当前位置:网站首页>What is the general yield of financial products in 2022?
What is the general yield of financial products in 2022?
2022-07-07 18:17:00 【Koufu Q & A】
Take the answer 1:
边栏推荐
- 2021年全国平均工资出炉,你达标了吗?
- 万字保姆级长文——Linkedin元数据管理平台Datahub离线安装指南
- Self made dataset in pytoch for dataset rewriting
- Mui side navigation anchor positioning JS special effect
- 数学分析_笔记_第11章:Fourier级数
- socket编程之常用api介绍与socket、select、poll、epoll高并发服务器模型代码实现
- Introduction of common API for socket programming and code implementation of socket, select, poll, epoll high concurrency server model
- [principle and technology of network attack and Defense] Chapter 7: password attack technology Chapter 8: network monitoring technology
- ICer知识点杂烩(后附大量题目,持续更新中)
- Summary of debian10 system problems
猜你喜欢

What is agile testing

Backup Alibaba cloud instance OSS browser
Click on the top of today's headline app to navigate in the middle
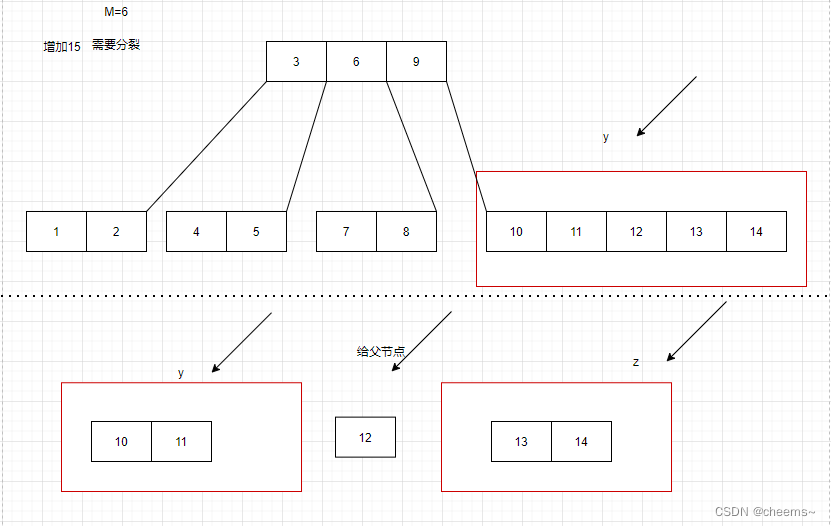
磁盘存储链式的B树与B+树
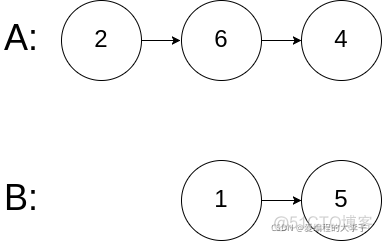
<代码随想录二刷>链表
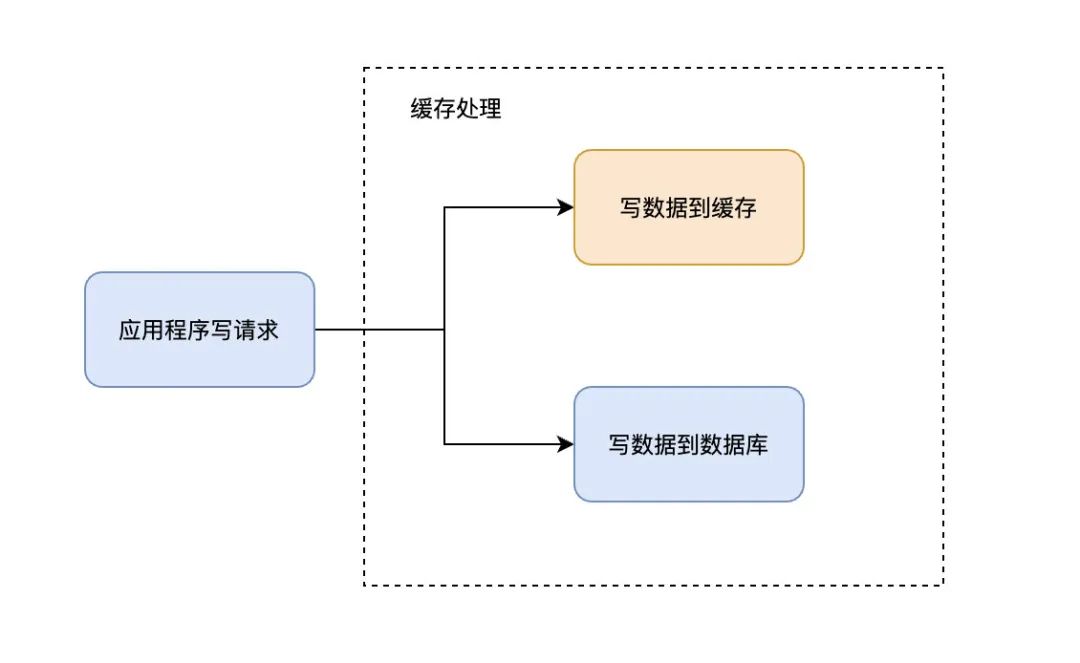
4种常见的缓存模式,你都知道吗?
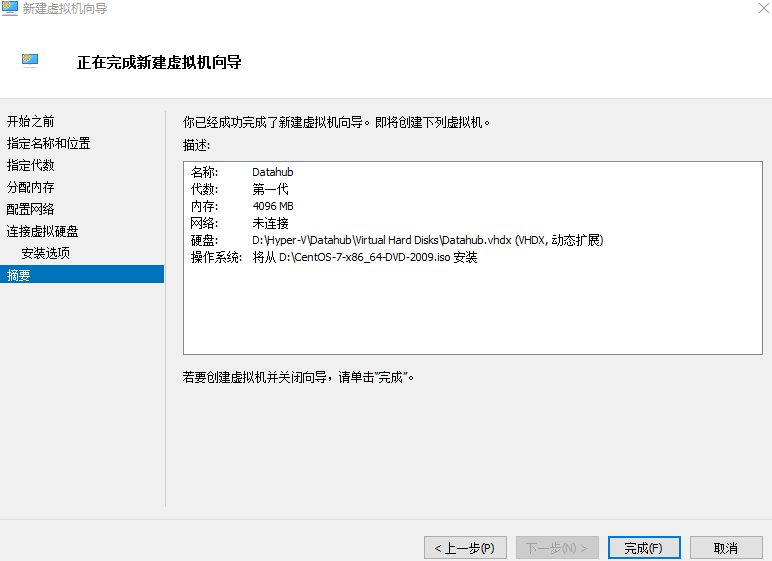
Ten thousand words nanny level long article -- offline installation guide for datahub of LinkedIn metadata management platform

The report of the state of world food security and nutrition was released: the number of hungry people in the world increased to 828million in 2021
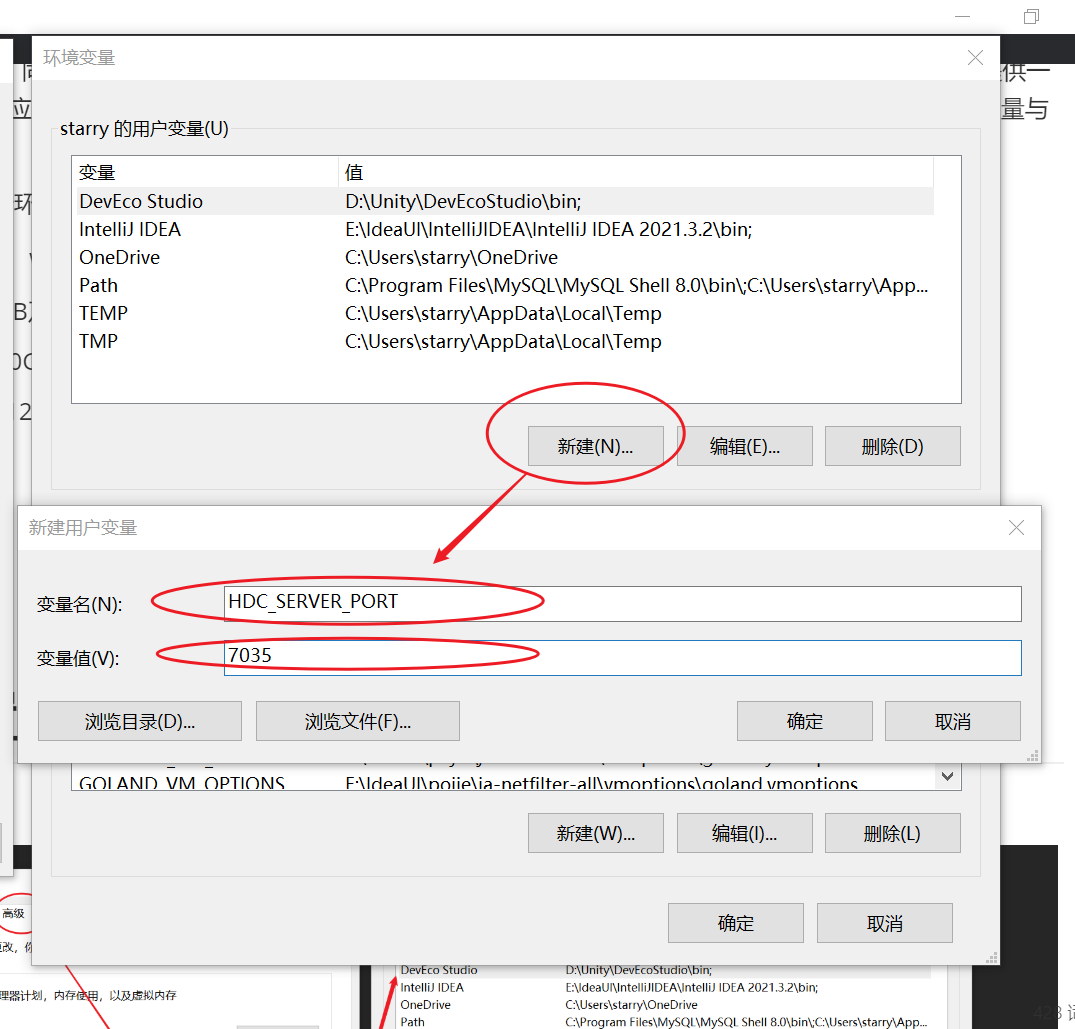
『HarmonyOS』DevEco的下载安装与开发环境搭建
手机app外卖订餐个人中心页面
随机推荐
【demo】循环队列及条件锁实现goroutine间的通信
[principle and technology of network attack and Defense] Chapter 6: Trojan horse
4种常见的缓存模式,你都知道吗?
海量数据去重的hash,bitmap与布隆过滤器Bloom Filter
上市十天就下线过万台,欧尚Z6产品实力备受点赞
科学家首次观察到“电子漩涡” 有助于设计出更高效的电子产品
nest.js入门之 database
Chapter 3 business function development (to remember account and password)
[network attack and defense principle and technology] Chapter 4: network scanning technology
Chapter 2 build CRM project development environment (database design)
Chapter 1 Introduction to CRM core business
Target detection 1 -- actual operation of Yolo data annotation and script for converting XML to TXT file
idea彻底卸载安装及配置笔记
不能忽略的现货白银短线操作小技巧
MySQL index hit level analysis
js拉下帷幕js特效显示层
JS pull down the curtain JS special effect display layer
手机版像素小鸟游js戏代码
仿今日头条APP顶部点击可居中导航
Ten thousand words nanny level long article -- offline installation guide for datahub of LinkedIn metadata management platform