当前位置:网站首页>On the idea of vulnerability discovery
On the idea of vulnerability discovery
2022-07-06 14:07:00 【Lazy and talented】
Catalog
Operating system vulnerability discovery
WEB Application vulnerability discovery
CMS Identification and scanning
Unknown CMS( Switch to detailed information collection )
The service agreement ( contain web Security )
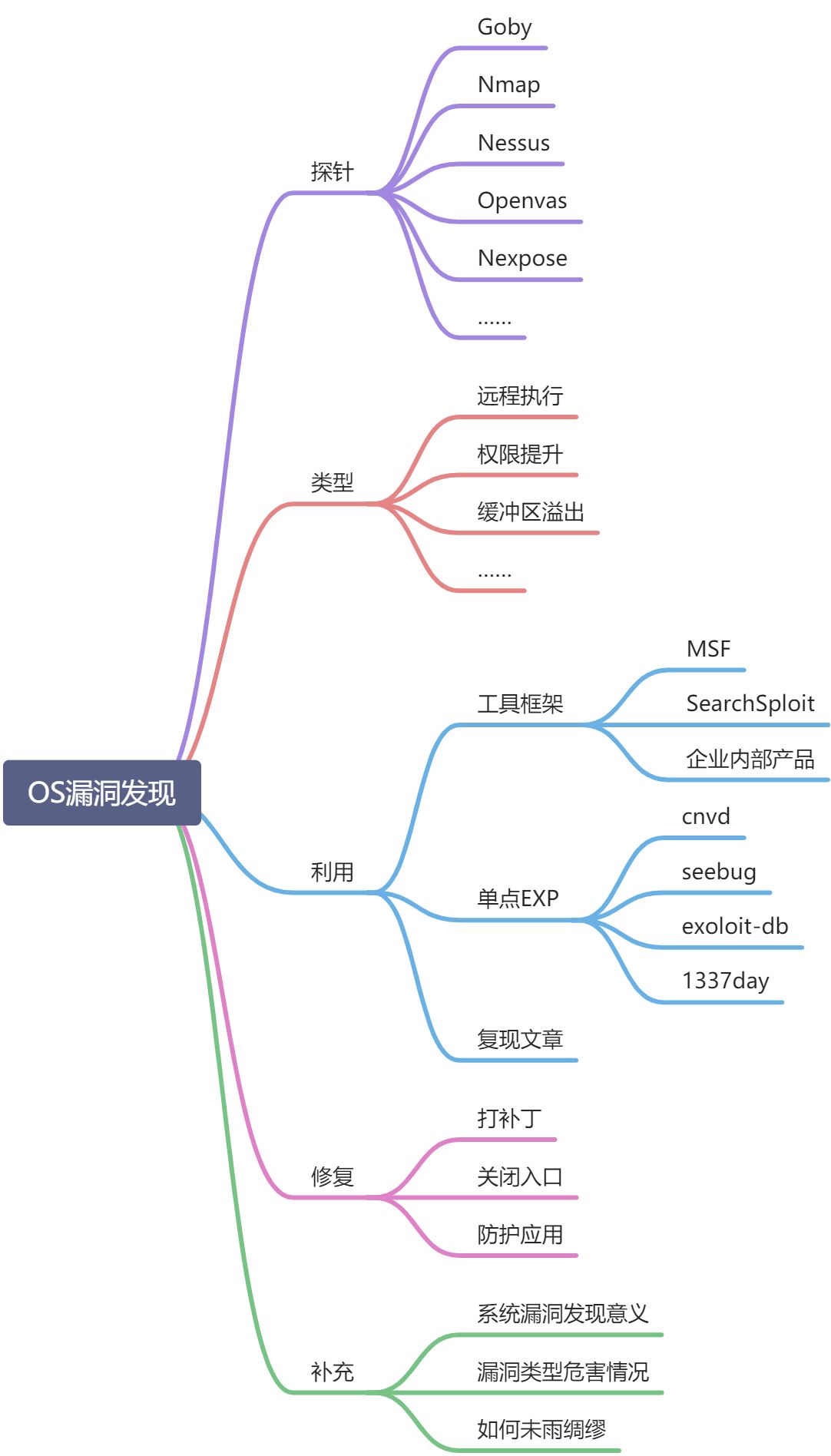
Operating system vulnerability discovery
Brain map
Leakage and
Use the missing scan tool to scan .
