当前位置:网站首页>Captcha killer verification code identification plug-in
Captcha killer verification code identification plug-in
2022-07-06 14:17:00 【Lazy and talented】
Catalog
Configuration of the environment
The first step in actual combat How to grab the bag
The second step of actual combat Interface configuration
The third step in actual combat Setting of blasting module
Configuration of the environment
Plug in download address GitHub - broken5/captcha-killer-java8 https://github.com/broken5/captcha-killer-java8
https://github.com/broken5/captcha-killer-java8
0x01 effect
In the current actual combat mining src Or penetration testing Most verification codes cannot be bypassed . Want to enter the background page by blasting . repeat After module test , The verification code cannot be bypassed , use captcha-killer Be able to identify the verification code . Then conduct weak password blasting .
0x02 Installing a plug-in
jar Installation of skipped The effect of successful installation is as follows
The first step in actual combat How to grab the bag
0x01 Intercept the verification code package
After intercepting here, there will be no porxy It shows that however history You can view packets
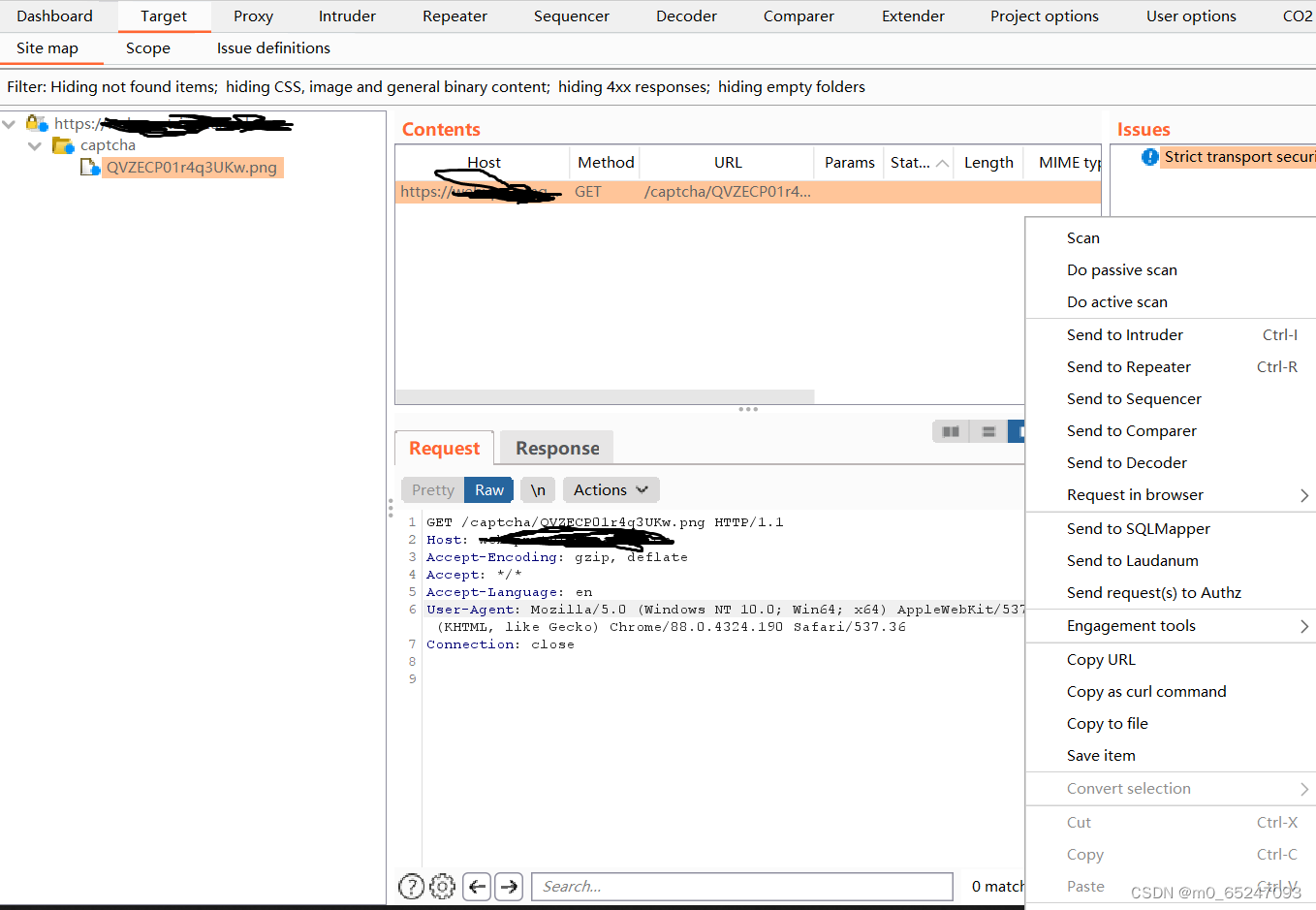
0x02 Send package
Send the verification code package to captcha-killer As shown in the figure above, there is no extension by right clicking
