当前位置:网站首页>Attack and defense world misc practice area (GIF lift table ext3)
Attack and defense world misc practice area (GIF lift table ext3)
2022-07-06 14:11:00 【Unknown white hat】
Catalog
Put the target file in kali To mount
gif
Topic introduction
Their thinking
Open the attachment


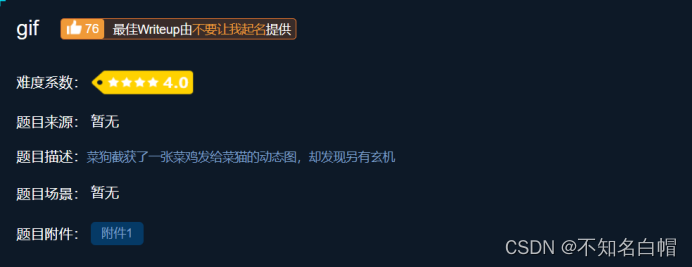
The content is in black and white , Guess it may be binary numbers , And altogether 104(0-103) A picture , We assume that white is 0, Black is 1, Every time 8 In groups ASCII decode .
ASCII decode
Convert pictures into binary digits
01100110 01101100 01100001 01100111 01111011 01000110 01110101 01001110 01011111 01100111 01101001 01000110 01111101
Binary to ASCII Address :https://coding.tools/cn/binary-to-text
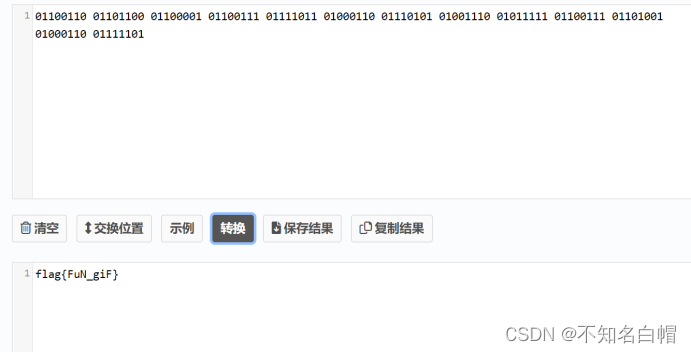
find flag
flag{FuN_giF}
Lift the table
Topic introduction
Their thinking
Decoding ciphertext
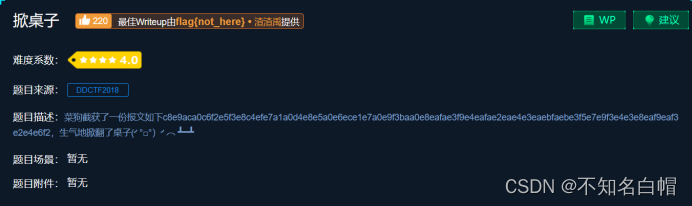
c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2
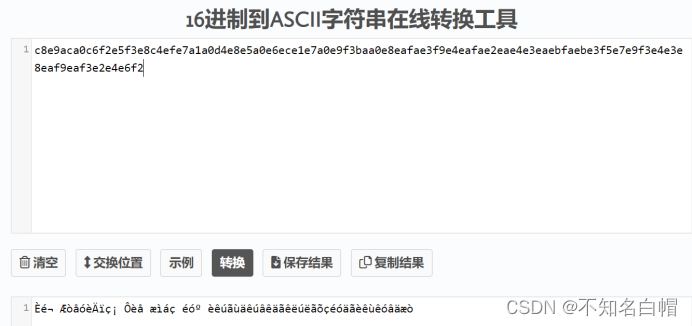
Check it out. ASCII clock
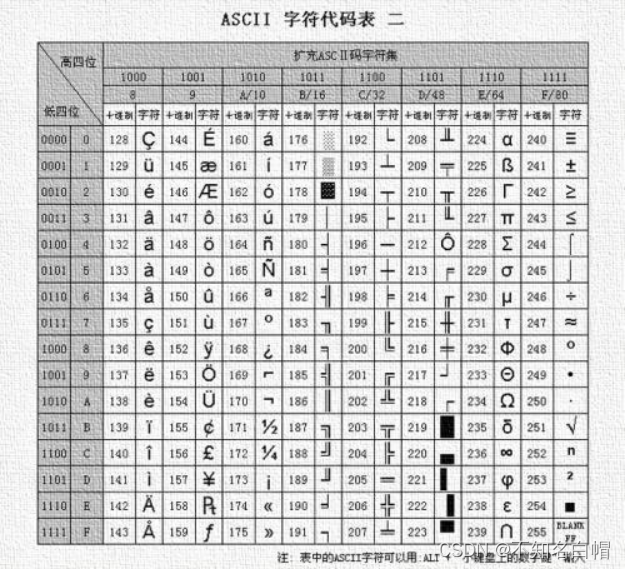
According to our observation, we find that , The string obtained is obviously 128-255 Part of the .