Goby
Download address :https://cn.gobies.org/
Usage method :https://cn.gobies.org/features.html
A simple example :
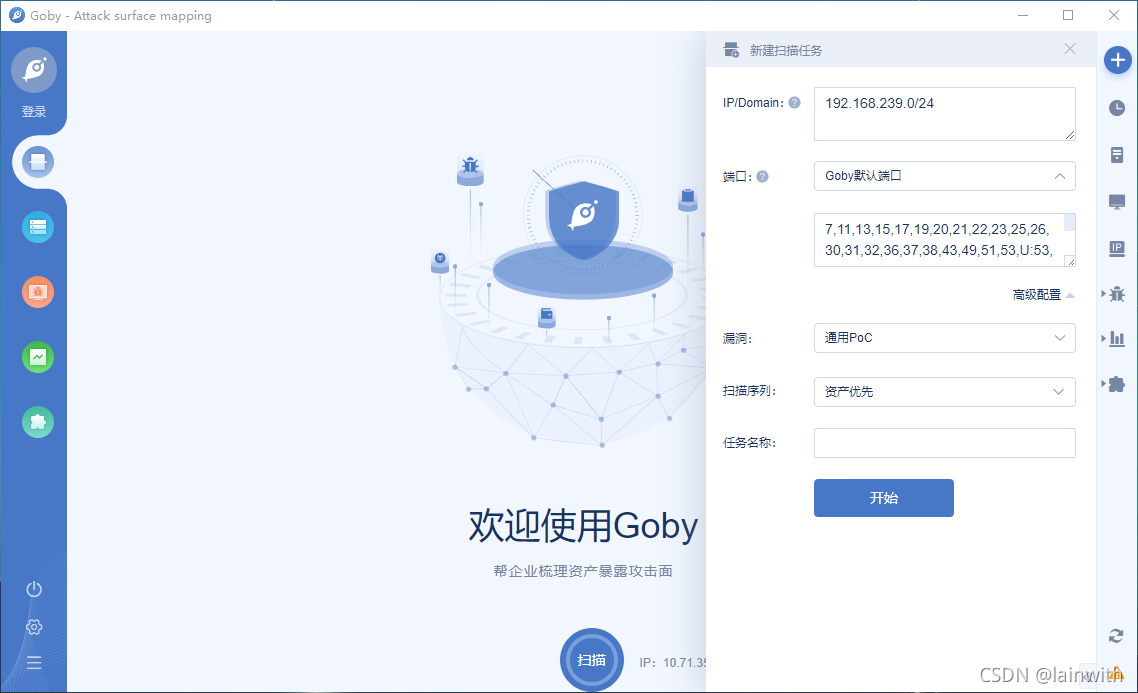
Insert picture description here
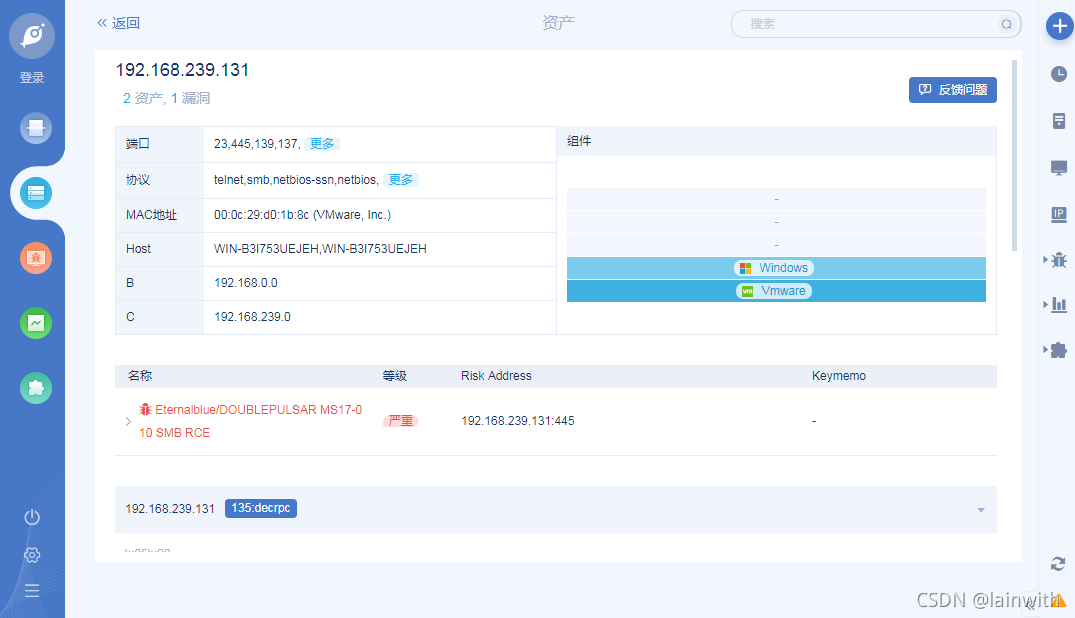
If there are loopholes , You can see directly
Nmap
nmap If you do a missed scan , You can use the built-in missed scan script .
| Port number | Port specification | Direction of attack | |
| 80/443/8080 | common web Service port | web attack , Blast , Corresponding server version vulnerability | |
| 7001/7002 | weblogic Console | java Deserialization , Weak password | |
| 8080/8089 | jboss/Resin?Jetty/Jenkins | Deserialization , Console weak password | |
| 9090 | WebShphere Console | Java Deserialization , Weak password | |
| 4848 | GlassFish Console | Weak password | |
| 1352 | Lotus domino The mail service | Weak password , Information disclosure , Blast | |
