当前位置:网站首页>OSI and tcp/ip protocol cluster
OSI and tcp/ip protocol cluster
2022-07-05 13:54:00 【Cwxh0125】
Catalog
The function and analysis of each layer
Data encapsulation and de encapsulation process
Common protocols and associations at all levels
Stratification thought
Communication requirements ----> Define protocol standards
There are too many agreements needed to complete one thing ——————> layered
Simplify complex problems
The same protocol is used between the same layers The lower class serves the upper class
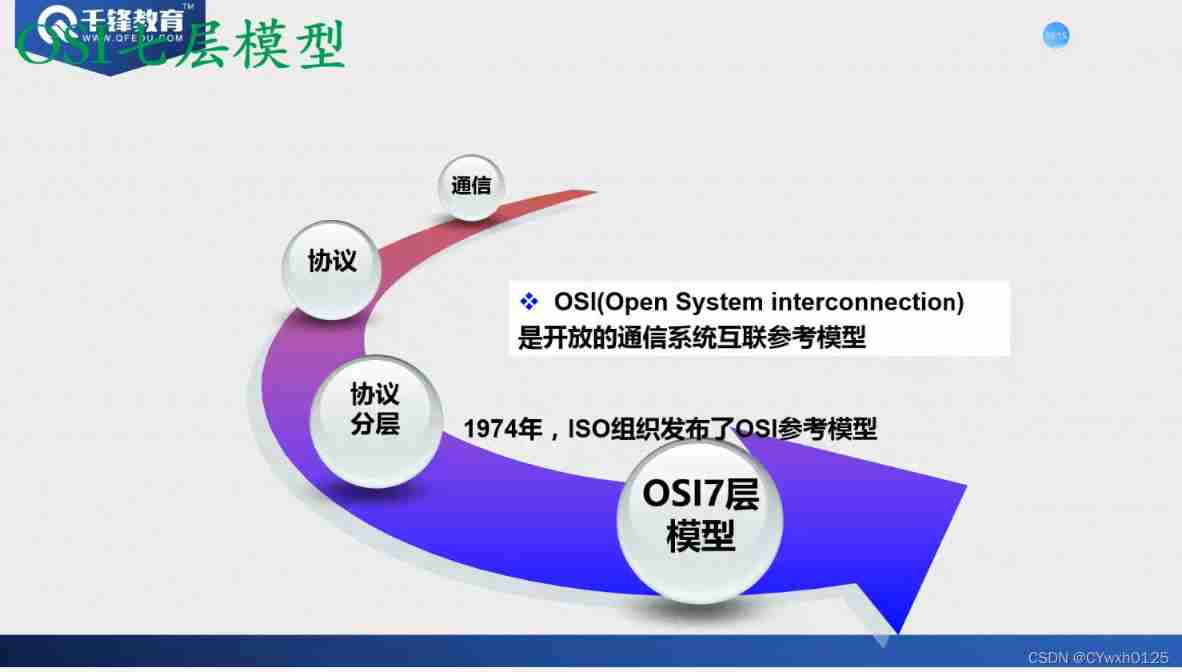
osi Seven layer model
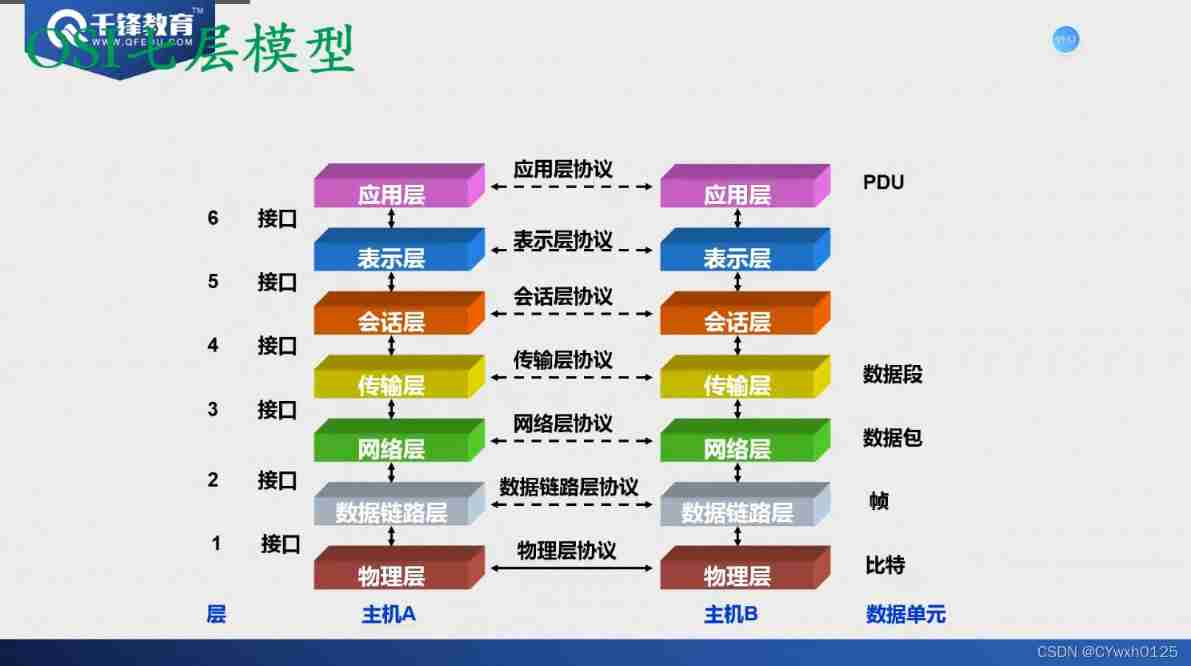
The function and analysis of each layer
(1). The physical layer
It specifies how to realize the lowest physical connection for network communication , And the machinery of physical equipment 、 electrical 、 Functional and process features . Such as : How to use cables and connectors
type 、 Voltage used to transmit signals, etc . It should be noted that , Physical media required in the process of network communication ( Ethernet cable 、 Cable, etc ), In fact, it does not belong to the physical layer , Because of things
Management is actually a rule , Specify various specifications of these physical media devices when connecting to the network 、 Parameters and working mode . But at the same time , Twisted pair 、 Cable and other physics
Media is the realization of physical layer .
(2). Data link layer
Specifies how to address physical addresses 、 How to conduct data on physical lines ( frame frame) Reliable transmission and flow control . The data link layer protocols are SLIP Association
discussion 、CSLIP agreement 、PPP Agreements, etc . Switch , Decode the frame and send the data to the correct receiver according to the information contained in the frame , So the switch works on data
Link layer .
(3). The network layer
