当前位置:网站首页>Based on authorized access, cross host, and permission allocation under sqlserver
Based on authorized access, cross host, and permission allocation under sqlserver
2022-07-06 14:21:00 【Code siege lion】
1. Open the remote access rights of the installed database ;
To the server to be accessed , The login mode set in security is sql server and windows Authentication mode login 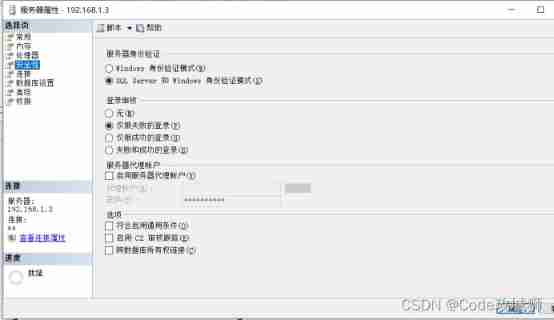
Sign in sa After account , In the status bar , Allow connections to the database engine 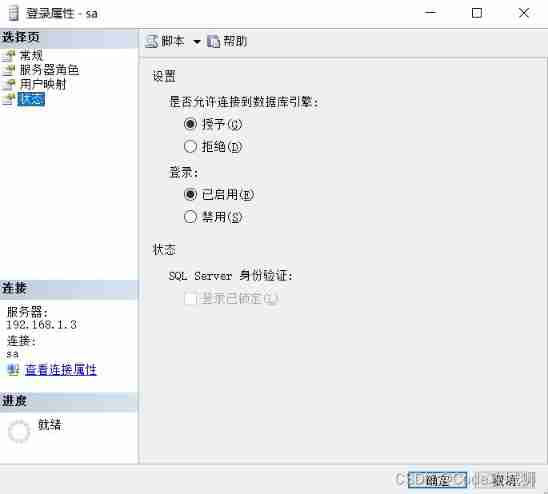
2. Create a user , Grant them access to the database ;
– Create a login account
create login xuniji with password=‘123456’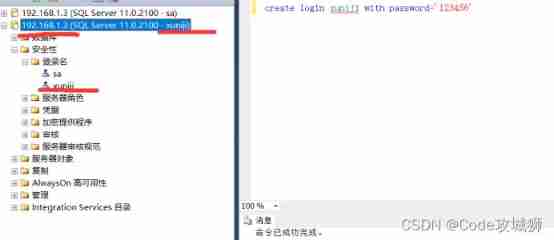
When the host acts as a client , use sa Account login to access the server of the virtual machine
It uses the host's (192.168.1.2) Of DBMS, Account sa, The address to visit is 192.168.1.3
use xuniji When logging in to this account , It is forbidden to log in and access the database without authorization 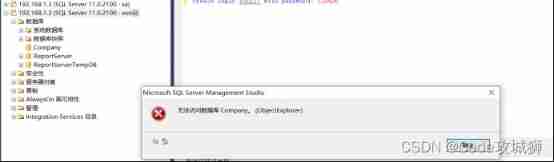
After authorization :
use Company This sentence is indispensable , If it is to let the login user access a specific database
– Create database users
create user xuniji for login xuniji with default_schema=dbo
Access all databases : Access all databases without adding use company
EXEC sp_grantdbaccess ‘xuniji’
GO
You can visit
3. The query and insert permissions of one or more specific tables form a role , And grant it to the user ;
grant select,insert on Department to xuniji
grant select,insert on Employees to xuniji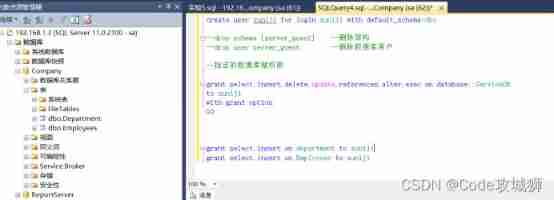
This statement gives the permission to query and insert to xuniji The name of this character , It can also be called login , Because I created one before xuniji The role name of and the login name of a virtual machine , Mapping relationship has been established , So there is no need to map here 
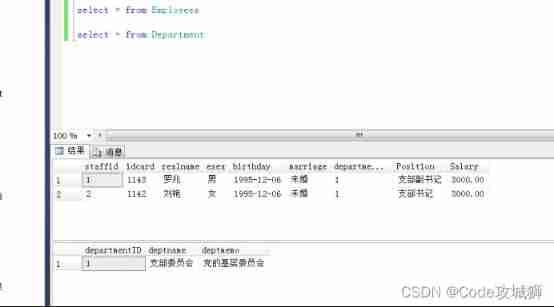
After authorization, both insert and query can be executed successfully , The authorization here is to use the host sa Account authorization , And I insert and query with xuniji This account .