First send the package to repeat in And then repeat Send to capcha-killer modular
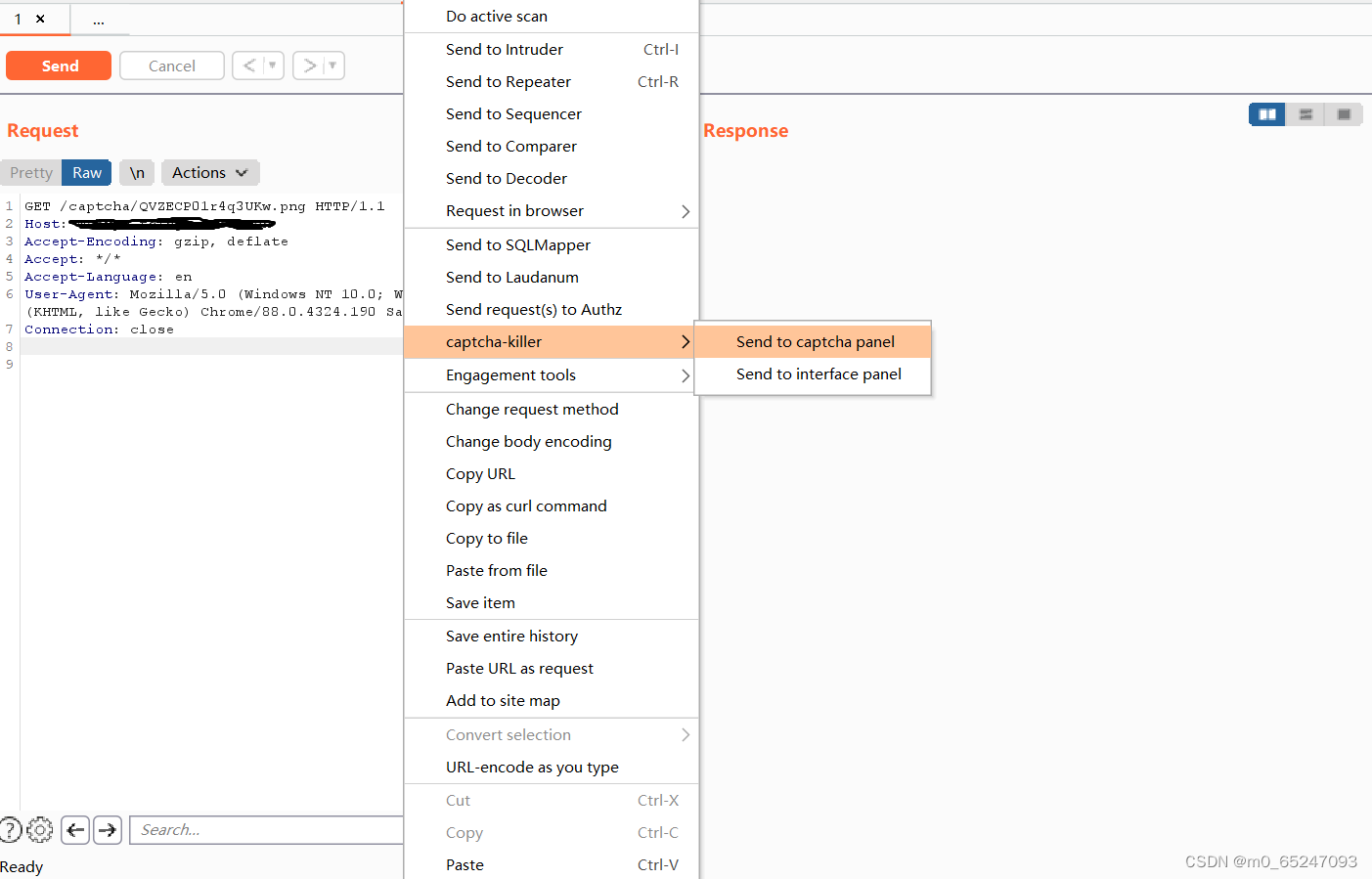
Send successfully, click to get
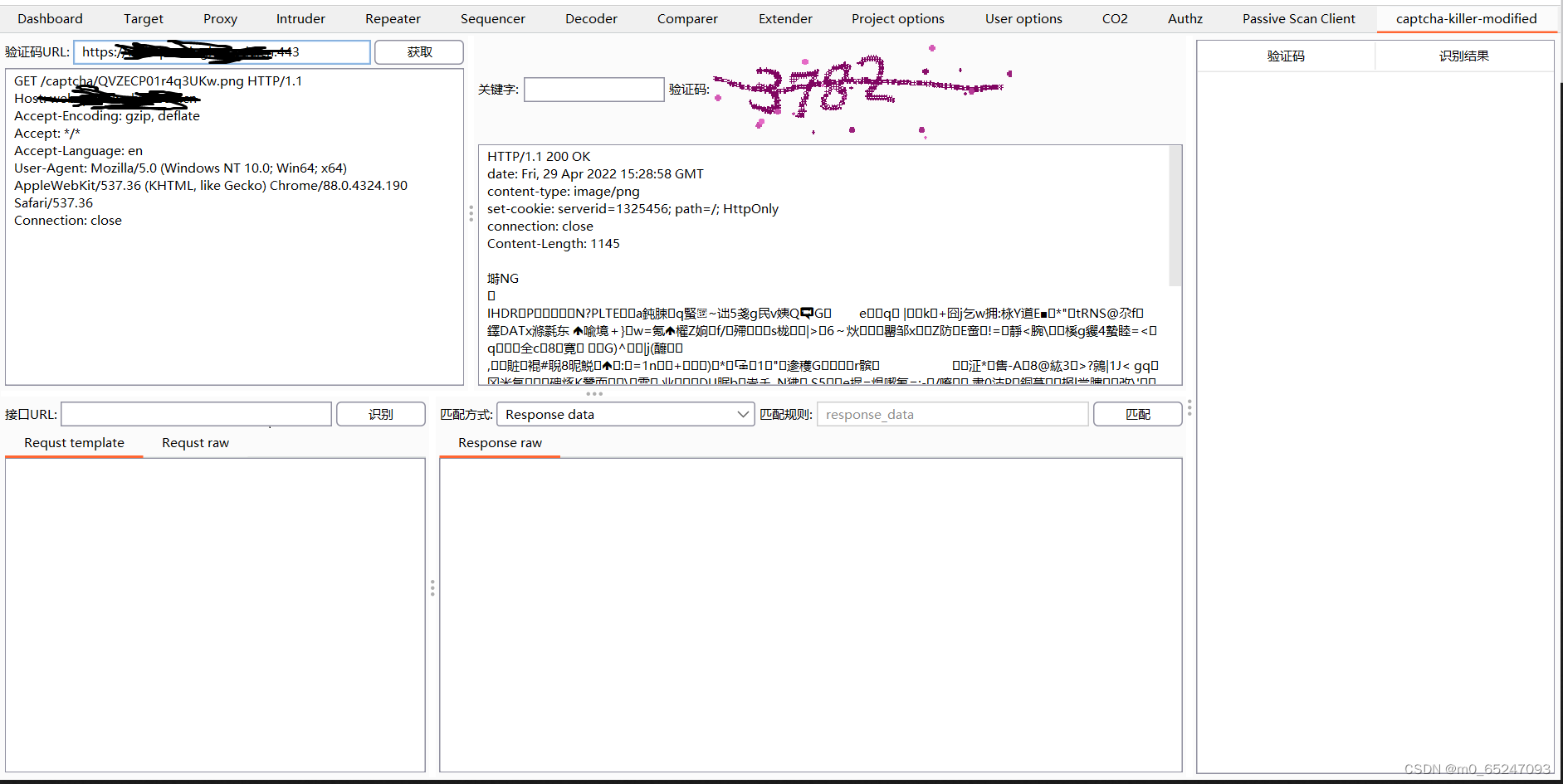
The second step of actual combat Interface configuration
0x01 Interface configuration
The interface here is cloud coding platform ( The error rate is probably 5%):
POST /predict HTTP/1.1
Host: api.ttshitu.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Accept: application/json;
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: Hm_lvt_d92eb5418ecf5150abbfe0e505020254=1585994993,1586144399; SESSION=5ebf9c31-a424-44f8-8188-62ca56de7bdf; Hm_lpvt_d92eb5418ecf5150abbfe0e505020254=1586144399