Specify which network nodes to pass 、 What kind of network path to send data ( Data packets ) From sender to receiver . In the network layer , Determined the slave node A Sending data
To the node B The network path of , Through which nodes . The network layer can be established LAN communication system , More importantly, it can be in WAN Establish communication in the network system , This is because
It has its own routing address structure , Through routing protocols ( Also known as routable protocol ) Route network communication .
(4). Transport layer
Responsible for overall data transmission and data control , Provide a mechanism for end-to-end data exchange . Transport layer for data ( paragraph ) Split and reorganize , And carry out flow control and
Determine the appropriate transmission rate according to the receiving capacity of the receiver . For example, Ethernet cannot handle greater than 1500 Byte packets , The transport layer divides data into data segments ,
And sequence number the small data segments . The receiver's transport layer will reorganize the data according to the sequence number . The transport layer protocol has TCP agreement 、UDP Agreements, etc .
(5). The session layer
Establish between two nodes in the network 、 Maintain and terminate Communications .
(6). The presentation layer
Format the data between the application and the network , So that it can be understood by the other party . That is, the presentation layer of the sender converts the abstract syntax of the application data into a net
Apply to OSI Transmission syntax of network transmission , The receiver is the opposite . besides , The presentation layer can also encrypt and decrypt data .
(7). application layer
Topmost OSI layer , Network services for applications . E-mail 、 The file transfer function provides protocol support . Application layer protocols include HTTP agreement 、FTP Association
discussion 、SMTP Agreements, etc .