| 10000 | Webmin-Web Control panel | Weak password | |
| See the agreement security below for details ... |
CVE scanning :
nmap -script=vuln ip
utilize
The next step is MSF Find the loophole number, a shuttle , I won't go into that
WEB Application vulnerability discovery
Brain map
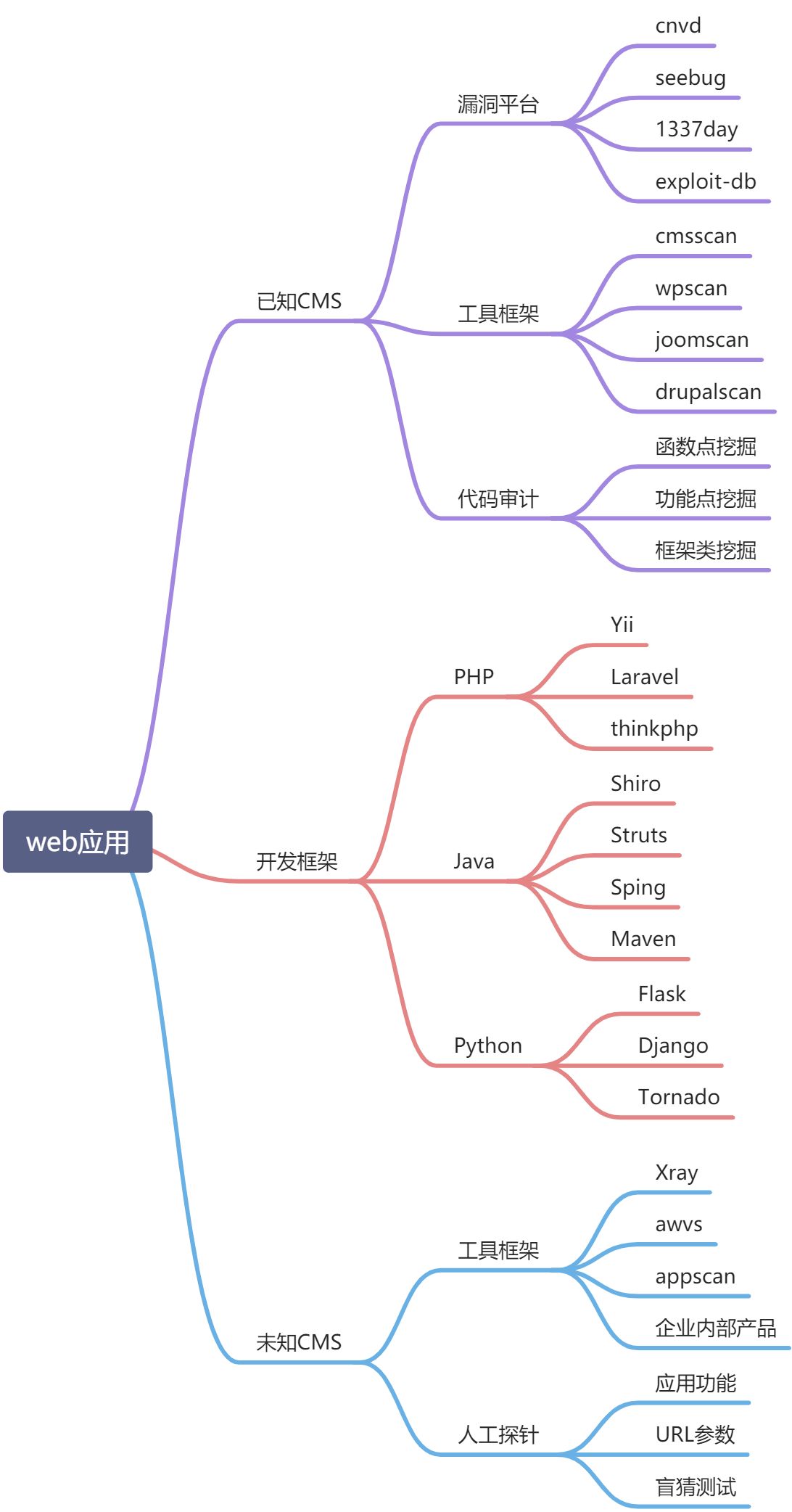
## Ideas
CMS Identification and scanning
Online identification whatcms
Detect which CMS a site is using - What CMS? https://whatcms.org/ Online fingerprint recognition , On-line cms Identify small plug-ins -- Online tools (bugscaner.com)
https://whatcms.org/ Online fingerprint recognition , On-line cms Identify small plug-ins -- Online tools (bugscaner.com) http://whatweb.bugscaner.com/look/
http://whatweb.bugscaner.com/look/
It is known that CMS
As is common dedecms,discuz,wordpress And so on , This is generally developed using non framework classes , However, a few of them adopt framework class development , Security checks for such source programs , To take advantage of open vulnerabilities for testing , If there is no , White box code audit can be used to mine by ourselves
Three major foreign open source enterprises php CMS
drupal 【 No dedicated scanner , however msf Built in modules 】
wordpress 【 There is a special scanner 】
joomla 【 There is a special scanner 】
Development framework
As is common thinkphp,spring,flask And so on , The detection idea of this source program :
First, get the corresponding development framework information ( name , edition ), Then test through the exposed framework class security problems , If it doesn't exist , You can use white box code audit to mine by yourself .
Unknown CMS( Switch to detailed information collection )
Such as the common enterprise or individual internal program source code , It can also be based on CMS Secondary development .