4. Choose a partner in the class or group , Let it access remotely through the set user , And complete and insert
operation ;
I used it 3 Middle method implementation :
One 、 The first is to establish a simulated environment through virtual machines (windows7x64 position ,sqlserver2012).
Two 、 The second is to connect the computer directly with two network cables
3、 ... and 、 The third way is to connect through the LAN under the router
1、 The two machines to establish remote access must be in the same network segment .
Hosts and virtual machines ( Machines that need access ) Both must be in the same network segment
The gateway I set is 192.168.1.1
host IP The address is 192.168.1.2
virtual machine IP The address is 192.168.1.3
among 192.168.1.0 Cannot set , Because this is the broadcast address
The subnet mask is set to 255.255.255.0( Subnet mask is used to allocate address space )
My address space allocation space is 2~254 All the machines in the segment can access each other .
virtual machine :IP Address 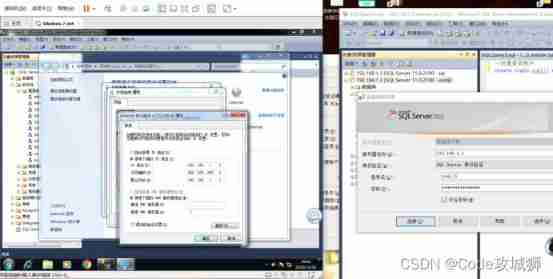
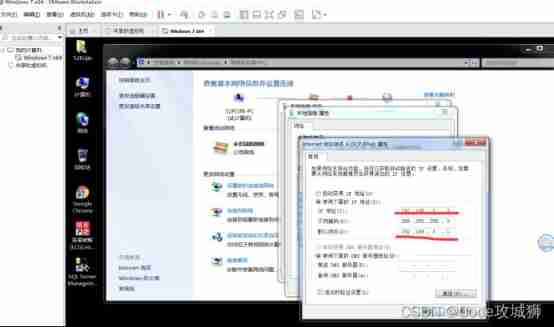
W1064 Bit host IP Address :
( After the environment is established, pass the command ping Conduct ping through )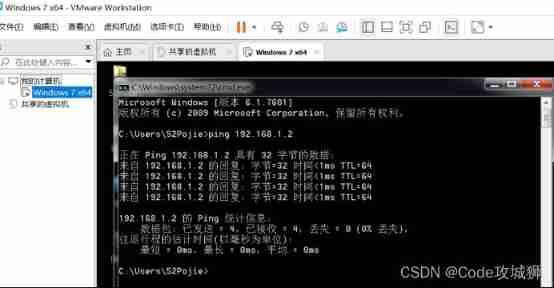
2、 commonly windows7 In the environment , There is no need to change the port. The default is 1433 port , But my host (windows10,sqlserver12) Port is not 1433 Need to use sqlserver Configure in the configuration manager
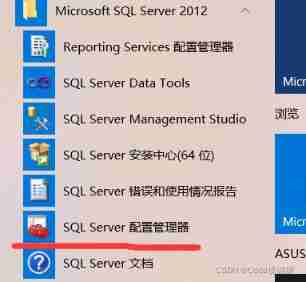
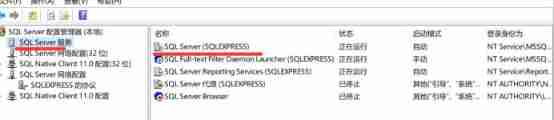
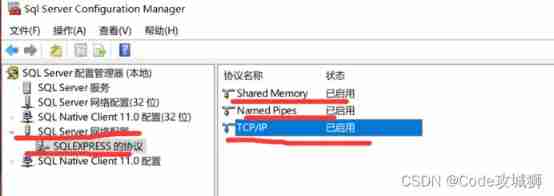
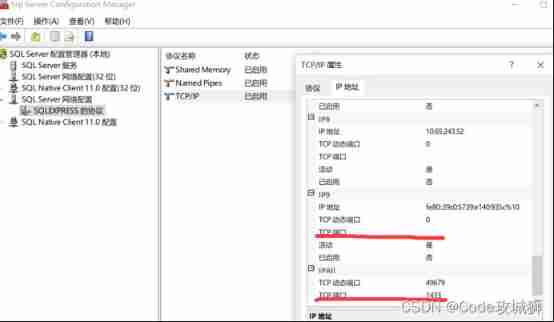
Windows10 Generally, the default port is empty , Can be in IPall Set in the for 1433.