TCP/IP Protocol cluster
And osi The difference between
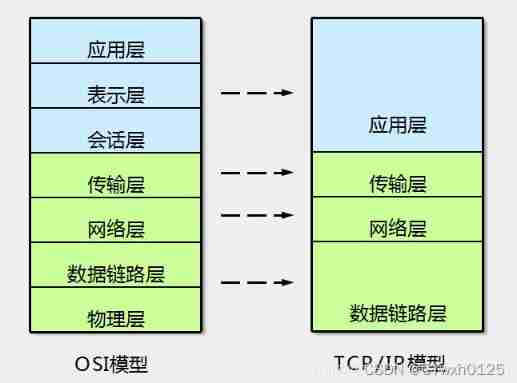
TCP/IP 5 Layer protocol cluster / Protocol stack
data /PDU application layer
Data segment / paragraph Fragment Transport layer
message / package /IP package packet The network layer
frame Frame Data link layer
The bit bit The physical layer
8bit = 1Bvte byte
Data encapsulation and de encapsulation process
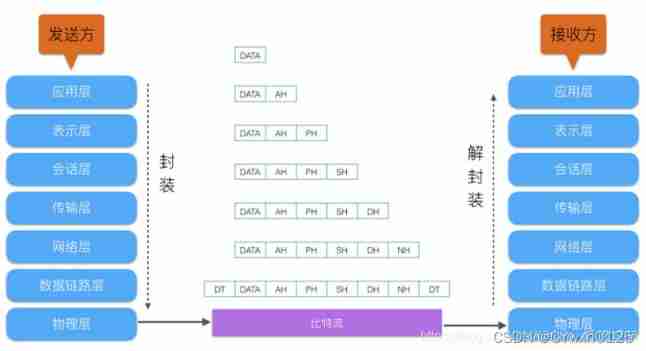
hypothesis from A towards B adopt QQ Send a message
Then the application layer is QQ
The transport layer will add a TCP( Comparison udp slow But it's safe )/UDP( fast , unsafe ) head Target port number
Add one to the network layer IP baotou primary IP And target IP
Data link layer Add MAC Sublayer FCS ( The switch doesn't know IP Know only MAC)
The physical layer Become a bitstream
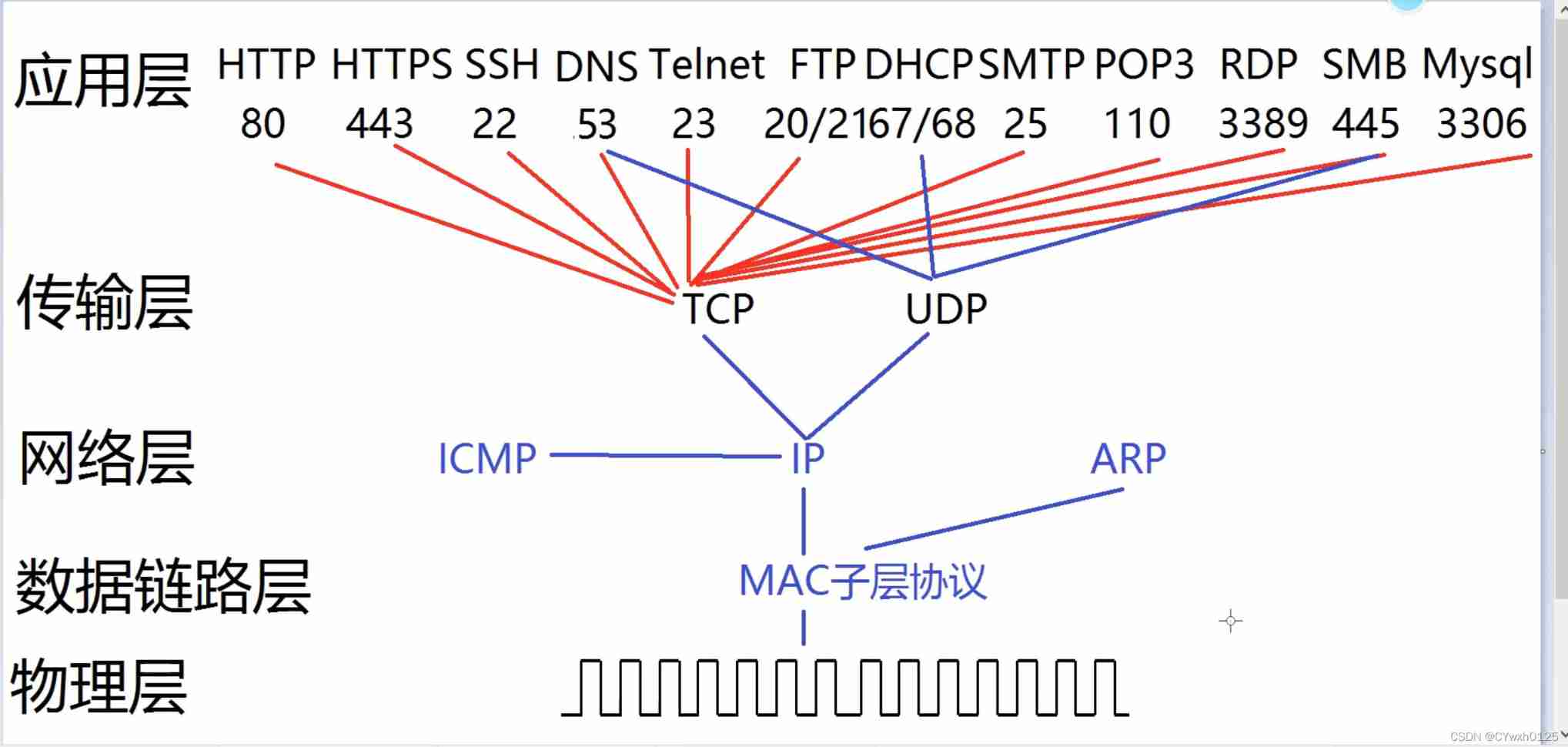
Common protocols and associations at all levels
边栏推荐
- 通讯录(链表实现)
- Require, require in PHP_ once、include、include_ Detailed explanation of the efficiency of repeated introduction of once class library
- laravel-dompdf导出pdf,中文乱码问题解决
- 那些考研后才知道的事
- 2022 machine fitter (Advanced) test question simulation test question bank simulation test platform operation
- Laravel框架运行报错:No application encryption key has been specified
- js 从一个数组对象中取key 和value组成一个新的对象
- 【公开课预告】:视频质量评价基础与实践
- Personal component - message prompt
- Network security HSRP protocol
猜你喜欢
Win10 - lightweight gadget