If it can be confirmed that it is based on CMS Secondary development , Just as you know CMS The idea of , If you are not sure , Use conventional scanning tools to detect , Or manual inspection .
APP application
Brain map
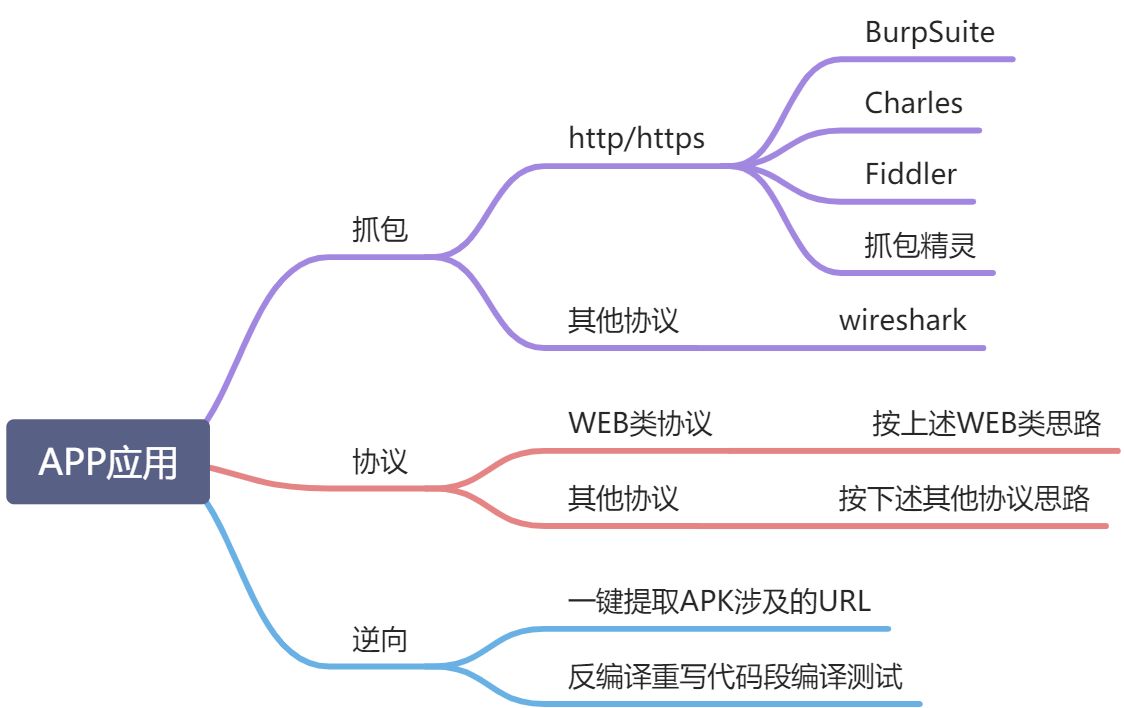
Ideas : obtain APP The site visited at runtime , Then infiltrate the site .