Connection: close
Content-Type: application/json;charset=UTF-8
Content-Length: 109
{"username":" account number ","password":" password ","typeid":"3","image":"<@BASE64><@IMG_RAW></@IMG_RAW></@BASE64>"}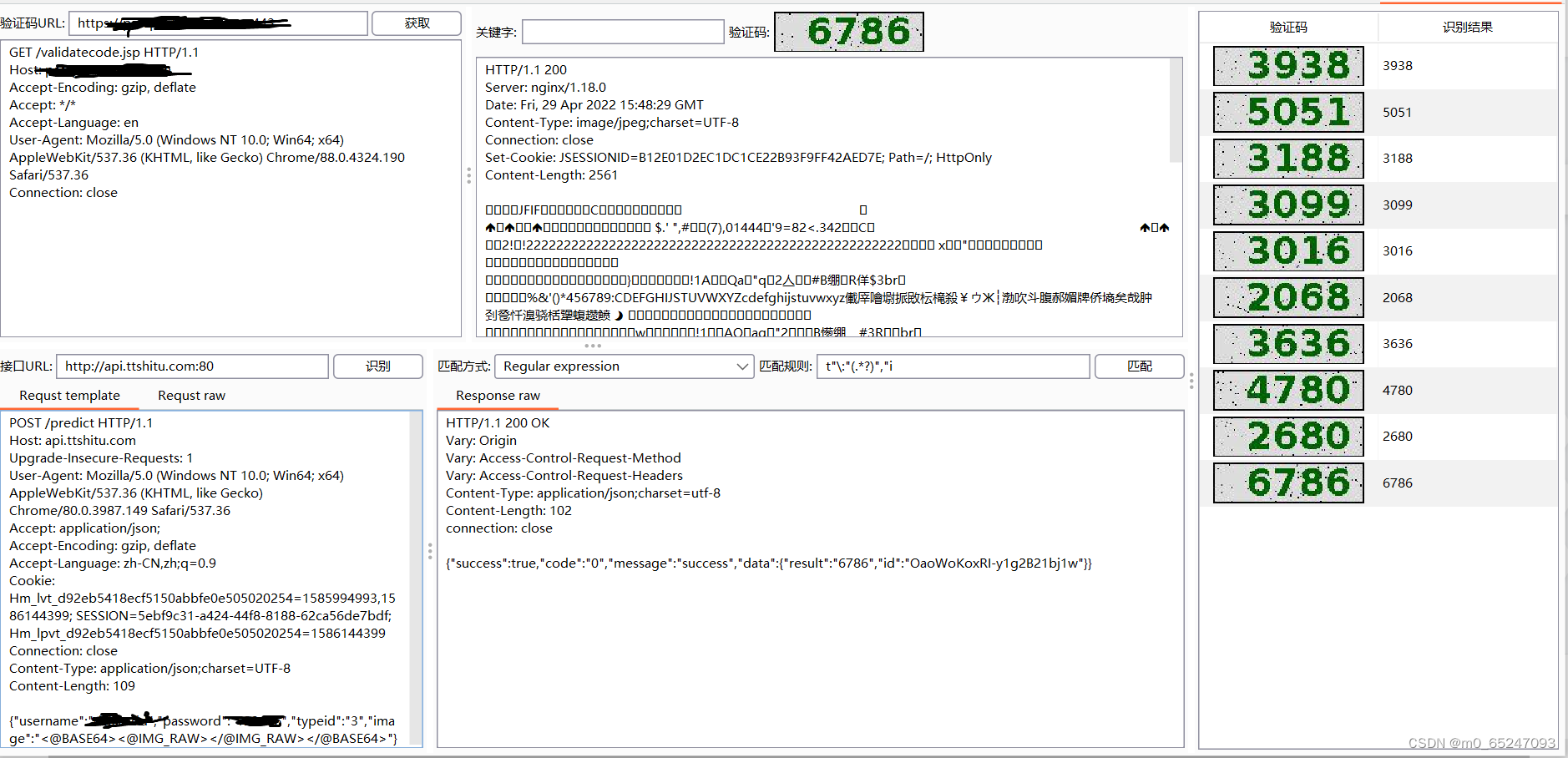
The recognition rate is shown in the figure above
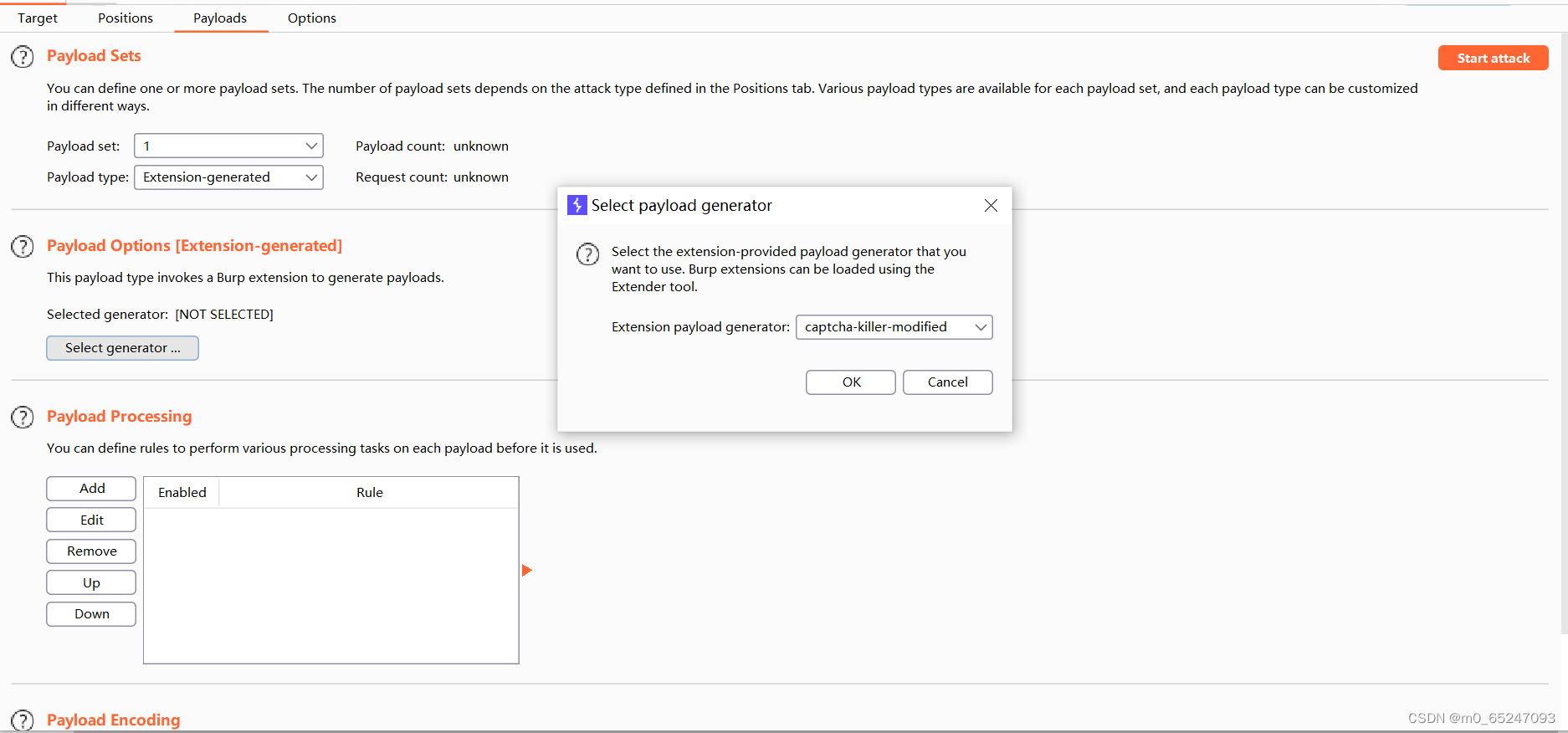
The third step in actual combat Setting of blasting module
0x01 Set variables for the verification code
边栏推荐
- Intranet information collection of Intranet penetration (5)
- Brief introduction to XHR - basic use of XHR
- SQL injection
- HackMyvm靶机系列(2)-warrior
- 7-5 staircase upgrade (PTA program design)
- JDBC事务、批处理以及连接池(超详细)