So we think about what we get ascii Code to get the remainder
Yes ASCII Take the rest
flag = ''
s='c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2'
l = len(s)//2
for i in range(l):
flag += chr(int(s[i*2:(i+1)*2], 16) % 128)
print(flag, end='')python Run URL :https://c.runoob.com/compile/9/
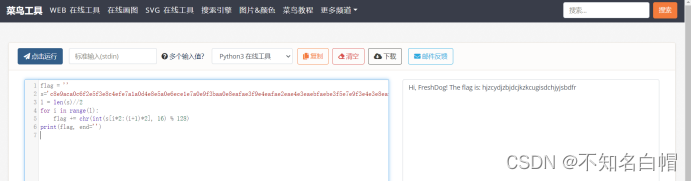
find flag
flag{hjzcydjzbjdcjkzkcugisdchjyjsbdfr}
ext3
Topic introduction
Their thinking
Put the target file in kali To mount
┌──(root㉿kali)-[~/Desktop]
└─# mkdir xctf-misc
┌──(root㉿kali)-[~/Desktop]
└─# ls
Burp_Suite_Pro_v2020.1.1 f1fc23f5c743425d9e0073887c846d23 vulhub xctf-misc
┌──(root㉿kali)-[~/Desktop]
└─# mount f1fc23f5c743425d9e0073887c846d23 xctf-misc/
┌──(root㉿kali)-[~/Desktop]
└─# cd xctf-misc
┌──(root㉿kali)-[~/Desktop/xctf-misc]
└─# ls
02CdWGSxGPX.bin 0wDq5 3J 7H7geLlS5 8RxQG4bvd h i jj LO0J8 m9V0lIaElz Nv orcA Q Raf3SYj sdb.cramfs T
0GY1l 0Xs 44aAm 8A2MFawD4 FinD H imgLDPt4BY KxEQM lost+found MiU o oSx2p qkCN8 rhZE1LZ6g sn TFGVOSwYd.txt
0h3a5 1 4A 8DQFirm0D fm H2Zj8FNbu ix1EMRHRpIc2 LG6F LvuGM Mnuc O7avZhikgKgbF OT QmUY1d Ruc9 SPaK8l2sYN
0l 2X 6JR3 8HhWfV9nK1 g hdi7 j6uLMX Lh lWIRfzP n o8 poiuy7Xdb QQY3sF63w RZTOGd SrZznhSAj
0qsd 3 6wUaZE1vbsW 8nwg gtj hYuPvID jE LlC6Z0zrgy.bin m NgzQPW OOoOs px6u r scripts t
┌──(root㉿kali)-[~/Desktop/xctf-misc]
└─# find / -name flag.txt
/root/Desktop/xctf-misc/O7avZhikgKgbF/flag.txt
┌──(root㉿kali)-[~/Desktop/xctf-misc]
└─# cd O7avZhikgKgbF
┌──(root㉿kali)-[~/Desktop/xctf-misc/O7avZhikgKgbF]
└─# ls
flag.txt
┌──(root㉿kali)-[~/Desktop/xctf-misc/O7avZhikgKgbF]
└─# cat flag.txt
ZmxhZ3tzYWpiY2lienNrampjbmJoc2J2Y2pianN6Y3N6Ymt6an0=
Conduct base64 decode
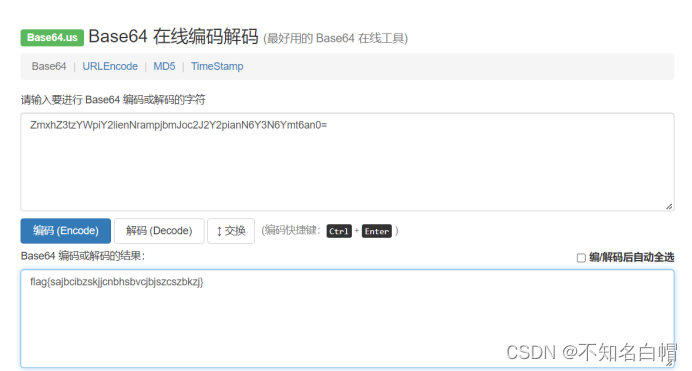
find flag
flag{sajbcibzskjjcnbhsbvcjbjszcszbkzj}
边栏推荐
- Record once, modify password logic vulnerability actual combat
- msf生成payload大全
- 7-15 h0161. 求最大公约数和最小公倍数(PTA程序设计)
- Hackmyvm target series (5) -warez
- 记一次猫舍由外到内的渗透撞库操作提取-flag
- Record an API interface SQL injection practice
- Applet Web Capture -fiddler
- 攻防世界MISC练习区(SimpleRAR、base64stego、功夫再高也怕菜刀)
- [err] 1055 - expression 1 of order by clause is not in group by clause MySQL
- Harmonyos JS demo application development
猜你喜欢
captcha-killer验证码识别插件
强化学习基础记录
Attach the simplified sample database to the SQLSERVER database instance
7-5 走楼梯升级版(PTA程序设计)
xray与burp联动 挖掘
网络层—简单的arp断网
Intranet information collection of Intranet penetration (I)
浅谈漏洞发现思路
Canvas foundation 1 - draw a straight line (easy to understand)
Web vulnerability - File Inclusion Vulnerability of file operation
随机推荐
[three paradigms of database] you can understand it at a glance
XSS之冷门事件
Safe driving skills on ice and snow roads
How to turn wechat applet into uniapp
. Net6: develop modern 3D industrial software based on WPF (2)
Hackmyvm Target Series (3) - vues
Build domain environment (win)
7-11 mechanic mustadio (PTA program design)
7-9 make house number 3.0 (PTA program design)
Poker game program - man machine confrontation
Read only error handling
附加简化版示例数据库到SqlServer数据库实例中
3. Input and output functions (printf, scanf, getchar and putchar)
Programme de jeu de cartes - confrontation homme - machine
7-7 7003 组合锁(PTA程序设计)
【VMware异常问题】问题分析&解决办法
记一次edu,SQL注入实战
Wechat applet
Hackmyvm target series (6) -videoclub
《英特尔 oneAPI—打开异构新纪元》