Jetpack Compose入门到精通
Laravel framework operation error: no application encryption key has been specified

Mmseg - Mutli view time series data inspection and visualization
Convolutional Neural Networks简述
Redis6 transaction and locking mechanism
![[public class preview]: basis and practice of video quality evaluation](/img/d8/a367c26b51d9dbaf53bf4fe2a13917.png)
[public class preview]: basis and practice of video quality evaluation

Brief introduction to revolutionary neural networks
uplad_ Labs first three levels
![[js] basic syntax - for loop](/img/7f/6ddc47c062caa7d39538f88e12b1a0.jpg)
[js] basic syntax - for loop
随机推荐
2022 driller (drilling) examination question bank and simulation examination
About the problem and solution of 403 error in wampserver
redis6数据类型及操作总结
Blue Bridge Cup study 2022.7.5 (morning)
Redis6 master-slave replication and clustering
Jasypt configuration file encryption | quick start | actual combat
内网穿透工具 netapp
牛客网:拦截导弹
Jetpack Compose入门到精通
Record in-depth learning - some bug handling
RK3566添加LED
Solve the problem of "unable to open source file" xx.h "in the custom header file on vs from the source
LeetCode_67(二进制求和)
leetcode 10. Regular expression matching regular expression matching (difficult)
PHP generate Poster
PHP basic syntax
Nantong online communication group
昆仑太科冲刺科创板:年营收1.3亿拟募资5亿 电科太极持股40%
Assembly language - Beginner's introduction
Data Lake (VII): Iceberg concept and review what is a data Lake