The service agreement ( contain web Security )
Brain map
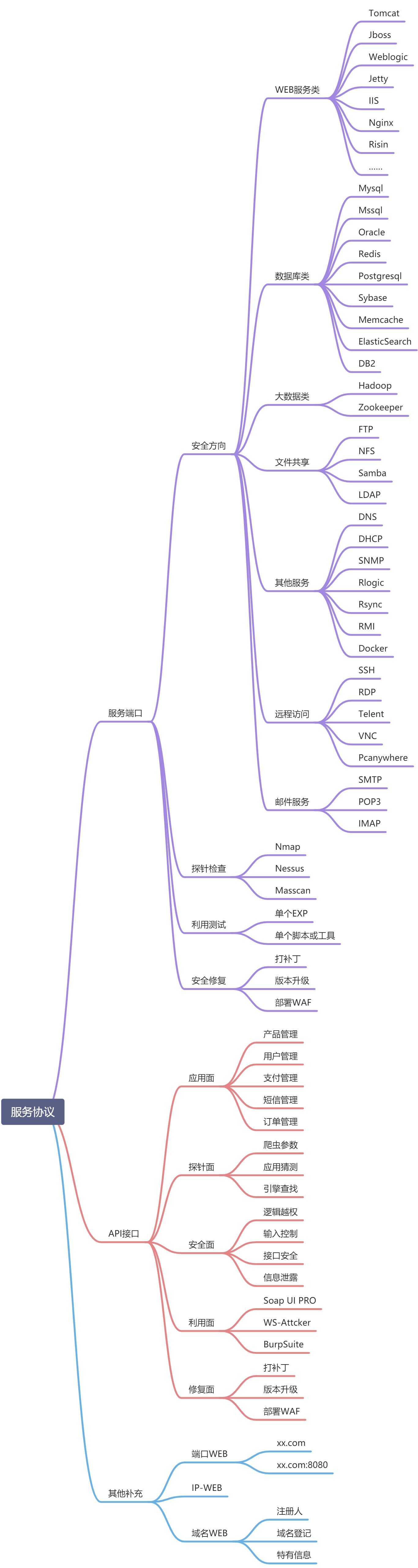
1. web Service
tomcat-- 80/8080/8009
- manager Weak password
- put Upload webshell
- HTTP Slow attack
- ajr The file contains a vulnerability :cve-2020-1938
Jboss --8080
- Weak background password
- Arbitrary file disclosure
- JAVA Deserialization
webSphere --9080
- Weak background password
- Arbitrary file disclosure
- JAVA Deserialization
weblogic --7001/7002
- Weak background password
- console Background deployment war package
- SSRF
- Test page upload webshell
- JAVA Deserialization
- cve-2018-2628
- cve-2018-2893
- cve-2017-10271
- cve-2019-2725
- cve-2019-2729
Glassfish --8080/4848
- Brute force
- Arbitrary file reading
- Authentication bypasses
Jetty --8080
- Remote shared buffer overflow
Apache --80/8080
- HTTP Slow attack
- Parsing vulnerabilities
- Directory traversal
Apache Solr --8983
- Remote command execution
- cve-2017-12629
- cve-2019-0193
IIS --80
- put Upload shell
- IIS Parsing vulnerabilities
- IIS Raise the right
- IIS Remote code execution
- cve-2017-7269
Resin --8080
- Weak background password
Lutos --1352
- Weak background password
- Information disclosure
- Cross-site scripting attacks
Nginx --80/443
- http Slow attack
- Parsing vulnerabilities
2. The database class
Mysql --3306
- Weak password
- Authentication vulnerability
- cve-2012-2122
- Denial of service attacks
- phpmyadmin Universal password 、 Weak password
- UDF、MOF Raise the right
Mssql --1433
- Weak password
- Stored procedure Authorization
Oracle --1521
- Weak password
- TNS Loophole
Redis --6379
- Weak password
- out of buffer
- cve-2014-2669
MongoDB --27001
- Weak password
- Unauthorized access to
DB2 --5000
- Security restrictions bypass unauthorized operations
- cve-2015-1922
SysBase --5000/4100
- Weak password
- Command injection
Memcache --11211
- Unauthorized access
- Configuration vulnerability
ElasticSearch --9200/9300
- Unauthorized access
- Remote code execution
- Document handling
- write in webshell
3. Big data
Hadoop --50010
- Remote command execution
Zookeeper --2181
- Unauthorized access to
4. File sharing
ftp --21
- Weak password
- Anonymous access
- Upload back door
- Remote overflow
- Jump attack
NFS --2049
- Unauthorized access
Samba --137
- Weak password
- Unauthorized access
- Remote code execution cve-2015-0240
LDAP --389
- Weak password
- Inject
- Unauthorized access
5. The remote access
SSH --22
- Weak password
- 28 Fallback vulnerability
- OpenSSL Loophole