- 7-7 7003 组合锁(PTA程序设计)
- Feature extraction and detection 14 plane object recognition
- Mixlab unbounded community white paper officially released
- 7-5 走楼梯升级版(PTA程序设计)
猜你喜欢

Low income from doing we media? 90% of people make mistakes in these three points

How to turn wechat applet into uniapp
Sqqyw (indifferent dot icon system) vulnerability recurrence and 74cms vulnerability recurrence
攻防世界MISC练习区(SimpleRAR、base64stego、功夫再高也怕菜刀)
Record an edu, SQL injection practice
Experiment 6 inheritance and polymorphism

记一次edu,SQL注入实战
循环队列(C语言)
Data mining - a discussion on sample imbalance in classification problems
. How to upload XMIND files to Jinshan document sharing online editing?
随机推荐
XSS之冷门事件
[MySQL table structure and integrity constraint modification (Alter)]
xray与burp联动 挖掘
The most popular colloquial system explains the base of numbers
Build domain environment (win)
Tencent map circle
Hackmyvm target series (3) -visions
HackMyvm靶机系列(4)-vulny
A complete collection of papers on text recognition
XSS unexpected event
Meituan dynamic thread pool practice ideas, open source
Record an API interface SQL injection practice
The United States has repeatedly revealed that the yield of interest rate hiked treasury bonds continued to rise
实验九 输入输出流(节选)
Strengthen basic learning records
captcha-killer验证码识别插件
撲克牌遊戲程序——人機對抗
网络层—简单的arp断网
7-4 散列表查找(PTA程序设计)
实验七 常用类的使用