当前位置:网站首页>Four methods of exchanging the values of a and B
Four methods of exchanging the values of a and B
2022-07-06 14:38:00 【Wang yeqiang】
In exchange for a,b Value , You may think it's very simple , But if you suddenly think of 4 Methods , Maybe the most basic method of temporary storage with the third variable appears in your mind for a moment , Now I summarize four methods :
initialization a and b:
# About python Replace a b It's worth it Method
a = 3
b = 5
print(" At the beginning of the :a = {} , b = {}".format(a,b))1. Use the third variable c The staging :
def ChangeFirst(a,b): # Take the third variable C The staging
c = a
a = b
b = c
print("ChangeFirst After method exchange :a = {} , b = {}".format(a,b))2. Exchange sum and difference ( The staging ):
def ChangeSecond(a,b): # Use sum and difference
a = a+b
b = a-b
a = a-b
print("ChangeSecond After method exchange :a = {} , b = {}".format(a,b))3. Using bitwise XOR :
def ChangeThird(a,b): # Bitwise XOR ( In binary , Same as 0 Different for 1)
a = a^b
b = a^b
a = a^b
print("ChangeThird After method exchange :a = {} , b = {}".format(a,b))4.Python Proprietary approach :
def ChangeFourth(a,b): #python Proprietary approach
a,b = b,a
print("ChangeFourth After method exchange :a = {} , b = {}".format(a,b))Code runs :
ChangeFirst(a,b)
ChangeSecond(a,b)
ChangeThird(a,b)
ChangeFourth(a,b)Code output :

边栏推荐
- 函数:求1-1/2+1/3-1/4+1/5-1/6+1/7-…+1/n
- Function: find 1-1/2+1/3-1/4+1/5-1/6+1/7-... +1/n
- 《统计学》第八版贾俊平第八章假设检验知识点总结及课后习题答案
- The most popular colloquial system explains the base of numbers
- 指針:最大值、最小值和平均值
- Intel oneapi - opening a new era of heterogeneity
- 《统计学》第八版贾俊平第一章课后习题及答案总结
- Numpy快速上手指南
- [pointer] find the largest string
- 《统计学》第八版贾俊平第十一章一元线性回归知识点总结及课后习题答案
猜你喜欢
Solutions to common problems in database development such as MySQL
MySQL中什么是索引?常用的索引有哪些种类?索引在什么情况下会失效?
Realize applet payment function with applet cloud development (including source code)
“Hello IC World”

线程的实现方式总结
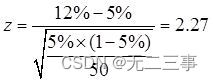
《统计学》第八版贾俊平第八章假设检验知识点总结及课后习题答案
Intranet information collection of Intranet penetration (2)

内网渗透之内网信息收集(二)
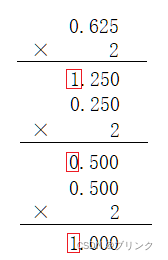
数字电路基础(一)数制与码制
JDBC事务、批处理以及连接池(超详细)
随机推荐
Uibutton status exploration and customization
【指针】数组逆序重新存放后并输出
Function: find the maximum common divisor and the minimum common multiple of two positive numbers
High concurrency programming series: 6 steps of JVM performance tuning and detailed explanation of key tuning parameters
Function: find the root of the equation by Newton iterative method
Pointeurs: maximum, minimum et moyenne
Fundamentals of digital circuit (IV) data distributor, data selector and numerical comparator
How does SQLite count the data that meets another condition under the data that has been classified once
Feature extraction and detection 14 plane object recognition
指针--剔除字符串中的所有数字
浙大版《C语言程序设计实验与习题指导(第3版)》题目集
Attack and defense world misc practice area (GIF lift table ext3)
《统计学》第八版贾俊平第十二章多元线性回归知识点总结及课后习题答案
Statistics 8th Edition Jia Junping Chapter 10 summary of knowledge points of analysis of variance and answers to exercises after class
Statistics 8th Edition Jia Junping Chapter IX summary of knowledge points of classified data analysis and answers to exercises after class
《统计学》第八版贾俊平第十四章指数知识点总结及课后习题答案
5 minutes to master machine learning iris logical regression classification
Statistics 8th Edition Jia Junping Chapter 7 Summary of knowledge points and answers to exercises after class
5分钟掌握机器学习鸢尾花逻辑回归分类
Record an edu, SQL injection practice