当前位置:网站首页>Fundamentals of digital circuit (IV) data distributor, data selector and numerical comparator
Fundamentals of digital circuit (IV) data distributor, data selector and numerical comparator
2022-07-06 14:34:00 【ブリンク】
Fundamentals of digital circuits ( Four ) Data distributor 、 Data selector and numeric comparator
One 、 Data distributor
In the process of data transmission , The data selector can allocate the data of a certain way to different data channels , This circuit is called a data distributor . abbreviation DEMUX, Generally, there are already input and multiple outputs . The following figure shows the chip integration diagram of a four-way data selector :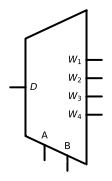
It can be D Send to the channel selected by the data variable , The following figure is the truth table of the data selector :
You can see , A A A and B B B The two digits represent the binary code of the output circuit , It is called selection input . The function expression of each path is :
W 0 = D A B ‾ W_0=D\overline{AB} W0=DAB
W 1 = D A ‾ B W_1=D\overline{A}B W1=DAB
W 2 = D A B ‾ W_2=DA\overline{B} W2=DAB
W 0 = D A B W_0=DAB W0=DAB
Two 、 Data selector
Data selector abbreviation MUX. Its logic function is under the control of address selection signal , Select one output from multiple data .
74153 It is a data selector of one out of four , The following figure shows its chip pin distribution :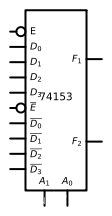
among A 0 A_0 A0, A 1 A_1 A1 Is the address selector , E ‾ \overline{E} E Is the enable end , Only if it is entered as 0 when , Data selector can work , Otherwise, the two outputs will output 0.
74151 It is a one out of eight data selector , The following figure shows its chip pin distribution :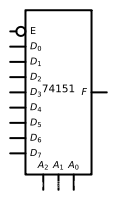
E E E The end is the enabling end , Only if it is 0 when , Data selector will work , Otherwise, the output end outputs 0; Because it is an eight bit selector , So we need A 0 A_0 A0 A 1 A_1 A1 A 2 A_2 A2 Three bit selector ( 2 3 = 8 2^3=8 23=8) The picture below is 74151 My menu :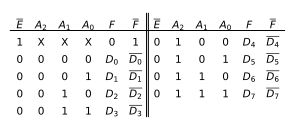
The output logic function of the data selector is in the form of and or of the sum of the minimum terms , So we can use data selector to realize any logic function .
3、 ... and 、 Numerical comparator
The function of numerical comparator is to compare the size of two binary numbers .
How does the numerical comparator realize comparison ? Suppose there are two four bit binary numbers A = A 3 A 2 A 1 A 0 A=A_3A_2A_1A_0 A=A3A2A1A0 and B = B 3 B 2 B 1 B 0 B=B_3B_2B_1B_0 B=B3B2B1B0, To compare the size of these two numbers, start from the highest order , If the highest order is not equal , Then it can be said that the number with the largest highest position is larger , The number with the smaller highest position is smaller ; If the highest order is equal , Compare the next , Again , If this bit is not equal , It means that the larger one is , This means that the smaller number is smaller , If this one is also equal , Then continue to compare the next , Until we can distinguish the size of these two numbers .
1. One digit value comparator
First, the truth table of a one digit numerical comparator is given :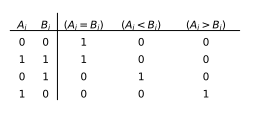
You can write an expression according to the truth table :
( A i = B i ) = A i ⊕ B i ‾ (A_i=B_i)=\overline{A_i\oplus B_i} (Ai=Bi)=Ai⊕Bi
( A i < B i ) = A i ‾ B i (A_i<B_i)=\overline{A_i}B_i (Ai<Bi)=AiBi
( A i > B i ) = A i B i ‾ (A_i>B_i)=A_i\overline{B_i} (Ai>Bi)=AiBi
Connect the logic diagram according to the expression .
2. Four digit value comparator
The following figure is the truth table of the four digit numeric comparator :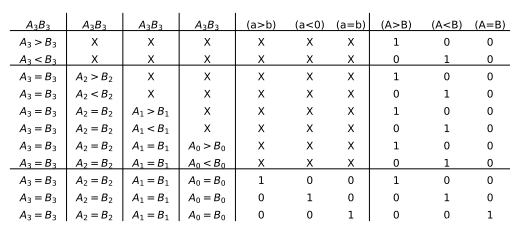
No 2-3 Line description as long as the highest order is not equal , Then you can judge the size
In the table 4-9 Row is the case when the highest bits are equal , At this time, it is relatively low , Finally, you can also compare the size
The last three rows in the table are the cases where each of the two numbers is equal , The result at this time is determined by the state of the cascade input , Which cascade input is 1, Then the output of the corresponding output end is 1.
first draft 2022/5/7
边栏推荐
- 函数:求1-1/2+1/3-1/4+1/5-1/6+1/7-…+1/n
- Sqqyw (indifferent dot icon system) vulnerability recurrence and 74cms vulnerability recurrence
- 《统计学》第八版贾俊平第十一章一元线性回归知识点总结及课后习题答案
- 指针--剔除字符串中的所有数字
- 《统计学》第八版贾俊平第十三章时间序列分析和预测知识点总结及课后习题答案
- Hcip -- MPLS experiment
- How does SQLite count the data that meets another condition under the data that has been classified once
- 《统计学》第八版贾俊平第十四章指数知识点总结及课后习题答案
- Ucos-iii learning records (11) - task management
- 浅谈漏洞发现思路
猜你喜欢
攻防世界MISC练习区(SimpleRAR、base64stego、功夫再高也怕菜刀)
Attack and defense world misc practice area (GIF lift table ext3)
Chain team implementation (C language)
JDBC read this article is enough
Statistics 8th Edition Jia Junping Chapter 10 summary of knowledge points of analysis of variance and answers to exercises after class
Hackmyvm target series (2) -warrior
Circular queue (C language)

循环队列(C语言)

关于交换a和b的值的四种方法
![New version of postman flows [introductory teaching chapter 01 send request]](/img/0f/a41a39093a1170cc3f62075fd76182.jpg)
New version of postman flows [introductory teaching chapter 01 send request]
随机推荐
Load balancing ribbon of microservices
Mathematical modeling idea of 2022 central China Cup
Intranet information collection of Intranet penetration (3)
SQL注入
《统计学》第八版贾俊平第七章知识点总结及课后习题答案
High concurrency programming series: 6 steps of JVM performance tuning and detailed explanation of key tuning parameters
《统计学》第八版贾俊平第九章分类数据分析知识点总结及课后习题答案
Record an edu, SQL injection practice
MySQL中什么是索引?常用的索引有哪些种类?索引在什么情况下会失效?
【指针】统计一字符串在另一个字符串中出现的次数
指针 --按字符串相反次序输出其中的所有字符
Applet Web Capture -fiddler
《统计学》第八版贾俊平第十一章一元线性回归知识点总结及课后习题答案
Based on authorized access, cross host, and permission allocation under sqlserver
《统计学》第八版贾俊平第十四章指数知识点总结及课后习题答案
SQL injection
网络基础之路由详解
Sentinel overall workflow
Hackmyvm target series (1) -webmaster
Statistics 8th Edition Jia Junping Chapter IX summary of knowledge points of classified data analysis and answers to exercises after class