ** Clear the rules in the table ** ```shell # Empty nat In the table PREROUTING The rules of the chain iptables -t nat -F PREROUTING # Empty filter Rules for all chains in the table iptables -t filter -F # Clear user-defined table rules iptables -X ``` ** Delete a rule ** ```shell # You can delete by number #--line-number The number is shown in front of the rule [
[email protected] /]# iptables -nL --line-number Chain INPUT (policy ACCEPT) num target prot opt source destination 1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 Chain FORWARD (policy ACCEPT) num target prot opt source destination Chain OUTPUT (policy ACCEPT) num target prot opt source destination [
[email protected] /]# [
[email protected] /]# iptables -D INPUT 1 # You can also delete rules directly # In the following order ,-D The following are all matching conditions , Delete everything that matches these in a rule [
[email protected] /]# iptables -D INPUT -p tcp --dport 80 -j DROP ``` ** Forbid ping** ```shell # Forbid others to ping own , But I can ping Others #type 8: Express ping Packet request traffic #type 0: Express ping Packet response traffic iptables -A INPUT -p icmp --icmp-type 0 -j DROP iptables -A OUTPUT -p icmp --icmp-type 8 -j DROP # Forbid others to ping own , And forbid yourself ping Others iptables -A INPUT -p icmp -m icmp --icmp-type any -j DROP # You can also change the argument to prohibit ping echo "1" > /proc/sys/net/ipv4/icmp_echo_ignore_all ``` ** Forward ** ```shell # Turn on forwarding echo 1 > /proc/sys/net/ipv4/ip_forward # For external access to oneself 80 The traffic of the port is all transferred to 172.17.0.4 Of 80 Port , #xxx.xxx.xxx.xx On behalf of the machine IP iptables -t nat -I PREROUTING -d xxx.xxx.xxx.xx -p tcp --dport 80 -j DNAT --to-destination 172.17.0.4:80 # For traffic coming out of this machine , Source ip All converted to 172.17.0.4 iptables -t nat -A POSTROUTING -p tcp -j SNAT --to-source 172.17.0.4 ``` ** Make rules for link states ** ```shell #NEW The user initiates a new request #ESTABLISHED Respond to a new request #RELATED The relationship between two complete lines , A complete connection , Need to rely on another complete connection . #INVALID Unrecognized state . iptables -A INPUT -m state –state ESTABLISHED,RELATED -j ACCEPT ``` First of all