3、 Login with user name and password sa Login is usually the user with the highest permission , Generally, the login name is set in the target machine that needs to be accessed ( This login name is usually not sa):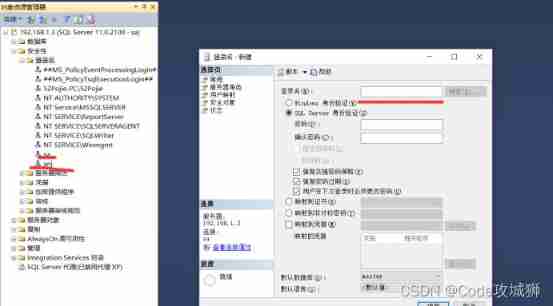
virtual machine (192.168.1.3) Go to the database Company323 There is no table
5. Withdraw the insert permission of the table .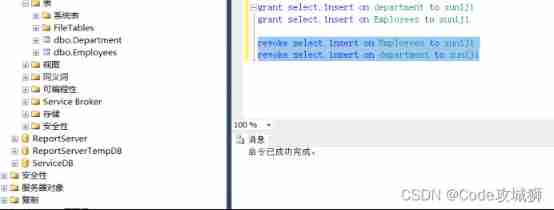
When I finish deleting authorization , You cannot insert any more :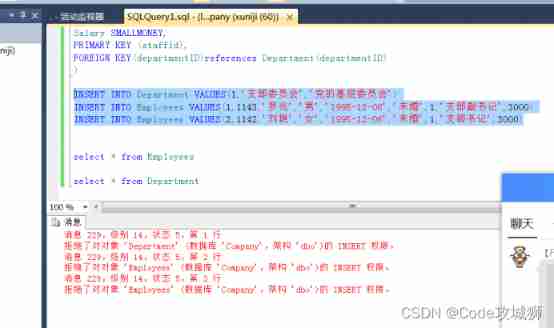
边栏推荐
- Captcha killer verification code identification plug-in
- [dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i
- Wei Shen of Peking University revealed the current situation: his class is not very good, and there are only 5 or 6 middle-term students left after leaving class
- WEB漏洞-文件操作之文件包含漏洞
- Experiment 6 inheritance and polymorphism
- Mixlab unbounded community white paper officially released
- Strengthen basic learning records
- 7-8 7104 Joseph problem (PTA program design)
- [experiment index of educator database]
- 【头歌educoder数据表中数据的插入、修改和删除】
猜你喜欢
Nuxtjs quick start (nuxt2)
强化学习基础记录
sqqyw(淡然点图标系统)漏洞复现和74cms漏洞复现
7-5 staircase upgrade (PTA program design)

How to turn wechat applet into uniapp
Intranet information collection of Intranet penetration (2)
网络基础之路由详解
Record once, modify password logic vulnerability actual combat
Captcha killer verification code identification plug-in
Strengthen basic learning records
随机推荐
实验七 常用类的使用
An unhandled exception occurred when C connected to SQL Server: system Argumentexception: "keyword not supported:" integrated
[three paradigms of database] you can understand it at a glance
captcha-killer验证码识别插件
Renforcer les dossiers de base de l'apprentissage
HackMyvm靶机系列(2)-warrior
网络层—简单的arp断网
The United States has repeatedly revealed that the yield of interest rate hiked treasury bonds continued to rise
小程序web抓包-fiddler
链队实现(C语言)
Poker game program - man machine confrontation
Sword finger offer 23 - print binary tree from top to bottom
What language should I learn from zero foundation. Suggestions
7-1 output all primes between 2 and n (PTA programming)
网络基础详解
Which is more advantageous in short-term or long-term spot gold investment?
记一次api接口SQL注入实战
Experiment five categories and objects
搭建域环境(win)
浅谈漏洞发现思路