- User name enumeration
Telent --23
- Weak password
VNC --5901
- Weak password
- Authentication password bypass
- Denial of service attacks cve-2015-5239
- Elevated privileges cve-2013-6886
Pcanywhere --5632
- Denial of service attacks
- Elevated privileges
- Code execution
X11 --6000
- Unauthorized access to cve-1999-0526
6. The mail service
SMTP --25/465
- Weak password
- Unauthorized access
- Mail forgery
POP3 --110/995
- Weak password
- Unauthorized access
IMAP --143/993
- Weak password
- Arbitrary file reading
7. Other services
DNS --53
- DNS Zone transfer
- DNS hijacked
- DNS cheating
- DNS Cache poisoning
- DNS Tunnel
DHCP --67/68
- DHCP hijacked
- DHCP cheating
SNMP --161
- Weak password
Rlogin --521/513/514
- rlogin Sign in
Rsync --873
- Unauthorized access
- Local privilege promotion
Zabbix --8069
- Remote command execution
RMI --1090/1099
- JAVA Deserialization
Docker --2375
- Unauthorized access to
Reprint  https://blog.csdn.net/weixin_44288604/article/details/120709567
https://blog.csdn.net/weixin_44288604/article/details/120709567
边栏推荐
猜你喜欢
Callback function ----------- callback
Canvas foundation 1 - draw a straight line (easy to understand)
. Net6: develop modern 3D industrial software based on WPF (2)
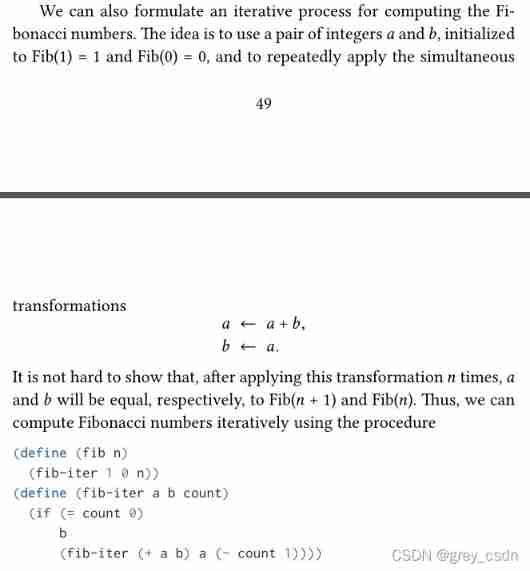
1143_ SiCp learning notes_ Tree recursion
Hackmyvm target series (2) -warrior
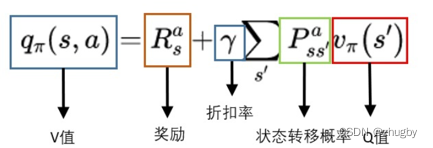
Reinforcement learning series (I): basic principles and concepts
List and data frame of R language experiment III
Strengthen basic learning records

QT meta object qmetaobject indexofslot and other functions to obtain class methods attention

Safe driving skills on ice and snow roads
随机推荐
Beautified table style
2022 Teddy cup data mining challenge question C idea and post game summary
JS several ways to judge whether an object is an array
记一次猫舍由外到内的渗透撞库操作提取-flag
. How to upload XMIND files to Jinshan document sharing online editing?
xray与burp联动 挖掘
HackMyvm靶机系列(1)-webmaster
Renforcer les dossiers de base de l'apprentissage
[err] 1055 - expression 1 of order by clause is not in group by clause MySQL
记一次edu,SQL注入实战
Strengthen basic learning records
Hackmyvm target series (5) -warez
Hackmyvm target series (1) -webmaster
The United States has repeatedly revealed that the yield of interest rate hiked treasury bonds continued to rise
HackMyvm靶机系列(6)-videoclub
浅谈漏洞发现思路
强化学习基础记录
Ucos-iii learning records (11) - task management
Experiment 8 exception handling
7-4 hash table search (PTA program design)